- Index
- Preface
- Product Overview
- Command-Line Interfaces
- Smart Port Macros
- Virtual Switching Systems (VSS)
- Enhanced Fast Software Upgrade (eFSU)
- Fast Software Upgrades
- Stateful Switchover (SSO)
- Non-Stop Forwarding (NSF)
- RPR Supervisor Engine Redundancy
- Layer 2 LAN Port Configuration
- Flex Links
- EtherChannels
- IEEE 802.1ak MVRP and MRP
- VLAN Trunking Protocol (VTP)
- VLANs
- Private VLANs (PVLANs)
- Private Hosts
- IEEE 802.1Q Tunneling
- Layer 2 Protocol Tunneling
- Spanning Tree Protocols (STP, MST)
- Optional STP Features
- IP Unicast Layer 3 Switching
- Policy Based Routing (PBR)
- Layer 3 Interface Configuration
- Unidirectional Ethernet (UDE) and unidirectional link routing (UDLR)
- Multiprotocol Label Switching (MPLS)
- MPLS VPN Support
- Ethernet over MPLS (EoMPLS)
- IPv4 Multicast Layer 3 Features
- IPv4 Multicast IGMP Snooping
- IPv4 PIM Snooping
- IPv4 Multicast VLAN Registration (MVR)
- IPv4 IGMP Filtering
- IPv4 Router Guard
- IPv4 Multicast VPN Support
- IPv6 Multicast Layer 3 Features
- IPv6 MLD Snooping
- Netflow
- NetFlow Data Export (NDE)
- Call Home
- System Event Archive (SEA)
- Backplane Platform Monitoring
- Local SPAN, RSPAN, and ERSPAN
- SNMP IfIndex Persistence
- Top-N Reports
- Layer 2 Traceroute Utility
- Mini Protocol Analyzer
- PFC QoS
- AutoQoS
- MPLS QoS
- PFC QoS Statistics Data Export
- Cisco IOS ACL Support
- Cisco TrustSec (CTS)
- AutoSecure
- MAC Address-Based Traffic Blocking
- Port ACLs (PACLs)
- VLAN ACLs (VACLs)
- Policy-Based Forwarding (PBF)
- Denial of Service (DoS) Protection
- Control Plane Policing (CoPP)
- Dynamic Host Configuration Protocol (DHCP) Snooping
- IP Source Guard
- Dynamic ARP Inspection (DAI)
- Traffic Storm Control
- Unknown Unicast and Multicast Flood Control
- IEEE 802.1X Port-Based Authentication
- Configuring Web-Based Authentication
- Port Security
- Lawful Intercept
- Online Diagnostic Tests
Release 15.1SY Supervisor Engine 720 Software Configuration Guide
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- May 3, 2013
Chapter: IPv4 PIM Snooping
PIM Snooping
•![]() Prerequisites for PIM Snooping
Prerequisites for PIM Snooping
•![]() Restrictions for PIM Snooping
Restrictions for PIM Snooping
•![]() Information About PIM Snooping
Information About PIM Snooping
•![]() Default Settings for PIM Snooping
Default Settings for PIM Snooping
•![]() How to Configure PIM Snooping
How to Configure PIM Snooping

Note![]() •
•![]() For complete syntax and usage information for the commands used in this chapter, see these publications:
For complete syntax and usage information for the commands used in this chapter, see these publications:
http://www.cisco.com/en/US/products/ps11846/prod_command_reference_list.html
•![]() Cisco IOS Release 15.1SY supports only Ethernet interfaces. Cisco IOS Release 15.1SY does not support any WAN features or commands.
Cisco IOS Release 15.1SY supports only Ethernet interfaces. Cisco IOS Release 15.1SY does not support any WAN features or commands.

