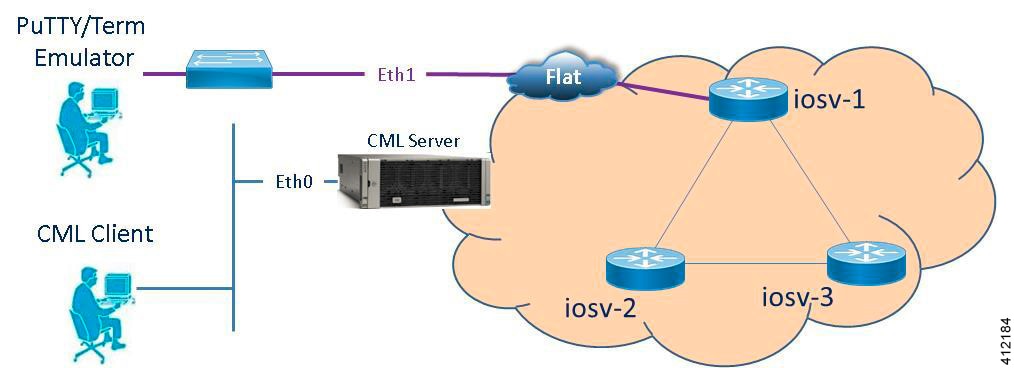
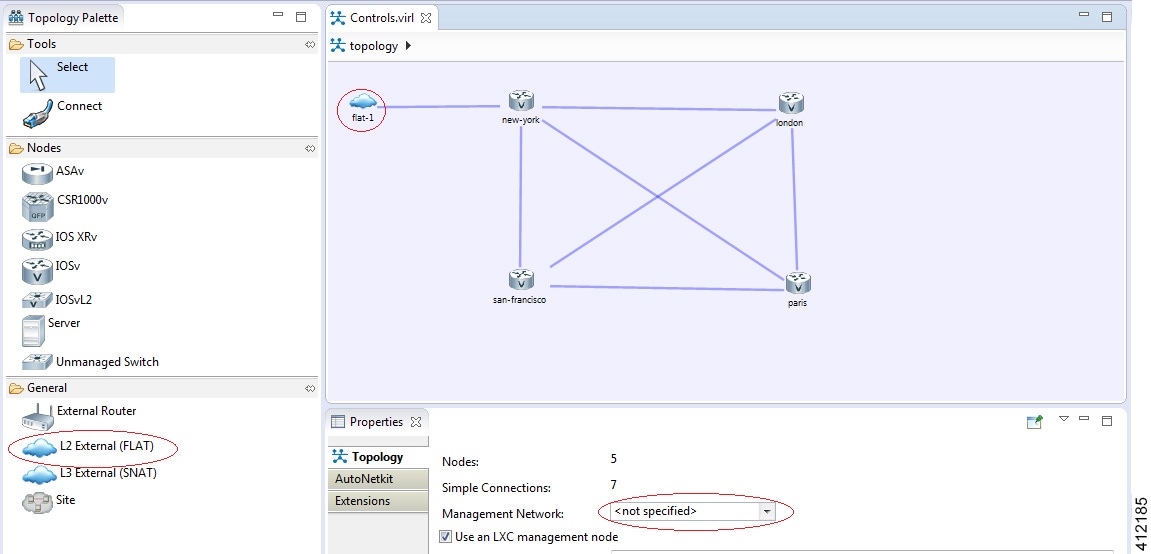
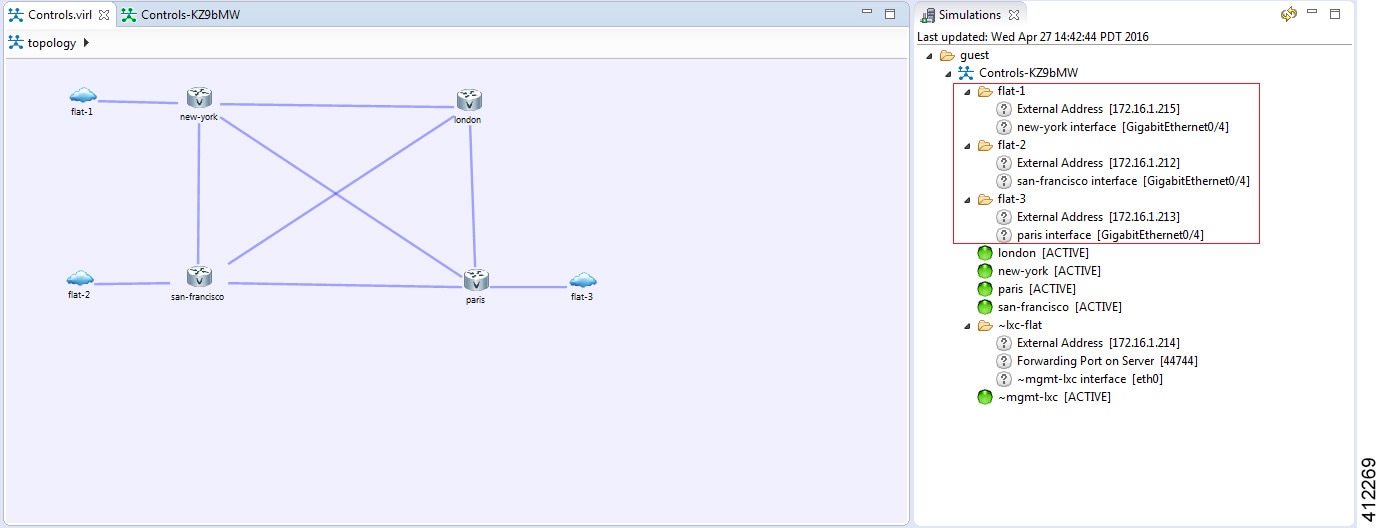
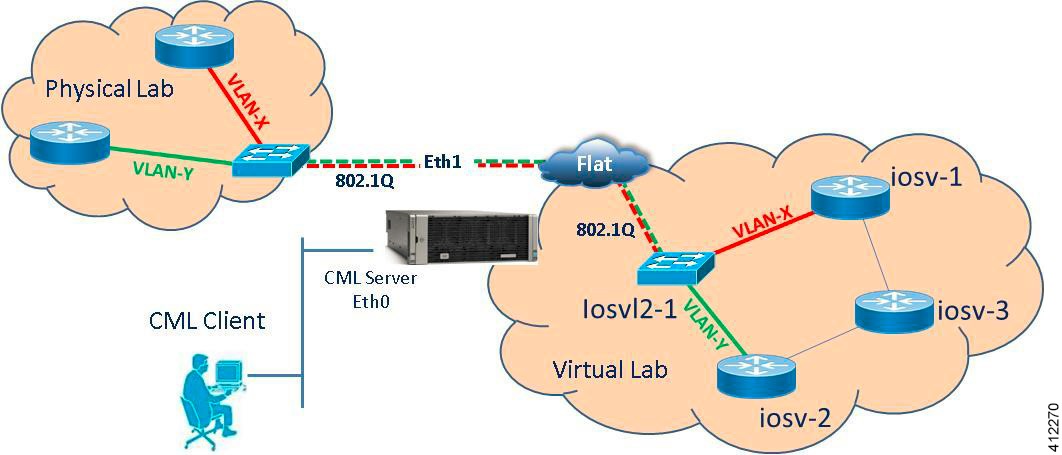
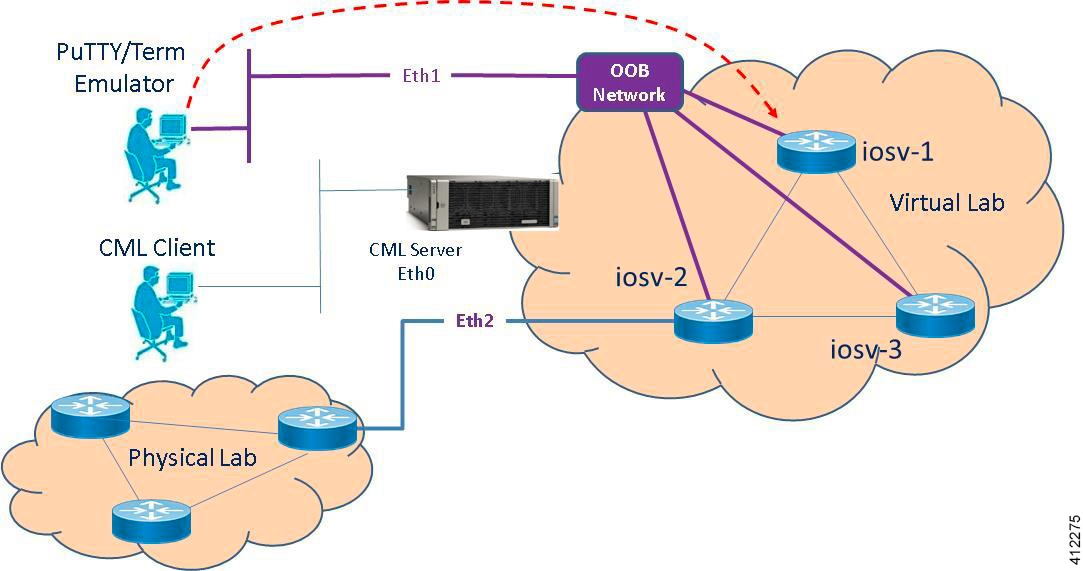
Basic Node Access
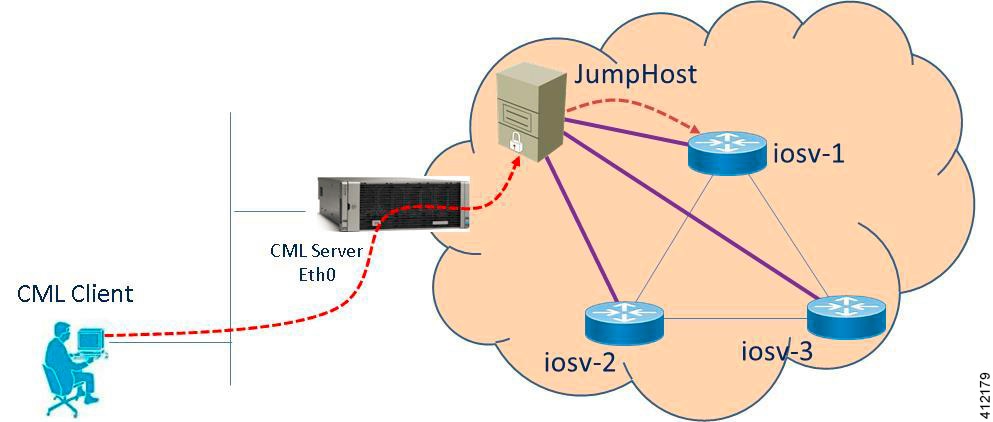
