Configuring Static NAT
This chapter includes the following sections:
- Information About Static NAT
- Licensing Requirements for Static NAT
- Guidelines and Limitations for Static NAT
- Configuring Static NAT
- Verifying the Static NAT Configuration
- Configuration Example for Static NAT and PAT
Information About Static NAT
Static Network Address Translation (NAT) allows the user to configure one-to-one translations of the inside local addresses to the outside global addresses. It allows both IP addresses and port number translations from the inside to the outside traffic and the outside to the inside traffic. The Cisco Nexus device supports Hitless NAT, which means that you can add or remove a NAT translation in the NAT configuration without affecting the existing NAT traffic flows.
Static NAT creates a fixed translation of private addresses to public addresses. Because static NAT assigns addresses on a one-to-one basis, you need an equal number of public addresses as private addresses. Because the public address is the same for each consecutive connection with static NAT, and a persistent translation rule exists, static NAT enables hosts on the destination network to initiate traffic to a translated host if an access list exists that allows it .
With dynamic NAT and Port Address Translation (PAT), each host uses a different address or port for each subsequent translation. The main difference between dynamic NAT and static NAT is that static NAT allows a remote host to initiate a connection to a translated host if an access list exists that allows it, while dynamic NAT does not.
The figure shows a typical static NAT scenario. The translation is always active so both translated and remote hosts can originate connections, and the mapped address is statically assigned by the static command.
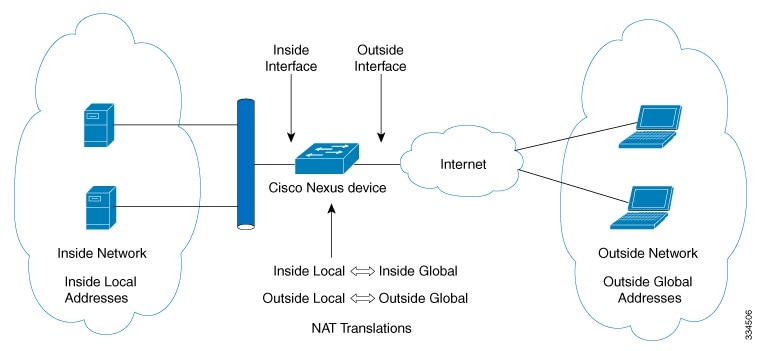
- NAT inside interface—The Layer 3 interface that faces the private network.
- NAT outside interface—The Layer 3 interface that faces the public network.
- Local address—Any address that appears on the inside (private) portion of the network.
- Global address—Any address that appears on the outside (public) portion of the network.
- Legitimate IP address—An address that is assigned by the Network Information Center (NIC) or service provider.
- Inside local address—The IP address assigned to a host on the inside network. This address does not need to be a legitimate IP address.
- Outside local address—The IP address of an outside host as it appears to the inside network. It does not have to be a legitimate address, because it is allocated from an address space that can be routed on the inside network.
- Inside global address—A legitimate IP address that represents one or more inside local IP addresses to the outside world.
- Outside global address—The IP address that the host owner assigns to a host on the outside network. The address is a legitimate address that is allocated from an address or network space that can be routed.
Licensing Requirements for Static NAT
This table shows the licensing requirements for static NAT.
| Product |
License Requirement |
||
|---|---|---|---|
| Cisco NX-OS |
Static NAT requires a LAN Base license and an Algo Boost license. For a complete explanation of the Cisco NX-OS licensing scheme and how to obtain and apply licenses, see the Cisco NX-OS Licensing Guide.
|
Guidelines and Limitations for Static NAT
Static NAT has the following configuration guidelines and limitations:
- Static NAT supports up to 1000 translations.
- The Cisco Nexus device supports NAT on the following interface types:
- NAT is supported on the default Virtual Routing and Forwarding (VRF) table only.
- NAT is supported for IPv4 Unicast only.
-
The Cisco Nexus device does not support the following:
- Software translation. All translations are done in the hardware.
- Application layer translation. Layer 4 and other embedded IPs are not translated, including FTP, ICMP failures, IPSec, and HTTPs.
- NAT and VLAN Access Control Lists (VACLs) that are configured on an interface at the same time.
- PAT translation of fragmented IP packets.
- NAT translation on software forwarded packets. For example, packets with IP-options are not NAT translated.
- Egress ACLs are applied to the original packets and not the NAT translated packets.
- By default, NAT can go up to 127 translations with 256 TCAM entries. If you need more NAT translations, you need to reduce the TCAM region allocation in other areas and then increase the NAT TCAM region using the hardware profile tcam region nat command.
- HSRP and VRRP are not supported on a NAT interface.
- Warp mode latency performance is not supported on packets coming from the outside to the inside domain.
- If an IP address is used for Static NAT or PAT translations, it cannot be used for any other purpose. For example, it cannot be assigned to an interface.
- For Static NAT, the outside global IP address should be different from the outside interface IP address.
- NAT statistics are not available.
- When configuring a large number of translations (more than 100), it is faster to configure the translations before configuring the NAT interfaces.
Configuring Static NAT
Enabling Static NAT
Configuring Static NAT on an Interface
This example shows how to configure an interface with static NAT from the inside:
switch# configure terminal switch(config)# interface ethernet 1/4 switch(config-if)# ip nat inside
Enabling Static NAT for an Inside Source Address
For inside source translation, the traffic flows from inside interface to the outside interface. NAT translates the inside local IP address to the inside global IP address. On the return traffic, the destination inside global IP address gets translated back to the inside local IP address.
