Information About DHCP Relay in a BGP EVPN VXLAN Fabric
Networks use DHCP relay to forward DHCP packets between host devices and a DHCP server. In a BGP EVPN VXLAN fabric, you can configure a VTEP as a relay agent to provide DCHP relay services in a multi-tenant VXLAN environment.
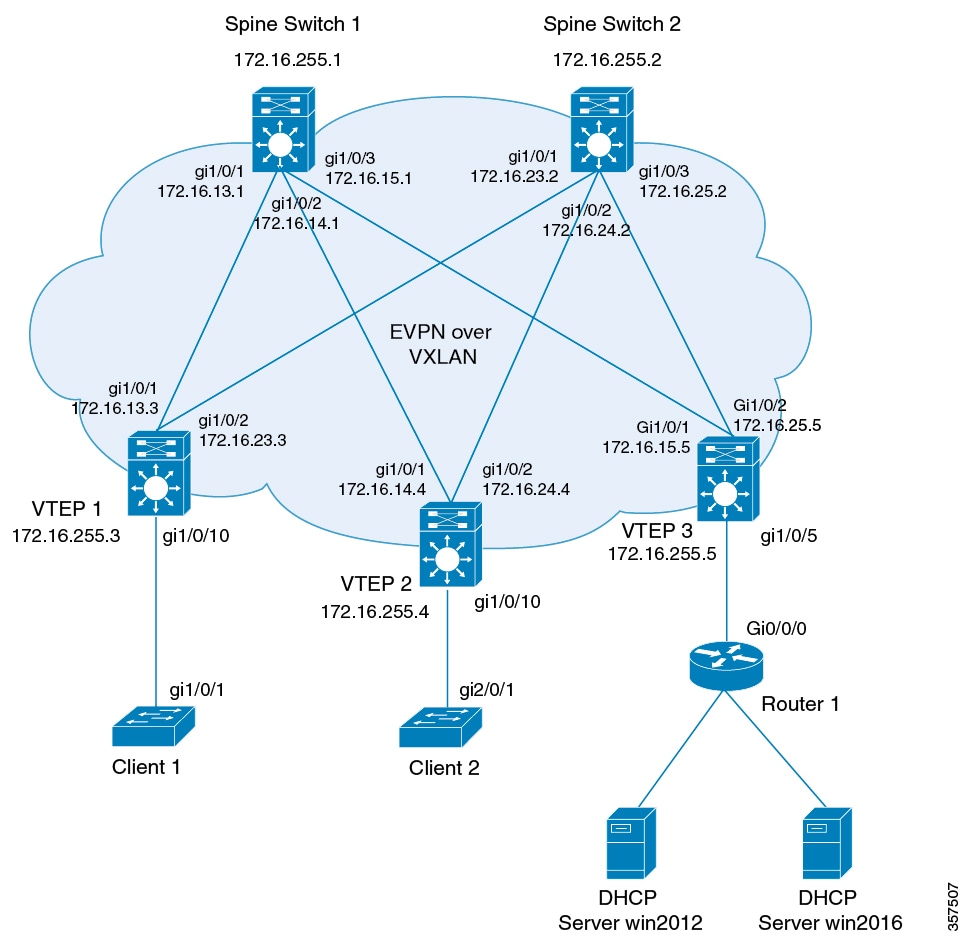
When a network uses DHCP relay, DHCP messages move through the same switch in both directions. DHCP relay generally uses the gateway IP address (GiAddr) for scope selection and DHCP response messages. In a BGP EVPN VXLAN fabric that has distributed IP anycast gateway enabled, DHCP messages can return to any switch that hosts the respective GiAddr.
Deploying DHCP relay in an EVPN VXLAN network requires a different method for scope selection and a unique IP address for each switch in the network. The unique Loopback interface for a switch becomes the GiAddr that a switch uses to respond to the correct switch. DHCP option 82, also referred to as DHCP option VPN, is used for scope selection based on the Layer 2 VNI.
In a multi-tenant EVPN environment, DHCP relay uses the following sub-options of option 82:
-
Sub-Option 151(0x97)—Virtual Subnet Selection:
The virtual subnet selection sub-option is used to convey VRF-related information to the DHCP server in an MPLS VPN and a VXLAN EVPN multi-tenant environment.
RFC 6607 provides the definition for this sub-option.
-
Sub-Option 11(0xb)—Server ID Override
The server identifier or server ID override sub-option allows the DHCP relay agent to specify a new value for the server ID option. The DHCP server inserts this new value in the reply packet. This sub-option allows the DHCP relay agent to act as the actual DHCP server. The DHCP relay agent begins to receive all the renew requests instead of the DHCP server. The server ID override sub-option contains the incoming interface IP address. The DHCP client accesses the DHCP relay agent using the incoming interface IP address. The DHCP client uses this information to send all the renew and release request packets to the DHCP relay agent. The DHCP relay agent adds all the appropriate sub-options and then forwards the renew and release request packets to the original DHCP server.
For this function, Cisco’s proprietary implementation is sub-option 152(0x98). To implement the suboption and manage the function, run the ip dhcp relay sub-option type cisco command in global configuration mode on the VTEP that acts as the DHCP relay agent.
