Flexible NetFlow Configuration Guide, Cisco IOS Release 15.2(2)E (Catalyst 3750-X and 3560-X Switches)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- June 30, 2014
Chapter: Configuring Flexible NetFlow
Configuring Flexible NetFlow
- Finding Feature Information
- Prerequisites for Flexible NetFlow
- Restrictions for Flexible NetFlow
- Information About Flexible Netflow
- How to Configure Flexible NetFlow
- Monitoring Flexible NetFlow
- Configuration Examples for Flexible NetFlow
- Additional References
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Flexible NetFlow
-
You are familiar with the Flexible NetFlow key fields as they are defined in the following commands in the Cisco IOS Flexible NetFlow Command Reference : -
You are familiar with the Flexible NetFlow nonkey fields as they are defined in the following commands in the Cisco IOS Flexible NetFlow Command Reference : - collect counter
- collect flow
- collect interface
- collect{ipv4 | ipv6}
- collect routing
- collect timestamp sys-uptime
- collect transport
-
The networking device must be running a Cisco release that supports Flexible NetFlow.
IPv4 Traffic
-
The networking device must be configured for IPv4 routing.
-
One of the following must be enabled on your router and on any interfaces on which you want to enable Flexible NetFlow: Cisco Express Forwarding or distributed Cisco Express Forwarding.
IPv6 Traffic
-
The networking device must be configured for IPv6 routing.
-
One of the following must be enabled on your router and on any interfaces on which you want to enable Flexible NetFlow: Cisco Express Forwarding IPv6 or distributed Cisco Express Forwarding.
Restrictions for Flexible NetFlow
The following are restrictions for Flexible NetFlow:
-
This feature is not supported on switches running the NPE or the LAN base image.
-
Not all of the Flexible NetFlow commands in the command reference are available on the switch. Unsupported commands are either not visible or generate an error message if entered.
-
Predefined flow records are not supported.
-
InterSwitch Link (ISL) is not supported.
-
Policy-based NetFlow is not supported.
-
Cisco TrustSec monitoring is not supported.
-
Flexible NetFlow version 5 export format is not supported, only NetFlow version 9 export format is supported.
-
Microflow policing feature shares the NetFlow hardware resource with FNF.
-
Although other modules that can be installed (switch the has 1-Gigabit and 10-Gigabit uplink interfaces), NetFlow is supported only on the network services module. Only one flow monitor per interface and per direction is supported by the network services module.
-
The switch supports up to 16 flow monitors.
Information About Flexible Netflow
Flexible NetFlow Overview
Flexible NetFlow uses flows to provide statistics for accounting, network monitoring, and network planning.
A flow is a unidirectional stream of packets that arrives on a source interface and has the same values for the keys. A key is an identified value for a field within the packet. You create a flow using a flow record to define the unique keys for your flow.
The switch supports the Flexible NetFlow feature that enables enhanced network anomalies and security detection. Flexible NetFlow allows you to define an optimal flow record for a particular application by selecting the keys from a large collection of predefined fields.
All key values must match for the packet to count in a given flow. A flow might gather other fields of interest, depending on the export record version that you configure. Flows are stored in the Flexible NetFlow cache.
You can export the data that Flexible NetFlow gathers for your flow by using an exporter and export this data to a remote system such as a Flexible NetFlow collector. The Flexible NetFlow collector can use an IPv4 address.
You define the size of the data that you want to collect for a flow using a monitor. The monitor combines the flow record and exporter with the Flexible NetFlow cache information.
Benefits of Flexible NetFlow
Flexible NetFlow allows the flow to be user defined. The benefits of Flexible NetFlow include:
-
High-capacity flow recognition, including scalability and aggregation of flow information.
-
Enhanced flow infrastructure for security monitoring and dDoS detection and identification.
-
New information from packets to adapt flow information to a particular service or operation in the network. The flow information available will be customizable by Flexible NetFlow users.
-
Extensive use of Cisco’s flexible and extensible NetFlow Version 9.
