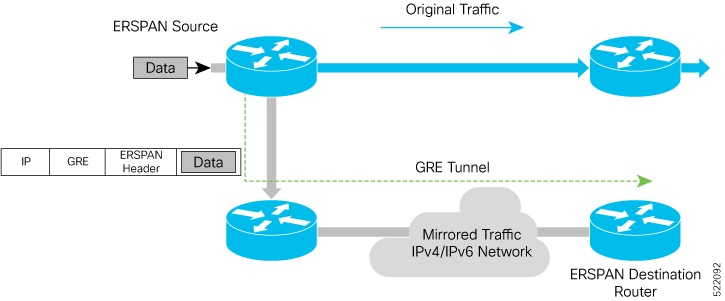
ERSPAN
Encapsulated Remote Switched Port Analyzer (ERSPAN) is a traffic mirroring feature that
-
monitors network traffic from one or more source ports on a router
-
mirrors traffic from one or more source ports, and
-
sends the mirrored traffic through GRE tunnels to destinations for analysis.
|
Feature Name |
Release Information |
Feature Description |
|---|---|---|
|
Higher payload analysis with eight ERSPAN sessions |
Release 25.4.1 |
Introduced in this release on: Fixed Systems (8010 [ASIC: A100])(select variants only*) *This feature is now supported on:
|
|
Higher payload analysis with eight ERSPAN sessions |
Release 25.1.1 |
Introduced in this release on: Fixed Systems (8010 [ASIC: A100] ) This feature is now supported on Cisco 8011-4G24Y4H-I routers. |
|
ERSPAN over GRE IPv6 |
Release 25.1.1 |
Introduced in this release on: Fixed Systems ( 8700 [ASIC: K100] , 8010 [ASIC: A100] ) This feature is now supported on:
|
|
Higher payload analysis with eight ERSPAN sessions |
Release 24.4.1 |
Introduced in this release on: Fixed Systems(8200 , 8700)(select variants only*); Modular Systems (8800 [LC ASIC: P100]) (select variants only*). This feature now enables the Cisco 8000 Series routers to support eight ERSPAN sessions on the following hardware thus allowing you to analyze higher payloads in real time across Layer 3 domains on your network. *This feature is now supported on:
|
|
ERSPAN over GRE IPv6 |
Release 24.4.1 |
Introduced in this release on: Fixed Systems(8200 , 8700)(select variants only*); Modular Systems (8800 [LC ASIC: P100]) (select variants only*). With this release, the router allows you to mirror IPv4 or IPv6 traffic with ERSPAN over GRE IPv6 sessions to monitor traffic on remote traffic analyzers on the following hardware. *This feature is now supported on:
|
|
Partial packet capture ability for ERSPAN (Rx) |
Release 7.5.3 |
With this feature, you can perform partial packet capture in the Rx direction. Earlier, the ability for entire packet capture was available, now you can choose entire or partial packet capture in the Rx direction. Here, partial packet capture is also known as truncation. |
|
ERSPAN over MPLS traffic |
Release 7.3.5 Release 7.5.3 |
With this release, the router allows you to mirror MPLS traffic and set up the GRE tunnel with the next hop over a labeled path. This feature helps you to remote-monitor the traffic on traffic analyzers. |
Benefits of ERSPAN
These are the benefits of ERSPAN:
-
It enables real-time network troubleshooting.
-
It automates configuration processes, allowing network operators to troubleshoot issues in real-time and send specific flows to management servers for detailed analysis.
-
It transports mirrored traffic over an IP network and encapsulates it at the source router for transfer across the network

 Feedback
Feedback