Field Notice: FN74284 - Cisco Firepower Device Manager: Some Firepower Software Releases Might Not Auto-Renew Talos Root Certificate After March 30, 2025 - Software Upgrade Recommended
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Products Affected
| Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|
| Firepower Threat Defense (FTD) Software | 7 | 7.6.0, 7.7.0 |
Defect Information
| Defect ID | Headline |
| CSCwo63951 | FMC/FDM Client side certificate used to communicate to Talos did not auto-renew correctly |
Problem Description
The Cisco Secure Firewall Device Manager (FDM) uses a client-side certificate to authenticate with the Cisco Talos threat intelligence service to download updates for the URL Reputation Databases (URLDBs), Lightweight Security Packages for Intrusion Rules (LSPs), and other enrichment data. Some releases of Cisco Firepower Software might not auto-renew this certificate after March 30, 2025, and this prevents updates to the URLDB and LSP threat intelligence databases.
Background
The client-side certificate used by FDM to communicate with the Cisco Talos threat intelligence service is pre-provisioned during Cisco Firepower Software installation and upgrades. It is auto-renewed when it nears expiration, but some releases fail to complete the auto-renewal process after March 30, 2025, and a process restart is required to perform the certificate renewal.
To check the current expiration date of the certificate, run the following sudo command in expert mode:
> expert
$ sudo openssl x509 --in /var/sf/beaker3/securefirewall-dev-prod-01_prod.pem --text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 46240369 (0x2c19271)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = US, ST = California, L = San Jose, O = Cisco Systems Inc., OU = Security, CN = Keymaster CA 2
Validity
Not Before: Jan 30 22:32:39 2024 GMT
Not After : Mar 30 22:32:39 2025 GMT
Subject: CN = SFW76EVAL-prod-01, C = US, ST = California, L = San Jose, O = Cisco, OU = Security
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:e5:3c:4f:84:b0:95:71:18:87:23:bf:96:88:f5:
e4:e7:d2:4d:3f:40:7a:a9:2f:54:aa:19:e4:bb:5c:
3a:23:89:56:23:c7:9a:53:69:88:35:0e:8d:ae:51:
0f:bb:eb:70:5c:40:03:bd:f5:d7:2b:80:8b:16:fc:
88:3c:46:36:3e:d8:1d:73:40:b6:26:4c:a1:28:d7:
e7:6f:7d:35:b3:69:1b:70:39:70:de:1c:7e:a8:8c:
da:0f:50:36:6a:f2:be:75:64:63:d1:df:03:2c:f1:
d7:19:be:12:e0:d4:3c:cd:21:83:15:92:6b:16:83:
a7:39:fc:0c:91:ca:9a:1e:64:15:ad:f2:ad:e8:30:
d1:28:a1:2d:d3:ce:83:cc:b5:13:56:be:9c:73:e9:
60:aa:54:4a:32:81:5d:08:32:b2:0d:52:a2:38:db:
e5:fd:cf:af:36:76:56:26:19:9a:33:9f:a0:db:04:
3e:54:3e:94:be:06:06:87:24:8f:05:47:80:0a:ac:
5e:04:d6:26:89:58:dd:76:7d:6a:de:ba:b8:a6:34:
9b:c4:7a:ad:c0:28:e7:36:01:08:07:ac:09:0e:fb:
c2:74:b6:58:b8:1c:fd:4d:7e:ab:04:da:62:4f:1f:
35:b3:08:00:20:02:81:72:11:d9:de:33:71:b5:e2:
49:3b
Exponent: 65537 (0x10001)
….
Note: The Not After date is the current expiration date of the client-side certificate.
Problem Symptom
The Cisco FDM Task List screen will display the following error to indicate failure of the LSP for Intrusion Rules database update.
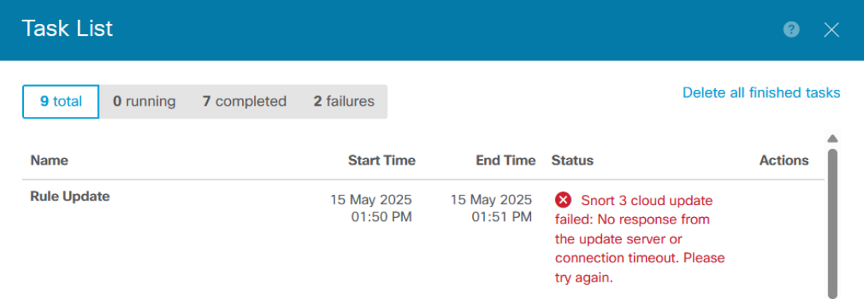
The Cisco FDM Device Summary screen will display the following error to indicate failure of the URLDB database update.
