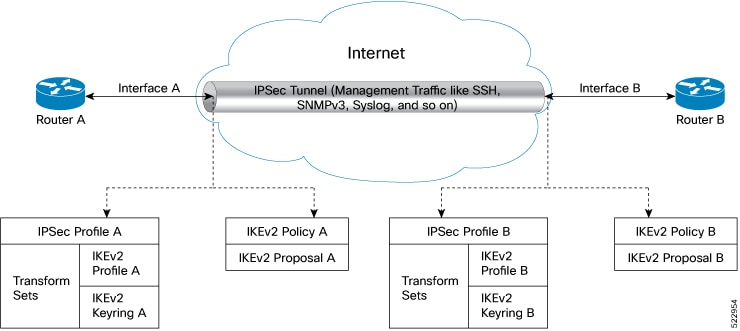
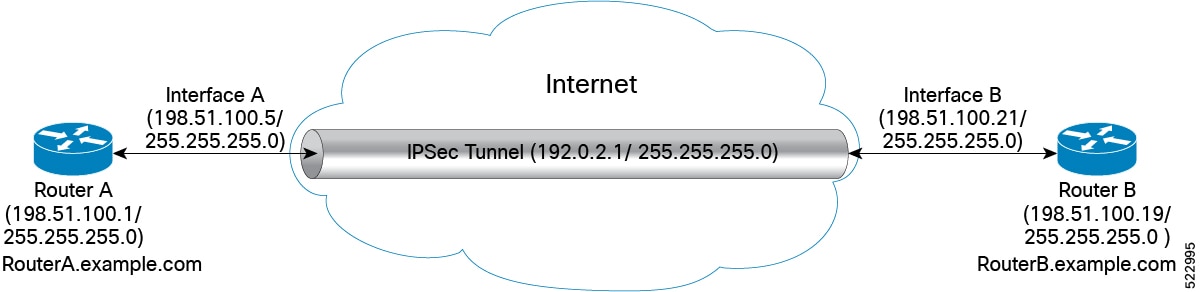
Restrictions for IP Security for Management Traffic
The following are some basic restrictions and limitations of the IPSec feature:
-
IPSec feature is supported only on N540X-12Z16G-SYS-A chassis.
-
IPsec feature is available for IPv4 traffic only.
-
IPSec feature is available only in tunnel mode.
-
IPSec is supported only on locally sourced traffic.
-
IPSec feature supports the management traffic over Management interfaces and Data ports.
-
For SSH authentication in IPsec tunnels, the default-route software-forwarding command must be applied within the default or a user-configured VRF instance, depending on the tunnel's configuration. If the IPsec tunnel is part of the global routing table, the command should be applied to the default VRF instance. If the tunnel is assigned to a user-configured VRF, the command must be applied to the associated VRF routing table. Some routers rely on software forwarding to handle packets that require additional software-based processing.
-
This example demonstrates how to apply the command in the default VRF (global routing table):
Router(config)#linux networking Router(config-vrf)#vrf default Router(config-vrf)#address-family ipv4 Router(config-vrf-afi)#default-route software-forwarding -
This example demonstrates how to apply the command in a user-defined VRF (custom routing table):
Router(config)#linux networking Router(config-vrf)#vrf vrf_name Router(config-vrf)#address-family ipv4 Router(config-vrf-afi)#default-route software-forwarding
The restriction applies to these routers:
-
N540X-16Z4G8Q2C-A/D
-
N540X-16Z8Q2C-D
-
N540-28Z4C-SYS-A/D
-
N540X-12Z16G-SYS-A/D
-
N540-12Z20G-SYS-A/D
-
-
IPSec tunnel failure results in packet loss.
-
IPSec process restart is stateless and results in packet loss.

 Feedback
Feedback