IOx on the IE 4000
Getting Started
The Industrial Ethernet (IE) 4000 Series Switch is a Cisco ruggedized switching platform. It is ideal for industrial Ethernet applications where hardened products are required, including factory automation, energy and process control, intelligent transportation systems (ITS), oil and gas field sites, city surveillance programs, and mining.
Please see the following document for more information:
Purpose and Audience
This document will guide you through the process of updating the IE 4000 software and installing the IE 4000 into the network. To enable IOx on the IE4000, the Cisco IOS IE 4000 software must be updated to a version supporting IOx. The standard installed image does not support IOx.
The audience for this document is someone that is not a networking expert, nor are they expected to be familiar with the Cisco IOS operating system.
High Level Platform Architecture
When IE 4000 is enabled with IOx, it’s running in a duel core mode with the Cisco IOS operating system running on the first core, and IOx Infrastructure and hosted applications on the second core.
IOx Infrastructure is bootstrapped by IOS at system bootup, and communicates with IOS through ICC (inter-core communication) during the bootstrap. After the bootstrap, IOS and IOx communicate over the internal Ethernet interface.
-
Networking connectivity for IOx Infrastructure and hosted applications is provided via an Internal Ethernet interface that carries multiple vlans. The VLAN ID to access IOx Infrastructure is configured using IOS CLI.
-
IOx Infrastructure and application containers have access to the 1GB removable SD flash memory card. The SD card is managed by IOS.
Northbound and Southbound Communication
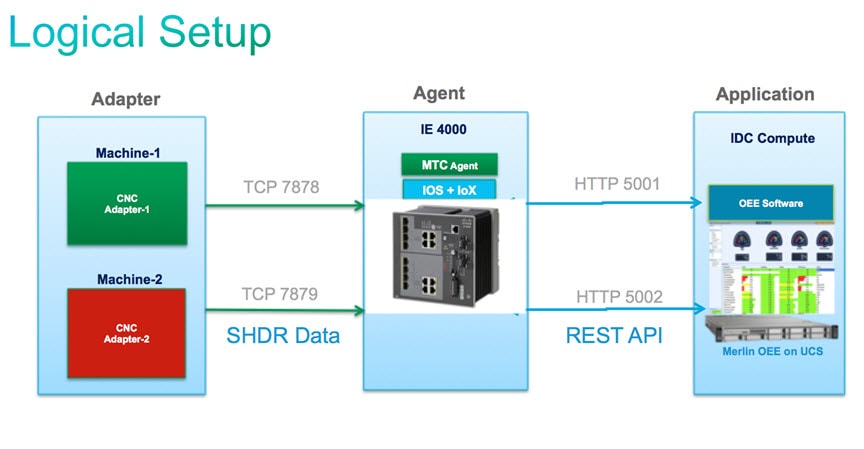
Throughout the document, the terms “Northbound” and “Southbound” are used. Let's say you have a machine and you want the data of the machine shown in the OEE app. You are using the IE 4000 enabled with IOx, which has an LXC container deployed. Let's say that the LXC container has an agent which can collect the data from the machine adapter and send it to the OEE app. The figure below is the logical setup to show the communication between machine adapter and OEE application. This is the example where the MTC agent resides on the IE 4000 within the LXC container and communicates with the MTC adapter over a TCP port (for example, 7878, 7879, etc.) defined in the agent.cfg file. As shown in the figure, it’s a one-way communication. This communication is referred to as “Southbound” communication.
Similarly, an OEE application pulls data from the MTC agent in the form of REST API over another TCP port (for example, 5001, 5002, etc.). This communication is referred to as “Northbound” communication.
 Note |
In this document, the MTConnect LXC container is used as a sample application. Networking configuration for any LXC container can be configured in a similar fashion. |
Basic Setup
Procedure
| Step 1 |
Download ie4000-universalk9_iox-tar.152-4.EB.tar image to your PC:https://software.cisco.com/download/special/release.152-4.EB |
| Step 2 |
Copy the IOx image on the switch’s sdflash: from your PC:
|
| Step 3 |
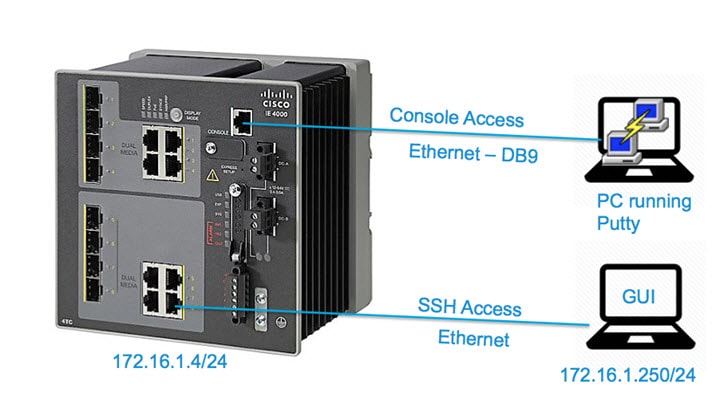
Set up the console of the switch to access the switch as shown in the following figure.
