- New and Changed Information
- Preface
-
- Configuring the MPLS Label Distribution Protocol
- Configuring MPLS LDP Autoconfiguration
- Configuring MPLS LDP Session Protection
- Configuring MPLS LDP IGP Synchronization
- Configuring MPLS LDP Lossless MD5 Session Authentication
- Configuring MPLS LDP Label Filtering
- Configuring MPLS LDP Static Label Binding
- Configuring MPLS LDP Graceful Restart
-
- Configuring Basic MPLS TE
- Configuring Automatic Bandwidth Adjustment for MPLS TE Tunnels
- Configuring MPLS TE RSVP
- Configuring the Path Selection Metric for MPLS TE Tunnels
- Configuring LSP Attributes for MPLS TE
- Configuring MPLS TE Verbatim Paths
- Configuring MPLS TE Forwarding Adjacency
- Configuring MPLS TE Class-Based Tunnel Selection
- Configuring MPLS TE Path Protection
- Configuring MPLS TE Fast Reroute Link and Node Protection
-
- Configuring Any Transport over MPLS
- Configuring Any Transport over MPLS Pseudowire Provisioning
- Configuring Ethernet over MPLS
- Configuring EoMPLS Layer 2 VPN Graceful Restart
- Configuring Virtual Private LAN Service
- Configuring Layer 2 VPN Pseudowire Redundancy
- Configuring Layer 2 VPN VPLS Dual-Homing with a vPC
- Configuration Limits for Cisco NX-OS MPLS
- RFCs
Cisco Nexus 7000 Series NX-OS MPLS Configuration Guide
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- June 4, 2014
Chapter: Configuring MPLS Layer 3 VPNs
- Finding Feature Information
- Information About MPLS Layer 3 VPNs
- MPLS Layer 3 VPN Definition
- How an MPLS Layer 3 VPN Works
- How VRF Tables Work in an MPLS Layer 3 VPN
- VPN Route Distribution and Route Targets
- Route Leaking and Importing Routes from the Default VRF
- VRF Route Table Limits
- VPN ID and Route Distinguisher
- 6VPE
- BGP PIC
- BGP Distribution of VPN Routing Information
- BGP Next-Hop Address Tracking
- MPLS Forwarding
- Site of Origin
- Site of Origin and EIGRP
- OSPF Sham Link
- OSPF LSA Throttling
- Components of MPLS Layer 3 VPNs
- High Availability and ISSU for MPLS Layer 3 VPNs
- Hub-and-Spoke Topology
- OSPF Sham-Link Support for MPLS VPN
- Example: MPLS Layer 3 VPN Using BGP
- Example: MPLS Layer 3 VPN Using RIP
- Example: MPLS Layer 3 VPN Using Static or Direct Routes
- Example: MPLS Layer 3 VPN Using OSPF
- Example: MPLS Layer 3 VPN Using EIGRP
- Example: MPLS 6VPE Using BGP
- Example: Hub-and-Spoke Topology
- Example: OSPF Sham-Link Support for an MPLS VPN
Configuring MPLS Layer 3 VPNs
This chapter describes how to configure Multiprotocol Label Switching (MPLS) Layer 3 virtual private networks (VPNs) on Cisco NX-OS devices.
This chapter includes the following sections:
- Finding Feature Information
- Information About MPLS Layer 3 VPNs
- Licensing Requirements for MPLS Layer 3 VPNs
- Prerequisites for MPLS Layer 3 VPNs
- Guidelines and Limitations for MPLS Layer 3 VPNs
- Default Settings for MPLS Layer 3 VPNs
- Configuring MPLS Layer 3 VPNs
- Verifying the MPLS Layer 3 VPN Configuration
- Configuration Examples for MPLS Layer 3 VPNs
- Additional References for MPLS Layer 3 VPNs
- Feature History for MPLS Layer 3 VPNs
Finding Feature Information
Your software release might not support all the features documented in this module. For the latest caveats and feature information, see the Bug Search Tool at https://tools.cisco.com/bugsearch/ and the release notes for your software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the “New and Changed Information” chapter or the Feature History table below.
Information About MPLS Layer 3 VPNs
An MPLS Layer 3 VPN consists of a set of sites that are interconnected by an MPLS provider core network. At each customer site, one or more customer edge (CE) routers or Layer 2 switches attach to one or more provider edge (PE) routers.
This section includes the following topics:
- MPLS Layer 3 VPN Definition
- How an MPLS Layer 3 VPN Works
- Components of MPLS Layer 3 VPNs
- High Availability and ISSU for MPLS Layer 3 VPNs
- Hub-and-Spoke Topology
- OSPF Sham-Link Support for MPLS VPN
MPLS Layer 3 VPN Definition
MPLS-based Layer 3 VPNs are based on a peer model that enables the provider and the customer to exchange Layer 3 routing information. The provider relays the data between the customer sites without direct customer involvement.
When you add a new site to an MPLS Layer 3 VPN, you must update the provider edge router that provides services to the customer site.
MPLS Layer 3 VPNs include the following components:
- Provider (P) router—A router in the core of the provider network. P routers run MPLS switching and do not attach VPN labels (an MPLS label in each route assigned by the PE router) to routed packets. P routers forward packets based on the Label Distribution Protocol (LDP).
- Resource Reservation Protocol (RSVP) traffic engineering (TE)— A protocol that assigns a label to the egress PE router.
- Provider edge (PE) router—A router that attaches the VPN label to incoming packets that are based on the interface or subinterface on which they are received. A PE router attaches directly to a CE router.
- Customer edge (CE) router—An edge router on the network of the provider that connects to the PE router on the network. A CE router must interface with a PE router.
Figure 22-1 shows a basic MPLS Layer 3 VPN.
Figure 22-1 Basic MPLS Layer 3 VPN Terminology
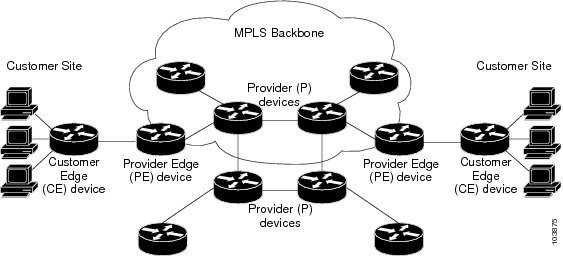
How an MPLS Layer 3 VPN Works
MPLS Layer 3 VPN functionality is enabled at the edge of an MPLS network. The PE router performs the following tasks:
How VRF Tables Work in an MPLS Layer 3 VPN
Each Layer 3 VPN is associated with one or more virtual routing and forwarding (VRF) instance. A VRF defines the VPN membership of a customer site that is attached to a PE router. A VRF consists of the following components:
- An IP routing table
- A set of interfaces that use the forwarding table
- A set of rules and routing protocol parameters that control the information that is included in the routing table
A one-to-one relationship does not necessarily exist between customer sites and VPNs. A site can be a member of multiple VPNs. Typically, a CE router at a site can associate with only one VRF. The VRF of the CE router contains all the routes that are available to the site from the VPNs of which the VRF is a member.
Packet forwarding information is stored in the IP routing table for each VRF. A separate set of routing tables is maintained for each VRF. These tables prevent information from being forwarded outside a VPN and also prevent packets that are outside a VPN from being forwarded to a router within the VPN.
VPN Route Distribution and Route Targets
The distribution of VPN routing information is controlled through VPN route targets that are implemented by BGP extended communities. VPN routing information is distributed as follows:
- When a VPN route that is learned from a CE router is injected into BGP, a list of VPN route target extended community attributes is associated with the VPN route. Typically, the list of route target community extended values is set from an export list of route targets associated with the VRF from which the route was learned.
- An import list of route target extended communities is associated with each VRF. The import list defines route target extended community attributes that a route must have in order for the route to be imported into the VRF. For example, if the import list for a particular VRF includes route target extended communities A, B, and C, then any VPN route that carries any of those route target extended communities—A, B, or C—is imported into the VRF.
Route Leaking and Importing Routes from the Default VRF
You can import IP prefixes from the global routing table (the default VRF) into any other VRF by using an import policy. The VRF import policy uses a route map to specify the prefixes to be imported into a VRF. The policy can import IPv4 and IPv6 unicast prefixes.