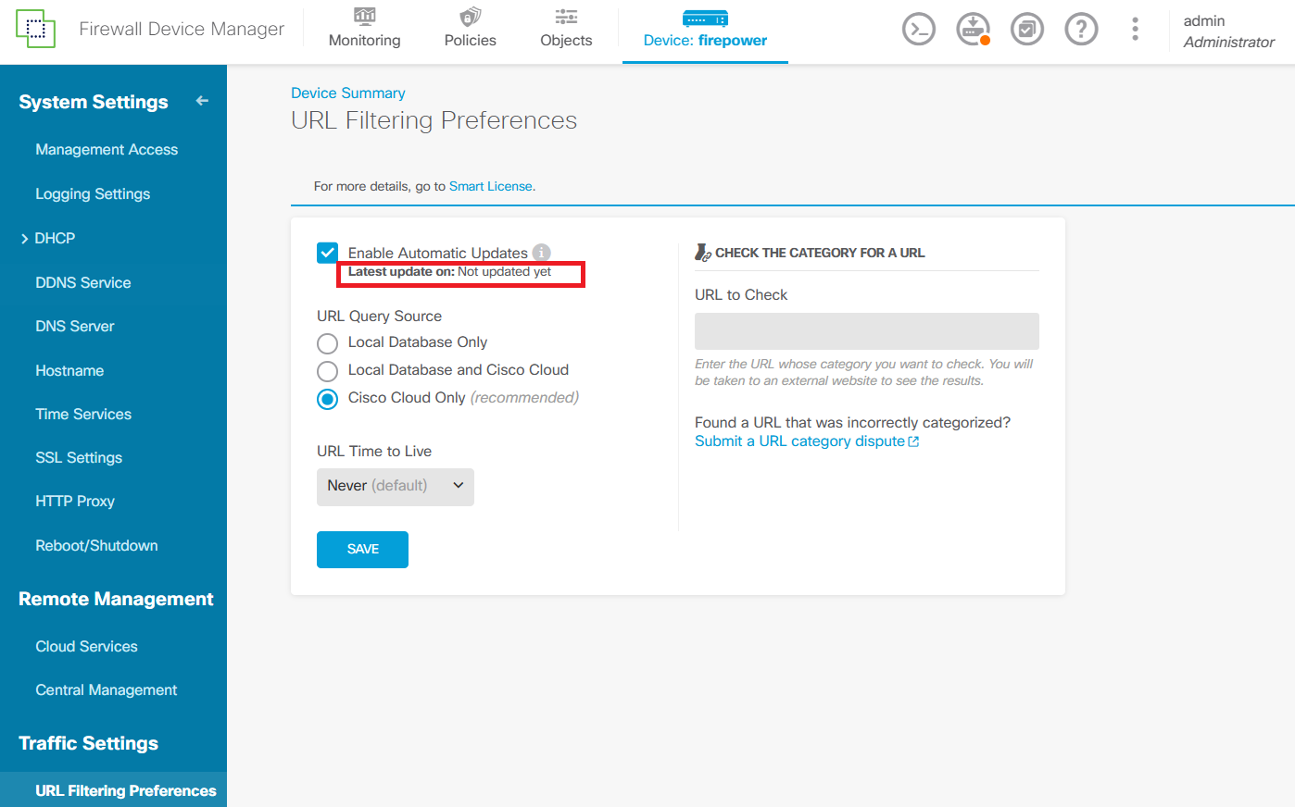
The system logs in /ngfw/var/log/messages might indicate failure to authenticate with the Cisco Talos threat intelligence service.
May 15 19:15:05 firepower-1010 SF-IMS[3940]: [61666] SFDataCorrelator:URLUserIP_CorrelatorThread_tunnelservice [ERROR] Failed to connect to tunnel (bb7d51aa-31b6-11f0-8b32-923f68cfdd03), error: Not connected
Workaround/Solution
Workaround
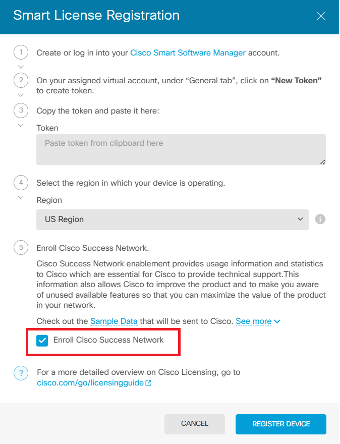
Step 1: Enable cloud connectivity for the Cisco Secure Firewall.