-
A comprehensive IP accounting feature that can be used to replace many accounting features, such as IP accounting, Border Gateway Protocol (BGP) Policy Accounting, and persistent caches.
-
Support for ingress and egress NetFlow accounting.
-
Support for full flow accounting and sampled NetFlow accounting.
Flexible NetFlow allows you to understand network behavior with more efficiency, with specific flow information tailored for various services used in the network. The following are some example applications for a Flexible NetFlow feature:
-
Flexible NetFlow enhances Cisco NetFlow as a security monitoring tool. For instance, new flow keys can be defined for packet length or MAC address, allowing users to search for a specific type of attack in the network.
-
Flexible NetFlow allows you to quickly identify how much application traffic is being sent between hosts by specifically tracking TCP or UDP applications by the class of service (CoS) in the packets.
-
The accounting of traffic entering a Multiprotocol Label Switching (MPLS) or IP core network and its destination for each next hop per class of service. This capability allows the building of an edge-to-edge traffic matrix.
The figure below is an example of how Flexible NetFlow might be deployed in a network.

Flexible NetFlow Components
Flexible NetFlow consists of components that can be used together in several variations to perform traffic analysis and data export. The user-defined flow records and the component structure of Flexible NetFlow facilitates the creation of various configurations for traffic analysis and data export on a networking device with a minimum number of configuration commands. Each flow monitor can have a unique combination of flow record, flow exporter, and cache type. If you change a parameter such as the destination IP address for a flow exporter, it is automatically changed for all the flow monitors that use the flow exporter. The same flow monitor can be used in conjunction with different flow samplers to sample the same type of network traffic at different rates on different interfaces. The following sections provide more information on Flexible NetFlow components:
Flow Records
In Flexible NetFlow a combination of key and nonkey fields is called a record. Flexible NetFlow records are assigned to Flexible NetFlow flow monitors to define the cache that is used for storing flow data.
A flow record defines the keys that Flexible NetFlow uses to identify packets in the flow, as well as other nonkey fields of interest that Flexible NetFlow gathers for the flow. You can define a flow record with any combination of keys and fields of interest. The switch supports a rich set of keys. A flow record also defines the types of counters gathered per flow. You can configure 64-bit packet or byte counters. The switch enables the following match fields as the defaults when you create a flow record:
User-Defined Records
Flexible NetFlow enables you to define your own records for a Flexible NetFlow flow monitor cache by specifying the key and nonkey fields to customize the data collection to your specific requirements. When you define your own records for a Flexible NetFlow flow monitor cache, they are referred to as user-defined records. The values in nonkey fields are added to flows to provide additional information about the traffic in the flows. A change in the value of a nonkey field does not create a new flow. In most cases the values for nonkey fields are taken from only the first packet in the flow. Flexible NetFlow enables you to capture counter values such as the number of bytes and packets in a flow as nonkey fields.
Flexible NetFlow adds a new Version 9 export format field type for the header and packet section types. Flexible NetFlow will communicate to the NetFlow collector the configured section sizes in the corresponding Version 9 export template fields. The payload sections will have a corresponding length field that can be used to collect the actual size of the collected section.
Flow Exporters
Flow exporters export the data in the flow monitor cache to a remote system, such as a server running NetFlow collector, for analysis and storage. Flow exporters are created as separate entities in the configuration. Flow exporters are assigned to flow monitors to provide data export capability for the flow monitors. You can create several flow exporters and assign them to one or more flow monitors to provide several export destinations. You can create one flow exporter and apply it to several flow monitors.
NetFlow Data Export Format Version 9
The basic output of NetFlow is a flow record. Several different formats for flow records have evolved as NetFlow has matured. The most recent evolution of the NetFlow export format is known as Version 9. The distinguishing feature of the NetFlow Version 9 export format is that it is template-based. Templates provide an extensible design to the record format, a feature that should allow future enhancements to NetFlow services without requiring concurrent changes to the basic flow-record format. Using templates provides several key benefits:
-
Third-party business partners who produce applications that provide collector or display services for NetFlow do not have to recompile their applications each time a new NetFlow feature is added. Instead, they should be able to use an external data file that documents the known template formats.
