Licensing Prime Cable Provisioning
To access this release, you must procure a new license of Prime Cable Provisioning 7.4.
 Note |
You need to get the permanent or evaluation license of 7.4 to upgrade from 5.x/6.x to 7.4. |
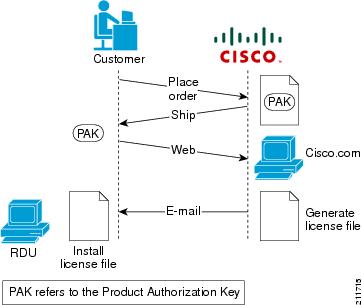
Prime Cable Provisioning software must be registered via Cisco.com in order to obtain a license file (*.lic). The license file will be sent to you by e-mail. For any licensing issues, please contact your Cisco account representative or mailto:ask-cableprovisioning@cisco.com.
Prime Cable Provisioning licenses are available either as a permanent or an evaluation license.
- Permanent -A permanent license is purchased for use in your network environment and activates the specific features for which it is intended.
- Evaluation -An evaluation license enables functionality for a specific length of time.
Prime Cable Provisioning evaluation licenses become invalid on a predetermined date. As such, evaluation licenses must be created when needed. To create your evaluation license, contact your Cisco representative, who will generate the necessary license file online and forward it to you via e-mail.
Prime Cable Provisioning enables you to install permanent and evaluation licenses at the same time. In addition, it also allows you to install more than one evaluation license. This enables you to increase your device limit when you are in short of licenses till you purchase a permanent license. While you can install more than one evaluation license, an expired license can be deleted and a new evaluation license (with a later expiry date), or a permanent license can be added. While deleting the expired license, ensure that the device limit of the new license at least equals the number of devices that is currently stored in the database.
Prime Cable Provisioning enables licensing using a Service License file. Each license translates to a DOCSIS IP device. The license file that you receive will contain the number of DOCSIS IP devices that are licensed.
Prior to Prime Cable Provisioning 5.x, every device type instance such as, DOCSIS, Computer, PacketCable, CableHome, etc. consumed a separate license. In addition, with dual-stack Computers, this approach created two IPDevice records, one each for IPv4 and IPv6, resulting in two licenses being consumed instead of one. In Prime Cable Provisioning 5.x, 6.x, the licensing scheme counts only the DOCSIS IP devices irrespective of whether the device is a stand-alone CM or an embedded eCM, each DOCSIS IP device consumes one license. Apart from the DOCSIS IP device, all other device types consume no license. In other words, Prime Cable Provisioning consumes only one license:
- if a subscriber has a CM to which a Computer and a PacketCable devices are connected.
- if a subscriber has a CM to which a dual-stack Computer and a PacketCable devices are connected.
- if a subscriber has an e-MTA or e-STB.
To know how the license mechanism for Prime Cable Provisioning 5.x is different from BAC 4.x, see the BAC 4.x and Prime Cable Provisioning 5.x Licensing Model document.
The Prime Cable Provisioning Admin UI shows the available and used licenses. You can also see the available and used licenses count through the API client.
 Caution |
Do not edit your license file. Changing the data in any way invalidates the license file. |
-
The DPE
-
The KDC, if you configure your network to support voice technology
While you must install the DPE license from the Admin UI, the KDC license continues to be proprietary as in previous releases, and is licensed during Prime Cable Provisioning installation.
The DPE license is either included in a single license file along with the Service License or it is a separate license file by itself. The DPE is licensed only when you install this license file from the Admin UI.
For detailed information on how to add and delete licenses, see the Cisco Prime Cable Provisioning 7.4 User Guide.
Obtaining a Permanent License
 Note |
With FlexLM licensing, you receive a Product Authorization Key (PAK) for each software CD package that you purchase. The PAK is affixed as a sticky label on the Software License Claim Certificate card that is included in your CD-ROM package. |
To obtain a permanent license:
Procedure
|
Step 1 |
Keep your PAK handy and access http://www.cisco.com/go/license. You must have a valid Cisco.com account to log into this site. The Product License Registration website appears. |
||
|
Step 2 |
Complete the steps detailed at the Product License Registration page.
|
||
|
Step 3 |
Once you receive your license file, install it using the procedure described in Installing Your License File. |
Obtaining an Evaluation License
For an evaluation license, contact your Cisco representative, who will generate the necessary key from the Cisco licensing website and e-mail it to you. Once you receive your license file, install it using the procedure described in Installing Your License File.
Installing Your License File
Before installing your license file, ensure that you back up your licenses in case you have to reinstall the Prime Cable Provisioning software.
To install your permanent or evaluation license:
Procedure
|
Step 1 |
Once you receive your license file, save each file to the local system on which you intend to launch your web browser. |
||
|
Step 2 |
Launch your web browser on that system. |
||
|
Step 3 |
Enter the administrator’s location using this syntax:
The main login page appears. |
||
|
Step 4 |
Enter the username and password.
|
||
|
Step 5 |
Click Login. The Main Menu page appears. |
||
|
Step 6 |
Click the license link at the top of the Main Menu page, or choose Configuration > License Keys. The Manage License Keys page appears. |
||
|
Step 7 |
In the License File field, enter the complete path to the location of the license file on your local system. Remember to include the name of the license file while specifying the pathname. Or, click Browse and navigate to the license file. |
||
|
Step 8 |
Click Add. The details regarding the number of services, the DPEs that you are licensed to use, and the type of license (Permanent or Evaluation) appear. |
Installing Your KDC License
Obtain a KDC license from your Cisco representative and then install it in the correct directory.
To install the KDC license file (bacckdc.license):
Procedure
|
Step 1 |
Obtain your license file from your Cisco representative. |
||
|
Step 2 |
Log into the Prime Cable Provisioning host as root or non-root. |
||
|
Step 3 |
Change to the <BPR_HOME>/kdc directory. |
||
|
Step 4 |
Copy the license file to this <BPR_HOME>/kdc directory.
|
||
|
Step 5 |
To restart the KDC server and make the changes take effect, run the bprAgent restart kdc command from the /etc/init.d directory. |

 Feedback
Feedback