- New and Changed Information
- Preface
- Overview
- Managing User Accounts
- Configuring VSD
- Configuring AAA
- Configuring RADIUS
- Configuring TACACS+
- Configuring SSH
- Configuring Telnet
- Configuring an IP ACL
- Configuring a MAC ACL
- Configuring Port Security
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring IP Source Guard
- Disabling the HTTP Server
- Blocking Unknown Unicast Flooding
- Configuration Limits
- Index
Configuring Dynamic ARP Inspection
This chapter describes how to configure dynamic Address Resolution Protocol (ARP) inspection (DAI).
This chapter includes the following sections:
•![]() Verifying the DAI Configuration
Verifying the DAI Configuration
Information About DAI
This section includes the following topics:
•![]() Interface Trust and Network Security
Interface Trust and Network Security
About ARP
ARP provides IP communication within a Layer 2 broadcast domain by mapping an IP address to a MAC address. For example, host B wants to send information to host A but does not have the MAC address of host A in its ARP cache. In ARP terms, host B is the sender and host A is the target.
To get the MAC address of host A, host B generates a broadcast message for all hosts within the broadcast domain to obtain the MAC address associated with the IP address of host A. All hosts within the broadcast domain receive the ARP request, and host A responds with its MAC address.
About ARP Spoofing Attacks
In an ARP spoofing attack, a host allows an unsolicited ARP response to update its cache so that traffic is directed through the attacker until it is discovered and the information in the ARP cache is corrected.
An ARP spoofing attack can affect hosts, switches, and routers connected to your Layer 2 network by sending false information to their ARP caches. Figure 13-1 shows an example of ARP cache poisoning.
Figure 13-1 ARP Cache Poisoning
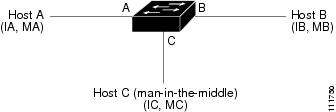
In Figure 13-1, hosts A, B, and C are connected to the device on interfaces A, B, and C, all of which are on the same subnet. Their IP and MAC addresses are shown in parentheses. For example, host A uses IP address IA and MAC address MA.
When host A needs to send IP data to host B, it broadcasts an ARP request for the MAC address associated with IP address IB. When the device and host B receive the ARP request, they add a binding to their ARP caches for a host with the IP address IA and a MAC address MA.
When host B responds, the device and host A update their ARP caches with a binding for a host with the IP address IB and the MAC address MB.
Host C can spoof host A and B by broadcasting the following forged ARP responses:
•![]() one for a host with an IP address of IA and a MAC address of MC
one for a host with an IP address of IA and a MAC address of MC
•![]() one for a host with the IP address of IB and a MAC address of MC.
one for a host with the IP address of IB and a MAC address of MC.
Host B then uses MC as the destination MAC address for traffic that was intended for IA, which means that host C intercepts that traffic. Likewise, host A and the device use MC as the destination MAC address for traffic intended for IB.
Because host C knows the authentic MAC addresses for IA and IB, it can forward the intercepted traffic.
About DAI and ARP Spoofing
DAI is used to validate ARP requests and responses as follows:
•![]() Intercepts all ARP requests and responses on untrusted ports.
Intercepts all ARP requests and responses on untrusted ports.
•![]() Verifies that a packet has a valid IP-to-MAC address binding before updating the ARP cache or forwarding the packet.
Verifies that a packet has a valid IP-to-MAC address binding before updating the ARP cache or forwarding the packet.
•![]() Drops invalid ARP packets.
Drops invalid ARP packets.
DAI can determine the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a Dynamic Host Configuration Protocol (DHCP) snooping binding database. This database is built by DHCP snooping when it is enabled on the VLANs and on the device. It may also contain static entries that you have created.
If an ARP packet is received on a trusted interface, the device forwards the packet without any checks. On untrusted interfaces, the device forwards the packet only if it is valid. For more information about trusted interfaces, see the Interface Trust and Network Security.
You can enable or disable validation of ARP packets for destination MAC address, source MAC address, and IP address. For more information, see the "Validating ARP Packets" section.
Interface Trust and Network Security
DAI identifies interfaces as trusted or untrusted.
In a typical network, interfaces are configured as follows:
•![]() Untrusted—Interfaces that are connected to hosts
Untrusted—Interfaces that are connected to hosts
Packets are validated by DAI.
•![]() Trusted—Interfaces that are connected to devices
Trusted—Interfaces that are connected to devices
Packets bypass all DAI validation checks.
