Information About FlexConnect Groups
To organize and manage your FlexConnect access points, you can create FlexConnect Groups and assign specific access points to them.
All of the FlexConnect APs in a group can share the same backup RADIUS server, fast secure roaming, local authentication configuration, and WLAN-VLAN mapping information. We recommend this feature if you have multiple FlexConnect APs in a remote office or on the floor of a building and you want to configure them all at once. For example, you can configure a backup RADIUS server for a FlexConnect group rather than having to configure the same server on each AP. A maximum of 100 APs is supported per FlexConnect group (other than the default FlexConnect group, which is limited only by the maximum APs supported by the controller).
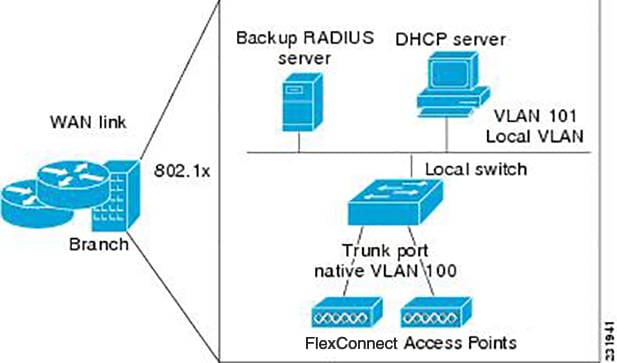
FlexConnect Groups and Backup RADIUS Servers
You can configure the controller to allow a FlexConnect access point in standalone mode to perform full 802.1X authentication to a backup RADIUS server. You can configure a primary backup RADIUS server or both a primary and secondary backup RADIUS server. These servers can be used when the FlexConnect access point is in of these two modes: standalone or connected.
FlexConnect Groups and Fast Secure Roaming
Fast secure roaming among FlexConnect APs is supported only if the APs are in non-default FlexConnect groups. For OKC, fast roaming is supported between APs in different FlexConnect groups (because key caching is handled by the controller). For 802.11r and CCKM, fast roaming is supported only among APs in the same FlexConnect group. Sticky key caching is not supported with FlexConnect APs.
 Note |
Fast roaming among FlexConnect and non-FlexConnect APs is not supported. |
 Note |
FlexConnect Groups is needed for fast roaming to work. Flex group needs to be created for fast roaming, 11r, and OKC , only then the caching can happen on an AP. The group name must be same between APs for a fast roaming to happen for 11r/fast roaming. The group can be different for OKC as final check is done at the controller. |
FlexConnect Groups and Opportunistic Key Caching
Starting with the Cisco Wireless LAN Controller Release 7.0.116.0, FlexConnect groups accelerate Opportunistic Key Caching (OKC) to enable fast roaming of clients. OKC facilitates fast roaming by using PMK caching in access points that are in the same FlexConnect group.
OKC prevents the need to perform a full authentication as the client roams from one access point to another. FlexConnect groups store the cached key on the APs of the same group, accelerating the process. However, they are not required, as OKC will still happen between access points belonging to different FlexConnect groups and will use the cached key present on the Cisco WLC, provided that Cisco WLC is reachable and APs are in connected mode.
To see the PMK cache entries at the FlexConnect access point, use the show capwap reap pmk command. This feature is supported on Cisco FlexConnect access points only. The PMK cache entries cannot be viewed on Non-FlexConnect access points.
 Note |
The FlexConnect access point must be in connected mode when the PMK is derived during WPA2/802.1x authentication. |
When using FlexConnect groups for OKC or CCKM, the PMK-cache is shared only across the access points that are part of the same FlexConnect group and are associated to the same controller. If the access points are in the same FlexConnect group but are associated to different controllers that are part of the same mobility group, the PMK cache is not updated and CCKM roaming will fail but OKC roaming will still work.
 Note |
Fast roaming works only if the APs are in the same FlexConnect group for APs in FlexConnect mode, 802.11r . |
FlexConnect Groups and Local Authentication Server
You can configure the controller to allow a Cisco Wave 1 (IOS-based) FlexConnect AP in standalone mode to perform LEAP, EAP-FAST authentication for up to 100 statically configured users. The controller sends the static list of usernames and passwords to each FlexConnect access point when it joins the controller. Each access point in the group authenticates only its own associated clients.
 Note |
This feature is not supported on Wave 2 and 802.11ax APs. |
 Note |
If you want to enable FlexConnect local authentication, you have to enable FlexConnect AP Local Authentication in the Local Authentication tab. If the FlexConnect APs act as an 802.11X authenticator (RADIUS client), then configure the RADIUS servers in the General tab. |
This feature is ideal for customers who are migrating from an autonomous access point network to a lightweight FlexConnect access point network and are not interested in maintaining a large user database or adding another hardware device to replace the RADIUS server functionality available in the autonomous access point.
 Note |
This feature can be used with the FlexConnect backup RADIUS server feature. If a FlexConnect is configured with both a backup RADIUS server and local authentication, the FlexConnect access point always attempts to authenticate clients using the primary backup RADIUS server first, followed by the secondary backup RADIUS server (if the primary is not reachable), and finally the FlexConnect access point itself (if the primary and secondary are not reachable). |
For information about the number of FlexConnect groups and access point support for a Cisco WLC model, see the data sheet of the respective Cisco WLC model.

 Feedback
Feedback