|
| Step 4 |
Make sure to have one IOS image (.bin) on local flash: or sdflash: as a backup (that is, while coping the IOx image do not overwrite the IOS image). |
| Step 5 |
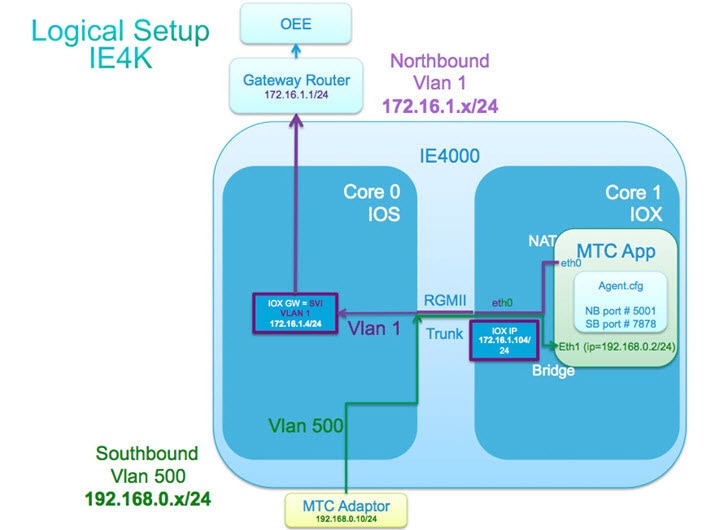
Review the network diagram and table below. What the LXC application (for example, MTConnect in this case) needs is a OEE type application running somewhere in the northbound network, and some data generation devices in the southbound network. You should be aware of how the IE 4000 is "connected" to the network as well as how IOx will connect to the network through the IE4000. |
IE 4000 CLI Based Initial Setup
This section can be done before or after the IOS software update. The configuration in this section is generic to the IE 4000 and doesn’t require a specific version of the IOS to be operational.
Procedure
| Step 1 |
After the IE 4000 switch powers up, answer "no" to the following prompt: Example: |
| Step 2 |
By default Auto boot is enabled in the switch, but if you happen to get a non-manufacturing unit, enable it manually. Example: |
| Step 3 |
Set up the Management IP of the switch (this will also be the Northbound connection): See Table 1 for more information. Example: |
| Step 4 |
1. Enable ip routing and configure a gateway of last resort (also known as the default route). By default “ip routing” is disabled on the IE 4000. Enable ip routing and configure a gateway of last resort as follows: Example: |
| Step 5 |
Configure the Ethernet interface connecting the IE 4000 to the northbound network on the correct VLAN. In the example provided it is vlan 1 and GigabitEthernet 1/1. Depending upon what type of device is on the other side of GigabitEthernet 1/1, the configuration is different. If the device is a router, follow step A. if the device is an Ethernet switch, follow step B. If you don’t know what type of device it is, follow step A. In either case, the VLAN used remains the same. |
| Step 6 |
Verify that you can ping the Gateway Router IP. Example:If the ping command does not work, then go back and check the following configurations:
|
| Step 7 |
1. Assuming the gateway router has correct routing configured and has connectivity to OEE, also try pinging your OEE IP (172.16.2.2). Example: |
| Step 8 |
Set up the console and enable SSH access. Privilege level 15 is a requirement to access the IOx Local Manager GUI. See Table 1 for more information. Example:For more information on configuring Secure Shell on routers and switches running Cisco IOS, see: http://www.cisco.com/c/en/us/support/docs/security-vpn/secure-shell-ssh/4145-ssh.html
|
| Step 9 |
Configure VTP mode transparent. Example:For more information on Spanning Tree Protocol, see: http://www.cisco.com/c/en/us/td/docs/switches/lan/cisco_ie4000/software/release/15-2_2_ea/configuration/guide/scg-ie4000/swstp.html#pgfId-1166029
|
| Step 10 |
Set up the GUI connection. Example: |
| Step 11 |
Save the configuration. Example: |
Installing an IOx Image on the IE 4000 Series Switch
Use the following procedure to install the IOx image on an IE 4000 Series Switch.
Before you begin
License Requirement: A Lanbase license is sufficient; no license upgrade is required to enable IOx.
