Getting started
After installing the Change Automation and Health Insights applications, there are a few initial steps that administrators must complete to ensure the application is properly configured and ready for use. For installation details, see the Cisco Crosswork Network Controller Installation guide.
Change Automation can be used independently or as part of workflows that leverage Health Insights or other applications.
Before you begin:
-
Make sure to install the Change Automation and Health Insights applications. See the Cisco Crosswork Network Controller Installation guide.
This initial setup includes configuring system settings, assigning appropriate user access levels, creating device access groups, and device tags. The following sections provide detailed guidance on each of these steps.
Verify installation and configure system settings
This section describes the system settings that must be configured to begin using Change Automation.
Change Automation provides several ways to run playbooks. As part of the initial activation process, you will need to select your preferred method for running playbooks.
-
Manually ("on demand") or via scheduled execution. These two methods are typically used for playbooks that accomplish data collection, configuration changes, or SMU deployment independent of any KPI-related fault detected in the network.
-
Manually or automatically when the playbook is tied to a KPI. These methods are typically used when you want to run a playbook intended to remediate a fault detected in the network. Key parameters needed to run the playbook are populated when the alert tied to the KPI is triggered.
To verify application installation and configure system settings:
-
Navigate to .
The first time you access Change Automation, you will see the Welcome to network automation page where the system will prompt you to complete the application's configuration.
Figure 1. Welcome to network automation 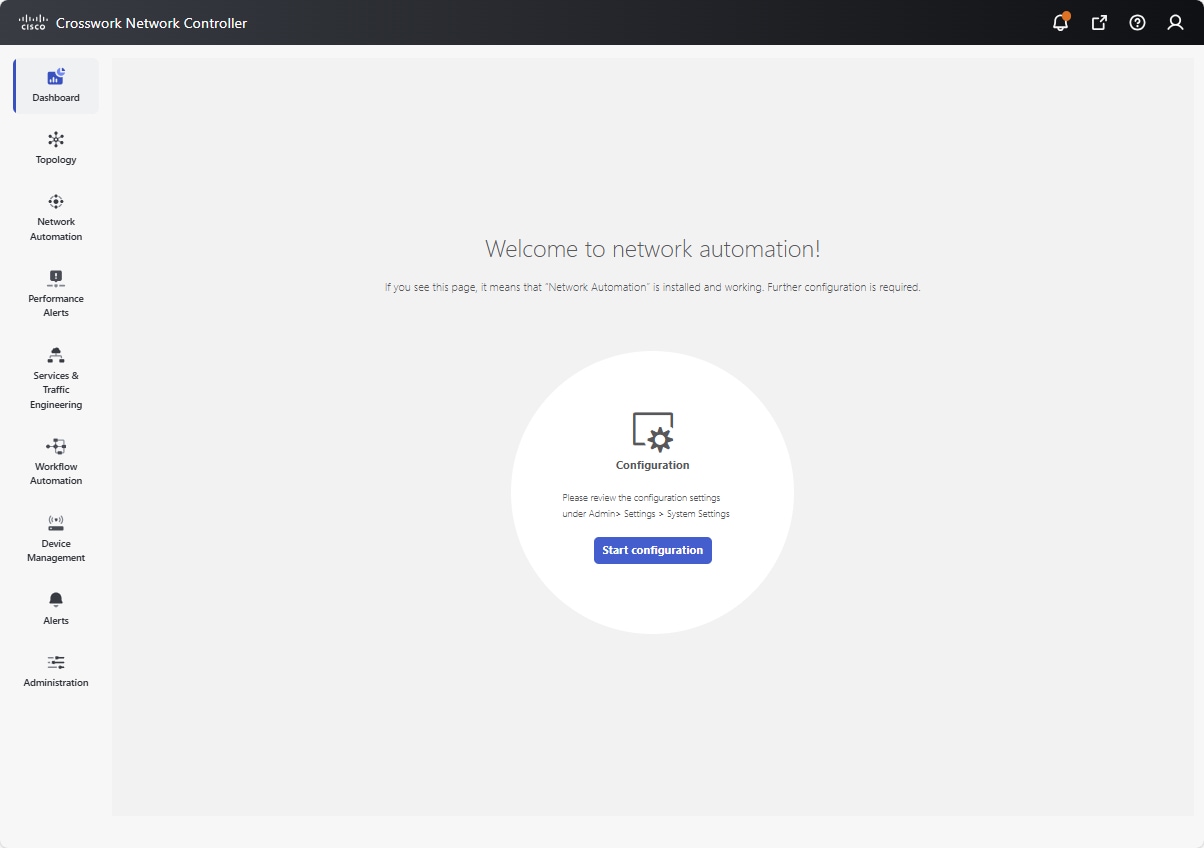
-
Click Start configuration or optionally, navigate to to make the settings.