-
New features can be added to NetFlow quickly without breaking current implementations.
-
NetFlow is “future-proofed” against new or developing protocols because the Version 9 format can be adapted to provide support for them.
The Version 9 export format consists of a packet header followed by one or more template flow or data flow sets. A template flow set provides a description of the fields that will be present in future data flow sets. These data flow sets may occur later within the same export packet or in subsequent export packets. Template flow and data flow sets can be intermingled within a single export packet, as illustrated in the figure below.
NetFlow Version 9 will periodically export the template data so the NetFlow collector will understand what data is to be sent and also export the data flow set for the template. The key advantage to Flexible NetFlow is that the user configures a flow record, which is effectively converted to a Version 9 template and then forwarded to the collector. The figure below is a detailed example of the NetFlow Version 9 export format, including the header, template flow, and data flow sets.
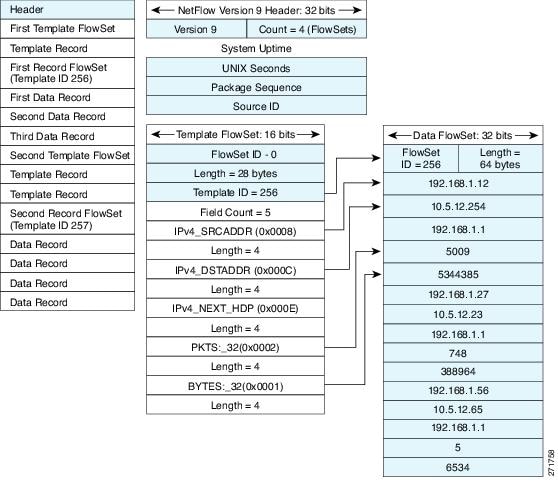
For more information on the Version 9 export format, refer to the white paper titled Cisco IOS NetFlow Version 9 Flow-Record Format, available at this URL: http://www.cisco.com/en/US/tech/tk648/tk362/technologies_white_paper09186a00800a3db9.shtml.
Flow Monitors
Flow monitors are the Flexible NetFlow component that is applied to interfaces to perform network traffic monitoring.
Flow monitors consist of a user-defined record, an optional flow exporter, and a cache that is automatically created at the time the flow monitor is applied to the first interface.
Flow data is collected from the network traffic and added to the flow monitor cache during the monitoring process based on the key and nonkey fields in the flow record.
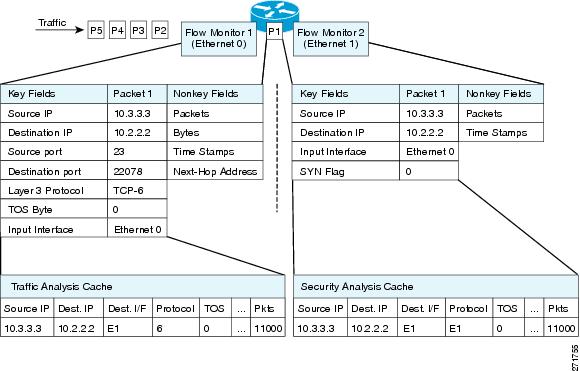
Flexible NetFlow can be used to perform different types of analysis on the same traffic. In the figure below, packet 1 is analyzed using a record designed for standard traffic analysis on the input interface and a record designed for security analysis on the output interface.
The figure below shows a more complex example of how you can apply different types of flow monitors with custom records.
Normal
The default cache type is “normal”. In this mode, the entries in the cache are aged out according to the timeout active and timeout inactive settings. When a cache entry is aged out, it is removed from the cache and exported via any exporters configured.
Flow Samplers
Flow samplers are created as separate components in a router’s configuration. Flow samplers are used to reduce the load on the device that is running Flexible NetFlow by limiting the number of packets that are selected for analysis.
