This white paper outlines the Cisco strategy for the transport network that will underpin the worldwide adoption of 5G technologies and delivery of applications. Along with major technological change to the mobile core and radio access network (RAN), operators will also need to evolve their transport networks to cost-effectively deliver a satisfying mobile broadband experience, while simultaneously meeting the scale requirements for massive Internet of Things (IoT), and the ultra-low latency requirements for real-time applications.
Executive summary
Worldwide, the promise of 5G services looks to be simultaneously an evolutionary and revolutionary opportunity. Massively scalable, low-latency enabled applications will open up new ecosystems, business models, and creativity across the enterprise and residential markets in every industry.
For mobile operators, the opportunity comes from creative new business models, innovative new revenue streams, and lean operational efficiency, all directly contributing to a more profitable set of offerings and robust business. However, the evolution of the mobile operator’s network is a significant financial and engineering undertaking that must be thought through from end to end. The new network infrastructure must simultaneously satisfy exploding bandwidth demands, massive logical scale, and the incredibly low-latency needs of new applications and services in an efficient, automated, programmable manner.
In enabling these new use cases, 5G evolves existing technologies and introduces new capabilities, such as new radio (NR), a strong reliance on virtualized functions, the introduction of network slicing and Control and User Plane Separation (CUPS). These developments, in turn, will have significant impacts on the underlying network. For example, to boost capacity, the footprint of the network will need to expand significantly. To host new ultra-reliable low latency communication (uRLLC) and massive machine-type communication (mMTC) applications efficiently it will need to be able to integrate regional data centers and distributed compute seamlessly - closer to the endpoints in the network.
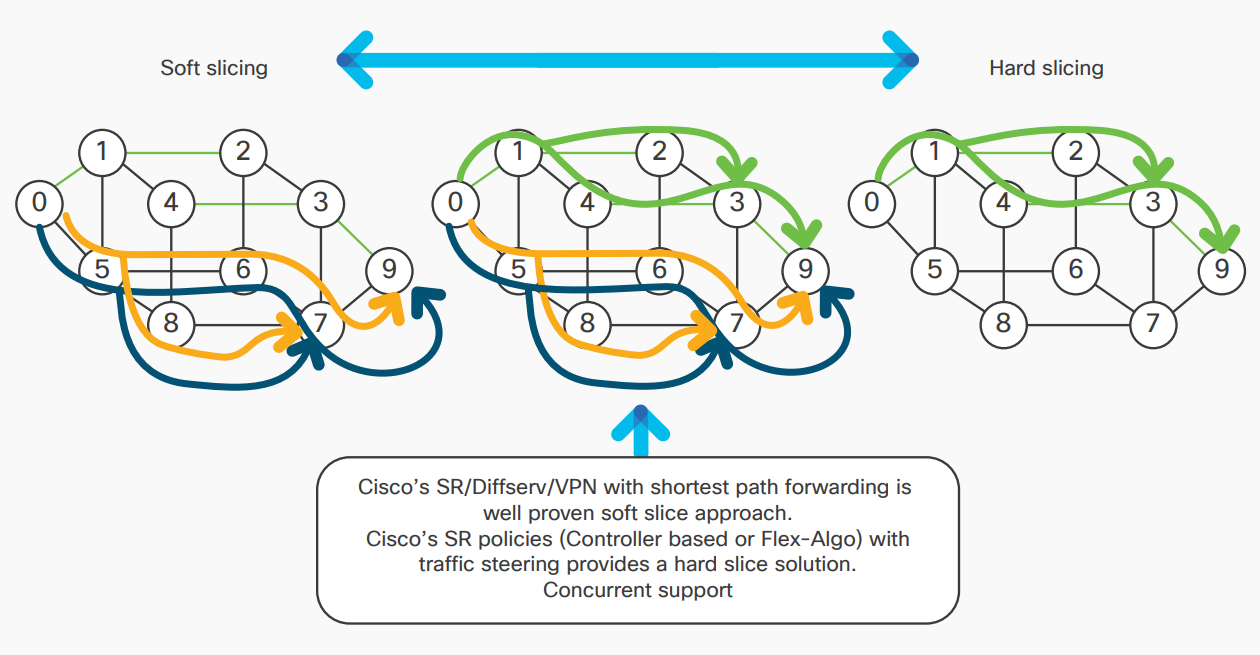
Another key attribute of the 5G transport infrastructure will be to easily carve out and reuse capacity, compute, and resiliency, and guarantee latency by supporting network slicing. Operators will have to manage the network using a completely new approach in order to enable the rapid provisioning and service automation required. In addition to the pure mobility requirements, operators must also consider how their network caters to the different classes of services they deliver, such as fixed line and broadband customers; as well as supporting the different customer types (consumer, small to medium business, and enterprise).