RFC 5107 provides the definition for this sub-option.
-
Sub-Option 5(0x5)—Link Selection:
The link selection sub-option provides a mechanism to separate the subnet or link, on which the DHCP client resides, from the GiAddr. The DHCP server uses this mechanism to communicate with the DHCP relay agent. The DHCP relay agent sets the sub-option to the correct subscriber subnet. The DHCP server then uses this value to assign an IP address different from the GiAddr. The DHCP relay agent sets the GiAddr to its own IP address to ensure that it is possible to forward the DHCP messages over the network.
For this function, Cisco’s proprietary implementation is sub-option 150(0x96). To manage the function, run the ip dhcp relay sub-option type cisco command in global configuration mode on the VTEP that acts as the DHCP relay agent.
RFC 3527 provides the definition for this sub-option.
DHCP Relay on VTEPs in Distributed Anycast Gateway Deployment
DHCP relay is generally configured on the default gateway that faces the DHCP client. You can configure a VTEP as a DHCP relay agent in different ways to automate IP addressing. The configuration depends on whether the DHCP server is present in the same network, the same VRF, or a different VRF compared to the DHCP client. When the DHCP server and DHCP client are in different VRFs, traffic is forwarded across the tenant or VRF boundaries.
The following are the common DHCP relay deployment scenarios for a BGP EVPN VXLAN fabric:
-
DHCP server is in the Layer 3 default VRF and DHCP client is in the tenant VRF.
See Example: DHCP Server is in the Layer 3 Default VRF and the DHCP Client is in the Tenant VRF for a configuration example.
-
DHCP server and DHCP client are in the same tenant VRF.
See Example: DHCP Server and DHCP Client are in the Same Tenant VRF for a configuration example.
-
DHCP server and DHCP client are in different tenant VRFs.
See Example: DHCP Client and DHCP Server are in Different Tenant VRFs for a configuration example.
-
DHCP server is in a non-default non-VXLAN VRF and DHCP client is in the tenant VRF.
See Example: DHCP Server is in a non-Default, non-VXLAN VRF and DHCP Client is in the Tenant VRF for a configuration example.
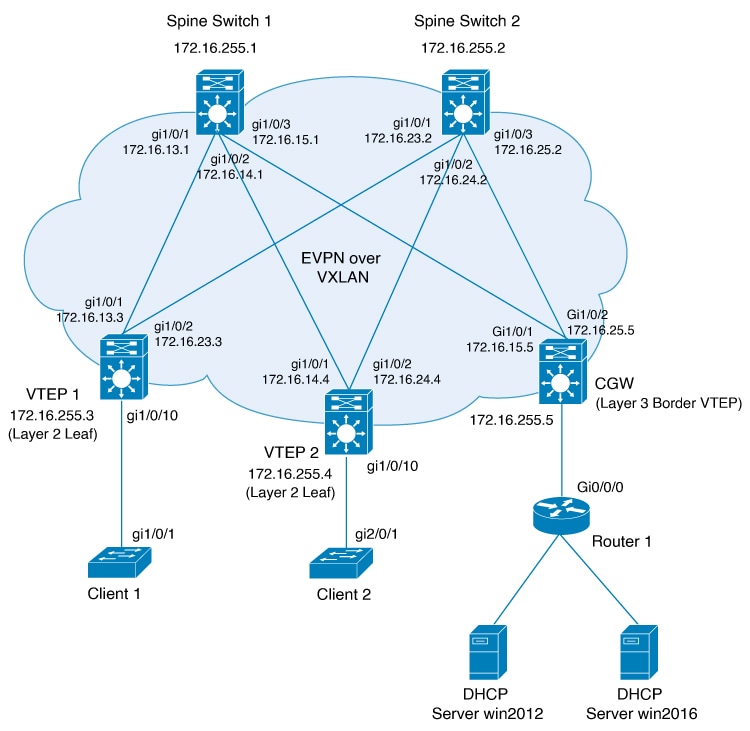
DHCP Relay on VTEPs in a Layer 2 Overlay Fabric
In an EVPN VXLAN centralized gateway (CGW) deployment, the CGW performs the Layer 3 gateway function for all the Layer 2 VNIs. All the other Leaf VTEPs in the network perform only bridging. The CGW VTEP acts as the Layer 3 gateway and performs routing for the intersubnet VXLAN traffic.
One of the VTEPs, usually a Border VTEP, is configured with an SVI to act as the Layer 3 gateway. You can also configure the Layer 3 gateway on an external router or a firewall that is connected to the Border Layer 2 VTEP, for policy enforcement and inspection of the intersubnet traffic.
DHCP follows the Discover, Offer, Request, Acknowledge (DORA) process to assign the IP addresses to the endpoints or hosts. To optimize the DORA sequence, a Layer 2 VTEP forwards the DHCP requests only to a Layer 3 VTEP. The Layer 2 VTEP uses the Gateway MAC-IP route (Route type 2 that is received with BGP gateway extended community attribute) to forward the packets to the Layer 3 gateway VTEP. The DHCP Relay on the Layer 3 gateway VTEP communicates with the DHCP server.
Starting with Cisco IOS XE 17.12.2, the following two configurations are supported.


 Feedback
Feedback