Flow sampling exchanges monitoring accuracy for router performance. When you apply a sampler to a flow monitor, the overhead load on the router of running the flow monitor is reduced because the number of packets that the flow monitor must analyze is reduced. The reduction in the number of packets that are analyzed by the flow monitor causes a corresponding reduction in the accuracy of the information stored in the flow monitor’s cache.
Samplers are combined with flow monitors when they are applied to an interface with the ip flow monitor command.
Supported Flexible NetFlow Fields
 Note | If the packet has a VLAN field, then that length is not accounted for. |
|
Field |
Layer 2 In |
Layer 2 Out |
IPv4 In |
IP v4 Out |
IPv6 In |
IPv6 Out |
Notes |
|---|---|---|---|---|---|---|---|
|
Key or Collect Fields |
|||||||
|
Interface input |
Yes |
— |
Yes |
— |
Yes |
— |
If you apply a flow monitor in the input direction: |
|
Interface output |
— |
Yes |
— |
Yes |
— |
Yes |
If you apply a flow monitor in the output direction: |
|
Field |
Layer 2 In |
Layer 2 Out |
IPv4 In |
IP v4 Out |
IPv6 In |
IPv6 Out |
Notes |
|---|---|---|---|---|---|---|---|
|
Key Fields |
|||||||
|
Flow direction |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
Ethertype |
Yes |
Yes |
— |
— |
— |
— |
|
|
VLAN input |
Yes |
— |
Yes |
— |
Yes |
— |
Supported only for a switch port. |
|
VLAN output |
— |
Yes |
— |
Yes |
— |
Yes |
Supported only for a switch port. |
|
dot1q VLAN input |
Yes |
— |
Yes |
— |
Yes |
— |
Supported only for a switch port. |
|
dot1q VLAN output |
— |
Yes |
— |
Yes |
— |
Yes |
Supported only for a switch port. |
|
dot1q priority |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Supported only for a switch port. |
|
MAC source address input |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
MAC source address output |
— |
— |
— |
— |
— |
— |
|
|
MAC destination address input |
Yes |
— |
Yes |
— |
Yes |
— |
|
|
MAC destination address output |
— |
Yes |
— |
Yes |
— |
Yes |
|
|
IPv4 version |
— |
— |
Yes |
Yes |
Yes |
Yes |
|
|
IPv4 TOS |
— |
— |
Yes |
Yes |
Yes |
Yes |
|
|
IPv4 protocol |
— |
— |
Yes |
Yes |
Yes |
Yes |
Must use if any of src/dest port, ICMP code/type, IGMP type or TCP flags are used. |
|
IPv4 TTL |
— |
— |
Yes |
Yes |
Yes |
Yes |
|
|
IPv4 source address |
— |
— |
Yes |
Yes |
— |
— |
|
|
IPv4 destination address |
— |
— |
Yes |
Yes |
— |
— |
|
|
ICMP IPv4 type |
— |
— |
Yes |
Yes |
— |
— |
|
|
ICMP IPv4 code |
— |
— |
Yes |
Yes |
— |
— |
|
|
IGMP type |
— |
— |
Yes |
Yes |
— |
— |
|
Field |
Layer 2 In |
Layer 2 Out |
IPv4 In |
IP v4 Out |
IPv6 In |
IPv6 Out |
Notes |
|---|---|---|---|---|---|---|---|
|
Key Fields continued |
|||||||
|
IPv6 version |
— |
— |
Yes |
Yes |
Yes |
Yes |
Same as IP version. |
|
IPv6 protocol |
— |
— |
Yes |
Yes |
Yes |
Yes |
Same as IP protocol. Must use if any of src/dest port, ICMP code/type, IGMP type or TCP flags are used. |
|
IPv6 source address |
— |
— |
— |
— |
Yes |
Yes |
|
|
IPv6 destination address |
— |
— |
— |
— |
Yes |
Yes |
|
|
IPv6 traffic-class |
— |
— |
Yes |
Yes |
Yes |
Yes |
Same as IP TOS. |
|
IPv6 hop-limit |
— |
— |
Yes |
Yes |
Yes |
Yes |
Same as IP TTL. |
|
ICMP IPv6 type |
— |
— |
— |
— |
Yes |
Yes |
|
|
ICMP IPv6 code |
— |
— |
— |
— |
Yes |
Yes |
|
|
source-port |
— |
— |
Yes |
Yes |
Yes |
Yes |
|
|
dest-port |
— |
— |
Yes |
Yes |
Yes |
Yes |
|
Field |
Layer 2 In |
Layer 2 Out |
IPv4 In |
IP v4 Out |
IPv6 In |
IPv6 Out |
Notes |
|---|---|---|---|---|---|---|---|
|
Collect Fields |
|||||||
|
Bytes long |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Packet size = (Ethernet frame size including FCS - 18 bytes) Recommended: Avoid this field and use Bytes layer2 long. |
|
Packets long |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
Timestamp absolute first |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
Timestamp absolute last |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
TCP flags |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Collects all flags. |
|
Bytes layer2 long |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Default Settings
The following table lists the Flexible NetFlow default settings for the switch.