With this configuration, all ARP packets that enter the network from a device bypass the security check. No other validation is needed at any other place in the VLAN or in the network. For information about configuring a trusted interface, see the "Configuring a Trusted vEthernet Interface" section.

In Figure 13-2, assume that both device A and device B are running DAI on the VLAN that includes host 1 and host 2. If host 1 and host 2 acquire their IP addresses from the DHCP server connected to device A, only device A binds the IP-to-MAC address of host 1. If the interface between device A and device B is untrusted, the ARP packets from host 1 are dropped by device B and connectivity between host 1 and host 2 is lost.
Figure 13-2 ARP Packet Validation on a VLAN Enabled for DAI
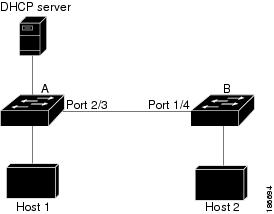
If you configure interfaces as trusted when they should be untrusted, you may open a security hole in a network. If device A is not running DAI, host 1 can easily poison the ARP cache of device B (and host 2, if you configured the link between the devices as trusted). This condition can occur even though device B is running DAI.
DAI ensures that hosts (on untrusted interfaces) connected to a device that runs DAI do not poison the ARP caches of other hosts in the network; however, DAI does not prevent hosts in other portions of the network from poisoning the caches of the hosts that are connected to a device that runs DAI.

Note ![]() Depending on your network setup, you may not be able to validate a given ARP packet on all devices in the VLAN.
Depending on your network setup, you may not be able to validate a given ARP packet on all devices in the VLAN.
Prerequisites for DAI
The following are prerequisite to configuring DAI.
•![]() You are familiar with the following:
You are familiar with the following:
–![]() ARP
ARP
For more information, see IETF Standard RFC-826, An Ethernet Address Resolution Protocol (http://tools.ietf.org/html/rfc826).
–![]() DHCP Snooping
DHCP Snooping
For more information, see Configuring DHCP Snooping.
•![]() The software running on your Cisco Nexus 1000V supports DAI.
The software running on your Cisco Nexus 1000V supports DAI.
•![]() The VEM feature level is updated to a release that supports DAI.
The VEM feature level is updated to a release that supports DAI.
For more information about setting the VEM feature level, see the Cisco Nexus 1000V Software Upgrade Guide, Release 4.2(1)SV1(4b).
Guidelines and Limitations
DAI has the following configuration guidelines and limitations:
•![]() DAI is an ingress security feature and does not perform any egress checking.
DAI is an ingress security feature and does not perform any egress checking.
•![]() DAI is not effective when the host is connected to a device that does not support DAI or that does not have DAI enabled. To prevent attacks that are limited to a single Layer 2 broadcast domain, you should separate a domain with DAI from those without DAI. This separation secures the ARP caches of hosts in the domain with DAI.
DAI is not effective when the host is connected to a device that does not support DAI or that does not have DAI enabled. To prevent attacks that are limited to a single Layer 2 broadcast domain, you should separate a domain with DAI from those without DAI. This separation secures the ARP caches of hosts in the domain with DAI.
•![]() DAI verifies IP-to-MAC address bindings in incoming ARP requests and ARP responses. If you have not configured static entries, then DHCP snooping must be enabled on the same VLANs on which you configure DAI. For more information, see the "Configuring DHCP Snooping" section.
DAI verifies IP-to-MAC address bindings in incoming ARP requests and ARP responses. If you have not configured static entries, then DHCP snooping must be enabled on the same VLANs on which you configure DAI. For more information, see the "Configuring DHCP Snooping" section.
•![]() DAI is supported on vEthernet interfaces and private VLAN ports.
DAI is supported on vEthernet interfaces and private VLAN ports.
•![]() If you want DAI to use dynamic IP-MAC address bindings to determine if ARP packets are valid, ensure that DHCP snooping is configured. For more information, see the "Configuring DHCP Snooping" section).
If you want DAI to use dynamic IP-MAC address bindings to determine if ARP packets are valid, ensure that DHCP snooping is configured. For more information, see the "Configuring DHCP Snooping" section).
•![]() Virtual Service Domain (VSD) service VM ports are trusted ports by default. Even if you configure VSD ports as untrusted, they still appear as trusted ports to DAI.
Virtual Service Domain (VSD) service VM ports are trusted ports by default. Even if you configure VSD ports as untrusted, they still appear as trusted ports to DAI.
Default Settings
Table 13-1 lists the DAI defaults.