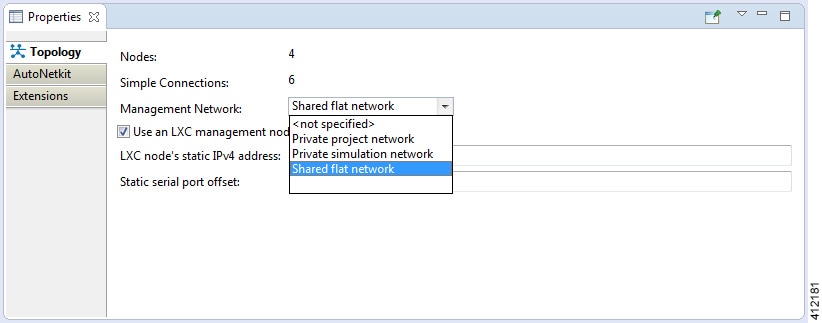
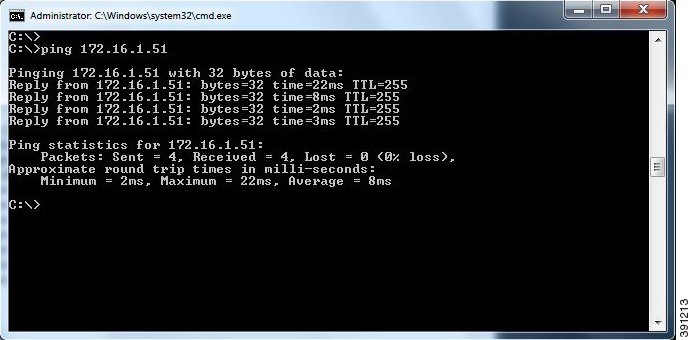
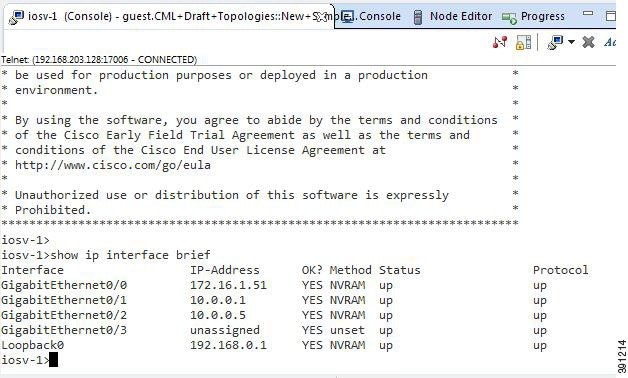
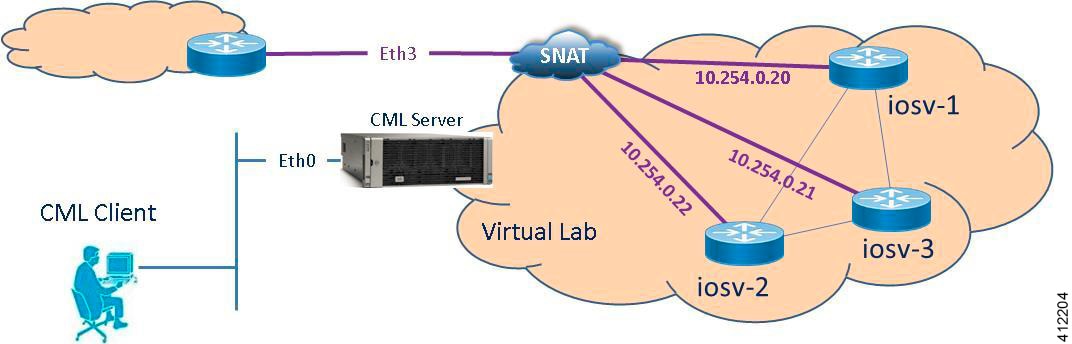
For simple network topology simulations, access to simulated nodes can be conducted through the Cisco Modeling Labs server’s management interface , Ethernet0. This is useful for simulation scenarios that do not require connection to external devices, and leverages the Cisco Modeling Labs server's management interface for communications with the virtual devices. No Flat or SNAT interfaces are configured or referenced, and no option is specified within the project’s setting. In this minimal configuration, connections to the virtual nodes instances are facilitated through the Cisco Modeling Labs’s client Server management option.
