Overview of Classify Users and Client Software
Identification Profiles let you classify users and user agents (client software) for these purposes:
- Group transaction requests for the application of policies (except SaaS)
- Specification of identification and authentication requirements
AsyncOS assigns an Identification Profile to every transaction:
- Custom Identification Profiles — AsyncOS assigns a custom profile based on that identity’s criteria.
- The Global Identification Profile — AsyncOS assigns the global profile to transactions that do not meet the criteria for any custom profile. By default, the global profile does not require authentication.
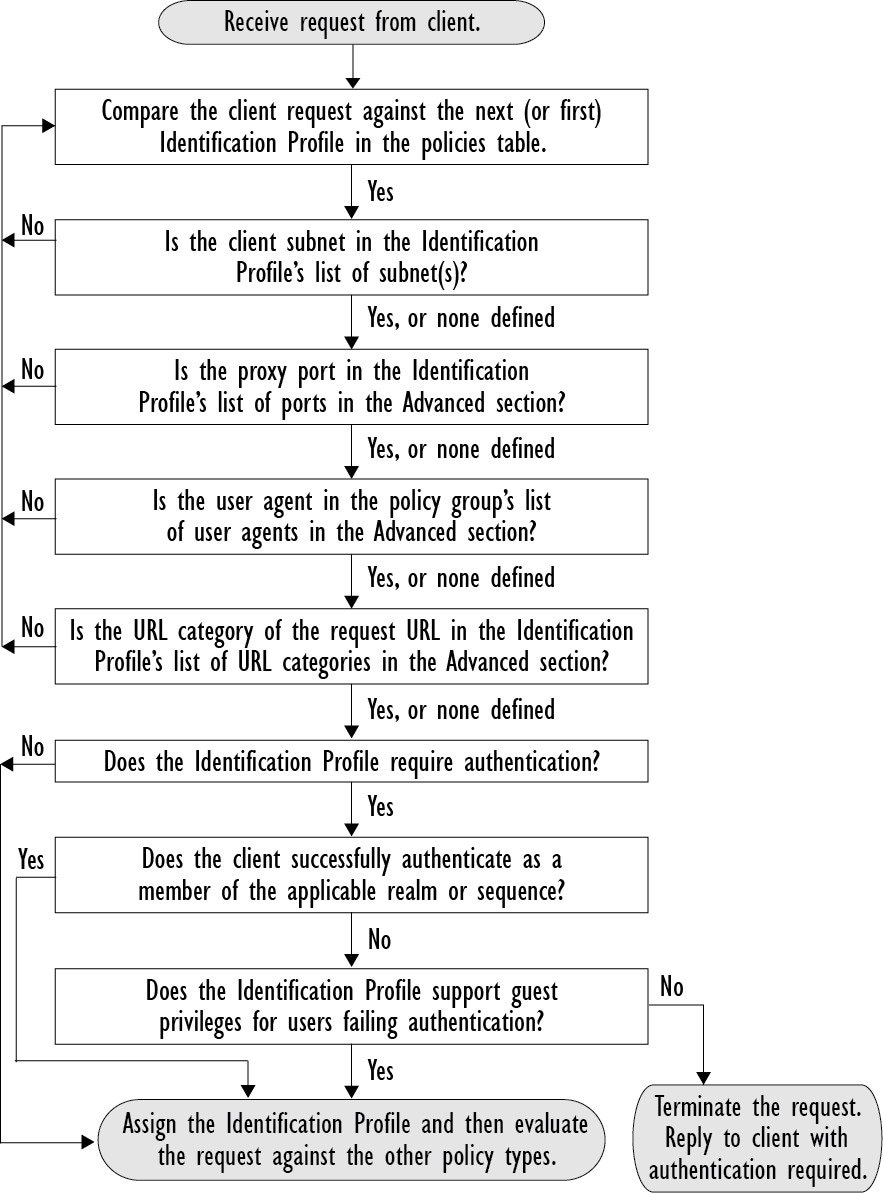
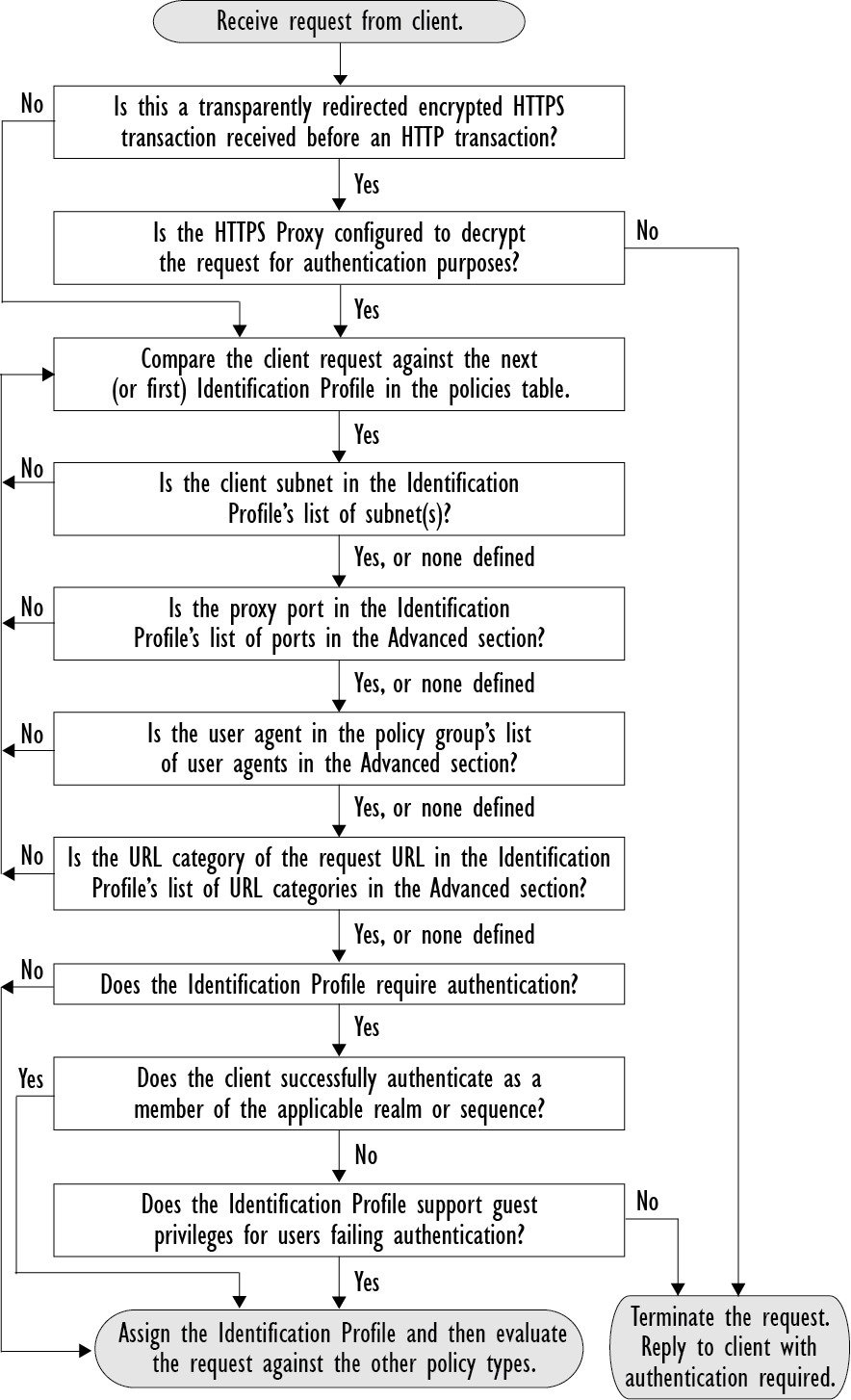