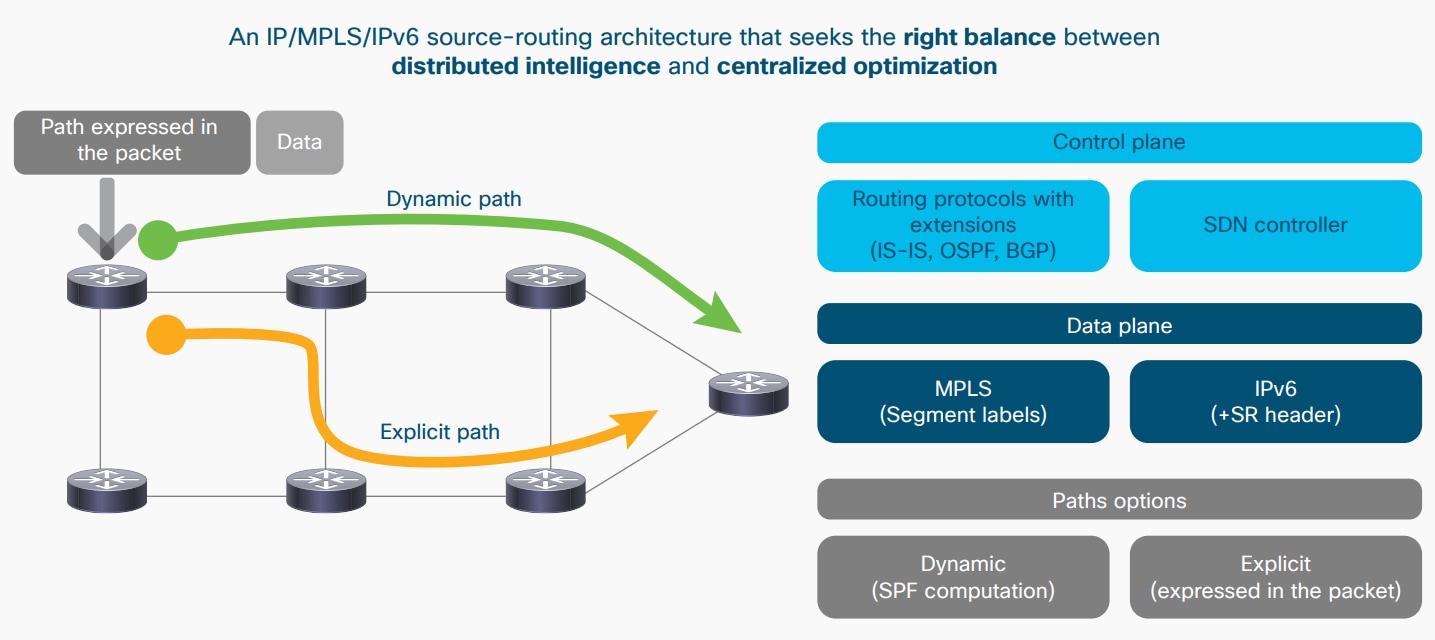
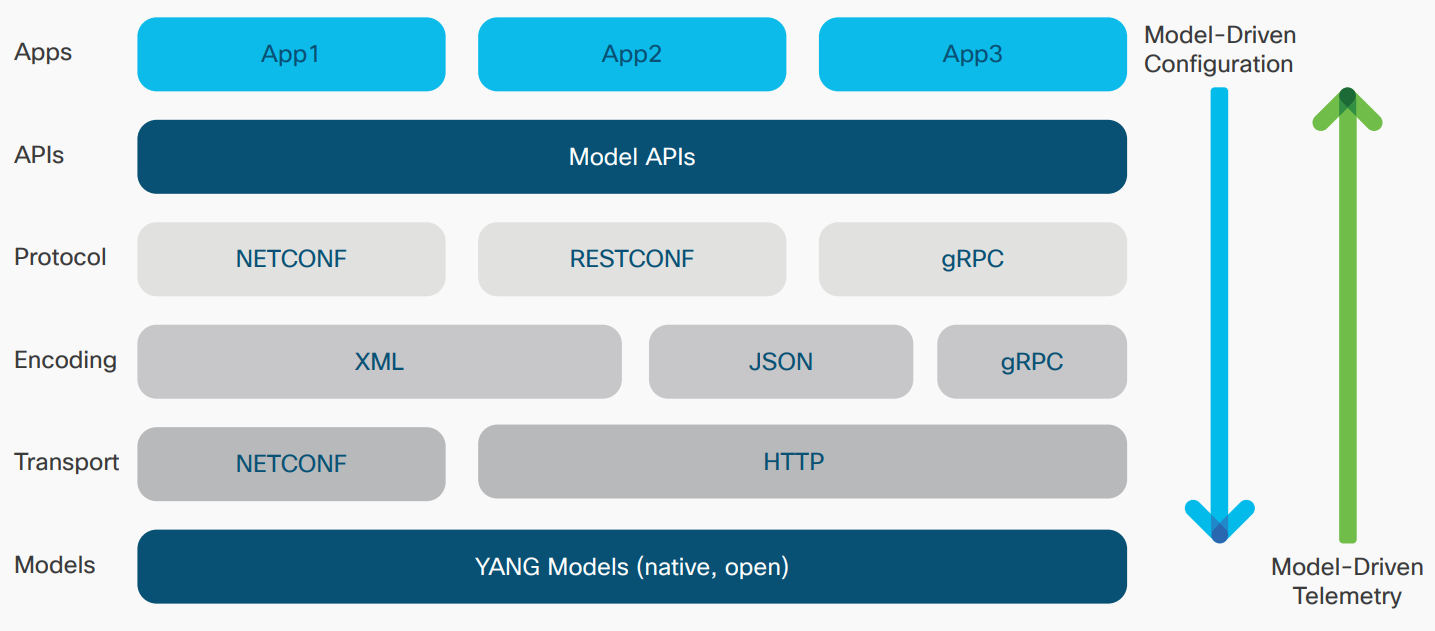
Cisco believes the most flexible and efficient transport architecture to achieve this will be based on packet technology with segment routing. Segment Routing can cost-effectively deliver this flexibility, affordability, and visibility in the transport network. It is capable of supporting consumer, enterprise, fixed, and mobile services across the transport network – all regardless of access technology.
This white paper outlines how such a converged xHaul transport network can be realized, starting with new requirements it must meet; the new technologies it needs to deploy 5G-capable services; and finally, the design features necessary to cost-effectively build and operate it.
Current transport architectures for mobile operators
Just as mobile services and technologies have evolved from circuit switched voice services to packet-technology-based data and voice services, the transport network has evolved rapidly from a purely time division multiplexing (TDM) infrastructure to a packet-based infrastructure.
Cisco has been at the forefront of this transition with our Unified Multiprotocol Label Switching (MPLS) solution, designed around standards-based packet technologies and carried over a high-capacity optical infrastructure. Globally, mobile operators have comprehensively adopted Unified MPLS, setting the standard for IP-based mobile service delivery.
