NetworkAddress Translation (NAT) supports several methods to translate IP addresses betweenprivate and public networks. Each
method serves a different use case and provides varying levels of address conservation and flexibility.
Static NAT
Static NAT (Static Address Translation) provides a permanent, one-to-one mapping between a private (inside local) IP address
and a public (inside global) IP address.
Use static NAT when a device inside your network must always be reachable from the outside using the same public IP address
(for example, servers or network devices requiring fixed external access).
Dynamic NAT
Dynamic NAT (Dynamic Address Translation) maps private (inside local) addresses to public (inside global) addresses selected
from a pool. The mapping is created dynamically when an inside device initiates a connection and is maintained only for the
duration of the session.
Dynamic NAT is useful when you have more inside hosts than public addresses, but not all hosts need simultaneous external
access.
Port Address Translation (PAT) / NAT Overloading
PAT, also known as NAT overloading, allows multiple inside local addresses to share a single inside global address. Each session
is uniquely identified by a combination of the IP address and Layer 4 port number.
PAT conserves public IP addresses and enables thousands of inside hosts to access external networks using just one or a few
public addresses.
Static Port Translation
Static port translation creates a fixed mapping between a specific IP address/port pair on the inside and a specific IP address/port
pair on the outside.
Use static port translation when both IP address and port mapping need to be preserved for consistent access, such as for
specific services hosted internally.
Subnet (Network) Static Translation
Subnet static translation allows a range of inside local subnets to be mapped to a corresponding range of inside global subnets.
The mapping is defined so that each host in the subnet has a predictable translation.
This is useful when a group of internal addresses needs to be mapped to a different address block externally, such as during
network migrations or for overlapping address resolution.
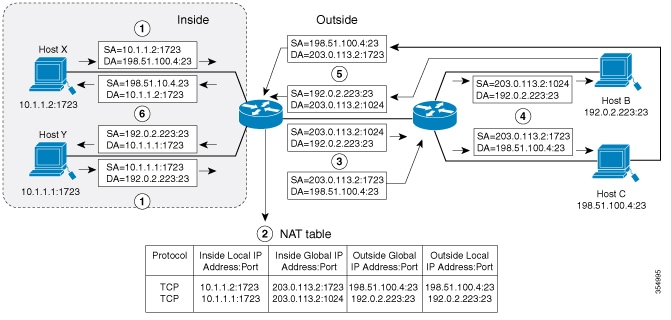
Inside Source Address Translation
Inside source address translation translates the source address of packets from internal hosts (inside local) to an external,
globally routable address (inside global).
Allows private hosts to initiate connections to the public network and appear as routable addresses.
-
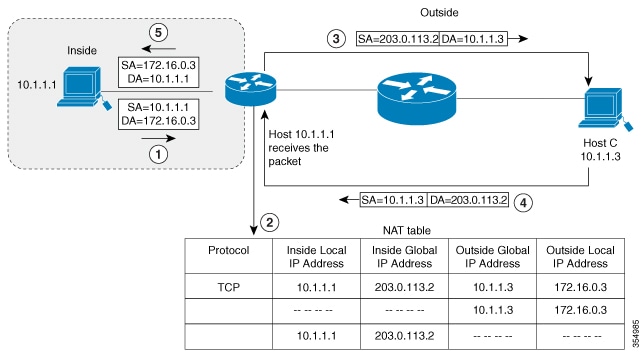
Connection Initiation
The user at host 10.1.1.1 initiates a connection to an external host (Host B) located on the outside network.
-
NAT Rule Evaluation and Translation Decision
The NAT module intercepts the outbound packet and evaluates it against the configured NAT rules:
-
If a matching static translation rule exists, the packet is translated to the specified inside global address.
-
If no static rule matches, the packet is checked against dynamic translation rules. If a matching dynamic rule is found, the
packet is translated using an available inside global address from the configured pool.
-
Upon a successful translation, the NAT module creates and stores a fully qualified flow entry in its translation database.
This enables fast bidirectional translation and forwarding for future packets in the same flow.
-
If no rule matches, the packet is forwarded without translation.
-
If a matching dynamic rule is found but no valid inside global address is available, the packet is dropped.

Note
|
If an Access Control List (ACL) is used for dynamic NAT, only packets permitted by the ACL are considered for translation.
|
-
Source Address Replacement and Fowarding
The device replaces the source IP address (inside local) of host 10.1.1.1 with the inside global address (for example, 203.0.113.2).
Only packet-relevant checksums are updated; all other packet fields remain unchanged. The translated packet is then forwarded
to the outside network.
-
Translation Flow Entry Maintenance
The NAT module maintains a fully qualified flow entry for the translated session in its translation database. This entry facilitates
fast hardware translation and forwarding for all subsequent packets in this flow, in both directions.
-
Response from Outside Host
Host B receives the packet and sends a response addressed to the inside global IP address (203.0.113.2).
-
Reverse Translation
The NAT module intercepts the response packet destined for the inside global address. Usingthe stored flow entry, the module
translates the destination address back to the original inside local address (10.1.1.1), and forwards the packet to the internal
host.
-
Ongoing Conversation
Host 10.1.1.1 receives the response and communication continues. The NAT device repeats Steps 2–6 for each packet in the session.
Outside Source Address Translation
Outside source address translation translates the source address of packets from external hosts (outside global) to an internal,
locally significant address (outside local).
Used in advanced scenarios, such as when connecting to overlapping networks or allowing external devices to appear as unique
addresses within your private network. For a detailed process, see the section on Overlapping Networks.

 Feedback
Feedback