|
Setting |
Default |
|---|---|
|
Flow active timeout |
1800 seconds |
|
Flow timeout inactive |
15 seconds |
How to Configure Flexible NetFlow
To configure Flexible NetFlow, follow these general steps:
-
Create a flow record by specifying keys and non-key fields to the flow.
-
Create an optional flow exporter by specifying the protocol and transport destination port, destination, and other parameters.
-
Create a flow monitor based on the flow record and flow exporter.
-
Create an optional sampler.
-
Apply the flow monitor to a Layer 2 port, Layer 3 port, or VLAN.
- Configuring a Flow Record
- Creating a Flow Exporter
- Creating a Flow Monitor
- Creating a Flow Sampler
- Applying a Flow to an Interface
Configuring a Flow Record
Perform this task to configure a customized flow record.
Customized flow records are used to analyze traffic data for a specific purpose. A customized flow record must have at least one match criterion for use as the key field and typically has at least one collect criterion for use as a nonkey field.
There are hundreds of possible permutations of customized flow records. This task shows the steps that are used to create one of the possible permutations. Modify the steps in this task as appropriate to create a customized flow record for your requirements.
1.
enable
2.
configure
terminal
3.
flow
record
record-name
4.
description
description
5.
match
{ipv4 |
ipv6} {destination |
source}
address
6. Repeat Step 5 as required to configure additional key fields for the record.
7.
collect
interface
{input |
output}
8. Repeat the above step as required to configure additional nonkey fields for the record.
9.
end
10.
show
flow
record
record-name
11.
show
running-config
flow
record
record-name
DETAILED STEPS
Creating a Flow Exporter
You can create a flow export to define the export parameters for a flow.
 Note | Each flow exporter supports only one destination. If you want to export the data to multiple destinations, you must configure multiple flow exporters and assign them to the flow monitor. You can export to a destination using IPv4 address. |
2.
flow exporter
name
3.
description
string
4.
destination {hostname |
ipv4-address}
[
vrf
vrf-name]
5.
dscp
value
6.
source {interface-id }
7.
option {exporter-stats |
interface-table |
sampler-table}
[timeout
seconds]
8.
template
data
timeout
seconds
9.
transport
udp
number
10.
ttl
seconds
11.
export-protocol
{netflow-v9}
13.
show running-config
flow
exporter
exporter-name
14.