 Note |
When the Cisco Nexus device is configured to translate an inside source IP address (Src:ip1) to an outside source IP address (newSrc:ip2), the Cisco Nexus device implicitly adds a translation for an outside destination IP address (Dst: ip2) to an inside destination IP address (newDst: ip1). |
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# ip nat inside source static local-ip-address global-ip-address [group group-id] | Configures static NAT to translate the inside global address to the inside local address or to translate the opposite (the inside local traffic to the inside global traffic). |
| Step 3 | switch(config)# copy running-config startup-config | (Optional) Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example shows how to configure static NAT for an inside source address:
switch# configure terminal switch(config)# ip nat inside source static 1.1.1.1 5.5.5.5 switch(config)# copy running-config startup-config
Enabling Static NAT for an Outside Source Address
For outside source translation, the traffic flows from the outside interface to the inside interface. NAT translates the outside global IP address to the outside local IP address. On the return traffic, the destination outside local IP address gets translated back to outside global IP address.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# ip nat outside source static global-ip-address local-ip-address [group group-id] [add-route] | Configures static NAT to translate the outside global address to the outside local address or to translate the opposite (the outside local traffic to the outside global traffic). |
| Step 3 | switch(config)# copy running-config startup-config | (Optional) Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example show how to configure static NAT for an outside source address:
switch# configure terminal switch(config)# ip nat outside source static 2.2.2.2 6.6.6.6 switch(config)# copy running-config startup-config
Configuring Static PAT for an Inside Source Address
You can map services to specific inside hosts using Port Address Translation (PAT).
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# ip nat inside source static {inside-local-address outside-local-address | {tcp| udp} inside-local-address {local-tcp-port | local-udp-port} inside-global-address {global-tcp-port | global-udp-port}} group group-id | Maps static NAT to an inside local port to an inside global port. |
| Step 3 | switch(config)# copy running-config startup-config | (Optional) Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example shows how to map UDP services to a specific inside source address and UDP port:
switch# configure terminal switch(config)# ip nat inside source static udp 20.1.9.2 63 35.48.35.48 130 switch(config)# copy running-config startup-config
Configuring Static PAT for an Outside Source Address
You can map services to specific outside hosts using Port Address Translation (PAT).
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# ip nat outside source static {outside-global-address outside-local-address | {tcp | udp} outside-global-address {global-tcp-port | global-udp-port} outside-local-address {global-tcp-port | global-udp-port}}group group-id add-route | Maps static NAT to an outside global port to an outside local port. |
| Step 3 | switch(config)# copy running-config startup-config | (Optional) Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example shows how to map TCP services to a specific outside source address and TCP port:
switch# configure terminal switch(config)# ip nat outside source static tcp 20.1.9.2 63 35.48.35.48 130 switch(config)# copy running-config startup-config
Verifying the Static NAT Configuration
To display the static NAT configuration, perform this task:
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# show ip nat translations | Shows the translations for the inside global, inside local, outside local, and outside global IP addresses. |
This example shows how to display the static NAT configuration:
switch# show ip nat translations Pro Inside global Inside local Outside local Outside global any --- --- 20.4.4.40 220.2.2.20 tcp --- --- 23.1.1.133:333 210.3.3.33:555 any 160.200.1.140 10.1.1.40 --- --- any 160.200.1.140 10.1.1.40 20.4.4.40 220.2.2.20 tcp 172.9.9.142:777 12.2.2.42:444 --- --- tcp 172.9.9.142:777 12.2.2.42:444 23.1.1.133:333 210.3.3.33:555
Configuration Example for Static NAT and PAT
This example shows the configuration for static NAT:
ip nat inside source static 103.1.1.1 11.3.1.1 ip nat inside source static 139.1.1.1 11.39.1.1 ip nat inside source static 141.1.1.1 11.41.1.1 ip nat inside source static 149.1.1.1 95.1.1.1 ip nat inside source static 149.2.1.1 96.1.1.1 ip nat outside source static 95.3.1.1 95.4.1.1 ip nat outside source static 96.3.1.1 96.4.1.1 ip nat outside source static 102.1.2.1 51.1.2.1 ip nat outside source static 104.1.1.1 51.3.1.1 ip nat outside source static 140.1.1.1 51.40.1.1
ip nat inside source static tcp 10.11.1.1 1 210.11.1.1 101 ip nat inside source static tcp 10.11.1.1 2 210.11.1.1 201 ip nat inside source static tcp 10.11.1.1 3 210.11.1.1 301 ip nat inside source static tcp 10.11.1.1 4 210.11.1.1 401 ip nat inside source static tcp 10.11.1.1 5 210.11.1.1 501 ip nat inside source static tcp 10.11.1.1 6 210.11.1.1 601 ip nat inside source static tcp 10.11.1.1 7 210.11.1.1 701 ip nat inside source static tcp 10.11.1.1 8 210.11.1.1 801 ip nat inside source static tcp 10.11.1.1 9 210.11.1.1 901 ip nat inside source static tcp 10.11.1.1 10 210.11.1.1 1001 ip nat inside source static tcp 10.11.1.1 11 210.11.1.1 1101 ip nat inside source static tcp 10.11.1.1 12 210.11.1.1 1201
 Feedback
Feedback