- New and Changed Information
- Preface
-
- Configuring the MPLS Label Distribution Protocol
- Configuring MPLS LDP Autoconfiguration
- Configuring MPLS LDP Session Protection
- Configuring MPLS LDP IGP Synchronization
- Configuring MPLS LDP Lossless MD5 Session Authentication
- Configuring MPLS LDP Label Filtering
- Configuring MPLS LDP Static Label Binding
- Configuring MPLS LDP Graceful Restart
-
- Configuring Basic MPLS TE
- Configuring Automatic Bandwidth Adjustment for MPLS TE Tunnels
- Configuring MPLS TE RSVP
- Configuring the Path Selection Metric for MPLS TE Tunnels
- Configuring LSP Attributes for MPLS TE
- Configuring MPLS TE Verbatim Paths
- Configuring MPLS TE Forwarding Adjacency
- Configuring MPLS TE Class-Based Tunnel Selection
- Configuring MPLS TE Path Protection
- Configuring MPLS TE Fast Reroute Link and Node Protection
-
- Configuring Any Transport over MPLS
- Configuring Any Transport over MPLS Pseudowire Provisioning
- Configuring Ethernet over MPLS
- Configuring EoMPLS Layer 2 VPN Graceful Restart
- Configuring Virtual Private LAN Service
- Configuring Layer 2 VPN Pseudowire Redundancy
- Configuring Layer 2 VPN VPLS Dual-Homing with a vPC
- Configuration Limits for Cisco NX-OS MPLS
- RFCs
Cisco Nexus 7000 Series NX-OS MPLS Configuration Guide
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- June 4, 2014
Chapter: Configuring MPLS over GRE
- Finding Feature Information
- Information About Configuring MPLS over GRE
- Licensing Requirements for MPLS on GRE
- Prerequisites for Configuring MPLS over GRE
- Guidelines and Limitations for Configuring MPLS over GRE
- Configuring MPLS over GRE
- Verifying Configuring MPLS over GRE
- Configuration Examples for Configuring MPLS over GRE
- Additional References for Configuring MPLS over GRE
- Feature History for Layer 3 VPN Configuring MPLS over GRE
Configuring MPLS over GRE
This chapter describes how to configure a Virtual Private Network (VPN) generic routing encapsulation (GRE) tunnel for moving Multiprotocol Label Switching (MPLS) packets over a non-MPLS network.
This chapter includes the following sections:
- Finding Feature Information
- Information About Configuring MPLS over GRE
- Licensing Requirements for MPLS on GRE
- Prerequisites for Configuring MPLS over GRE
- Guidelines and Limitations for Configuring MPLS over GRE
- Configuring MPLS over GRE
- Verifying Configuring MPLS over GRE
- Configuration Examples for Configuring MPLS over GRE
- Additional References for Configuring MPLS over GRE
- Feature History for Layer 3 VPN Configuring MPLS over GRE
Finding Feature Information
Your software release might not support all the features documented in this module. For the latest caveats and feature information, see the Bug Search Tool at https://tools.cisco.com/bugsearch/ and the release notes for your software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the “New and Changed Information” chapter or the Feature History table below.
Information About Configuring MPLS over GRE
This section includes the following topics:
PE-to-PE GRE Tunneling
A provider-edge-to-provider-edge (PE-to-PE) tunnel provides a scalable way to connect multiple customer networks across a non-MPLS network. With this configuration, traffic that is destined to multiple customer networks is multiplexed through a single generic routing encapsulation (GRE) tunnel. A similar nonscalable alternative is to connect each customer network through separate GRE tunnels (for example, connecting one customer network to each GRE tunnel).
The PE devices assign virtual routing and forwarding (VRF) numbers to the customer edge (CE) devices on each side of the non-MPLS network. The PE devices use routing protocols such as Border Gateway Protocol (BGP), Open Shortest Path First (OSPF), or Routing Information Protocol (RIP) to learn about the IP networks behind the CE devices. The routes to the IP networks behind the CE devices are stored in the VRF routing table of the associated CE device.
