Information About User Accounts and RBAC
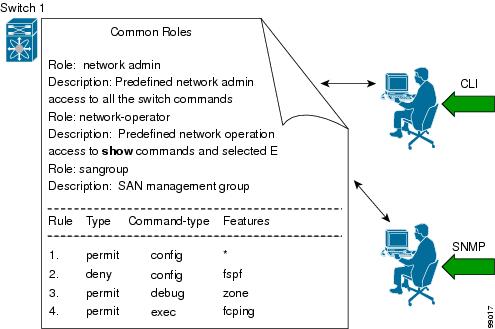
You can create and manage users accounts and assign roles that limit access to operations on the Cisco MDS 9000 devices. Role-based access control (RBAC) allows you to define the rules for an assign role that restrict the authorization that the user has to access management operations.
User authentication information, user name, user password, password expiration date, and role membership are stored in the user profile.
The tasks explained in this section enables you to create users and modify the profile of an existing user. These tasks are restricted to privileged users as determined by your administrator.
User Accounts
You can configure up to a maximum of 256 user accounts. By default, the user account does not expire unless you explicitly configure it to expire. The expire option determines the date when the user account is disabled.
When creating users, note the following guidelines:
-
The following words are reserved and cannot be used to configure users: bin, daemon, adm, lp, sync, shutdown, halt, mail, news, uucp, operator, games, gopher, ftp, nobody, nscd, mailnull, rpc, rpcuser, xfs, gdm, mtsuser, ftpuser, man, and sys.
-
User passwords are not displayed in the switch configuration file.
-
The passphrase specified in the snmp-server user command and the password specified username command are synchronized.
-
By default, the user account does not expire unless you explicitly configure it to expire. The expire option determines the date on which the user account is disabled. The date is specified in the YYYY-MM-DD format.
-
If a password is trivial (short, easy-to-decipher), your password configuration is rejected. Be sure to configure a strong password as shown in the sample configuration. Passwords are case-sensitive.
-
To issue commands with the internal keyword for troubleshooting purposes, you must have an account that is a member of the network-admin group.
 Caution |
Cisco MDS NX-OS supports user names that are created with alphanumeric characters or specific special characters (+ [plus], = [equal], _ [underscore], - [hyphen], \ [backslash], and . [period]) whether created remotely (using TACACS+ or RADIUS) or locally, provided that the user name starts with an alphanumeric character. Local user names cannot be created with any special characters (apart from those specified). If a nonsupported special character user name exists on an AAA server, and is entered during login, then the user is denied access. |
Characteristics of Strong Passwords
A strong password has the following characteristics:
-
Is at least eight characters long
-
Does not contain many consecutive characters (such as “abcd”)
-
Does not contain many repeating characters (such as “aaabbb”)
-
Does not contain dictionary words
-
Does not contain proper names
-
Contains both uppercase and lowercase characters
-
Contains numbers
The following are examples of strong passwords:
-
If2CoM18
-
2004AsdfLkj30
-
Cb1955S21
If a password is trivial (such as a short, easy-to-decipher password), the Cisco MDS NX-OS software will reject your password configuration, if the password-strength checking is enabled. Be sure to configure a strong password as shown in the sample configuration. Passwords are case sensitive.
The above rules for generating passwords are applicable to remote user authentication via AAA servers such as TACACS+, RADIUS or LDAP.
Checking Password Strength
You can enable password-strength checking that prevents you from creating weak passwords for user accounts.