1. Register the device in Smart License and check the box next to Enroll Cisco Success Network (telemetry).
2. When the Smart License registration is complete, go to the Cloud Services screen and enable any of the three services.
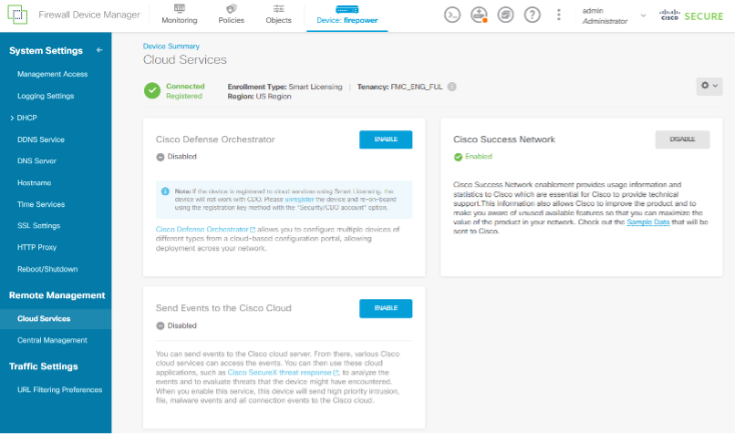
Note: If no services are enabled, the status at the top left of the screen will display "Issues - Registration Unknown".
3. If the Cisco Secure Firewall was manually unregistered from the cloud, the Cloud Services screen will have two options.
- Option A: Re-register the device in Smart Licensing and check the box next to Cisco Success Network.
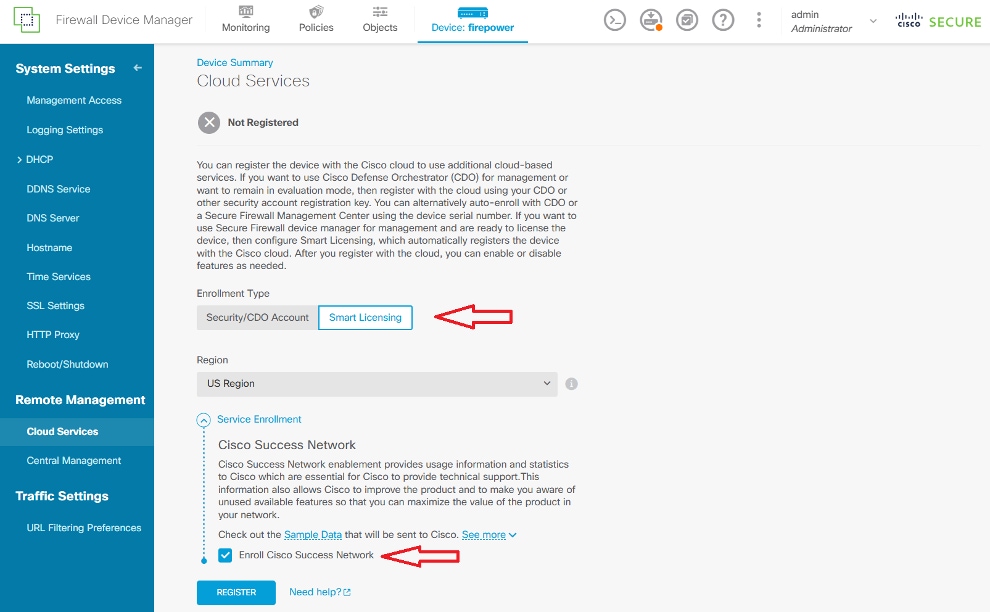
- Option B: Token onboard with Cisco Defense Orchestrator (CDO)/Security Cloud Control (SCC). This option is available only to CDO/SCC tenants that are feature flagged for Cisco Secure Firewall Device Manager support and is not available by default.
Step 2: Update the Vulnerability Database (VDB) or Geolocation Database (GeoDB). For update instructions, see the Secure Firewall Device Manager Configuration Guide for the appropriate Cisco Firepower Software release.
Go to Device > View Configuration in the Updates summary to update the VDB or the GeoDB database. Either of these updates will auto-renew the client-side certificate for cloud connectivity.