Configuring DAI
This section includes the following topics:
•![]() Configuring a Trusted vEthernet Interface
Configuring a Trusted vEthernet Interface
•![]() Resetting a vEthernet Interface to Untrusted
Resetting a vEthernet Interface to Untrusted
•![]() Resetting DAI Rate Limits to Default Values
Resetting DAI Rate Limits to Default Values
•![]() Detecting and Recovering Error-Disabled Interfaces
Detecting and Recovering Error-Disabled Interfaces
Configuring a VLAN for DAI
Use this procedure to configure a VLAN or a list of VLANs for DAI.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() By default, VLANs are not configured for DAI.
By default, VLANs are not configured for DAI.
•![]() You have already enabled DHCP snooping. For more information, see the "Enabling or Disabling the DHCP Feature" section.
You have already enabled DHCP snooping. For more information, see the "Enabling or Disabling the DHCP Feature" section.
•![]() You know which VLANs you want to configure for DAI and they have already been created.
You know which VLANs you want to configure for DAI and they have already been created.
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() [no] ip arp inspection vlan list
[no] ip arp inspection vlan list
3. ![]() show ip arp inspection vlan list
show ip arp inspection vlan list
4. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
Configuring a Trusted vEthernet Interface
Use this procedure to configure a trusted vEthernet interface.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() By default, vEthernet interfaces are untrusted, unless they are part of a VSD.
By default, vEthernet interfaces are untrusted, unless they are part of a VSD.
•![]() If an interface is untrusted, all ARP requests and responses are verified for a valid IP-MAC address binding before the local cache is updated and the packet forwarded. If a packet has an invalid IP-MAC address binding, it is dropped.
If an interface is untrusted, all ARP requests and responses are verified for a valid IP-MAC address binding before the local cache is updated and the packet forwarded. If a packet has an invalid IP-MAC address binding, it is dropped.
•![]() ARP packets received on a trusted interface are forwarded but not checked.
ARP packets received on a trusted interface are forwarded but not checked.
•![]() You can configure a trusted interface on either of the following:
You can configure a trusted interface on either of the following:
–![]() the interface, itself
the interface, itself
–![]() the existing port profile that the interface is assigned to
the existing port profile that the interface is assigned to
If configuring a trusted interface on the port profile, it has already been created and you know its name.
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() interface vethernet interface-number
interface vethernet interface-number
port-profile profilename
3. ![]() [no] ip arp inspection trust
[no] ip arp inspection trust
4. ![]() show ip arp inspection interface type slot/number
show ip arp inspection interface type slot/number
show port-profile profilename
5. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
Resetting a vEthernet Interface to Untrusted
Use this procedure to remove a trusted designation from a vEthernet interface, returning it to the default untrusted designation.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() By default, vEthernet interfaces are untrusted, unless they are part of a VSD.
By default, vEthernet interfaces are untrusted, unless they are part of a VSD.
•![]() If an interface is untrusted, all ARP requests and responses are verified for a valid IP-MAC address binding before the local cache is updated and the packet forwarded. If a packet has an invalid IP-MAC address binding, it is dropped.
If an interface is untrusted, all ARP requests and responses are verified for a valid IP-MAC address binding before the local cache is updated and the packet forwarded. If a packet has an invalid IP-MAC address binding, it is dropped.
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() interface vethernet interface-number
interface vethernet interface-number
3. ![]() default ip arp inspection trust
default ip arp inspection trust
4. ![]() show ip arp inspection interface type slot/number
show ip arp inspection interface type slot/number
5. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
Configuring DAI Rate Limits
Use this procedure to set the rate limit of ARP requests and responses.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() Because of their aggregation, trunk ports should be configured with higher rate limit.
Because of their aggregation, trunk ports should be configured with higher rate limit.
•![]() Once the rate of incoming packets exceeds the configured rate, the interface is automatically put into an errdisable state.
Once the rate of incoming packets exceeds the configured rate, the interface is automatically put into an errdisable state.
•![]() The default DAI rate limits are as follows:
The default DAI rate limits are as follows:
–![]() Untrusted interfaces = 15 packets per second
Untrusted interfaces = 15 packets per second
–![]() Trusted interfaces = unlimited
Trusted interfaces = unlimited
–![]() Burst interval = 1 second
Burst interval = 1 second
•![]() You can configure the rate limits for an interface on either of the following:
You can configure the rate limits for an interface on either of the following:
–![]() the interface, itself
the interface, itself
–![]() the existing port profile that the interface is assigned to
the existing port profile that the interface is assigned to
If configuring the port profile, it has already been created and you know its name.
