Prerequisites
The following prerequisites must be met before you proceed with RDU redundancy setup:
Utility Requirements
-
Identify the two servers on which you wish to configure the primary and secondary RDU nodes.
-
RHEL 8.10 or Rocky Linux 8.10 must be installed on both of these servers.
Kernel 4.18.0-553 must be installed on both of these servers.
-
Network configuration file should contain only the system hostname, not the fully qualified domain name (FQDN).
 Caution |
In the network configuration file, if the system has FQDN name as hostname, it will cause failure in creating DRBD blocks. |
Redundancy Requirements
-
Redundant network configuration should be available to avoid network downtime.
-
Redundant electrical supply must be available on both servers. Ensure that the electrical supply source for both servers is reachable.
PCP Geo Redundancy Requirements
Route injection for VIP (virtual IP) needs to be done on the ingress routers to which primary and secondary servers are connected.
The VIP will be advertised as RIP2 advertisement from the active server ,so route redistribution needs to be done for RIP2 to the dynamic routing protocol running in the user environment.
Example: Here OSPF is the dynamic protocol
router ospf 1
redistribute rip metric-type 1 subnets.
Logical Volume Manager (LVM) Setup
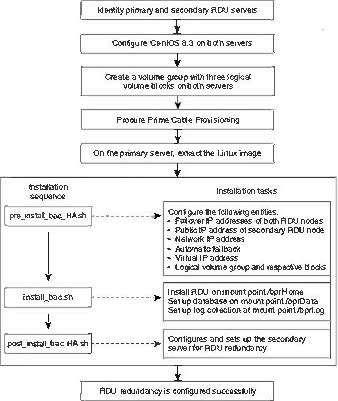
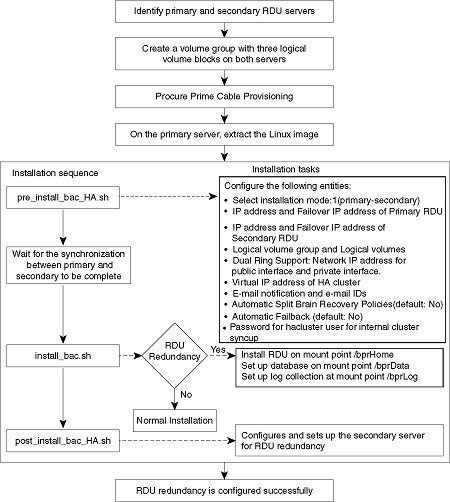
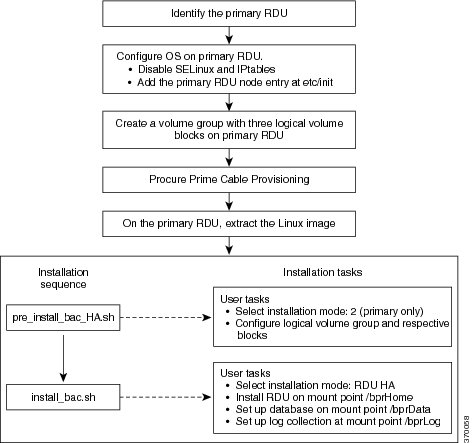
Both RDU nodes must be configured over Logical Volume Manager (LVM). The LVM allows you to create a volume group which can be further divided into logical volumes based on the requirement. The LVM also provides the flexibility to resize the volume group and logical volumes based on the dynamic memory usage.
-
On both primary and secondary RDU nodes, a logical volume group must be created with three logical volumes on it. The logical volumes are created based on the following specifications:
-
<logical volume for Prime Cable Provisioning install directory> - Mounted on /bprHome directory. For example, LVBPRHOME.
-
<logical volume for Prime Cable Provisioning data directory> - Mounted on /bprData directory. For example, LVBPRDATA
-
<logical volume for Prime Cable Provisioning log directory > - Mounted on /bprLog directory. For example, LVBPRDBLOG
-
-
Ensure that the /bprData, /bprHome, and /bprLog directories are empty.
-
The logical volumes should be of same capacity on both the nodes with a pre-created xfs filesystem.
Requirements for Proper Synchronization between Nodes
-
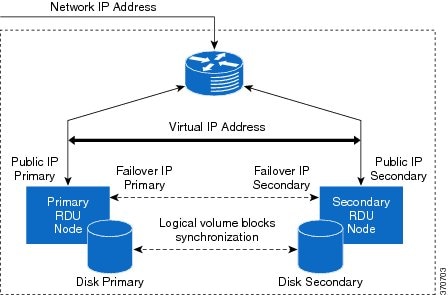
Identify the virtual IP address that can be used to locate both servers. Ensure that this virtual IP address is not configured for any physical interfaces in the network infrastructure. Also, this virtual IP address must belong to the network cluster in which you configure the primary and secondary RDU nodes.
-
In PCP Geo redundancy solution the VIP can be in any subnet
-
Identify the network IP addresses for public and private interface to configure dual ring support. For more information on dual ring support, see Cisco Prime Cable Provisioning User Guide.
-
The Network Time Protocol (NTP) must be synchronized between primary and secondary RDU nodes.
-
Both RDU nodes must exist in the same network cluster. This ensures that the same virtual IP address can be used to reach both the RDU nodes.
-
Both RDU nodes must be configured with the following two network interfaces:
-
Public access - Used for external communication. The DPE, REST PWS, CPNR_EP, and API clients use this interface to communicate with the RDU. A public IP address is configured to access this network interface.
-
Failover link between RDU nodes - Used for disk synchronization. If the RDU nodes are co-located, the failover link can be a crossover link, else the failover link must be configured in the private LAN. The failover IP addresses for primary and secondary nodes must be unique in the network cluster. This is to achieve the high speed access between primary and secondary RDU nodes, and also make them isolated from the network traffic.
-
Miscellaneous Requirements
-
To enable RDU HA notifications support, ensure that the SMTP server is configured. For more information on RDU HA notifications, see Cisco Prime Cable Provisioning User Guide.
-
Both RDU nodes must be configured with Gigabyte network interfaces.
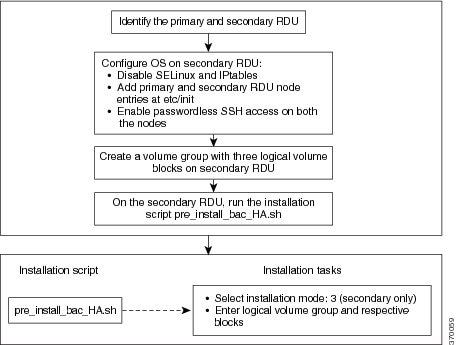
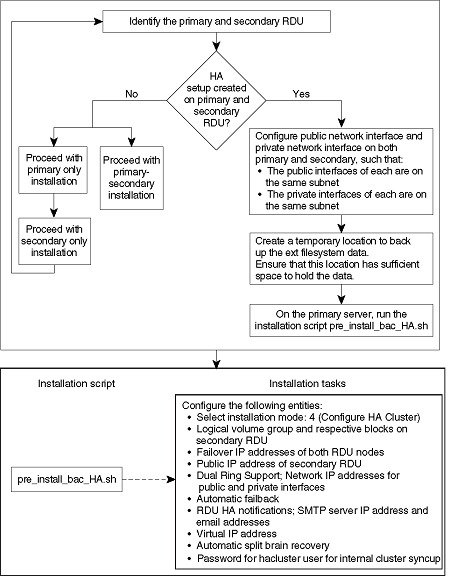
The following figure provides a high level RDU HA setup.

 Feedback
Feedback