Figure 2. System settings - Device override credentials 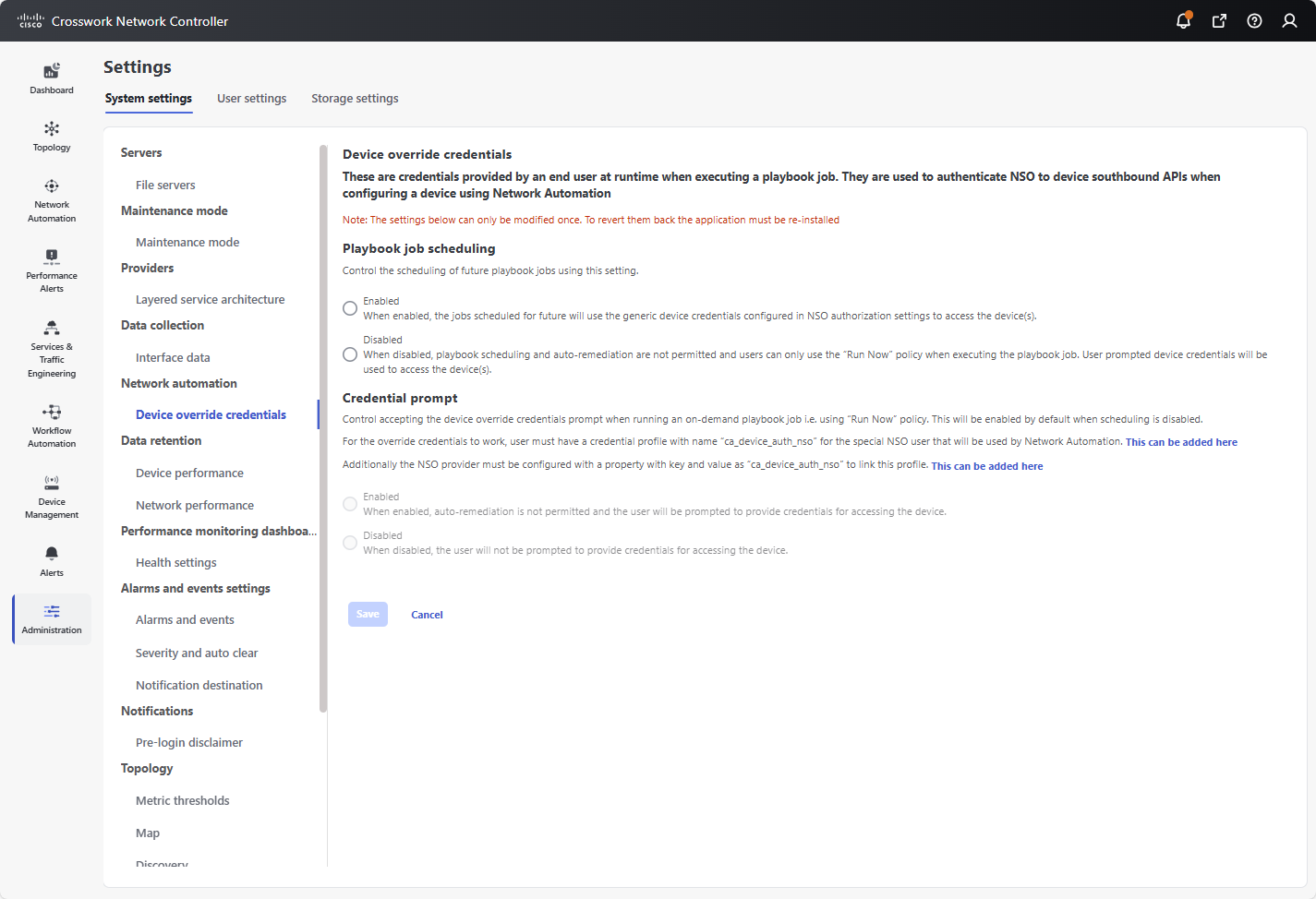
-
During this initial setup, you will be required to configure device override credential settings for Playbook job scheduling and Credential prompt. These settings work together to determine whether playbooks can be run unattended, either as a scheduled task or as automatic remediation to changes detected in the network by Health Insights.