show flow exporter
[name
record-name]
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |||
| Step 2 | flow exporter
name
Example:
Switch(config)# flow exporter ExportTest
|
Creates a flow exporter and enters flow exporter configuration mode. | ||
| Step 3 | description
string
Example:
Switch(config-flow-exporter)# description ExportV9
|
(Optional) Describes this flow record as a maximum 63-character string. | ||
| Step 4 | destination {hostname |
ipv4-address}
[
vrf
vrf-name]
Example:
Switch(config-flow-exporter)# destination 192.0.2.1 (IPv4 destination)
|
Sets the IPv4 destination address or hostname for this exporter. | ||
| Step 5 |
dscp
value
Example:
Switch(config-flow-exporter)# dscp 0
|
(Optional) Specifies the differentiated services codepoint value. The range is from 0 to 63. The default is 0. | ||
| Step 6 | source {interface-id }
Example:
Switch(config-flow-exporter)# source gigabitEthernet1/0/1
|
(Optional) Specifies the interface to use to reach the NetFlow collector at the configured destination. The following interfaces can be configured as source: | ||
| Step 7 | option {exporter-stats |
interface-table |
sampler-table}
[timeout
seconds]
Example: Switch
|
(Optional) Configures options data parameters for the exporter. You can configure all three options concurrently. The range for the timeout is 1 to 86400 seconds. The default is 600. | ||
| Step 8 | template
data
timeout
seconds
Example: Switch
|
(Optional) Configures resending of templates based on a timeout. The range is 1 to 86400 seconds (86400 seconds equals 24 hours). The default is 600.
| ||
| Step 9 | transport
udp
number
Example:
Switch(config-flow-exporter)# transport udp 200
|
(Optional) Specifies the UDP port to use to reach the NetFlow collector. The range is from 0 to 65535. The range is from 1 to 65536 | ||
| Step 10 | ttl
seconds
Example: Switch(config-flow-exporter)# ttl 210
|
(Optional) Configures the time-to-live (TTL) value for datagrams sent by the exporter. The range is from 1 to 255 seconds. The default is 255. | ||
| Step 11 |
export-protocol
{netflow-v9}
Example:
Switch(config-flow-exporter)# export-protocol netflow-v9
|
Specifies the version of the NetFlow export protocol used by the exporter. | ||
| Step 12 | end
Example: Switch(config-flow-record)# end | |||
| Step 13 | show running-config
flow
exporter
exporter-name
Example: Switch# show running-config flow exporter ExportTest
| (Optional) Verifies the configured flow exporter. | ||
| Step 14 | show flow exporter
[name
record-name]
Example:
Switch show flow exporter ExportTest
|
(Optional) Displays information about NetFlow flow exporters. | ||
| Step 15 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Define a flow monitor based on the flow record and flow exporter.
Creating a Flow Monitor
Perform this required task to create a customized flow monitor.
Each flow monitor has a separate cache assigned to it. Each flow monitor requires a record to define the contents and layout of its cache entries. These record formats can be a user-defined format. An advanced user can create a customized format using the flow record command.
If you want to use a customized record, you must create the customized record before you can perform this task. If you want to add a flow exporter to the flow monitor for data export, you must create the exporter before you can complete this task.
 Note | You must use the no ip flow monitor command to remove a flow monitor from all of the interfaces to which you have applied it before you can modify the parameters for the record command on the flow monitor. For information about the ip flow monitor command, refer to the Cisco IOS Flexible NetFlow Command Reference. |
1.
enable
2.
configure
terminal
3.
flow
monitor
monitor-name
4.
description
description
5.
record
{record-name}
6.
cache
{timeout
{active}
seconds |
type {
normal
}
7. Repeat Step 6 as required to finish modifying the cache parameters for this flow monitor.
8.
exporter
exporter-name
9.
end
10.
show
flow
monitor
[[name]
monitor-name
[cache [format {csv |
record |
table}]]
]
11.
show
running-config
flow
monitor
monitor-name
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. | ||
| Step 2 |
configure
terminal
Example:
Switch# configure terminal
|
Enters global configuration mode. | ||
| Step 3 |
flow
monitor
monitor-name
Example:
Switch(config)# flow monitor FLOW-MONITOR-1
|
Creates a flow monitor and enters Flexible NetFlow flow monitor configuration mode. | ||
| Step 4 |
description
description
Example:
Switch(config-flow-monitor)# description Used for basic ipv4 traffic analysis
|
(Optional) Creates a description for the flow monitor. | ||
| Step 5 |
record
{record-name}
Example:
Switch(config-flow-monitor)# record FLOW-RECORD-1
|
Specifies the record for the flow monitor. | ||
| Step 6 |
cache
{timeout
{active}
seconds |
type {
normal
}
Example: Device(config-flow-monitor)# cache type normal |
(Optional) Modifies the flow monitor cache parameters such as timeout values, number of cache entries, and the cache type.