The PE device on one side of the non-MPLS network uses routing protocols (that operate within the non-MPLS network) to learn about the PE device on the other side of the non-MPLS network. The learned routes that are established between the PE devices are then stored in the main or default routing table. PE device on the other side of the network uses BGP to learn about the routes that are associated with the customer networks that are associated with the PE devices. These learned routes are not known to the non-MPLS network.
The following figure shows BGP defining a route to the BGP neighbor (the opposing PE device) through the GRE tunnel that spans the non-MPLS network. Because routes that are learned by the BGP neighbor include the GRE tunnel next hop, all customer network traffic is sent using the GRE tunnel.
Figure 25-1 PE-to-PE GRE Tunnel
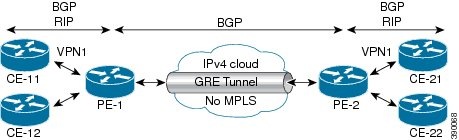
P-to-PE Tunneling
As shown in the figure below, the provider-to-provider-edge (P-to-PE) tunneling configuration provides a way to connect a PE device (P1) to a Multiprotocol Label Switching (MPLS) segment (PE-2) across a non-MPLS network. In this configuration, MPLS traffic that is destined to the other side of the non-MPLS network is sent through a single generic routing encapsulation (GRE) tunnel.
Figure 25-2 P-to-PE GRE Tunnel
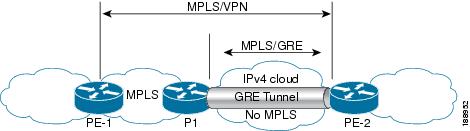
P-to-P Tunneling
As shown in the figure below, the provider-to-provider (P-to-P) configuration provides a method of connecting two Multiprotocol Label Switching (MPLS) segments (P1 to P2) across a non-MPLS network. In this configuration, MPLS traffic that is destined to the other side of the non-MPLS network is sent through a single generic routing encapsulation (GRE) tunnel.
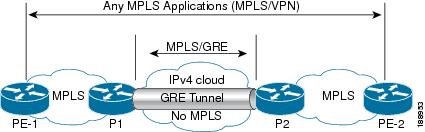
Licensing Requirements for MPLS on GRE
The following table shows the licensing requirements for this feature:
|
|
|
|---|---|
MPLS Layer 3 and Layer 2 VPNs require an MPLS license. For a complete explanation of the NX-OS licensing scheme, see the Cisco NX-OS Licensing Guide. |
Prerequisites for Configuring MPLS over GRE
Guidelines and Limitations for Configuring MPLS over GRE
Layer 3 VPN MPLS over GRE does not support the following:
- Quality of service (QoS) service policies that are configured on the tunnel interface. QoS service policies are supported on the physical interface or subinterface.
- GRE options—Sequencing, checksum, and source route.
- IPv6 generic routing encapsulation (GRE).
- Advance features such as Carrier Supporting Carrier (CSC) and Interautonomous System (Inter-AS).
- GRE-based Layer 3 VPN does not interwork with MPLS or IP VPNs.
- GRE tunnel is supported only as a core link (PE-PE, PE-P, P-P, P-PE). A Provide-Edge to Customer-Edge (PE-CE) link is not supported.
- IPv6 VPN forwarding using GRE tunnels.
- Static route mapping to GRE tunnels.
- Bidirectional Forwarding Detection (BFD) with GRE tunnels.
Layer 2 VPLS over GRE has the following configuration guidelines and limitations:
- A VPLS instance must be configured on each Provider Edge (PE) device.
- Load balancing at the Virtual Private LAN Service (VPLS) ingress or at the core is not supported for flood or multicast traffic.
- Virtual circuit connection verification (VCCV) over flow aware transport of MPLS pseudowires (FAT PW) is not supported. The Interior Gateway Protocol (IGP) load balancing for VCCV is also unsupported.
Ethernet over MPLS over GRE has the following configuration guidelines and limitations:
- Multiple point-to-point tunnels can saturate the physical link with routing information if bandwidth is not configured correctly on a tunnel interface.