Note
The Change Automation settings can only be configured once. If you need to modify them later, Change Automation must be re-installed. Before re-installing, export any plays or playbooks you have created, and after re-installing, import them. For more information, see Export plays, Import custom plays, Export playbooks, and Import playbooks.
Playbook job scheduling: This setting enables or disables the ability to schedule playbook jobs.
Credential prompt: This setting determines whether user interaction is required when running an on-demand playbook.

Note
In addition to the administrative user account needed to allow Crosswork Network Controller to communicate with NSO, a second credential profile with name "ca_device_auth_nso" must be created for the override credentials to work when running playbooks. For details on creating credential profile in NSO, see Cisco Crosswork Change Automation NSO Function Pack Installation Guide.
If Playbook job scheduling is...
and the Credential prompt is...
This will...
enabled
disabled
enable both automatic playbook scheduling and auto-remediation. With this setting:
-
future jobs will use generic device credentials configured in Cisco NSO to access the devices.
-
you will not be prompted to provide credentials for accessing the device.
-
the system will be able to automatically detect network issues and take corrective actions without requiring manual intervention.
-
you can run playbooks automatically whenever the KPI linked to that playbook raises an alert of sufficient severity.
enabled
enabled
only enable automatic playbook scheduling. With this setting:
-
automatic remediation is not permitted.
-
you will be prompted to provide credentials for accessing the device.
-
future jobs will use generic device credentials configured in Cisco NSO to access the devices.
-
you can run playbooks automatically whenever the KPI linked to that playbook raises an alert of sufficient severity.
disabled
enabled (by default)
disable both automatic playbook scheduling and auto-remediation. With this setting:
-
you can only use Run Now to run the playbook job.
-
you will be prompted to provide credentials for accessing the device.
-
credential prompt is enabled by default and cannot be disabled.
Special considerations
-
If Credential prompt is enabled: While executing Device Config plays, entering incorrect device override credentials will cause the playbook execution to fail. However, for a Check play or Data Collection play, the device override credentials are not validated and the playbook will execute successfully irrespective of their accuracy.
-
If Credential prompt is disabled: Only user IDs with write permissions for Administration APIs under Change Automation can complete the credential profile and provider setup tasks. If you are unsure if your user ID has the required privileges, you can check by selecting and inspecting the ID's privileges.
