Overview of High Availability Deployment for IoT FND
IoT FND is a critical application for monitoring and managing a connected grid. This chapter discusses on IoT FND solution High Availability (HA), the different components, how it can be achieved, and what configurations are required to achieve it at various levels.
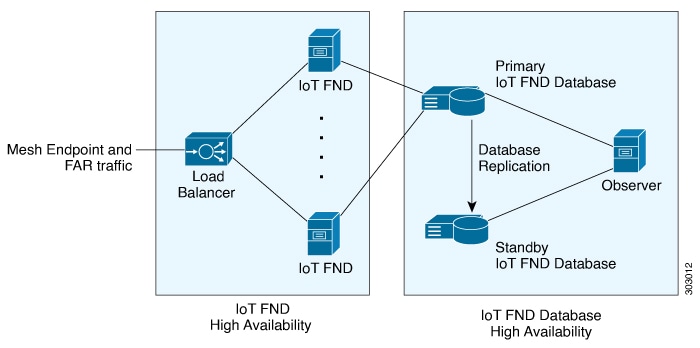
IoT FND provides two main levels of HA:
-
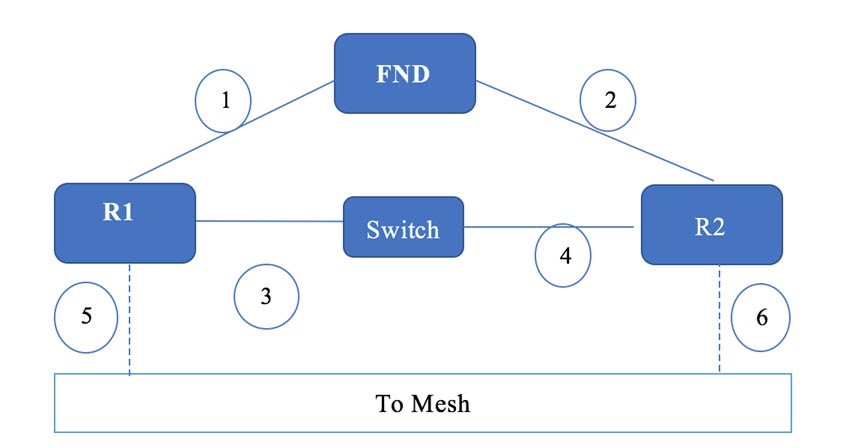
IoT FND Server HA—This is achieved by connecting multiple IoT FND servers to a load balancer. Traffic originating at Mesh Endpoints (ME), Field Area Routers (FAR), and Aggregation Services Routers (ASR) goes to the load balancer, which uses a load balancing algorithm to distribute the load among the IoT FND cluster servers.
-
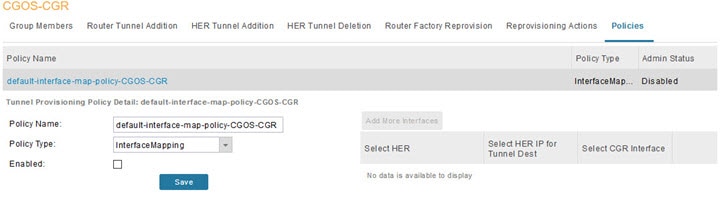
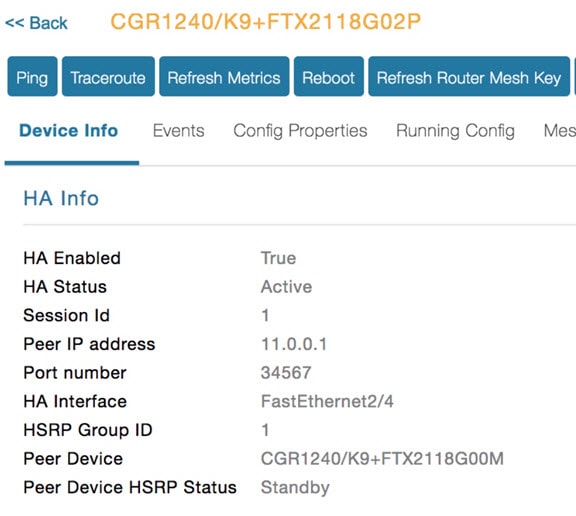
IoT FND Database HA—This is achieved by configuring two IoT FND Database servers: a primary server and a standby (or secondary) server. When the primary database receives new data it sends a copy to the standby database. A separate system runs the Observer (the Observer can also run on the standby server), which is a program that monitors the IoT FND Database servers. If the primary database fails, the Observer configures the standby server as the new primary database. IoT FND Database HA works in single and cluster IoT FND server deployments.
 Note |
To set up an Observer server which runs Oracle 12c on a separate server (distinct from the IoT FND Database servers), refer to the following instructions found on the online Oracle Help Center for Oracle 12c (12.1.0.2): Documentation Library. |
 Feedback
Feedback