Tip ![]() For additional information about Cisco Catalyst 6500 Series Switches (including configuration examples and troubleshooting information), see the documents listed on this page:
For additional information about Cisco Catalyst 6500 Series Switches (including configuration examples and troubleshooting information), see the documents listed on this page:
http://www.cisco.com/en/US/products/hw/switches/ps708/tsd_products_support_series_home.html
Participate in the Technical Documentation Ideas forum
Prerequisites for PIM Snooping
None.
Restrictions for PIM Snooping
•![]() Multicast packets are not bridged in a VLAN to local receivers that send IGMP joins when PIM snooping is enabled in the VLAN and IGMP snooping is disabled in the VLAN. (CSCta03980)
Multicast packets are not bridged in a VLAN to local receivers that send IGMP joins when PIM snooping is enabled in the VLAN and IGMP snooping is disabled in the VLAN. (CSCta03980)
•![]() When you use the PIM-sparse mode (PIM-SM) feature, downstream routers only see traffic if they previously indicated interest through a PIM join or prune message. An upstream router only sees traffic if it was used as an upstream router during the PIM join or prune process.
When you use the PIM-sparse mode (PIM-SM) feature, downstream routers only see traffic if they previously indicated interest through a PIM join or prune message. An upstream router only sees traffic if it was used as an upstream router during the PIM join or prune process.
•![]() Join or prune messages are not flooded on all router ports but are sent only to the port corresponding to the upstream router mentioned in the payload of the join or prune message.
Join or prune messages are not flooded on all router ports but are sent only to the port corresponding to the upstream router mentioned in the payload of the join or prune message.
•![]() Directly connected sources are supported for bidirectional PIM groups. Traffic from directly connected sources is forwarded to the designated router and designated forwarder for a VLAN. In some cases, a nondesignated router (NDR) can receive a downstream (S, G) join. For source-only networks, the initial unknown traffic is flooded only to the designated routers and designated forwarders.
Directly connected sources are supported for bidirectional PIM groups. Traffic from directly connected sources is forwarded to the designated router and designated forwarder for a VLAN. In some cases, a nondesignated router (NDR) can receive a downstream (S, G) join. For source-only networks, the initial unknown traffic is flooded only to the designated routers and designated forwarders.
•![]() Dense group mode traffic is seen as unknown traffic and is dropped.
Dense group mode traffic is seen as unknown traffic and is dropped.
•![]() The AUTO-RP groups (224.0.1.39 and 224.0.1.40) are always flooded.
The AUTO-RP groups (224.0.1.39 and 224.0.1.40) are always flooded.
•![]() The switch snoops on designated forwarder election and maintains a list of all designated forwarder routers for various RPs for the VLAN. All traffic is sent to all designated forwarders which ensures that bidirectional functionality works properly.
The switch snoops on designated forwarder election and maintains a list of all designated forwarder routers for various RPs for the VLAN. All traffic is sent to all designated forwarders which ensures that bidirectional functionality works properly.
•![]() PIM snooping and IGMP snooping can be enabled at the same time in a VLAN. Either RGMP or PIM snooping can be enabled in a VLAN but not both.
PIM snooping and IGMP snooping can be enabled at the same time in a VLAN. Either RGMP or PIM snooping can be enabled in a VLAN but not both.
•![]() Any non-PIMv2 multicast router will receive all traffic.
Any non-PIMv2 multicast router will receive all traffic.
•![]() You can enable or disable PIM snooping on a per-VLAN basis.
You can enable or disable PIM snooping on a per-VLAN basis.
•![]() All mroute and router information is timed out based on the hold-time indicated in the PIM hello and join/prune control packets. All mroute state and neighbor information is maintained per VLAN.
All mroute and router information is timed out based on the hold-time indicated in the PIM hello and join/prune control packets. All mroute state and neighbor information is maintained per VLAN.
Information About PIM Snooping
In networks where a Layer 2 switch interconnects several routers, such as an Internet exchange point (IXP), the switch floods IP multicast packets on all multicast router ports by default, even if there are no multicast receivers downstream. With PIM snooping enabled, the switch restricts multicast packets for each IP multicast group to only those multicast router ports that have downstream receivers joined to that group. When you enable PIM snooping, the switch learns which multicast router ports need to receive the multicast traffic within a specific VLAN by listening to the PIM hello messages, PIM join and prune messages, and bidirectional PIM designated forwarder-election messages.