Note Routes in the BGP default VRF can be imported directly. Any other routes in the global routing table should be redistributed into BGP first.
IP prefixes are defined as match criteria for the import route map through standard route policy filtering mechanisms. For example, you can create an IP prefix list or an as-path filter to define an IP prefix or IP prefix range and use that prefix list or as-path filter in a match clause for the route map. Prefixes that pass through the route map are imported into the specified VRF using the import policy. IP prefixes that are imported into a VRF through this import policy cannot be reimported into another VPN VRF.
The maximum number of prefixes that can be imported from the default VRF is controlled by a limit that you configure.
VRF Route Table Limits
You can configure a limit to the number of routes that are accepted and installed into a VRF routing table to prevent overloading the PE router. This limit applies only to dynamic routing protocols and not to static or connected routes. Alternately, when you use eBGP as the PE-CE protocol, you can configure a per-neighbor maximum prefix limit.
VPN ID and Route Distinguisher
You use an MPLS VPN ID to identify a VPN but not to control route distribution or routing updates. You assign the same VPN ID to all routers in the provider network that service the VPN. The VPN ID format is specified in RFC 2685.
The route distinguisher (RD) is an eight-byte value that is combined with the IPv4 or IPv6 prefix learned by the PE router to create a globally unique address.
6VPE
The IPv6 PE router over MPLS Virtual Private Network (6VPE) feature is an extension of Layer 3 VPNs that support VPN connectivity for IPv6 sites over an MPLS/IPv4 provider core network. The VPN-IPv6 address is formed by adding an 8-byte RD to a 16-byte IPv6 address, which results in a 24-byte VPN-IPv6 address. 6VPE uses VRF tables to assign the forwarding information at the PE and uses the IPv6 address family. BGP supports the VPN-IPv6 address family. This address family supports both per-prefix and per-VRF label allocation modes.
6VPE prepends the IPv4 next-hop address with ::FFFF: to create the IPv4-mapped IPv6 address for the next hop that is advertised.