| ||
| Step 7 | Repeat Step 6 as required to finish modifying the cache parameters for this flow monitor. |
— | ||
| Step 8 |
exporter
exporter-name
Example:
Switch(config-flow-monitor)# exporter EXPORTER-1
|
(Optional) Specifies the name of an exporter that was created previously. | ||
| Step 9 |
end
Example:
Switch(config-flow-monitor)# end
|
Exits Flexible NetFlow flow monitor configuration mode and returns to privileged EXEC mode. | ||
| Step 10 |
show
flow
monitor
[[name]
monitor-name
[cache [format {csv |
record |
table}]]
]
Example:
Switch# show flow monitor FLOW-MONITOR-2 cache
|
(Optional) Displays the status for a Flexible NetFlow flow monitor. | ||
| Step 11 |
show
running-config
flow
monitor
monitor-name
Example:
Switch# show running-config flow monitor FLOW_MONITOR-1
|
(Optional) Displays the configuration of the specified flow monitor. | ||
| Step 12 | copy running-config startup-config
Example: Switch# copy running-config startup-config |
Creating a Flow Sampler
Perform this required task to configure and enable a flow sampler.
1.
enable
2.
configure
terminal
3.
sampler
sampler-name
4.
description
description
5.
mode
{random}
1
out-of
window-size
6.
exit
7.
interface
type
number
8. {ip | ipv6} flow monitor monitor-name [[sampler] sampler-name] {input | output}
9.
end
10.
show
sampler
sampler-name
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example: Device> enable |
Enables privileged EXEC mode. |
| Step 2 |
configure
terminal
Example: Device# configure terminal |
Enters global configuration mode. |
| Step 3 |
sampler
sampler-name
Example: Device(config)# sampler SAMPLER-1 |
Creates a sampler and enters sampler configuration mode. |
| Step 4 |
description
description
Example: Device(config-sampler)# description Sample at 50% |
(Optional) Creates a description for the flow sampler. |
| Step 5 |
mode
{random}
1
out-of
window-size
Example: Device(config-sampler)# mode random 1 out-of 2 |
Specifies the sampler mode and the flow sampler window size. |
| Step 6 |
exit
Example: Device(config-sampler)# exit |
Exits sampler configuration mode and returns to global configuration mode. |
| Step 7 |
interface
type
number
Example: Device(config)# interface GigabitEthernet 0/0/0 |
Specifies an interface and enters interface configuration mode. |
| Step 8 | {ip |
ipv6}
flow
monitor
monitor-name
[[sampler]
sampler-name]
{input |
output}
Example: Device(config-if)# ip flow monitor FLOW-MONITOR-1 sampler SAMPLER-1 input |
Assigns the flow monitor and the flow sampler that you created to the interface to enable sampling. |
| Step 9 |
end
Example: Device(config-if)# end |
Exits interface configuration mode and returns to privileged EXEC mode. |
| Step 10 |
show
sampler
sampler-name
Example: Device# show sampler SAMPLER-1 |
Displays the status and statistics of the flow sampler that you configured and enabled. |
Applying a Flow to an Interface
You can apply a flow monitor and an optional sampler to an interface.
2.
interface
type
3.