There are three fundamental aims of Unified MPLS. The first is obvious; to build an infrastructure able to support the packet and TDM services needed for a 2G/3G/4G mobile network. The second is scalability, such that the architecture can support the networking requirements of the very largest operators using packet technology starting from the core all the way to the access layer of the network. The third is building a cost-effective infrastructure, so that as you move from the core toward the access, the forwarding and control plane of the network equipment can become simpler and more cost-effective.
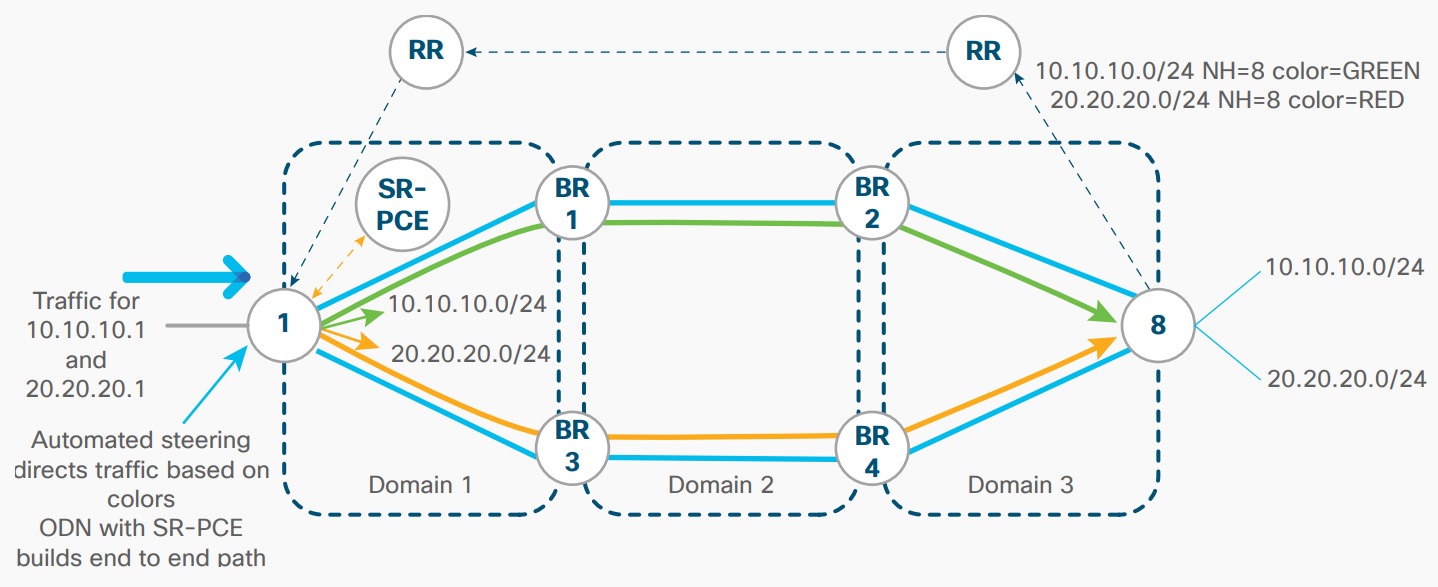
Unified MPLS relies on splitting the network into different domains and introducing a hierarchy that has an IP core domain (not to be confused with the mobile core) in the center, with aggregation and access domains surrounding it. Each domain is isolated from the others and runs its own Interior Gateway Protocol (IGP). Where inter-domain connectivity is required to deliver a service, Border Gateway Protocol (BGP) carries the appropriate inter-domain prefixes, allowing communication from end to end.
This technique has proven to be extremely successful and many 3G and 4G networks are deployed today using Unified MPLS running in the core, metro, and access networks. Currently, some mobile networks that use this architecture support in excess of 150,000 network devices.
Why do we need a new approach?