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() interface vethernet interface-number
interface vethernet interface-number
port-profile profilename
3. ![]() ip arp inspection limit {rate pps [burst interval bint] | none}
ip arp inspection limit {rate pps [burst interval bint] | none}
4. ![]() show running-config dhcp
show running-config dhcp
5. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
Resetting DAI Rate Limits to Default Values
Use this procedure to set the rate limit of ARP requests and responses to the defaults, removing any configured values.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() The default DAI rate limits are as follows:
The default DAI rate limits are as follows:
–![]() Untrusted interfaces = 15 packets per second
Untrusted interfaces = 15 packets per second
–![]() Trusted interfaces = unlimited
Trusted interfaces = unlimited
–![]() Burst interval = 1 second
Burst interval = 1 second
•![]() You can configure the rate limits for an interface on either of the following:
You can configure the rate limits for an interface on either of the following:
–![]() the interface, itself
the interface, itself
–![]() the existing port profile that the interface is assigned to
the existing port profile that the interface is assigned to
If configuring the port profile, it has already been created and you know its name.
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() interface vethernet interface-number
interface vethernet interface-number
3. ![]() default ip arp inspection limit {rate pps [burst interval bint] | none}
default ip arp inspection limit {rate pps [burst interval bint] | none}
4. ![]() show running-config dhcp
show running-config dhcp
5. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
Detecting and Recovering Error-Disabled Interfaces
Use this procedure to configure the detection and recovery of error-disabled interfaces.
BEFORE YOU BEGIN
Before beginning this procedures, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() By default, interfaces are not configured for DAI error-disabled recovery.
By default, interfaces are not configured for DAI error-disabled recovery.
•![]() To manually recover an interface from the error-disabled state, use the following command sequence.
To manually recover an interface from the error-disabled state, use the following command sequence.
1. shutdown
2. no shutdown
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() [no] errdisable detect cause arp-inspection
[no] errdisable detect cause arp-inspection
3. ![]() [no] errdisable recovery cause arp-inspection
[no] errdisable recovery cause arp-inspection
4. ![]() errdisable recovery interval timer-interval
errdisable recovery interval timer-interval
5. ![]() show running-config | include errdisable
show running-config | include errdisable
6. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
Validating ARP Packets
Use this procedure to configure the validation of ARP packets.
BEFORE YOU BEGIN
Before beginning this procedure, you must know or do the following:
•![]() You are logged in to the CLI in EXEC mode.
You are logged in to the CLI in EXEC mode.
•![]() You can enable validation of the following, which are disabled by default:
You can enable validation of the following, which are disabled by default:
–![]() Destination MAC address
Destination MAC address
Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body, and drops packets with an invalid MAC address.
–![]() IP address
IP address
Checks the ARP body for invalid and unexpected IP addresses, including 0.0.0.0, 255.255.255.255, and any IP multicast address. Sender IP addresses are checked in both ARP requests and responses. Target IP addresses are checked only in ARP responses.
–![]() Source MAC address
Source MAC address
Checks the source MAC address in the Ethernet header against the sender MAC address in the ARP body for ARP requests and responses, and drops packets with invalid MAC addresses.
•![]() Whenever you configure a validation, any previous validation configuration is overwritten.
Whenever you configure a validation, any previous validation configuration is overwritten.
SUMMARY STEPS
1. ![]() config t
config t
2. ![]() [no] ip arp inspection validate {[src-mac] [dst-mac] [ip]}
[no] ip arp inspection validate {[src-mac] [dst-mac] [ip]}
3. ![]() show running-config dhcp
show running-config dhcp
4. ![]() copy running-config startup-config
copy running-config startup-config
DETAILED STEPS
Verifying the DAI Configuration
To display and verify the DAI configuration, use the following commands:
For detailed information about command output, see the Cisco Nexus 1000V Command Reference, Release 4.2(1)SV1(4a).
Monitoring DAI
To monitor DAI, use the following commands:
For detailed information about command output, see the Cisco Nexus 1000V Command Reference, Release 4.2(1)SV1(4a).
Example DAI Configuration
This example shows how to configure DAI in a network with two VEMs:
•![]() One VEM is hosting an authentic web server and a DHCP server.
One VEM is hosting an authentic web server and a DHCP server.
•![]() The other VEM is hosting a client virtual machine (VM 1) and a virtual machine (VM 2) with a rogue web server. VM 1 is connected to vEthernet interface 3, which is untrusted by default, and belongs to VLAN 1. VM 2 is connected to vEthernet 10 and VLAN 1.
The other VEM is hosting a client virtual machine (VM 1) and a virtual machine (VM 2) with a rogue web server. VM 1 is connected to vEthernet interface 3, which is untrusted by default, and belongs to VLAN 1. VM 2 is connected to vEthernet 10 and VLAN 1.
Without DAI enabled, VM 2 can spoof the ARP cache in VM 1 by sending a packet even though an ARP request was not generated. In this case, the packet directs VM 1 to send its traffic to the VM 2 web server instead of the authentic web server.
If DAI is enabled when VM2 attempts to spoof the ARP cache in VM1, the unsolicited ARP packet sent by VM 2 is dropped because DAI detects the invalid IP-to-MAC address binding. The attempt to spoof the ARP cache fails, and VM 1 connects to the authentic web server.

Note ![]() DAI depends on the DHCP snooping database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically-assigned IP addresses. For configuration information, see Chapter 12 "Configuring DHCP Snooping."
DAI depends on the DHCP snooping database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically-assigned IP addresses. For configuration information, see Chapter 12 "Configuring DHCP Snooping."
The following steps are used to configure DAI for this example:
Step 1 ![]() Enable DAI on VLAN 1 and verify the configuration.
Enable DAI on VLAN 1 and verify the configuration.
n1000v# config t
n1000v(config)# ip arp inspection vlan 1
n1000v(config)# show ip arp inspection vlan 1
Source Mac Validation : Disabled
Destination Mac Validation : Disabled
IP Address Validation : Disabled
Vlan : 1
-----------
Configuration : Enabled
Operation State : Active
n1000v(config)#
Step 2 ![]() Check the statistics before and after DAI processes any packets.
Check the statistics before and after DAI processes any packets.
n1000v# show ip arp inspection statistics vlan 1
Vlan : 1
-----------
ARP Req Forwarded = 0
ARP Res Forwarded = 0
ARP Req Dropped = 0
ARP Res Dropped = 0
DHCP Drops = 0
DHCP Permits = 0
SMAC Fails-ARP Req = 0
SMAC Fails-ARP Res = 0
DMAC Fails-ARP Res = 0
IP Fails-ARP Req = 0
IP Fails-ARP Res = 0
n1000v#
If VM 1 sends out two ARP requests with an IP address of 10.0.0.1 and a MAC address of 0002.0002.0002, both requests are permitted, as shown in the following command output:
n1000v# show ip arp inspection statistics vlan 1
Vlan : 1
-----------
ARP Req Forwarded = 2
ARP Res Forwarded = 0
ARP Req Dropped = 0
ARP Res Dropped = 0
DHCP Drops = 0
DHCP Permits = 2
SMAC Fails-ARP Req = 0
SMAC Fails-ARP Res = 0
DMAC Fails-ARP Res = 0
IP Fails-ARP Req = 0
IP Fails-ARP Res = 0
If VM 2 tries to send an ARP request with an IP address of 10.0.0.3, the packet is dropped and an error message is logged.
00:12:08: %SW_DAI-4-DHCP_SNOOPING_DENY: 2 Invalid ARPs (Req) on vEthernet3, vlan 1.([0002.0002.0002/10.0.0.3/0000.0000.0000/0.0.0.0/02:42:35 UTC Fri Jul 13 2008])
The statistics display as follows:
n1000v# show ip arp inspection statistics vlan 1
n1000v#
Vlan : 1
-----------
ARP Req Forwarded = 2
ARP Res Forwarded = 0
ARP Req Dropped = 2
ARP Res Dropped = 0
DHCP Drops = 2
DHCP Permits = 2
SMAC Fails-ARP Req = 0
SMAC Fails-ARP Res = 0
DMAC Fails-ARP Res = 0
IP Fails-ARP Req = 0
IP Fails-ARP Res = 0
n1000v#
Additional References
For additional information related to implementing DAI, see the following sections:
Related Documents
Standards
|
|
|
|---|---|
RFC-826 |
An Ethernet Address Resolution Protocol (http://tools.ietf.org/html/rfc826) |
Feature History for DAI
Table 13-2 lists the release history for the DAI feature.
|
|
|
|
|---|---|---|
DAI |
4.0(4)SV1(2) |
This feature was introduced. |
 Feedback
Feedback