Note ![]() To use PIM snooping, you must enable IGMP snooping on the switch. IGMP snooping restricts multicast traffic that exits through the LAN ports to which hosts are connected. IGMP snooping does not restrict traffic that exits through the LAN ports to which one or more multicast routers are connected.
To use PIM snooping, you must enable IGMP snooping on the switch. IGMP snooping restricts multicast traffic that exits through the LAN ports to which hosts are connected. IGMP snooping does not restrict traffic that exits through the LAN ports to which one or more multicast routers are connected.
The following illustrations show the flow of traffic and flooding that results in networks without PIM snooping enabled and the flow of traffic and traffic restriction when PIM snooping is enabled.
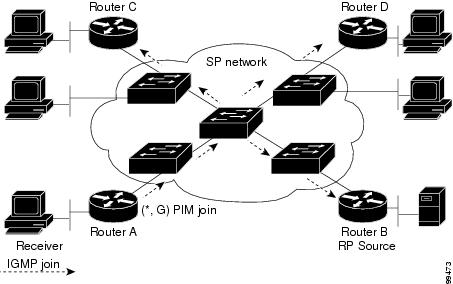
Figure 41-1 shows the flow of a PIM join message without PIM snooping enabled. In the figure, the switches flood the PIM join message intended for Router B to all connected routers.
Figure 41-1 PIM Join Message Flow without PIM Snooping
\
Figure 41-2 shows the flow of a PIM join message with PIM snooping enabled. In the figure, the switches restrict the PIM join message and forward it only to the router that needs to receive it (Router B).
Figure 41-2 PIM Join Message Flow with PIM Snooping
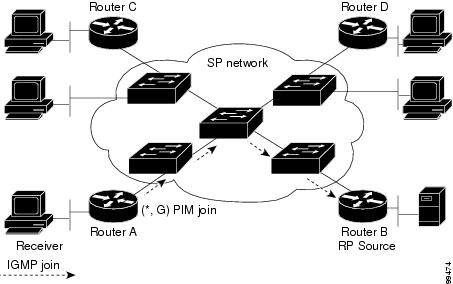
Figure 41-3 shows the flow of data traffic without PIM snooping enabled. In the figure, the switches flood the data traffic intended for Router A to all connected routers.
Figure 41-3 Data Traffic Flow without PIM Snooping
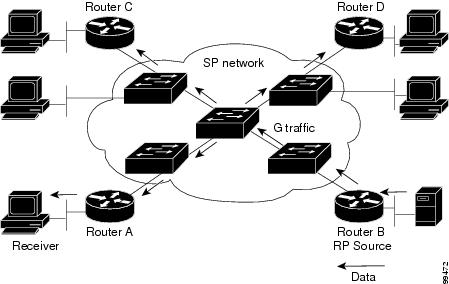
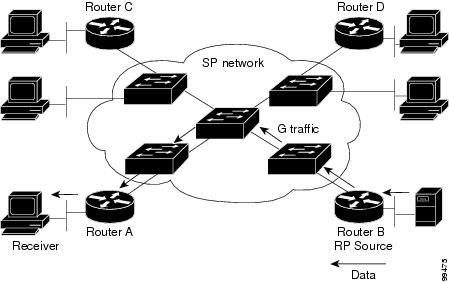
Figure 41-4 shows the flow of data traffic with PIM snooping enabled. In the figure, the switches forward the data traffic only to the router that needs to receive it (Router A).
Figure 41-4 Data Traffic Flow with PIM Snooping
Default Settings for PIM Snooping
PIM snooping is disabled by default.
How to Configure PIM Snooping
•![]() Enabling PIM Snooping Globally
Enabling PIM Snooping Globally
•![]() Enabling PIM Snooping in a VLAN
Enabling PIM Snooping in a VLAN
•![]() Disabling PIM Snooping Designated-Router Flooding
Disabling PIM Snooping Designated-Router Flooding
Enabling PIM Snooping Globally
To enable PIM snooping globally, perform this task:
|
|
|
|
|---|---|---|
Step 1 |
Router(config)# ip pim snooping |
Enables PIM snooping. |
Step 2 |
Router(config)# end |
Exits configuration mode. |
This example shows how to enable PIM snooping globally and verify the configuration:
Router(config)# ip pim snooping
Router(config)# end
Router# show ip pim snooping
Global runtime mode: Enabled
Global admin mode : Enabled
Number of user enabled VLANs: 1
User enabled VLANs: 10
Router#

Note ![]() You do not need to configure an IP address or IP PIM in order to run PIM snooping.
You do not need to configure an IP address or IP PIM in order to run PIM snooping.
Enabling PIM Snooping in a VLAN
To enable PIM snooping in a VLAN, perform this task:
This example shows how to enable PIM snooping on VLAN 10 and verify the configuration:
Router# interface vlan 10
Router(config-if)# ip pim snooping
Router(config-if)# end
Router# show ip pim snooping vlan 10
3 neighbors (0 DR priority incapable, 0 Bi-dir incapable)
6 mroutes, 3 mac entries
DR is 10.10.10.4
RP DF Set
Router#
Disabling PIM Snooping Designated-Router Flooding

Note ![]() Do not disable designated-router flooding on switches in a Layer 2 broadcast domain that supports multicast sources.
Do not disable designated-router flooding on switches in a Layer 2 broadcast domain that supports multicast sources.
By default, switches that have PIM snooping enabled will flood multicast traffic to the designated router (DR). This method of operation can send unnecessary multicast packets to the designated router. The network must carry the unnecessary traffic, and the designated router must process and drop the unnecessary traffic.
To reduce the traffic sent over the network to the designated router, disable designated-router flooding. With designated-router flooding disabled, PIM snooping only passes to the designated-router traffic that is in multicast groups for which PIM snooping receives an explicit join from the link towards the designated router.
To disable PIM snooping designated-router flooding, perform this task:
|
|
|
|
|---|---|---|
Step 1 |
Router(config)# no ip pim snooping dr-flood |
Disables PIM snooping designated-router flooding. |
Step 2 |
Router(config)# end |
Exits configuration mode. |
This example shows how to disable PIM snooping designated-router flooding:
Router(config)# no ip pim snooping dr-flood
Router(config)# end

Tip ![]() For additional information about Cisco Catalyst 6500 Series Switches (including configuration examples and troubleshooting information), see the documents listed on this page:
For additional information about Cisco Catalyst 6500 Series Switches (including configuration examples and troubleshooting information), see the documents listed on this page:
http://www.cisco.com/en/US/products/hw/switches/ps708/tsd_products_support_series_home.html
Participate in the Technical Documentation Ideas forum
 Feedback
Feedback