Procedure
| Step 1 |
Copy the IOx enabled IOS image to sdflash following the regular IOS file copy procedures. While copying the iox file, do not overwrite the IOS image.
|
| Step 2 |
Untar the file on sdflash using the archive download-sw command. Example: |
| Step 3 |
Reload the switch. If the IE 4000 prompts to save the configuration, respond with "yes". Example: |
Configuring IOx
After the IOx capable IOS version is operational, Device Manager can be used for configuration as well as the CLI. In this section, both methods are shown.
Procedure
| Step 1 |
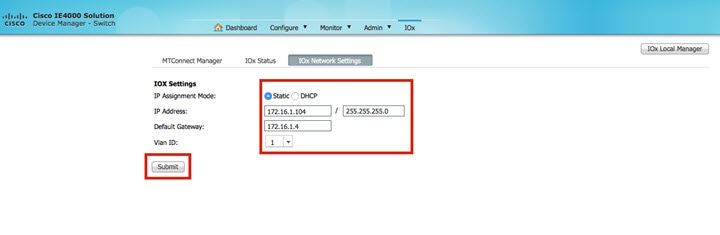
Configure IOx (Northbound IP).
Example:
|
||||||||||||||||||||
| Step 2 |
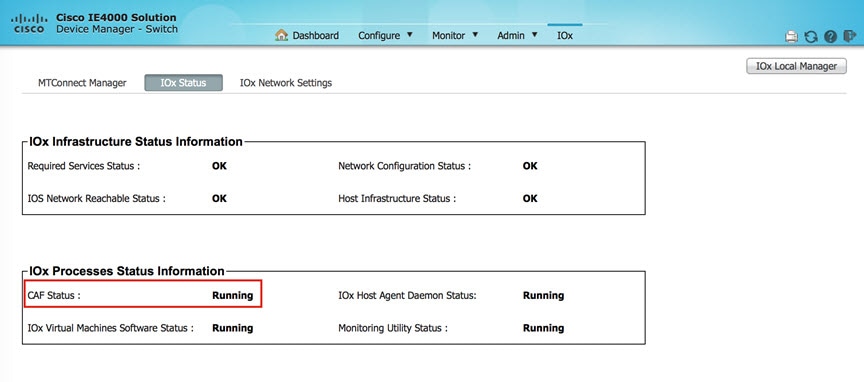
Verify CAF (Cisco Application Framework) is running in IOx. CAF is responsible for orchestrating and managing applications on Fog Node.
|
||||||||||||||||||||
| Step 3 |
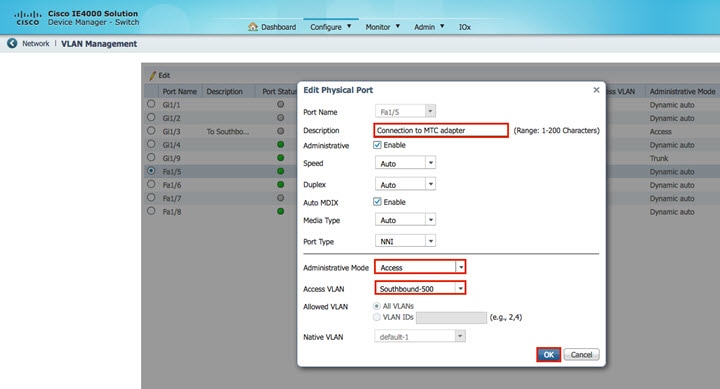
Configure Southbound network. Default is vlan 500. By default all the Ethernet interfaces on IE 4000 are members of vlan 1. If you are utilizing default vlan 500, just add the interface connected to MTC adapter in vlan 500.
|
||||||||||||||||||||
| Step 4 |
Verify IOx Southbound default IP. Example:
You can verifiy southbound IOx IP using device Manager. Go to DM (http://172.16.1.4) > IOx > MTConnect Manager > Southbound Network Settings. 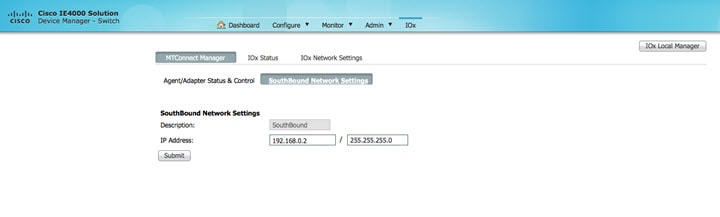 |
||||||||||||||||||||
| Step 5 |
Save the configuration.
|
||||||||||||||||||||
| Step 6 |
The IE 4000 configuration is complete, and IOx is ready to use. Proceed with configuring the LXC app using Local manager using the Cisco IOx Local Manager Reference Guide. |
||||||||||||||||||||
| Step 7 |
By configuring an OEE application with 192.168.0.0/16 network interface, it will communicate to the MTC agent using its northbound interface. |
IOx on IE 4000 Example
This is an example of a IOx configuration on an IE 4000 switch.
switch#sh running-config
Building configuration...
