Download Cisco Edge Intelligence software
Two Cisco Edge Intelligence software packages are available on software.cisco.com, based on how you want to install the agent on your devices:
-
Using the IOx Local Manager.
-
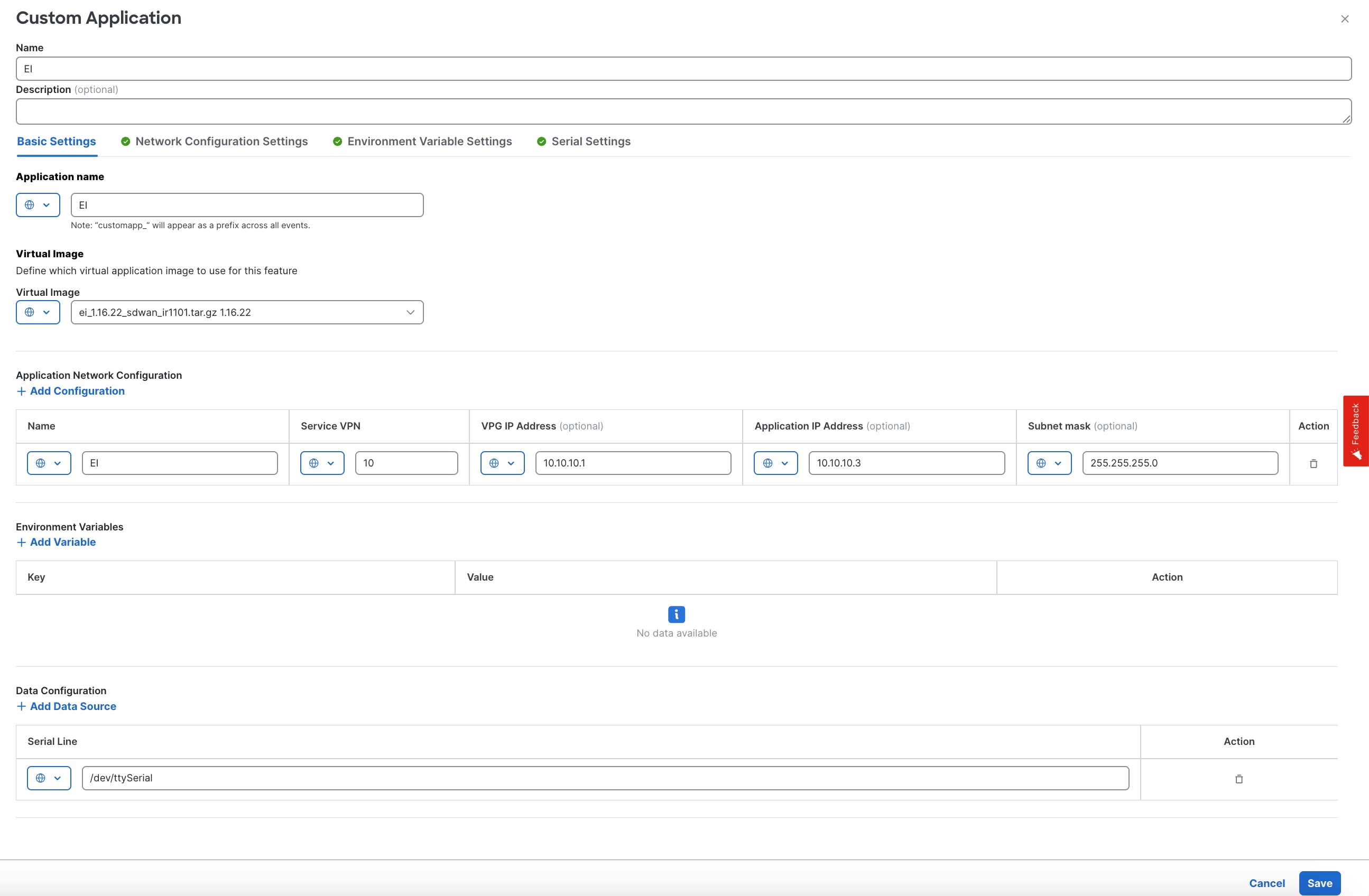
Using the Cisco Catalyst SD-WAN Manager.

 Feedback
Feedback