AsyncOS processes Identification Profiles sequentially, beginning with the first. The global profile is the last profile.
An Identification Profile may include only one criterion. Alternately, Identification Profiles that include multiple criteria require that all the criteria are met.
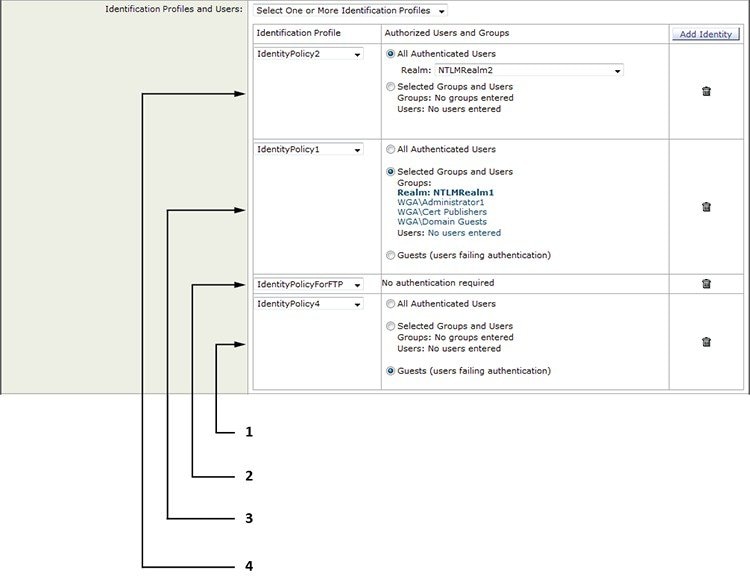
One policy may call on multiple Identification Profiles:
|
1 |
This Identification Profile allows guest access and applies to users who fail authentication. |
|
2 |
Authentication is not used for this Identification Profile. |
|
3 |
The specified user groups in this Identification Profile are authorized for this policy. |
|
4 |
This Identification Profile uses an authentication sequence and this policy applies to one realm in the sequence. |
 Feedback
Feedback