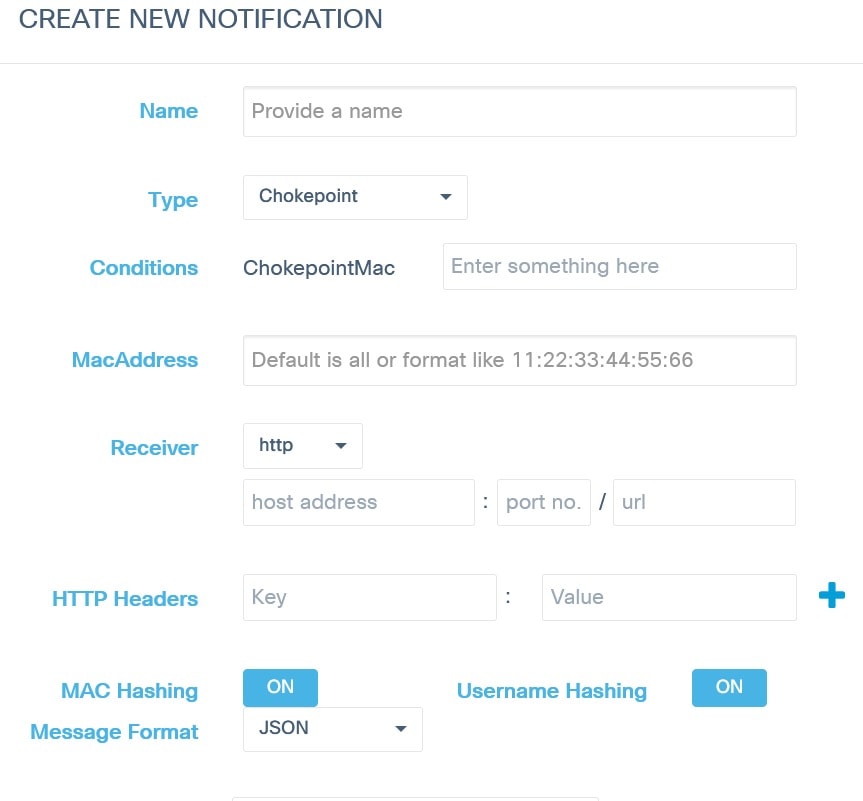
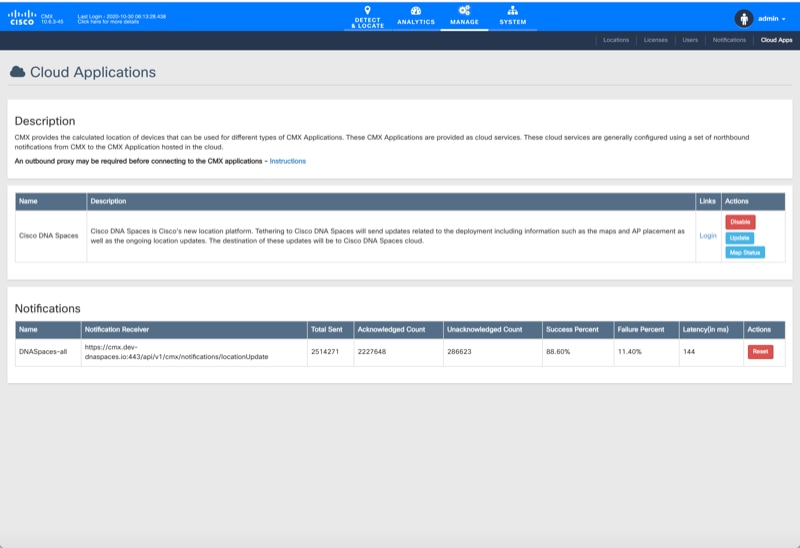
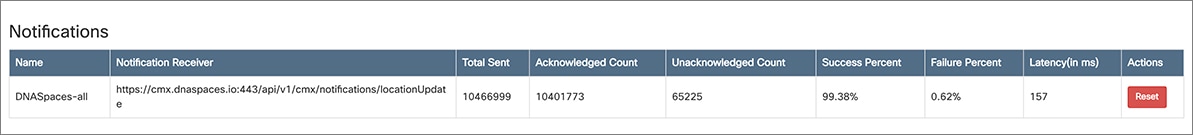
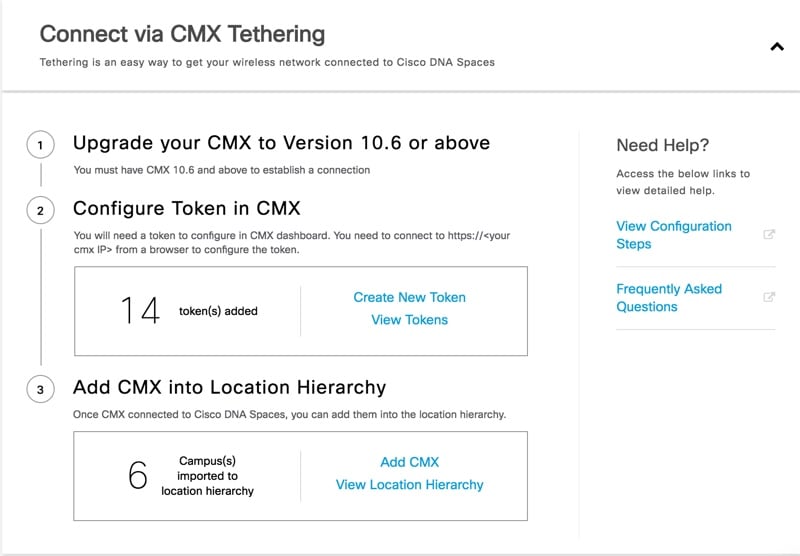
|
Notification Type
|
What type of notification this output describes (For example, locationupdate)
|
|
Subscription Name
|
The name of the notification created in CMX (user provided)
|
|
Event ID
|
Unique for notification identification per event
|
|
Location Map Hierarchy
|
The Hierarchy string that shows campus, building, floor, and zone (if applicable)
|
|
Location Coordinate
|
XY location for the device
|
|
Geo Coordinate
|
GPS location for device, if GPS markers are set
|
|
Confidence Factor
|
Represents a square box of where the client should be, lower means better location accuracy
|
|
AP Mac Address
|
The AP that the client is connected to
|
|
Associated
|
Shows if this device is associated or not
|
|
Username
|
The username of this Associated client if using 802.11x
|
|
IP address
|
If this client is associated, what IP address(es) are assigned to it, can include IPv4 and IPv6 addresses
|
Note
|
Some client devices uses Extended Unique Identifier (EUI-64) to auto-generate the IPv6 address. In this scenario, MAC address
of the device is displayed in the IPv6 address field too. When the controller sends the client data to Cisco CMX using NMSP, IPv6 address and MAC address of the device
is displayed in the northbound notification. However, Cisco CMX hashes the IPv6 address to comply with privacy regulations
as per General Data Protection Regulation (GDPR).
|
|
|
SSID
|
The SSID of the client is Associated
|
|
Band
|
802.11 band the device is it connected to