Current configuration : 3408 bytes
!
! Last configuration change at 22:36:34 UTC Sun Aug 14 2016 by admin
! NVRAM config last updated at 22:36:34 UTC Sun Aug 14 2016 by admin
!
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname switch
!
boot-start-marker
boot-end-marker
!
!
enable secret 5 cisco
!
username admin privilege 15 password 7 cisco
username cisco privilege 15 secret 5 cisco
no aaa new-model
system mtu routing 1500
ip routing
!
!
!
vtp mode transparent
!
!
!
!
!
ptp mode e2etransparent
!
!
crypto pki trustpoint TP-self-signed-1749792128
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1749792128
revocation-check none
rsakeypair TP-self-signed-1749792128
!
!
crypto pki certificate chain TP-self-signed-1749792128
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 31373439 37393231 3238301E 170D3136 30383131 31383239
32315A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 37343937
39323132 3830819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
81009B3C 1E4473A6 488B5EE0 731BED37 6ABBC91F 2568BA12 D3AD1BEC F3C3F285
633C1178 DE81AB3D 1D73FEF5 99B7A904 6016FB8D 8490015B 7E2B94E5 922AA725
AA5FAC23 EB721785 D4CC25FC A1358707 F99B76E2 D2725C20 98EB4776 8246398B
148A49B7 223CD493 8A22CC06 63B46B0C 48BC4A4F 7A467D9E 8D083643 470DB89F
B94D0203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 142234D6 DC71C00F 5E0DC60E DB52FCCC 44B856D0 C1301D06
03551D0E 04160414 2234D6DC 71C00F5E 0DC60EDB 52FCCC44 B856D0C1 300D0609
2A864886 F70D0101 05050003 81810020 9E4A3C93 690E1D1D 67160754 E980BB15
E0126F6E 90C34539 481F77EF 6589C2CB 91FADDAF 0DF4535E 95233E75 6382E2C1
6C839C92 0E631C7D 86942E17 0C5CCBBC EB58540B 365056E2 1AE0BD28 40E0E79D
63F55926 E2A694BB E4650572 855DAAC1 3360E9C9 A4BB4891 390E5DF6 F22A53E3
70F1DEAE 85971EBE 468080A2 671D3B
quit
!
spanning-tree mode pvst
spanning-tree extend system-id
!
alarm profile defaultPort
alarm not-operating
syslog not-operating
notifies not-operating
!
!
!
vlan internal allocation policy ascending
!
vlan 500
name Southbound
!
lldp run
!
!
!
!
!
interface GigabitEthernet1/1
!
interface GigabitEthernet1/2
!
interface GigabitEthernet1/3
!
interface GigabitEthernet1/4
!
interface GigabitEthernet1/9
!
interface FastEthernet1/5
Description Connection to MTC adapter
Switchport mode access
Switchport access vlan 500
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface Vlan1
description Northbound-Mgmt
ip address 172.16.1.4 255.255.255.0
!
!
iox
host ip address 172.16.1.104 255.255.255.0 vlan 1
host ip default-gateway 172.16.1.4
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
!
!
ip route 0.0.0.0 0.0.0.0 172.16.1.1
!!
!
privilege exec level 15 ssh
!
line con 0
exec-timeout 0 0
password 7 03070A180500701E1D
line vty 0 4
exec-timeout 0 0
password 7 15115A1F07257A767B
login local
transport preferred none
transport input ssh
line vty 5 15
exec-timeout 0 0
password 7 15115A1F07257A767B
login local
transport preferred none
transport input ssh
!
!
end
Additional References
Related Documents
|
Document |
URL |
|---|---|
| IE4000 15.2(4)EB Image download | https://software.cisco.com/download/special/release.152-4.EB |
| IE4000 IOX Release note URL | http://www.cisco.com/c/en/us/td/docs/switches/Connexa/Software/Release/15_2_4_EB_relnotes.html |
|
Cisco IOx DevNet |
https://developer.cisco.com/site/iox/ |
|
Cisco IOx DevNet Getting Started Documentation |
https://developer.cisco.com/site/iox/documents/developer-guide/?ref=quickstart |
|
IOx App developer’s guide on DevNet |
https://developer.cisco.com/site/iox/documents/developer-guide/ |
MIBs
| MIB | MIBs Link |
|---|---|
|
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Technical Assistance
| Description | Link |
|---|---|
|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
 Feedback
Feedback