- A tunnel may have a recursive routing problem if routing is not configured accurately. The best path to a tunnel destination through the tunnel itself; therefore recursive routing causes the tunnel interface to flap. To avoid recursive routing problems, keep control-plane routing separate from tunnel routing by using the following methods:
–![]() Use a different autonomous system number or tag.
Use a different autonomous system number or tag.
–![]() Use a different routing protocol.
Use a different routing protocol.
–![]() Ensure that static routes are used to override the first hop (watch for routing loops).
Ensure that static routes are used to override the first hop (watch for routing loops).
%TUN-RECURDOWN Interface Tunnel 0 temporarily disabled due to recursive routing
Configuring MPLS over GRE
This section includes the following topics:
Configuring Layer 3 VPN Configuring MPLS over GRE
To configure a generic routing encapsulation (GRE) tunnel and create a virtual point-to-point link across the non-MPLS network, you must perform this task on the devices located at both ends of the GRE tunnel.
SUMMARY STEPS
4.![]() interface tunnel tunnel-number
interface tunnel tunnel-number
5.![]() ip address ip-address ip-address-mask
ip address ip-address ip-address-mask
7.![]() tunnel source source-address
tunnel source source-address
DETAILED STEPS
Configuring Layer 2 VPN Configuring MPLS over GRE
Restrictions
You cannot have two tunnels using the same encapsulation mode with exactly the same source and destination addresses. The work around is to create a loopback interface and source packets from the loopback interface. This restriction is applicable only for generic routing encapsulation (GRE) tunnels.
SUMMARY STEPS
9.![]() tunnel source { ip-address | type / number }
tunnel source { ip-address | type / number }
10.![]() tunnel destination { hostname | ip-address }
tunnel destination { hostname | ip-address }
11.![]() mpls ip { propagate-ttl | ttl-expiration pop [ labels ]}
mpls ip { propagate-ttl | ttl-expiration pop [ labels ]}
13.![]() ip route prefix mask interface-type interface-number
ip route prefix mask interface-type interface-number
14.![]() ip route prefix mask interface-type interface-number
ip route prefix mask interface-type interface-number
15.![]() [ no ] l2vpn vfi context context-name
[ no ] l2vpn vfi context context-name
16.![]() (Optional) description description
(Optional) description description
18.![]() member peer ip-address [ vc-id ] encapsulation mpls
member peer ip-address [ vc-id ] encapsulation mpls
DETAILED STEPS
Verifying Configuring MPLS over GRE
To verify IP tunnel configuration information, perform one of the following tasks:
Configuration Examples for Configuring MPLS over GRE
This section includes the following topics:
- Example: Configuring a GRE Tunnel That Spans a Non-MPLS Network
- Example: MPLS Configuration with PE-to-PE GRE Tunnel
- Example: MPLS Configuration with P-to-PE GRE Tunnel
Example: Configuring a GRE Tunnel That Spans a Non-MPLS Network
The following example shows how to configure a generic routing encapsulation (GRE) tunnel configuration that spans a non-MPLS network. This example shows the tunnel configuration on the provider edge (PE) devices (PE1 and PE2) located at both ends of the tunnel:
Example: MPLS Configuration with PE-to-PE GRE Tunnel
The following example is for a basic PE-to-PE tunneling configuration that uses a generic routing encapsulation (GRE) tunnel to span a non-MPLS network:
Example: MPLS Configuration with P-to-PE GRE Tunnel
The following example is for a basic P-to- PE tunneling configuration that uses a generic routing encapsulation (GRE) tunnel to span a non-MPLS network:
Additional References for Configuring MPLS over GRE
This section includes the following topics:
Related Documents
|
|
|
|---|---|
MIBs
|
|
|
|---|---|
To locate and download MIBs, go to the following URL: http://www.cisco.com/dc-os/mibs |
Feature History for Layer 3 VPN Configuring MPLS over GRE
Table 25-1 lists the release history for this feature.
|
|
|
|
|---|---|---|
The MPLS over GRE feature provides a mechanism for tunneling Multiprotocol Label Switching (MPLS) packets over a non-MPLS network. |
 Feedback
Feedback