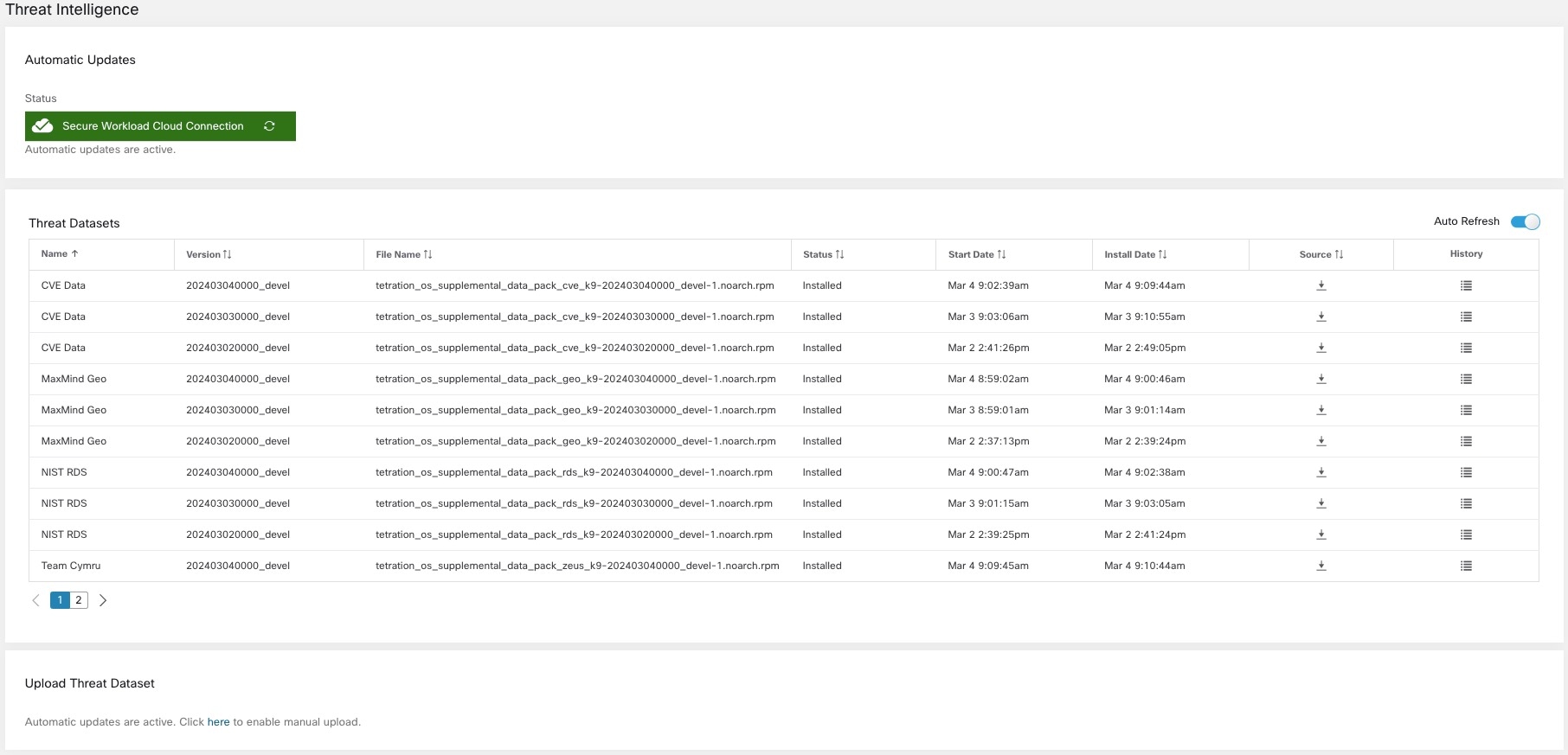
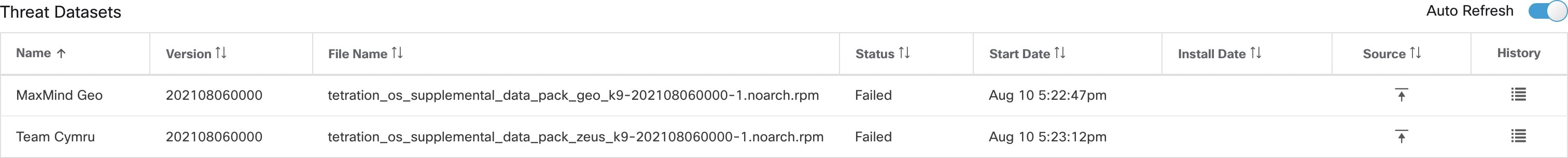
Manage Threat Intelligence
To manage threat intelligence, from the navigation pane, choose .
 Note |
By default, the feature to identify well-known malicious IP addresses is disabled. To enable this feature, see Visibility of Well-Known Malicious IPv4 Addresses. |
 Feedback
Feedback