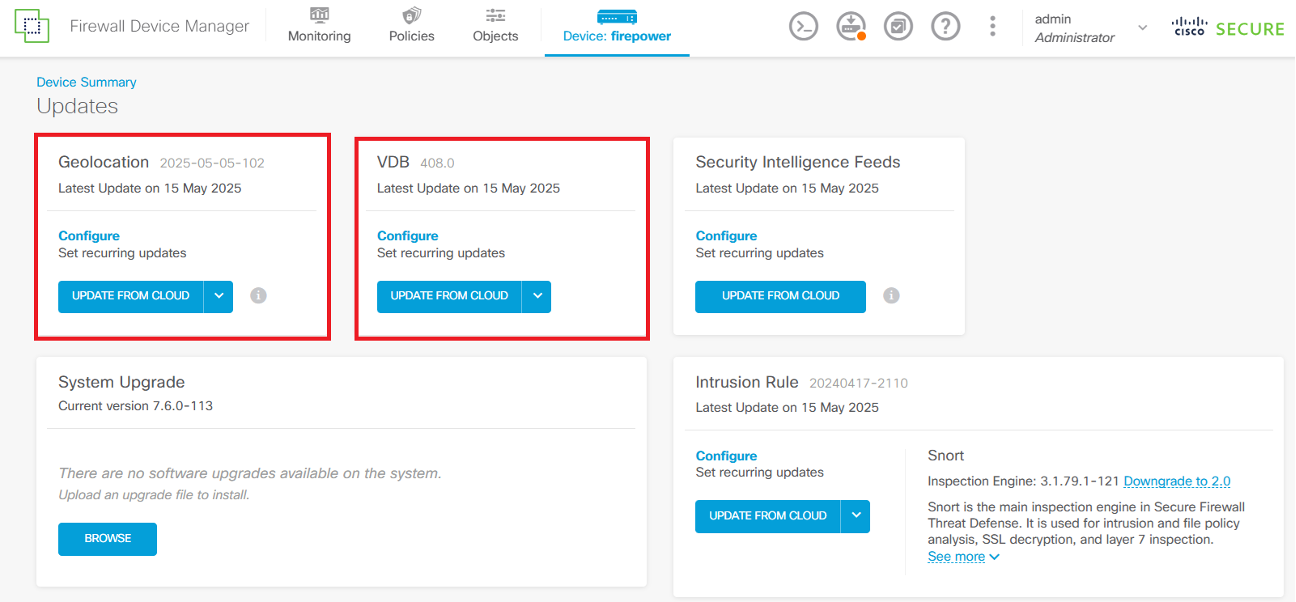
Notes:
- Establish cloud connectivity before updating the VDB or GeoDB packages.
- The new client-side certificate will expire in one year. When a new VDB or GeoDB is downloaded, the software will auto-renew the client-side certificate if it will expire within 30 days.
- After the VDB or GeoDB update is installed and the client-side certificate is renewed, the Cloud Services and device telemetry can be disabled.
Solution
Option 1: Cisco recommends upgrading to one of the Cisco Firepower Threat Defense (FTD) software releases shown in the following table to fix the Cisco Firewall Device Manager (FDM) client-side certificate issue:
| Cisco FTD Software Release | First Fixed Release |
|---|---|
| 7.6.0 | 7.6.1 |
| 7.7.0 | 7.7.10 (Planned for release Aug 2025) |
Option 2: Install Vulnerability Database version VDB406 or later to fix the client-side certificate issue. This option requires both cloud connectivity and telemetry to be enabled. For installation instructions, see the Secure Firewall Management Center Device Configuration Guide for the appropriate Cisco Firepower Software release.
Additional Information
Cisco offers a guided upgrade experience through the Cisco Secure Firewall Upgrade program. This program will provide environment-specific software upgrade guidance, a customized procedure to follow, and a customized pre-upgrade checklist. For additional information and to register for the upgrade program, see Get Access to Cisco Secure Firewall LevelUp.
Revision History
| Version | Description | Section | Date |
| 1.0 | Initial Release | — | 2025-JUN-18 |
For More Information
For further assistance or for more information about this field notice, contact the Cisco Technical Assistance Center (TAC) using one of the following methods:
Receive Email Notification About New Field Notices
To receive email updates about Field Notices (reliability and safety issues), Security Advisories (network security issues), and end-of-life announcements for specific Cisco products, set up a profile in My Notifications.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
This Document Applies to These Products
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback