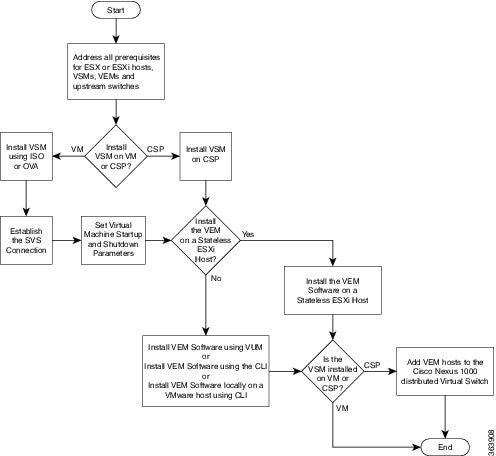
| Step 1 |
From the vSphere
Client, choose
File > Deploy OVF
Template .
|
| Step 2 |
In the
Source screen, specify the location of the OVA file
and click
Next.
The OVF Template
Details screen opens displaying product information, including the size of the
file and the size of the VM disk.
|
| Step 3 |
Click
Next.
|
| Step 4 |
Read the Cisco
Nexus 1000V License Agreement.
|
| Step 5 |
Click
Accept and then click
Next.
|
| Step 6 |
In the
Name: field, add the VSM name, choose the folder
location within the inventory where it will reside, and click
Next.
The name for the
VSM must be unique within the inventory folder and less than 80 characters.
|
| Step 7 |
From the
Configuration drop-down list, choose
Nexus
1000V Installer.
This choice
configures the primary VSM using the GUI setup dialog.
|
| Step 8 |
If you want
to configure a secondary VSM, select
Nexus
1000V Secondary.
|
| Step 9 |
Click
Next.
|
| Step 10 |
Choose the data
center or cluster on which to install the VSM.
|
| Step 11 |
Click
Next.
|
| Step 12 |
Choose the
datastore in which to store the file if one is available.
On this page,
you choose from datastores already configured on the destination cluster or
host. The virtual machine configuration file and virtual disk files are stored
on the datastore. Choose a datastore large enough to accommodate the virtual
machine and all of its virtual disk files.
|
| Step 13 |
Click
Next.
|
| Step 14 |
Choose one of
the following disk formats for storing virtual machine virtual disks, and click
Next.
|
Format
|
Description
|
|
Thick
Provision Lazy Zeroed
|
Creates a virtual disk in a default thick format. In this format, the space
required for the virtual disk is allocated when the disk is created. The data
remaining on the physical device is not erased during creation. The data is
zeroed out on demand at a later time on first write from the virtual machine.
Virtual machines do not read stale data from the physical device.
|
|
Thick
Provision Eager Zeroed
|
Creates a virtual disk that supports clustering features such as Fault
Tolerance. In this format, the space required for the virtual disk is allocated
when the disk is created. The data remaining on the physical device is zeroed
out when the virtual disk is created. It might take longer to create virtual
disks in this format than to create other types of disks.
|
|
Thin
Provision
|
Creates a virtual disk in thin provision format. This format is useful for
saving storage space. In this format, storage blocks are allocated and zeroed
out when they are first accessed.
Thin provisioning is the fastest method to create a virtual disk because it
creates a disk with just the header information. It does not allocate or zero
out storage blocks. If the thin disk needs more space later, it can grow to its
maximum capacity and occupy the entire datastore space provisioned to it.
|
|
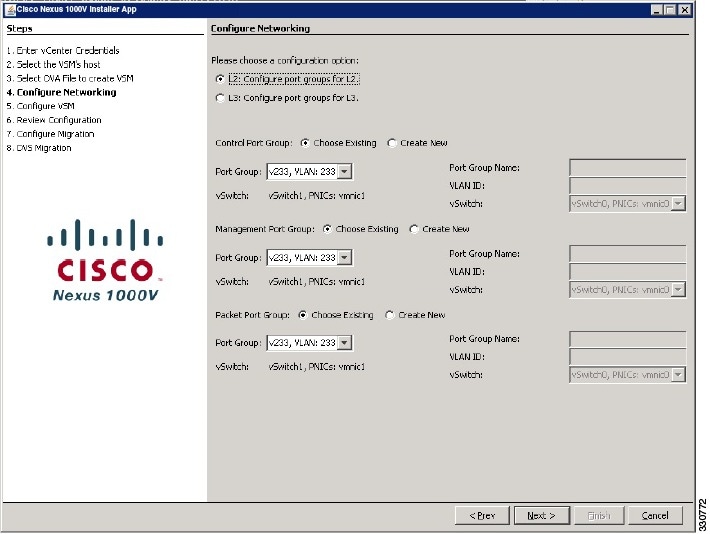
| Step 15 |
In the
Network
Mapping screen, choose the networks (the control, management, and
packet port groups) that are present in your inventory.
|
| Step 16 |
Click
Next
|
| Step 17 |
Do one of the
following:
-
If you are
installing software on a primary VSM, specify the following properties for your
primary VSM:
-
If you are
installing software on a secondary VSM, specify only the following properties
for your secondary VSM (all other properties are acquired on synchronization
with the primary VSM), and then click Next:
|
| Step 18 |
Click
Next.
|
| Step 19 |
In the
Ready
to Complete screen, if the configuration is correct, click
Finish.
A status bar
displays as the VM installation progresses.
|
| Step 20 |
Click
Close.
You have
completed installing the
Cisco Nexus 1000V
software.
|
| Step 21 |
Right-click
the VSM and choose
Open
Console.
|
| Step 22 |
Click the
green
arrow to power on the VSM.
|
| Step 23 |
Enter the
following commands at the VSM prompt.
switch# configure terminal
switch(config)# setup
|
| Step 24 |
Enter the HA
role.
If you do not
specify a role, standalone is assigned by default.
This example
shows the HA role as primary.
Enter HA role[standalone/primary/secondary]: primary
[#########################################] 100%
---- Basic System Configuration Dialog ----
This setup utility will guide you through the basic configuration of
the system. Setup configures only enough connectivity for management
of the system.
*Note: setup is mainly used for configuring the system initially,
when no configuration is present. So setup always assumes system
defaults and not the current system configuration values.
Press Enter at anytime to skip a dialog. Use ctrl-c at anytime
to skip the remaining dialogs.
Would you like to enter the basic configuration dialog (yes/no):
|
| Step 25 |
Do one of the
following:
-
If you are
setting up the primary/active VSM, go to Step 18.
-
If you are
setting up the secondary/standby VSM, then continue with the next step.
|
| Step 26 |
If you have
set up the VSM virtual machine (VM) to boot from the CD-ROM, and are installing
the secondary VSM from the ISO image attached to your CD-ROM, remove the
virtual CD-ROM now so that the VSM does not boot from the CD.
This step is
necessary if you have set up the VSM VM to boot from the CD-ROM before the hard
drive.
|
| Step 27 |
If you are
setting up the secondary or standby VSM, do the following:
-
Enter the
HA role at the following prompt:
Enter HA role[standalone/primary/secondary]:
-
Enter
yes at the following prompt about rebooting the VSM:
Setting HA role to secondary will cause a system reboot. Are you sure (yes/no) ? :
-
Enter the
domain ID at the following prompt:
Enter the domain id<1-1023>:
The secondary
VSM VM is rebooted and brought up in standby mode. The password on the
secondary VSM is synchronized with the password on the active/primary VSM. Any
configuration made on the active/primary VSM is now automatically synchronized
with the standby.
This example
shows the system rebooting when the HA role is set to secondary.
Enter HA role[standalone/primary/secondary]: secondary
Setting HA role to secondary will cause a system reboot. Are you sure (yes/no) ? : y
Enter the domain id<1-1023>: 1020
[########################################] 100%
HA mode set to secondary. Rebooting now...
You have
completed this procedure for the secondary VSM.
|
| Step 28 |
Enter
yes to enter the basic configuration dialog.
Would you like to enter the
basic configuration dialog (yes/no):
yes
|
| Step 29 |
Enter
no to create another Login account.
Create another login account (yes/no) [n]: no
|
| Step 30 |
Enter
no to configure a read-only SNMP community string.
Configure read-only SNMP community string (yes/no) [n]: no
|
| Step 31 |
Enter
no to configure a read-write SNMP community string.
Configure read-write SNMP community string (yes/no) [n]: no
|
| Step 32 |
Enter a name
for the switch.
Enter the switch name: n1000v
|
| Step 33 |
Enter
yes to configure out-of-band management and then
enter the mgmt0 IPv4 address and subnet mask.
Continue with Out-of-band (mgmt0) management configuration? [yes/no] [y]: yes
Mgmt0 IPv4 address: 172.28.15.152
Mgmt0 IPv4 netmask: 255.255.255.0
|
| Step 34 |
Enter
yes to configure the default gateway.
Configure the default-gateway: (yes/no) [y]: yes
IPv4 address of the default gateway : 172.23.233.1
|
| Step 35 |
Enter
no to configure advanced IP options.
Configure Advanced IP options (yes/no)? [n]: no
|
| Step 36 |
Enter
yes to enable the Telnet service.
Enable the telnet service? (yes/no) [y]: yes
|
| Step 37 |
Enter
yes to enable the SSH service and then enter the key
type and number of key bits.
Enable the ssh service? (yes/no) [y]: yes
Type of ssh key you would like to generate (dsa/rsa) : rsa
Number of key bits <768-2048> : 1024
For more
information, see the document,
Cisco Nexus 1000V Security
Configuration Guide.
|
| Step 38 |
Enter
yes to enable the HTTP server.
Enable the http-server? (yes/no) [y]: yes
|
| Step 39 |
Enter
no to configure the NTP server.
Configure NTP server? (yes/no) [n]: no
|
| Step 40 |
Enter
yes to configure the SVS domain parameters and then
enter the mode (L2 or L3), and the control and packet VLAN IDs.
Configure svs domain parameters? (yes/no) [y]: yes
Enter SVS Control mode (L2 / L3) : L2
Enter control vlan <1-3967, 4048-4093> : 100
Enter packet vlan <1-3967, 4048-4093> : 101
|
| Step 41 |
Enter
yes to configure the VEM feature level and then
enter
0 or
1.
Vem feature level will be set to 5.2.1.SV3.4.1a,
Do you want to reconfigure? (yes/no) [n] yes
Current vem feature level is set to 5.2.1.SV3.4.1a
You can change the feature level to:
vem feature level is set to the highest value possible
The system now
summarizes the complete configuration and asks if you want to edit it.
The following configuration will be applied:
Switchname n1000v
interface Mgmt0
ip address 172.28.15.152 255.255.255.0
no shutdown
no telnet server enable
ssh key rsa 1024 force
ssh server enable
feature http-server
svs-domain
svs mode L2
control vlan 100
packet vlan 101
domain id 101
vlan 100
vlan 101
|
| Step 42 |
Do one of the
following:
-
If you do
not want to edit the configuration enter
no and continue with the next step.
-
If you
want to edit the configuration, enter
yes and return to Step 19 to revisit each command.
Would you like to edit the configuration? (yes/no) [n]:no
|
| Step 43 |
Enter
yes to use and save this configuration.
| Caution
|
If you do
not save the configuration now, none of your changes will be part of the
configuration the next time that the switch is rebooted. Enter yes to save the
new configuration and to ensure that the kickstart and system images are also
automatically configured.
|
Use this configuration and save it? (yes/no) [y]: yes
[########################################] 100%
The new
configuration is saved into nonvolatile storage.
| Note
|
You can use
the setup routine to update the configuration done in Step 18 through Step 33
at any time by entering the
setup command
in EXEC mode. Once setup begins, press
Enter to skip a command. Press
Ctrl-C to skip the remaining commands.
|
| Note
|
If you are
installing redundant VSMs, make sure that you configure the software on the
primary VSM before installing the software on the secondary VSM.
|
|
| Step 44 |
Register the
vCenter extension file in VMware vCenter. See
Registering a vCenter Extension File in VMware vCenter
for more information.
|
| Step 45 |
Create the SVS
connection manually or go to
Establishing the SVS Connection.
|


 Feedback
Feedback