 Note |
When you enable password checking, it does not check the strength of existing passwords. |
To enable password strength checking, follow these steps:
Procedure
|
Step 1 |
switch# configure terminal Enters configuration mode. |
|
Step 2 |
switch(config)# password strength-check Enables password-strength checking. The default is enabled. You can disable password-strength checking by using the no form of this command. |
|
Step 3 |
switch(config)# exit (Optional) Exits global configuration mode. |
|
Step 4 |
switch(config)# show password strength-check (Optional) Displays the password-strength check configuration. |
|
Step 5 |
switch(config)# copy running-config startup-config (Optional) Copies the running configuration to the startup configuration. |
Configuring Users
To configure a new user or to modify the profile of an existing user, follow these steps:
Procedure
|
Step 1 |
switch# configure terminal Enters configuration mode. |
||
|
Step 2 |
switch(config)# username usam password abcd123AAA expire 2003-05-31 Creates or updates the user account (usam) along with a password (abcd123AAA) that is set to expire on 2003-05-31. |
||
|
Step 3 |
switch(config)# username msam password 0 abcd12AAA role network-operator Creates or updates the user account (msam) along with a password (abcd12AAA) specified in clear text (indicated by 0). The password is limited to 64 characters. |
||
|
Step 4 |
switch(config)# username user1 password 5 $1$UgOR6Xqb$z.HZlMk.ZGr9VH67a
|
||
|
Step 5 |
switch(config)# username usam role network-admin Adds the specified user (usam) to the network-admin role. |
||
|
Step 6 |
switch(config)# no username usam role vsan-admin (Optional) Deletes the specified user (usam) from the vsan-admin role. |
||
|
Step 7 |
switch(config)# username admin sshkey ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEAtjIHrIt/3dDeohix6JcRSIYZ0EOdJ3l5RONWcwSgAuTUSrLk3a9hdYkzY94fhHmNGQGCjVg+8cbOxyH4Z1jcVFcrDogtQT+Q8dveqts/8XQhqkNAFeGy4u8TJ2Us3a9hdYkzY94fhHmNGQGCjVg+8cbOxyH4Z1jcVFcrDogtQT+Q8dveqts/8XQhqkNAFeGy4u8TJ2Us Specifies the SSH key for an existing user account (admin). |
||
|
Step 8 |
switch(config)# no username admin sshkey ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEAtjIHrIt/3dDeohix6JcRSIYZ0EOdJ3l5RONWcwSgAuTUSrLk3a9hdYkzY94fhHmNGQGCjVg+8cbOxyH4Z1jcVFcrDogtQT+Q8dveqts/8XQhqkNAFeGy4u8TJ2Us3a9hdYkzY94fhHmNGQGCjVg+8cbOxyH4Z1jcVFcrDogtQT+Q8dveqts/8XQhqkNAFeGy4u8TJ2Us (Optional) Deletes the SSH key for the user account (admin). |
||
|
Step 9 |
switch(config)# username usam ssh-cert-dn usam-dn dsa Specifies an SSH X.509 certificate distinguished name and DSA algorithm to use for authentication for an existing user account (usam). |
||
|
Step 10 |
switch(config)# username user1 ssh-cert-dn user1-dn rsa Specifies an SSH X.509 certificate distinguished name and RSA algorithm to use for authentication for an existing user account (user1). |
||
|
Step 11 |
switch(config)# no username admin ssh-cert-dn admin-dn dsa Removes the SSH X.509 certificate distinguished name for the user account (admin). |
Logging Out Users
To log out another user on the switch, use the clear user command.
Displays All Logged in Users
In the following example, the user named vsam is logged out from the switch:
switch# clear user vsamUse the show users command to view a list of the logged in users (see the following example).
switch# show users
admin pts/7 Jan 12 20:56 (10.77.202.149)
admin pts/9 Jan 12 23:29 (user.example.com)
admin pts/10 Jan 13 03:05 (dhcp-10-10-1-1.example.com)
admin pts/11 Jan 13 01:53 (dhcp-10-10-2-2.example.com)
Displaying User Account Information
Displays Information for a Specified User
Use the show user-account command to display configured information about user accounts. See the following examples.
switch# show user-account user1
user:user1
this user account has no expiry date
roles:network-operator
no password set. Local login not allowed
Remote login through RADIUS is possible
switch# show user-account
show user-account
user:admin
this user account has no expiry date
roles:network-admin
user:usam
expires on Sat May 31 00:00:00 2003
roles:network-admin network-operator
user:msam
this user account has no expiry date
roles:network-operator
user:user1
this user account has no expiry date
roles:network-operator
no password set. local login not allowed
Remote login through RADIUS is possible 
 Feedback
Feedback