-
-
Once you have made your selections as per your requirements, click Save to commit to these settings.
Assign user access levels
Once the system settings are configured, an administrator should review user roles to ensure that all users have the appropriate level of access required for Change Automation and Health Insights management.
Change Automation API permissions allow users to run, import, and create plays and playbooks. Only users with write permissions for Administration APIs can disable or enable playbook execution access and assign labels.
Health Insights KPI Management APIs allow users to:
-
Create, edit, or delete KPIs and KPI profiles.
-
Monitor the status of KPI-related jobs.
-
Configure alerts to proactively manage network performance.
To enable user access for Change Automation and Health Insights:
Procedure
|
Step 1 |
Go to . |
|
Step 2 |
Under the Roles pane, select the role to which you want to grant access. |
|
Step 3 |
Under , find Change Automation. |
|
Step 4 |
For Play and Playbook APIs, enable Read and Write check boxes (as necessary). 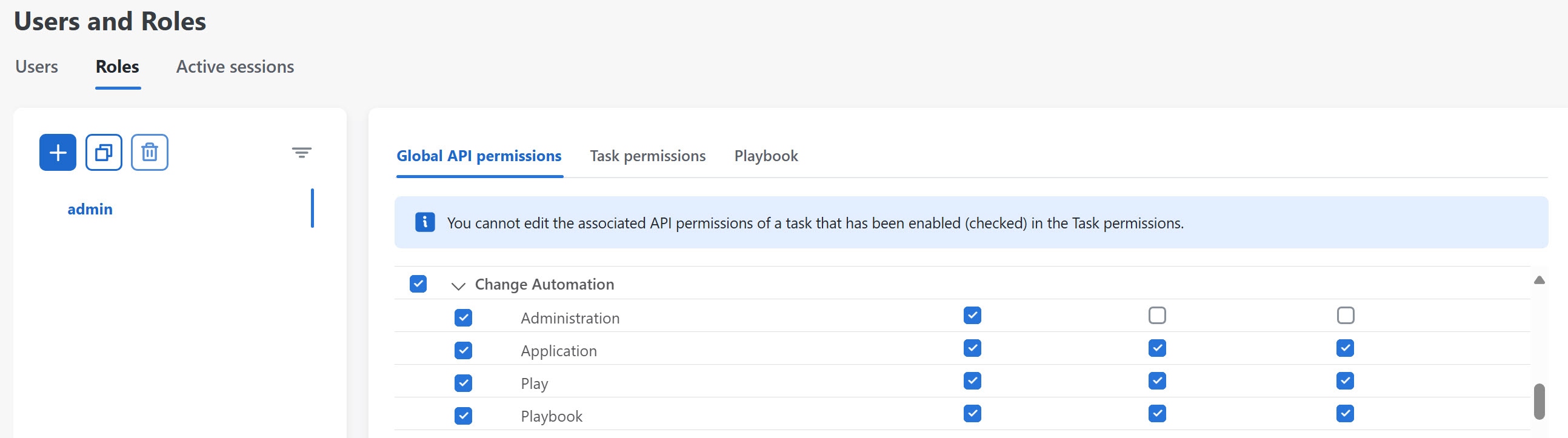
|
|
Step 5 |
Scroll down to find Health Insights. |
|
Step 6 |
For Health Insight KPI Management, enable Read and Write check boxes (as necessary). 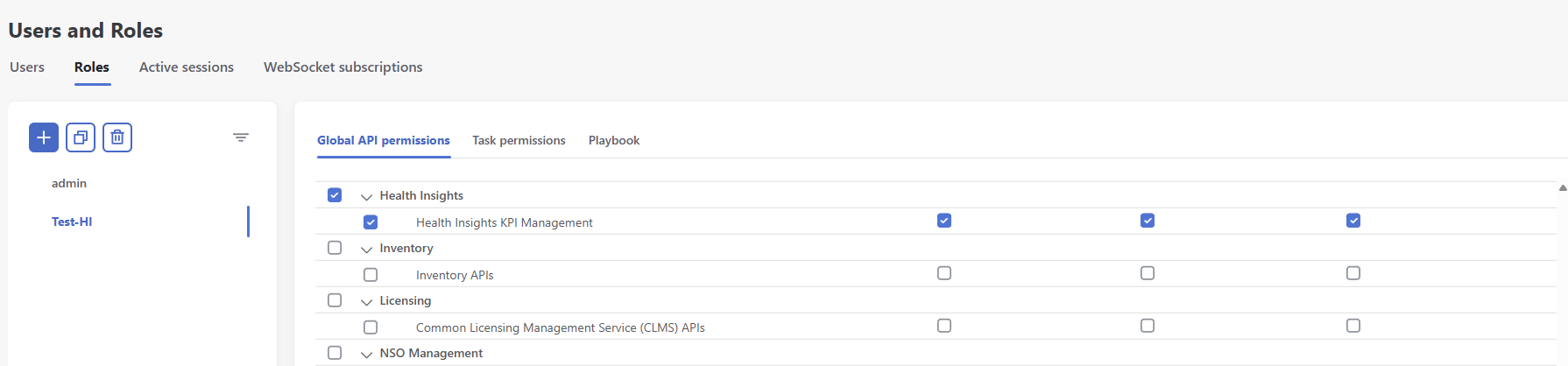
|
|
Step 7 |
Click Save. |
Create Device Access Groups
After administrators have assigned the required permissions to users, they can further control which devices users are allowed to access and manage. This can be achieved using Device Access Groups, which logically group devices to streamline access control. Non-administrative users with the system-level task of Device Access Groups management can create and manage these groups as needed.
For more information on Device Access Groups and how to associate a user with a Device Access Group, see the Manage Device Access Groups section in the Cisco Crosswork Network Controller Administration guide.
Create device tags
Device tags in Crosswork Network Controller are optional but highly beneficial for organizing and streamlining network management. They allow you to group devices based on shared attributes, making it easier to run playbooks or create KPI profiles. Tags can also provide useful information, such as a device’s physical location or its administrator’s email ID. Once you have a set of devices with the same tag, you can use it to:
-
run playbooks on a specific group of devices. For example, if devices are tagged by region, you can run a playbook exclusively on devices in that region.
-
build KPI profiles tailored to a group of devices. Newly tagged devices are automatically included in the existing KPI profiles, eliminating the need for manual updates.
For more information on creating device tags, see the Manage Tags section in the Cisco Crosswork Network Controller Administration guide.
 Feedback
Feedback