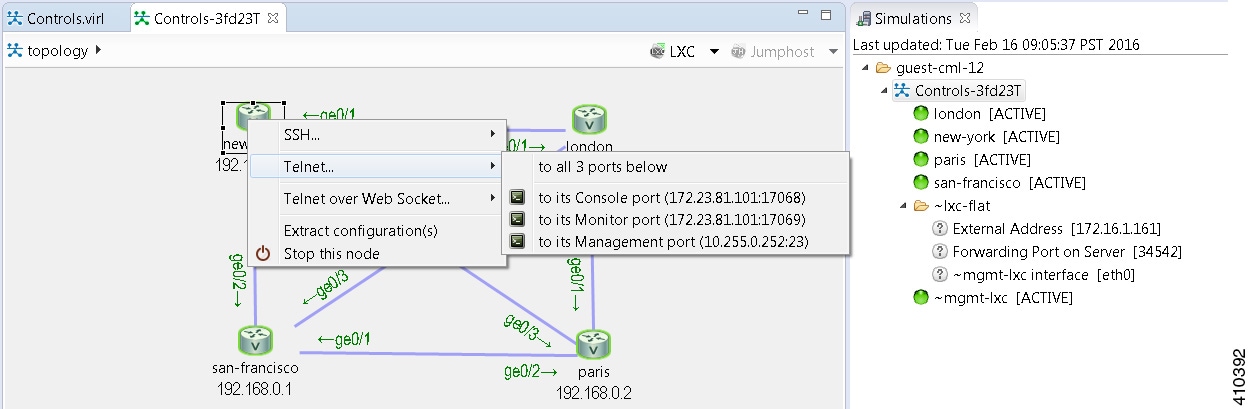
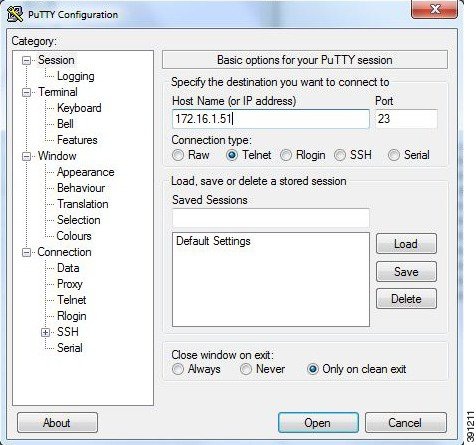
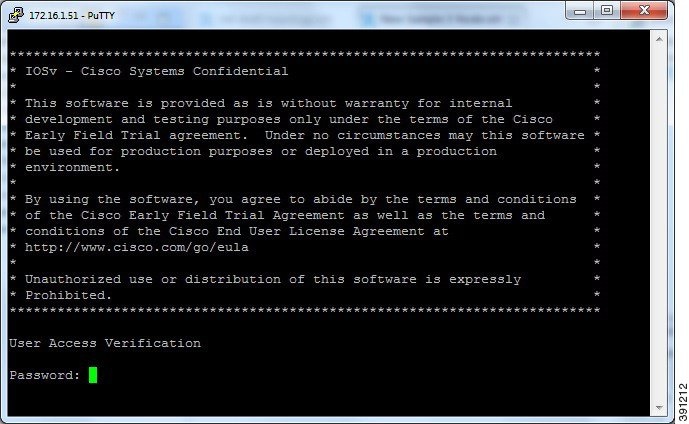
Telnet via Cisco Modeling Labs Client Console
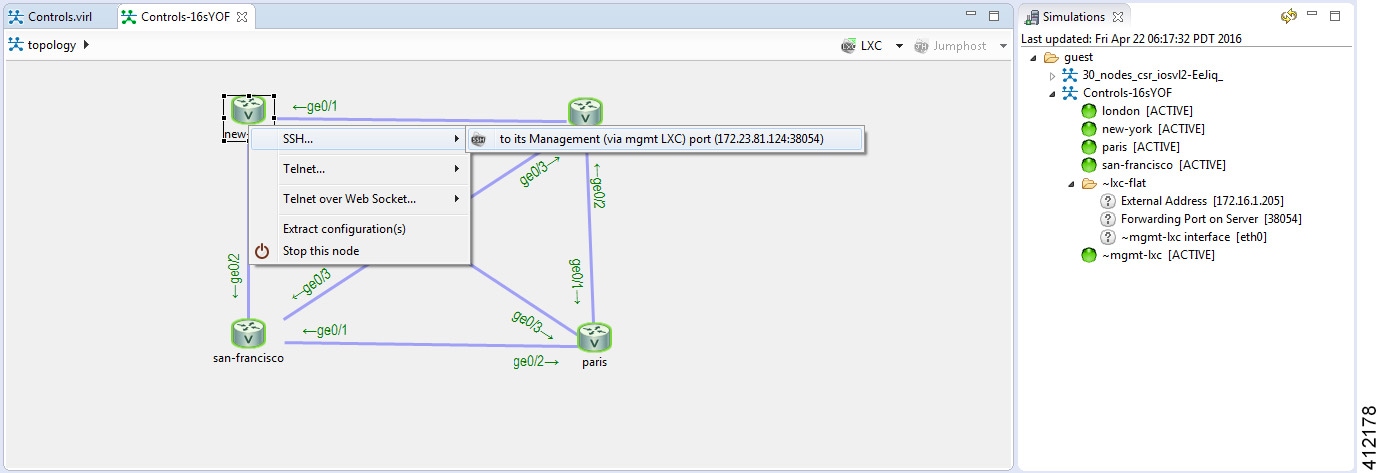
SSH via Cisco Modeling Labs Client Console
Access via User Workspace Management Interface
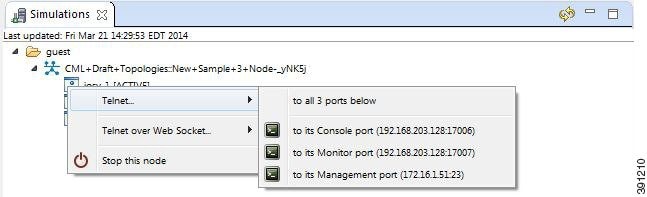
