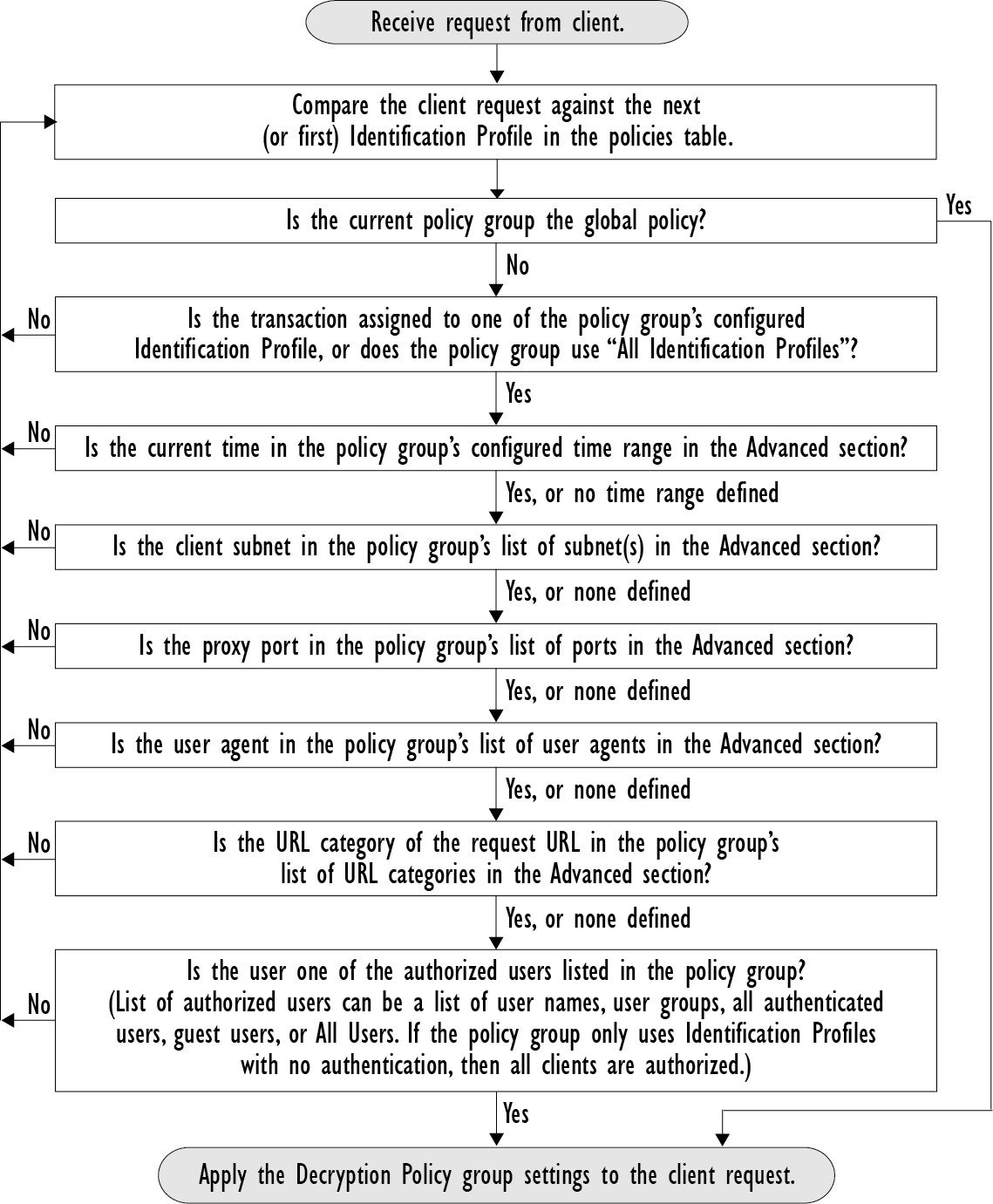
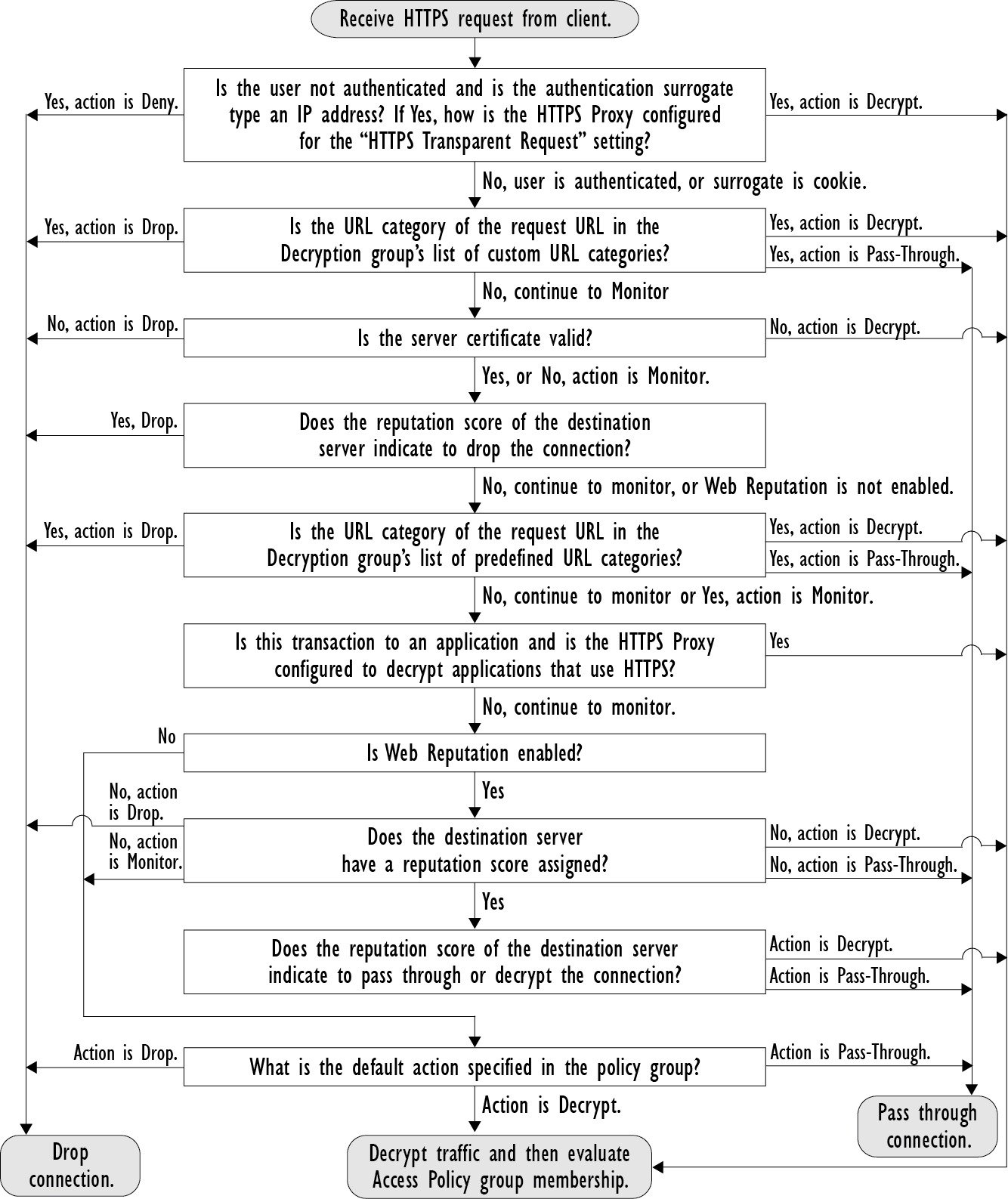
Overview of Create Decryption Policies to Control HTTPS Traffic
Decryption policies define the handling of HTTPS traffic within the web proxy:
- When to decrypt HTTPS traffic.
- How to handle requests that use invalid or revoked security certificates.
You can create decryption policies to handle HTTPS traffic in the following ways:
- Pass through encrypted traffic
- Decrypt traffic and apply the content-based access policies defined for HTTP traffic. This also makes malware scanning possible.
- Drop the HTTPS connection
- Monitor the request (take no final action) as the web proxy continues to evaluate the request against policies that may lead to a final drop, pass through, or decrypt action.
 Caution |
Handle personally
identifiable information with care: If you choose to decrypt an
end-user’s HTTPS session, the Web Security appliance access logs and reports
may contain personally identifiable information. The Administrator can
configure how much URI text is stored in the logs using the
|
Managing HTTPS Traffic through Decryption Policies Task Overview
|
Step |
Task List for Managing HTTPS Traffic through Decryption Policies |
Links to Related Topics and Procedures |
|---|---|---|
|
1 |
Enabling the HTTPS proxy |
|
|
2 |
Upload or Generate a certificate and key |
|
|
3 |
Configuring Decryption options |
|
|
5 |
(Optional) Configure invalid certificate handling |
|
|
6 |
(Optional) Enabling real-time revocation status checking |
|
|
7 |
(Optional) Manage trusted and blocked certificates |

 Feedback
Feedback