Note MPLS Layer 3 load balancing is supported for 6VPE but is not supported with per-VRF label allocation.
VPN IPv4 sites often use private addressing for their addressing plan. These addresses do not need to be registered, and they are not routable on the public network. Whenever a host within a private site needs to access a public domain, it goes through a device that finds a public address on its behalf, such as a network address translator or an application proxy.
Due to the larger address space available with IPv6, the easiest approach to IPv6 addressing is to use IPv6 global addresses for the private addressing plan. Another approach is to use unique local addresses (ULAs). ULAs are easy to filter at site boundaries based on their local scope. ULAs are Internet service provider (ISP)-independent and can be used for communications inside a site without any permanent or intermittent Internet connectivity.
In 6VPE, ULAs are treated as regular global addresses. The router configuration filters ULA prefixes to prevent them from appearing in the public domain. Link-local addresses on the peer are not announced by BGP (IPv6 or IPv6 VPN) speakers.
A host within a private site that needs to access a public domain can do so through an IPv6 application proxy (such as a web proxy for accessing web pages), which accesses the public resource, on behalf of the host, with a global routable address, or the host can use a public address of its own. In the latter case, if you have deployed ULAs, the IPv6 host also is configured with a routable global address. A source address selection algorithm is used to select one or the other, based on the destination address.
BGP PIC
BGP Prefix Independent Convergence (PIC) achieves subsecond convergence in the forwarding plane for BGP IP and Layer 3 VPN routes in various cases of BGP next-hop network reachability failures. BGP PIC has two categories: PIC Core and PIC Edge. PIC Core ensures fast convergence for BGP routes when there is a link or node failure in the core that causes a change in the IGP reachability to a remote BGP next-hop address. PIC Edge ensures fast convergence to a precomputed BGP backup path when an external (eBGP) edge link or an external neighbor node fails.
IPv4, VPNv4, 6PE, and VPNv6 (6VPE) support PIC Core with the following constraints:
- For both IP and MPLS core, convergence for Internet routes is prefix-independent on the order of BGP next hops.
- With per-VRF label allocation, VPN route convergence is also prefix-independent on the order of BGP next hops. That is, when a path to a remote PE changes, convergence is determined by the number of VRFs on that PE.
- With per-prefix label allocation, route convergence is not prefix-independent. Convergence moves to the order of VPN routes that are advertised by a remote PE if a failure or change occurs in the reachability to that PE.

Note PIC edge is not supported.
BGP Distribution of VPN Routing Information
A PE router can learn an IP prefix from the following sources:
- A CE router by static configuration
- A directly connected network
- A BGP session with the CE router
- A routing protocol exchange with the CE router
After the PE router learns the IP prefix, the PE can conditionally export the prefix into a VPN prefix by combining it with an 8-byte route distinguisher. The generated prefix is a member of the VPN-IPv4 or the VPN-IPv6 address family. It uniquely identifies the customer address, even if the customer site is using globally nonunique (unregistered private) IP addresses. You configure the route distinguisher that generates the VPN-IPv4 or VPN-IPv6 prefix on the VRF on the PE router.
BGP distributes reachability information for VPN prefixes for each VPN. BGP communication takes place at two levels:
- Within an autonomous system using interior BGP (iBGP)
- Between autonomous systems using external BGP (eBGP)
PE-PE or PE-RR (route reflector) sessions are iBGP sessions, and PE-CE sessions are eBGP sessions. BGP propagates reachability information for VPN-IPv4 and VPN-IPv6 prefixes among PE routers by using BGP multiprotocol extensions (see RFC 2283, Multiprotocol Extensions for BGP-4 ). The BGP multiprotocol extensions define support for address families other than IPv4. When you use the extensions, you ensure that the routes for a given VPN are learned only by other members of that VPN. This process enables members of the VPN to communicate with each other.
In an Enhanced Interior Gateway Routing Protocol (EIGRP) PE-CE environment, when an EIGRP internal route is redistributed into BGP by one PE, then back into EIGRP by another PE, the originating router ID for the route is set to the router ID of the second PE. This process replaces the original internal router ID.

Note The BGP minimum route advertisement interval (MRAI) value for all iBGP and eBGP sessions is zero and is not configurable.
BGP Next-Hop Address Tracking
See the “Configuring Advanced BGP” chapter of the Cisco Nexus 7000 Series NX-OS Unicast Routing Configuration Guide for information.
MPLS Forwarding
Based on routing information in the VRF IP routing table, the router forwards packets to their destination using MPLS.
A PE router binds a label to each customer prefix that is learned from a CE router and includes the label in the network reachability information for the prefix that it advertises to other PE routers. When a PE router forwards a packet that it received from a CE router across the provider network, it labels the packet with the label learned from the destination PE router. When the destination PE router receives the labeled packet, it removes the label and uses it to direct the packet to the correct CE router. Label forwarding across the provider backbone is based on either dynamic label switching or traffic engineered paths. A customer data packet carries two levels of labels when it traverses the backbone:
Site of Origin
The site of origin prevents routing loops when you have a multihomed VPN site. Routes learned from the same site are tagged with the same site-of-origin value that is configured at the PE on all the PE-CE links to the same site. Routes with a particular site-of-origin value are never readvertised back to a CE with the same site-of-origin value configured at the PE-CE link. This process prevents a CE router from relearning routes that originated from the same site. BGP and EIGRP use site of origin to prevent loops.
You can override the autonomous system number (ASN) of a site with the ASN of the provider. This feature is often used with the site of origin to identify the site where a route originated and prevent routing loops between routers within a VPN.
Site of Origin and EIGRP
When EIGRP is used as the PE-CE routing protocol, EIGRP uses BGP extended communities to carry the EIGRP vector metric, AS number, and other information to recreate the EIGRP internal routes with the original attributes across the VPN cloud. EIGRP external routes or routes from a different autonomous system are recreated as external routes.
EIGRP uses site of origin to prevent routing loops when you have a multihomed VPN site. You must configure the site of origin for EIGRP-based PE routes that are learned from the CE. We recommend you use the site of origin for CE routers for better performance.
You might want to disable the BGP best path cost community option in a multihomed VPN site and use the internal routes to fully utilize all PE-CE links. The default behavior is that only one PE-CE link is used and the other PE-CE links serve as backup links.
OSPF Sham Link
Although Open Shortest Path First (OSPF) PE-CE connections assume that the only path between two client sites is across the MPLS Layer 3 VPN backbone, backdoor paths between VPN sites might exist. If these sites belong to the same OSPF area, the router always chooses the path over a backdoor link because OSPF prefers intra-area paths to interarea paths. (PE routers advertise OSPF routes that they learned over the VPN backbone as interarea paths.)
To reestablish the desired path selection over the MPLS Layer 3 VPN backbone, you must create an additional OSPF intra-area (logical) link between ingress and egress VRFs on the relevant PE routers. This link is called a sham link. A sham link is required between any two VPN sites that belong to the same OSPF area and share an OSPF backdoor link. If no backdoor link exists between the sites, no sham link is required. When a sham link is configured between PE routers, the PEs can populate the VRF routing table with the OSPF routes learned over the sham link. Because OSPF sees the sham link as an intra-area link between PE routers, an OSPF creates an adjacency and triggers a database exchange (for the particular OSPF process) across the link. The PE router can then flood LSAs between sites from across the MPLS VPN backbone and create intra-area connectivity.
OSPF LSA Throttling
OSPF LSA throttling is enabled by default and allows faster OSPF convergence (in milliseconds). You can control the generation (sending) of LSAs, control the receiving interval, and provide a dynamic mechanism to slow down the frequency of LSA updates in OSPF during times of network instability.
The first LSA is always generated immediately upon an OSPF topology change, and the next LSA generated is controlled by a configured minimum start interval. The subsequent LSAs generated for the same LSA are rate limited until the configured maximum interval is reached. The same LSA is defined as an LSA instance that contains the same LSA ID number, LSA type, and advertising router ID.
If an instance of the same LSA arrives sooner than the configured receive interval, the LSA is dropped.

Note We recommend that you use an arrival interval that is less than or equal to the hold-time interval.
Components of MPLS Layer 3 VPNs
An MPLS-based Layer 3 VPN network has three components:
1. VPN route target communities—A VPN route target community is a list of all members of a Layer 3 VPN community. You must configure the VPN route targets for each Layer 3 VPN community member.
2. Multiprotocol BGP peering of VPN community PE routers—Multiprotocol BGP propagates VRF reachability information to all members of a VPN community. You must configure Multiprotocol BGP peering in all PE routers within a VPN community.
3. MPLS forwarding—MPLS transports all traffic between all VPN community members across a VPN enterprise or service provider network.
A one-to-one relationship does not necessarily exist between customer sites and VPNs. A site can be a member of multiple VPNs. However, a site can associate with only one VRF. A customer-site VRF contains all the routes that are available to the site from the VPNs of which it is a member.
High Availability and ISSU for MPLS Layer 3 VPNs
The Cisco NX-OS architecture and high availability (HA) infrastructure enables feature components to restart and resume operations transparently to other services on the device and on neighboring devices. This process allows for continuous operation and minimal data loss during planned software changes and unplanned software failures.
MPLS 6PE/6VPE supports these Cisco NX-OS HA features:
MPLS 6PE/6VPE supports these Cisco NX-OS HA technologies to allow NSF and stateful HA:
MPLS Layer 3 VPN supports these Cisco NX-OS HA technologies:

Note NSF requires that graceful restart is enabled in BGP and LDP.
BGP has graceful restart extensions for labels that are received from peers and recovers the local labels that are allocated for VPN routes across a BGP restart or for a supervisor switchover. BGP does not support stateful restart but on a supervisor switchover, BGP does a stateless recovery through graceful restart procedures. Cisco NX-OS forces a supervisor switchover if the BGP process fails to restart after two attempts.
The PE-CE protocols are either stateful or use graceful restart for routes that are learned from locally connected CEs. The forwarding plane continues to switch packets both for IPv4 and IPv6 routes as well as MPLS labels during any component restart or supervisor switchover.
Hub-and-Spoke Topology
A hub-and-spoke topology prevents local connectivity between subscribers at the spoke provider edge (PE) routers and ensures that a hub site provides subscriber connectivity. Any sites that connect to the same PE router must forward intersite traffic using the hub site. This topology ensures that the routing at the spoke sites moves from the access-side interface to the network-side interface or from the network-side interface to the access-side interface but never from the access-side interface to the access-side interface. A hub-and-spoke topology allows you to maintain access restrictions between sites.
A hub-and-spoke topology prevents situations where the PE router locally switches the spokes without passing the traffic through the hub site. This topology prevents subscribers from directly connecting to each other.
A hub-and-spoke topology does not require one VRF for each spoke.
Figure 22-2 shows a sample hub-and-spoke topology.
Figure 22-2 Hub-and-Spoke Topology
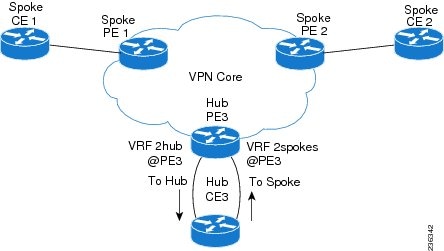
As shown in the figure, a hub-and-spoke topology is typically set up with a hub PE that is configured with two VRFs:
- VRF 2hub with a dedicated link connected to the hub customer edge (CE).
- VRF 2spokes with another dedicated link connected to the hub CE.
Interior Gateway Protocol (IGP) or external BGP (eBGP) sessions are usually set up through the hub PE-CE links. The VRF 2hub imports all the exported route targets from all the spoke PEs. The hub CE learns all routes from the spoke sites and readvertises them back to the VRF 2spoke of the hub PE. The VRF 2spoke exports all these routes to the spoke PEs.
If you use eBGP between the hub PE and hub CE, you must allow duplicate autonomous system (AS) numbers in the path which is normally prohibited. You can configure the router to allow this duplicate AS number at the neighbor of VRF 2spokes of the hub PE and also for VPN address family neighbors at all the spoke PEs. In addition, you must disable the peer AS number check at the hub CE when distributing routes to the neighbor at VRF 2spokes of the hub PE.
Reverse Path Forwarding Check
The unicast Reverse Path Forwarding (uRPF) check ensures that an IP packet that enters a router uses the correct inbound interface. A hub-and-spoke configuration supports uRPF checks on the spoke-side interfaces. Because different virtual routing and forwarding instances (VRFs) are used for downstream and upstream forwarding, the uRPF mechanism ensures that source address checks occur in the downstream VRF.
OSPF Sham-Link Support for MPLS VPN
In a Multiprotocol Label Switching (MPLS) VPN configuration, you can use the Open Shortest Path First (OSPF) protocol to connect customer edge (CE) devices to service provider edge (PE) devices in the VPN backbone. Many customers run OSPF as their intrasite routing protocol, subscribe to a VPN service, and want to exchange routing information between their sites using OSPF (during migration or on a permanent basis) over an MPLS VPN backbone.
The benefits of the OSPF sham-link support for MPLS VPN are as follows:
- Client site connection across the MPLS VPN Backbone—A sham link ensures that OSPF client sites that share a backdoor link can communicate over the MPLS VPN backbone and participate in VPN services.
- Flexible routing in an MPLS VPN configuration—In an MPLS VPN configuration, the OSPF cost tha is configured with a sham link allows you to decide if OSPF client site traffic is routed over a backdoor link or through the VPN backbone.
The figure below shows an example of how VPN client sites that run OSPF can connect over an MPLS VPN backbone.
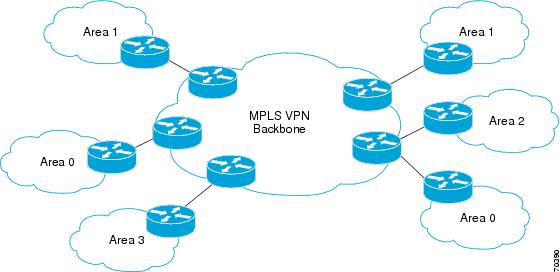
When you use OSPF to connect PE and CE devices, all routing information learned from a VPN site is placed in the VPN routing and forwarding (VRF) instance that is associated with the incoming interface. The PE devices that attach to the VPN use the Border Gateway Protocol (BGP) to distribute VPN routes to each other. A CE device can learn the routes to other sites in the VPN by peering with its attached PE device. The MPLS VPN super backbone provides an additional level of routing hierarchy to interconnect the VPN sites that are running OSPF.
When OSPF routes are propagated over the MPLS VPN backbone, additional information about the prefix in the form of BGP extended communities (route type, domain ID extended communities) is appended to the BGP update. This community information is used by the receiving PE device to decide the type of link-state advertisement (LSA) to be generated when the BGP route is redistributed to the OSPF PE-CE process. In this way, internal OSPF routes that belong to the same VPN and are advertised over the VPN backbone are seen as interarea routes on the remote sites.
Correcting OSPF Backdoor Routing
Although the Open Shortest Path First (OSPF) provider edge-to-customer edge (PE-CE) connections assume that the only path between two client sites is across the Multiprotocol Layer Switching (MPLS) VPN backbone, backdoor paths between VPN sites (shown in gray in the figure below) might exist. If these sites belong to the same OSPF area, the device chooses a path over a backdoor link because OSPF prefers intra-area paths to interarea paths. (PE devices advertise OSPF routes learned over the VPN backbone as interarea paths.) Therefore, routing is performed based on policy.
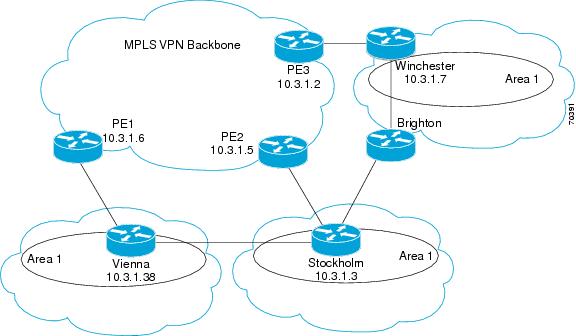
For example, the figure above shows three client sites, each with backdoor links. Because each site runs OSPF within the same Area 1 configuration, all routing between the three sites follows the intra-area path across the backdoor links, rather than over the MPLS VPN backbone.
The following example shows Border Gateway Protocol (BGP) routing table entries for the prefix 10.3.1.7/32 in the PE-1 device in the figure above. This prefix is the loopback interface of the Winchester CE device. As shown in bold in this example, the loopback interface is learned through BGP from PE-2 and PE-3. It is also generated through redistribution into BGP on PE-1.
Within BGP, the locally generated route (10.2.1.38) is considered to be the best route. However, as shown in bold in the next example, the VRF routing table shows that the selected path is learned through OSPF with a next hop of 10.2.1.38, shown in the figure as the Vienna CE device.
This path is selected for the following reasons:
- The OSPF intra-area path is preferred over the interarea path (over the MPLS VPN backbone) that is generated by the PE-1 device.
- OSPF has a lower administrative distance (AD) than internal BGP (BGP running between devices in the same autonomous system).
If the backdoor links between sites are used only for backup and do not participate in the VPN service, the default route selection shown in the preceding example is not acceptable. To reestablish the desired path selection over the MPLS VPN backbone, you must create an additional OSPF intra-area (logical) link between ingress and egress VRFs on the relevant PE devices. This link is called a sham link.
A sham link is required between any two VPN sites that belong to the same OSPF area and share an OSPF backdoor link. If no backdoor link exists between the sites, no sham link is required.
The figure below shows a sample sham link between PE-1 and PE-2. A cost is configured with each sham link and is used to decide whether traffic is sent over the backdoor path or the sham-link path. When a sham link is configured between PE devices, the PEs can populate the VRF routing table with the OSPF routes learned over the sham link.
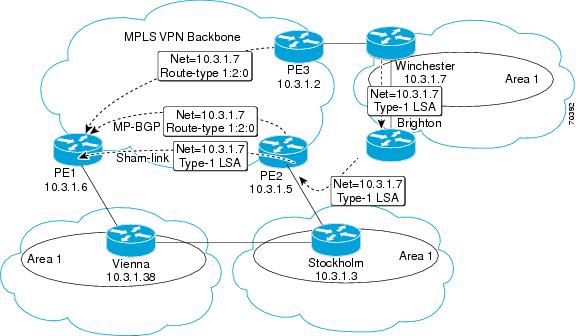
Because the sham link is seen as an intra-area link between PE devices, an OSPF adjacency is created and database exchange (for the particular OSPF process) occurs across the link. The PE device can then flood LSAs between sites from across the MPLS VPN backbone. As a result, intra-area connectivity is created.
Prerequisites for MPLS Layer 3 VPNs
MPLS Layer 3 VPNs has the following prerequisites:
- Ensure that you have configured MPLS and Label Distribution Protocol (LDP) or Resource Reservation Protocol (RSVP) Traffic Engineering (TE) in your network. All routers in the core, including the PE routers, must be able to support MPLS forwarding.
- Ensure that you have installed the correct license for MPLS and any other features you will be using with MPLS.
Guidelines and Limitations for MPLS Layer 3 VPNs
MPLS Layer 3 VPNs have the following configuration guidelines and limitations:
– Enhanced Interior Gateway Protocol (EIGRP) (IPv4)
– Open Shortest Path First (OSPFv2)
– Routing Information Protocol (RIPv2)

Note Cisco NX-OS supports static routes (IPv4 and IPv6) for PE-CE routing.
- Set statements in an import route map are ignored.
- The BGP minimum route advertisement interval (MRAI) value for all iBGP and eBGP sessions is zero and is not configurable.
- In a high scale setup with many BGP routes getting redistributed into EIGRP, modify the EIGRP signal timer to ensure that the EIGRP convergence time is higher than the BGP convergence time. This process allows all the BGP routes to be redistributed into EIGRP, before EIGRP signals convergence.
- For Cisco NX-OS releases before Cisco NX-OS Release 5.2(5), the EIGRP site of origin requires an MPLS license and he MPLS Layer 3 VPN feature is enabled. Beginning with Cisco NX-OS Release 5.2(5), the EIGRP site of origin feature does not require an MPLS license.
OSPF sham-link support for MPLS VPN has the following guideline and limitation:
- When OSPF is used as a protocol between PE and CE devices, the OSPF metric is preserved when routes are advertised over the VPN backbone. The metric is used on the remote PE devices to select the correct route. Do not modify the metric value when OSPF is redistributed to BGP and when BGP is redistributed to OSPF. If you modify the metric value, routing loops might occur.
Default Settings for MPLS Layer 3 VPNs
Table 22-1 lists the default settings for MPLS Layer 3 VPN parameters.
Configuring MPLS Layer 3 VPNs
This section includes the following topics:
- Configuring the Core Network
- Connecting the MPLS VPN Customers
- Configuring Sham-Link for OSPF Support of an MPLS VPN
Assessing the Needs of MPLS Layer 3 VPN Customers
You can identify the core network topology so that it can best serve MPLS Layer 3 VPN customers.
Step 1 Identify the size of the network:
– Identify the following to determine the number of routers and ports you need:
– How many customers do you need to support?
– How many VPNs are needed per customer?
– How many virtual routing and forwarding instances are there for each VPN?
Step 2 Determine which routing protocols you need in the core network.
Step 3 Determine if you need MPLS VPN high availability support.

Note MPLS VPN nonstop forwarding and graceful restart are supported on select routers and Cisco NX-OS releases. You need to make sure that graceful restart for BGP and LDP is enabled.
Step 4 Configure the routing protocols in the core network.

Note See the Cisco Nexus 7000 Series NX-OS Unicast Routing Configuration Guide for configuration steps.
Step 5 Determine if you need BGP load sharing and redundant paths in the MPLS Layer 3 VPN core.

Note See the “Configuring MPLS Layer 3 VPN Load Balancing” section for more information.
Configuring MPLS in the Core
To enable MPLS on all routers in the core, you must configure a label distribution protocol. You can use either of the following as a label distribution protocol:
Configuring Multiprotocol BGP on the PE Routers and Route Reflectors
You can configure multiprotocol BGP connectivity on the PE routers and route reflectors.
DETAILED STEPS
Defining VRFs on the PE Routers to Enable Customer Connectivity
You must create VRFs on the PE routers to enable customer connectivity. You configure route targets to control which IP prefixes are imported into the customer VPN site and which IP prefixes are exported to the BGP network. You can optionally use an import or export route map to provide more fine-grained control over the IP prefixes that are imported into the customer VPN site or exported out of the VPN site. You can use a route map to filter routes that are eligible for import or export in a VRF, based on the route target extended community attributes of the route. The route map might, for example, deny access to selected routes from a community that is on the import route target list.