{ip flow monitor |
ipv6 flow
monitor}name
[layer2-switched|multicast|sampler|unicast
name] { input}
5.
show flow interface
[interface-type
number]
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configure
terminal
Example: Switch# configure terminal | |
| Step 2 | interface
type
Example:
Switch(config)# interface GigabitEthernet1/0/1
|
Enters interface configuration mode and configures an interface. Command parameters for the interface configuration include: Flexible Net Flow is supported only on the service module 1-Gigabit or 10-Gigabit Ethernet interfaces. You cannot attach a NetFlow monitor to a port channel interface. If both service module interfaces are part of an EtherChannel, you should attach the monitor to both physical interfaces. |
| Step 3 | {ip flow monitor |
ipv6 flow
monitor}name
[layer2-switched|multicast|sampler|unicast
name] { input}
Example:
Switch(config-if)# ip flow monitor MonitorTest input
|
Associate an IPv4 or an IPv6 flow monitor, and an optional sampler to the interface for input or output packets. |
| Step 4 | end
Example: Switch(config-flow-monitor)# end | |
| Step 5 | show flow interface
[interface-type
number]
Example:
Switch# show flow interface
|
(Optional) Displays information about NetFlow on an interface. |
| Step 6 | copy
running-config startup-config
Example: Switch# copy running-config startup-config |
Monitoring Flexible NetFlow
|
Command |
Purpose |
|---|---|
|
show flow exporter [broker | export-ids | name | name | statistics | templates] |
Displays information about NetFlow flow exporters and statistics. |
|
show flow exporter [ name exporter-name] |
Displays information about NetFlow flow exporters and statistics. |
|
show flow interface |
Displays information about NetFlow interfaces. |
|
show flow monitor [ name exporter-name] |
Displays information about NetFlow flow monitors and statistics. |
|
show flow monitor statistics |
Displays the statistics for the flow monitor |
|
show flow monitor cache format {table | record | csv} |
Displays the contents of the cache for the flow monitor, in the format specified. |
|
show flow record [ name record-name] |
Displays information about NetFlow flow records. |
|
show flow ssid |
Displays NetFlow monitor installation status for a WLAN. |
|
show sampler [broker | name | name] |
Displays information about NetFlow samplers. |
|
show wlan wlan-name |
Displays the WLAN configured on the device. |
Configuration Examples for Flexible NetFlow
Example: Configuring a Flow
This example shows how to create a flow and apply it to an interface:
Switch# configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)# flow export export1 Switch(config-flow-exporter)# destination 10.0.101.254 Switch(config-flow-exporter)# transport udp 2055 Switch(config-flow-exporter)# exit Switch(config)# flow record record1 Switch(config-flow-record)# match ipv4 source address Switch(config-flow-record)# match ipv4 destination address Switch(config-flow-record)# match ipv4 protocol Switch(config-flow-record)# match transport source-port Switch(config-flow-record)# match transport destination-port Switch(config-flow-record)# collect counter byte long Switch(config-flow-record)# collect counter packet long Switch(config-flow-record)# collect timestamp absolute first Switch(config-flow-record)# collect timestamp absolute last Switch(config-flow-record)# exit Switch(config)# flow monitor monitor1 Switch(config-flow-monitor)# record record1 Switch(config-flow-monitor)# exporter export1 Switch(config-flow-monitor)# exit Switch(config)# interface tenGigabitEthernet 1/0/1 Switch(config-if)# ip flow monitor monitor1 input Switch(config-if)# end
Additional References
Related Documents
| Related Topic | Document Title |
|---|---|
|
Flexible NetFlow CLI Commands |
Flexible NetFlow Command Reference, Cisco IOS XE Release 3SE (Cisco WLC 5700 Series) |
Error Message Decoder
| Description | Link |
|---|---|
|
To help you research and resolve system error messages in this release, use the Error Message Decoder tool. |
https://www.cisco.com/cgi-bin/Support/Errordecoder/index.cgi |
Standards and RFCs
| Standard/RFC | Title |
|---|---|
|
RFC 3954 |
Cisco Systems NetFlow Services Export Version 9 |
MIBs
| MIB | MIBs Link |
|---|---|
|
All supported MIBs for this release. |
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Technical Assistance
| Description | Link |
|---|---|
|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
 Feedback
Feedback