Multi-preshared key
A multi-preshared key (multi-PSK) is a wireless security feature that
-
Allows multiple pre-shared keys (PSKs) to be configured for a single SSID
-
Enables any configured PSK to grant access to the same wireless network
-
Improves network flexibility by supporting concurrent user groups or devices with different credentials.
PSK: A pre-shared key is a password or passphrase used to authenticate clients on a wireless network.
Supporting analogy: keycards to the same door
Having multi-PSk keys for a single SSID is like giving different colored keycards to various teams. Each keycard opens the same door, but you can manage which card goes to which team. This approach increases flexibility and security compared to using one generic key.
Comparing traditional PSK with
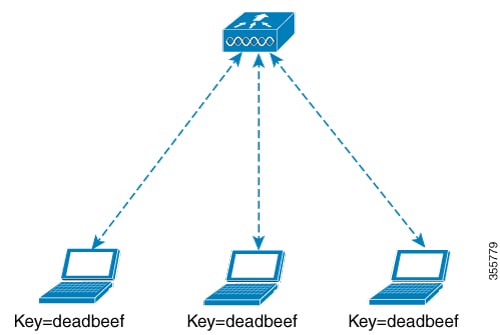
In a traditional PSK, all the clients joining the network use the same password as shown in the figure.
But with multi-PSK, client can use any of the configured pre-shared keys to connect to the network as shown in the figure.
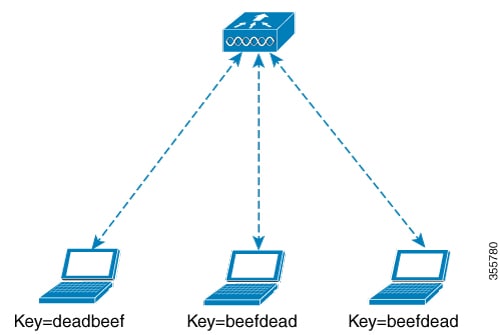
In the Multi-PSK example, two passwords—deadbeef and beefdead—are configured for the same SSIDIn this scenario, clients can connect to the network using either of the passwords.
 Note |
|
|
Feature |
Traditional PSK |
Multi-PSK |
Identity PSK (iPSK) |
|---|---|---|---|
| Number of PSKs per SSID |
One shared key |
Multiple keys (up to five) |
Unique key per user or per group |
| Use case flexibility |
All users share one credential |
Separate keys for groups or devices |
Per-user or per-group credentials for high granularity |
| Example |
All staff share same key |
Staff, guests, IoT devices have different keys |
Each staff member, contractor, or device gets its own key |
| Key management |
Single change affects all users |
Changes can target specific groups or devices |
Changes can target specific users or devices; policy-driven from ISE |
| Security granularity | Lowest — one compromise affects all |
Better — compromise isolated to that PSK group |
Highest — compromise isolated to individual user or device and fully policy-based |
 Feedback
Feedback