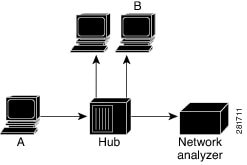
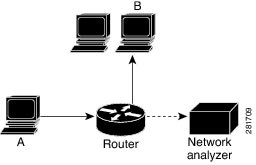
Traffic mirroring
Traffic mirroring or port mirroring is a network monitoring feature that
-
monitors Layer 3 network traffic passing in or out of Ethernet interfaces
-
directs this traffic to a network analyzer for analysis, and
-
operates as a proprietary function under Cisco Switched Port Analyzer (SPAN).
|
Feature Name |
Release Information |
Feature Description |
|---|---|---|
|
Traffic Mirroring |
Release 25.1.1 |
Introduced in this release on: Fixed Systems (8010 [ASIC: A100]) Traffic mirroring, also known as port mirroring or Switched Port Analyzer (SPAN), is a proprietary feature by Cisco. It allows the monitoring of Layer 3 network traffic that enters or exits a set of Ethernet interfaces. This mirrored traffic can then be directed to a network analyzer for further analysis. This feature is now supported on:
|
Benefits of traffic mirroring
Traffic mirroring allows you to
-
monitor Layer 3 network traffic
-
analyze traffic using a network analyzer, and
-
mirror traffic without affecting the switching of traffic on source interfaces.

 Feedback
Feedback