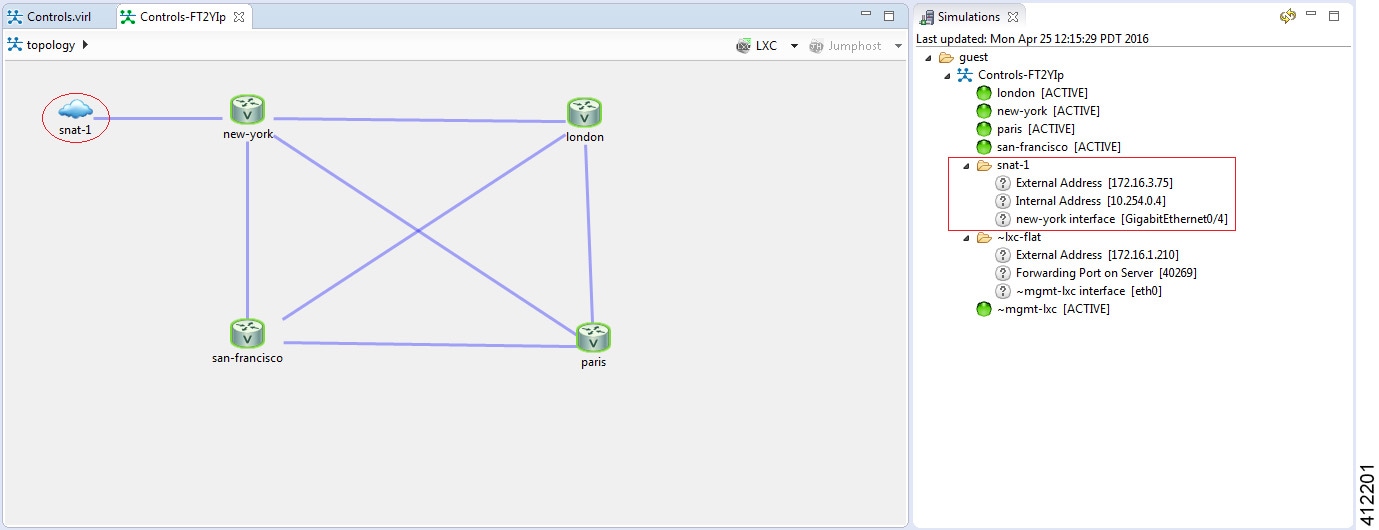
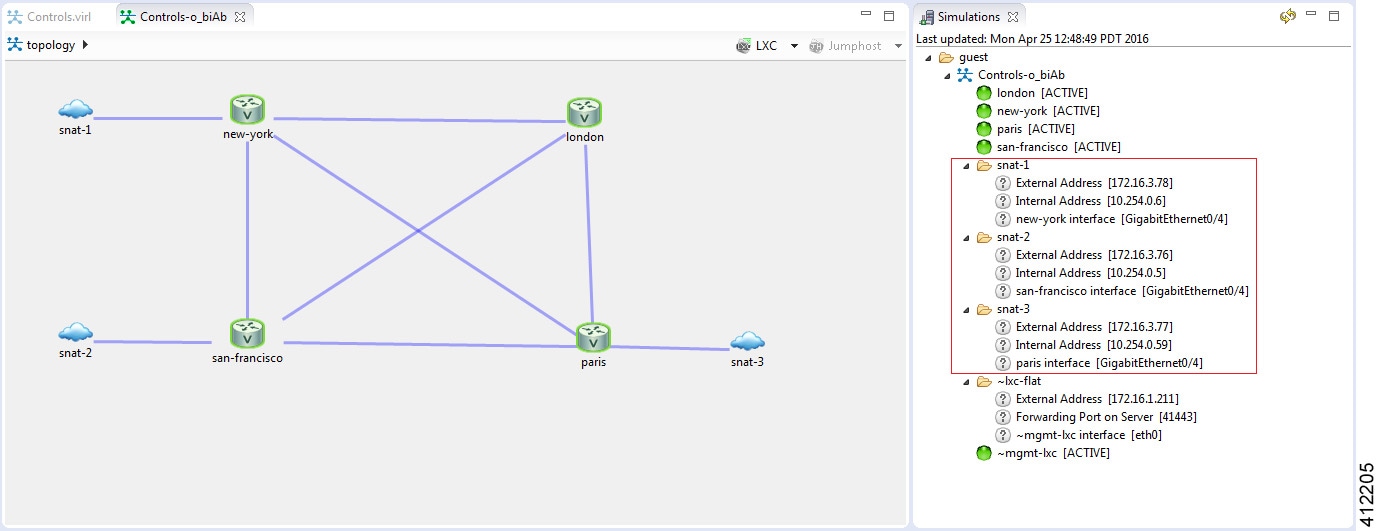
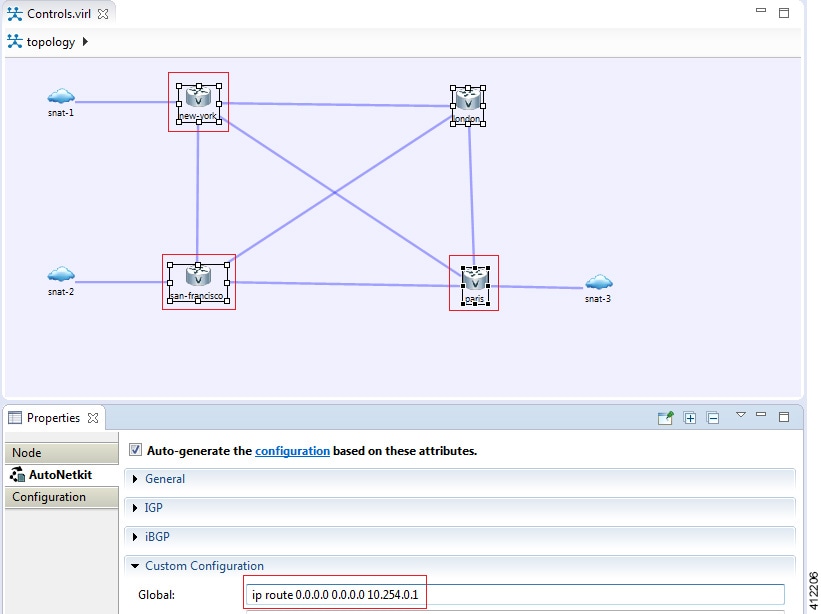
Another option is to access the nodes in a running simulation through the User Workspace Management interface via a web browser. After entering log in credentials, click the My Simulations option to view a list of running simulations. Select the applicable simulation to view a list of nodes comprising the running simulation. To access a node, click one of the ports icons, representing Serial-0, Serial-1, or the Management port, associated with the desired node. As shown, a corresponding session is started for the selected node.



 Feedback
Feedback