|
|
Floor Id
|
Long value representing hieracrchy, would not use
|
|
Floor Ref Id
|
New to 10.3.1, represents a long for what hierarchy it is on (Floor Id might be rounded if the number is large enough due
to a conversion from long to double), only is filled in for location update, recommended for use
|
|
Entity
|
What type of device is it, Client (normal devices), RFID Tag (these are devices that send a chirp on an interval), Interferers
(Devices that are connected to APs or are APs that aren’t on the network controlled by a controller on this CMX)
|
|
Device Id
|
MAC address of device
|
|
Last Seen
|
Timestamp of packet last received from controller for this device
|
|
Raw Location
|
-
|
|
Area Global Id List
|
-
|
|
Tag Vendor Data
|
For RFID tags, information that was encoded in packets we received like battery life or something like that.
|
|
Manufacturer
|
Based on the first half of the MAC address of this device
|
|
Timestamp
|
When the notification is generated
|
|
status
|
Refers to what the status of the device is - IDLE(0), AAA_PENDING(1), AUTHENTICATED(2),
ASSOCIATED(3), POWERSAVE(4), DISASSOCIATED(5), TO_BE_DELETED(6), PROBING(7),
BLACK_LISTED(8), WAIT_AUTHENTICATED(256), WAIT_ASSOCIATED(257);
|
|
rssiEntries
|
Displays the Access Points information used for determining the location of the device.
"rssiEntries": [
{
"apMacAddress": "6c:8b:d3:ef:d4:60",
"band": "IEEE_802_11_B",
"slot": 2,
"antennaIndex": 0,
"rssi": -55,
"lastHeardSecs": 7
},
{
"apMacAddress": "6c:8b:d3:b2:ba:60",
"band": "IEEE_802_11_B",
"slot": 2,
"antennaIndex": 0,
"rssi": -69,
"lastHeardSecs": 2
}
]
|


 Feedback
Feedback