Note If you are using import maps, you must configure an import statement in order for the import map to take effect. Similarly, you must configure an export statement in order for the export map to take effect. Beginning with Cisco NX-OS Release 5.2(5), however, an export statement is not required in order for the export map to take effect.

Note Beginning with Cisco NX-OS Releases 5.2(7) and 6.1(2), import maps support matching and setting on standard and extended communities. In earlier releases, import maps do not support matching and setting on standard and extended communities. Beginning with Cisco NX-OS Release 5.2(1), export maps support matching and setting on standard and extended communities.
SUMMARY STEPS
6. address-family { ipv4 | ipv6 } unicast
7. route-target { import | export } route-target-ext-community
8. (Optional) maximum routes max-prefix [ threshold value] [ reinstall]
9. (Optional) import [ vrf default max-prefix ] map route-map
DETAILED STEPS
Configuring VRF Interfaces on PE Routers for Each VPN Customer
You can associate a virtual routing and forwarding instance (VRF) with an interface or subinterface on the PE routers.
DETAILED STEPS
Configuring Routing Protocols Between the PE and CE Routers
This section includes the following topics:
- Configuring Static or Directly Connected Routes Between the PE and CE Routers
- Configuring BGP as the Routing Protocol Between the PE and CE Routers
- Configuring RIPv2 Between the PE and CE Routers
- Configuring OSPF Between the PE and CE Routers
- Configuring EIGRP Between the PE and CE Routers
- Configuring PE-CE Redistribution in BGP for the MPLS VPN
Configuring Static or Directly Connected Routes Between the PE and CE Routers
You can configure the PE router for PE-to-CE routing sessions that use static routes.
SUMMARY STEPS
3. { ip | ipv6 } route prefix/mask nexthop
4. address-family { ipv4 | ipv6 } unicast
8. address-family { ipv4 | ipv6 } unicast
9. redistribute static route-map map-tag
10. redistribute direct route-map map-tag
11. (Optional) show { ipv4 | ipv6 } route static vrf vrf-name
DETAILED STEPS
Configuring BGP as the Routing Protocol Between the PE and CE Routers
You can use eBGP to configure the PE router for PE-to-CE routing sessions.
SUMMARY STEPS
5. neighbor ip-address remote-as as-number
6. address-family { ipv4 | ipv6 } unicast
DETAILED STEPS
Configuring RIPv2 Between the PE and CE Routers
You can use RIP to configure the PE router for PE-to-CE routing sessions.
SUMMARY STEPS
5. address-family ipv4 unicast
6. redistribute { bgp as | direct | { eigrp | ospf | rip } instance-tag | static } route-map map-name
DETAILED STEPS
Configuring OSPF Between the PE and CE Routers
You can use OSPFv2 to configure the PE router for PE-to-CE routing sessions. You can optionally create an OSPF sham link if you have OSPF back door links that are not part of the MPLS network.
SUMMARY STEPS
5. (Optional) area area-id sham-link source-address destination-address
6. address-family { ipv4 | ipv6 } unicast
7. redistribute { bgp as | direct | { eigrp | ospf | rip } instance-tag | static } route-map map-name
DETAILED STEPS
Configuring EIGRP Between the PE and CE Routers
You can configure the PE router to use Enhanced Interior Gateway Routing Protocol (EIGRP) between the PE and CE routers to transparently connect EIGRP customer networks through an MPLS-enabled BGP core network so that EIGRP routes are redistributed through the VPN across the BGP network as internal BGP (iBGP) routes.
Prerequisites
You must configure BGP in the network core.
Ensure that you are in the correct VDC (or use the switchto vdc command).
SUMMARY STEPS
5. (Optional) address-family ipv4 unicast
6. redistribute bgp as-number route-map map-name
7. (Optional) autonomous-system as-number
DETAILED STEPS
Configuring PE-CE Redistribution in BGP for the MPLS VPN
You must configure BGP to distribute the PE-CE routing protocol on every PE router that provides MPLS Layer 3 VPN services if the PE-CE protocol is not BGP.
SUMMARY STEPS
4. (Optional) router-id ip-address
5. neighbor ip-address remote-as as-number
6. update-source loopback [ 0 | 1 ]
7. address-family { vpnv4 | vpnv6 }
10. address-family { ipv4 | ipv6 } unicast
11. redistribute { direct | { eigrp | ospf | rip } instance-tag | static } route-map map-name
12. (Optional) show bgp { ipv4 | ipv6 } unicast vrf vrf-name
DETAILED STEPS
DETAILED STEPS
Configuring eBGP on the Hub PE Router
You can use eBGP to configure PE-to-CE hub routing sessions.

Note If all CE sites are using the same BGP AS number, you must perform the following tasks:
DETAILED STEPS
Configuring eBGP on the Hub CE Router
You can use eBGP to configure PE-to-CE hub routing sessions.