Although extremely successful and widely deployed, there are complexities to the Unified MPLS architecture when deployed in extremely large networks. These revolve around the complexity of the control plane, the number of control plane protocols, and the amount of device-level configurations required when building a service that spans many domains.
The introduction of 5G introduces additional challenges, which include:
- Footprint expansion due to the densification of the radio
- Need to incorporate the network or edge data center seamlessly into the transport network
- Use of virtualized network functions (VNF) for radio and mobile core functions
- Network slicing
- Control plane and user plane separation introduced by the CUPS architecture
These changes, plus a desire by many operators to build a single converged transport architecture for their entire customer base, reinforces the need for an end-to-end packet infrastructure that can support a wide range of layer 2 and layer 3 services.
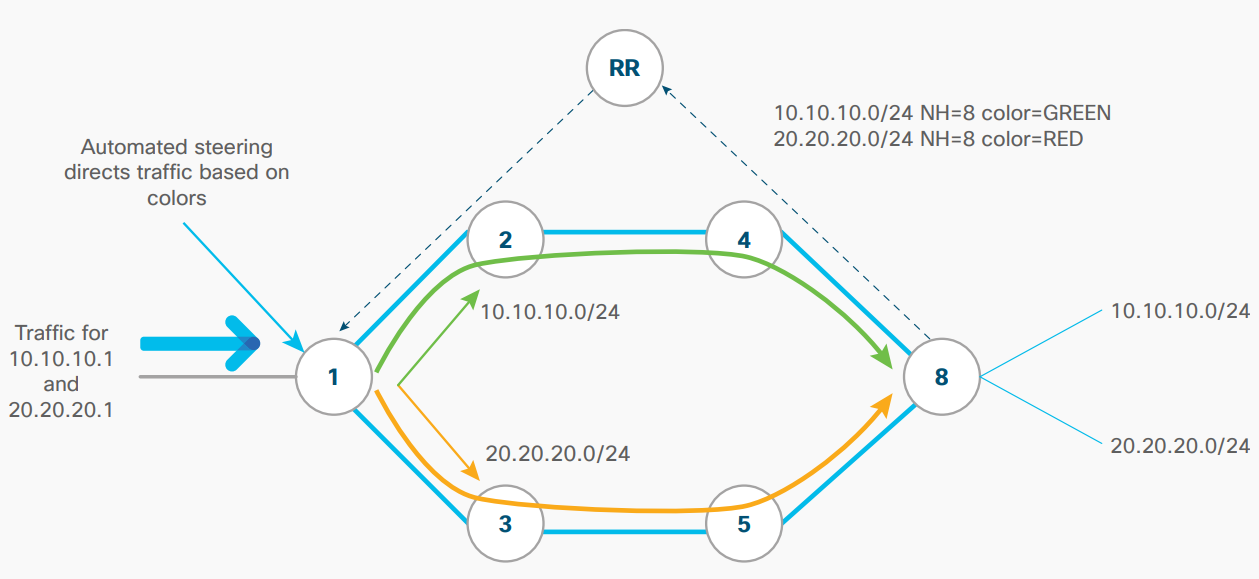
The proposed solution is to evolve the transport network’s control and data plane toward segment routing, with the option of moving toward an infrastructure orientated around software-defined networks (SDN). This approach reduces control plane protocols, such as Label Distribution Protocol (LDP) and Resource Reservation Protocol – Traffic Engineering (RSVP-TE), removes flow state from the network, and provides several options for control plane implementation. These options range from a fully distributed implementation to a hybrid approach where the router and the SDN controller divide the functionality between themselves.
This transport infrastructure is capable of overlaying a wide range of service technologies, with associated IP-based service-level agreements (SLAs), including BGP-based VPN technologies, such as EVPNs and VPNv4/v6s, and emerging SD-WAN VPN technologies.
5G network requirements
The 3GPP standards organization and 5G industry developers are specifying the main features of 5G. Figure 1 outlines the functionality already specified and to be available in upcoming 3GPP releases.
Figure 1. 5G technology evolutions