Note If all CE sites are using the same BGP AS number, you must perform the following tasks:
- Configure either the as-override command at the PE (hub) or the allowas-in command at the receiving CE router.
- Configure the disable-peer-as-check command at the CE router.
- To advertise BGP routes learned from one ASN back to the same ASN, configure the disable-peer-as-check command at the PE router to prevent loopback.
DETAILED STEPS
Configuring VRFs on the Spoke PE Router
You can configure hub and spoke VRFs on the spoke PE router.
DETAILED STEPS
Configuring eBGP on the Spoke PE Router
You can use eBGP to configure PE spoke routing sessions.

Note If all CE sites are using the same BGP AS number, you must perform the following tasks:
DETAILED STEPS
Preventing Loops
You can configure the site of origin and ASN controls to prevent routing loops within a VPN.
Because CEs usually share the same ASN, to advertise BGP routes learned from one ASN back to the same ASN, the neighbor onfiguration disable-peer-as-check command is required. In addition, to allow BGP routes with the same ASN to be received at a CE, configure either the neighbor configuration as-override command or the a llowas-in command at the PE.
DETAILED STEPS
Before You Begin
– Create an OSPF routing process.
– Specify the range of IP addresses to be associated with the routing process.
– Assign area IDs to be associated with the range of IP addresses.
- Before you create a sham link between PE devices in an MPLS VPN, you must configure a separate /32 address on the remote PE so that OSPF packets can be sent over the VPN backbone to the remote end of the sham link. The /32 address must meet the following criteria:

Note You can use the /32 address for other sham links.
SUMMARY STEPS
7. area area-id sham-link source-address destination-address
9. address-family { ipv4 | ipv6 } unicast
10. redistribute { bgp as | direct | { eigrp | ospf | rip } instance-tag | static } route-map map-name
DETAILED STEPS
Verifying the MPLS Layer 3 VPN Configuration
To display the MPLS Layer 3 VPN configuration, perform one of the following tasks:
For detailed information about the fields in the output from these commands, see the Cisco NX-OS MPLS Command Reference .
Configuration Examples for MPLS Layer 3 VPNs
This section uses the following sample MPLS network shown in Figure 22-3.
Figure 22-3 Sample MPLS Layer3 Network
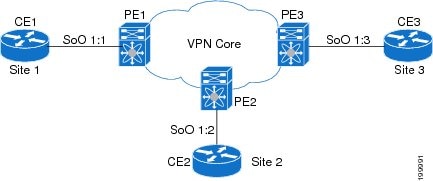
- Example: MPLS Layer 3 VPN Using BGP
- Example: MPLS Layer 3 VPN Using RIP
- Example: MPLS Layer 3 VPN Using Static or Direct Routes
- Example: MPLS Layer 3 VPN Using OSPF
- Example: MPLS Layer 3 VPN Using EIGRP
- Example: MPLS 6VPE Using BGP
- Example: Hub-and-Spoke Topology
- Example: OSPF Sham-Link Support for an MPLS VPN

Note All examples show the basic configuration required for the PE router and the CE router.
Example: MPLS Layer 3 VPN Using BGP
The following example shows how to configure an MPLS Layer 3 VPN using BGP:
Example: MPLS Layer 3 VPN Using RIP
The following example shows how to configure an MPLS Layer 3 VPN using RIP:
Example: MPLS Layer 3 VPN Using Static or Direct Routes
The following example shows how to configure an MPLS Layer 3 VPN using static or direct routes:
Example: MPLS Layer 3 VPN Using OSPF
The following example shows how to configure a MPLS Layer 3 VPN using OSPF:
Example: MPLS Layer 3 VPN Using EIGRP
The following example shows how to configure a MPLS Layer3 VPN using OSPF:
Example: Hub-and-Spoke Topology
The following example shows how to configure a hub-and-spoke configuration for an IPv4 MPLS network with eBGP configured between the hub PE3 and hub CE3 routers. It uses the sample hub-and-spoke topology shown in Figure 22-2.
Example: OSPF Sham-Link Support for an MPLS VPN
The example in this section shows how to use a sham link to affect only the OSPF intra-area path selection of the PE and CE devices. The PE device also uses the information received from the multiprotocol Border Gateway Protocol (MP-BGP) to set the outgoing label stack of incoming packets and to decide the egress PE device to which the packets must be label switched.
The figure below shows a sample MPLS VPN topology in which a sham-link configuration is necessary. A VPN client has three sites, each with a backdoor link. Two sham links have been configured, one between PE-1 and PE-2, and another between PE-2 and PE-3. A sham link between PE-1 and PE-3 is not necessary in this configuration because the Vienna and Winchester sites do not share a backdoor link.
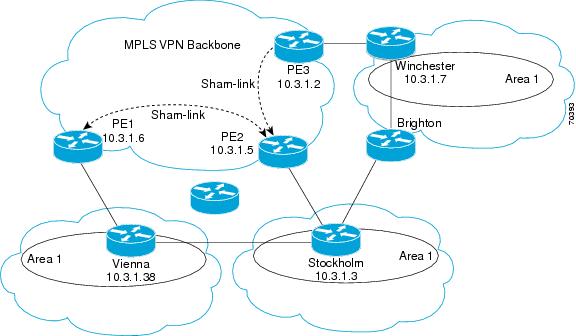
The following example shows how to configure sham links and a demand circuit:
The following example show how to display the configuration values for demand circuit in sham links for VRF value class1:
The following example show how to display the configuration values for a demand circuit in sham links for all VRFs:
Additional References for MPLS Layer 3 VPNs
For additional information related to implementing MPLS Layer 3 VPNs, see the following sections:
Feature History for MPLS Layer 3 VPNs
Table 22-2 lists the release history for this feature.
 Feedback
Feedback