Policy Compliance in Secure Workload
What Is Noncompliant Traffic?
Noncompliant traffic includes unauthorized access attempts, misconfigurations, malicious activities, or any traffic that does not comply the rules set in policies. Dealing with noncompliant traffic within an organization's network poses significant challenges. Noncompliance affects not only the security posture of the company, but also its compliance with industry regulations, legal requirements, and internal policies.
What Is the Risk?
Noncompliant traffic in an organization could lead to potential data breach and loss of customer trust. If not resolved immediately, it could lead to violation of regulatory laws and local data-protection laws.
Is This Use Case for You?
The intended audience for the Secure Workload Policy Compliance use case is the administrator, who is responsible for managing and securing the network of an organization. Since it is the administrator who applies several policies to safeguard the network, it is of utmost importance for the administrator to ensure that the traffic complies with the policies, that is, traffic behaves as intended. Cisco Secure Workload provides insight into the traffic flow for the administrator to immediately identify and isolate unintended traffic, if any.
Cisco Secure Workload provides comprehensive workload protection by tailoring the security posture that is based on the application behavior. It can maintain the compliance of the network by automatically identifying application behavior deviations and invoking appropriate workflows for policy updates.
Scenario
A financial services company sees a significant surge in noncompliant traffic in its network. The company handles sensitive cardholder and customer data. It operates in a highly regulated industry and must comply with various financial regulations and industry-specific guidelines to protect cardholders’ data such as the Payment Card Industry Data Security Standard (PCI DSS).
The company’s administrator is responsible for configuring and managing the network.
There could be many reasons for noncompliant traffic in an organization, including the following:
-
Attempts to connect to unauthorized ports or IP addresses, leading to a potential violation of the security system rules.
-
Incoming or outgoing traffic not complying with the defined ingress and egress policies, for example, access from geographically restricted locations.
-
Unapproved, outdated, or unsecured protocols that are vulnerable to exploitation.
-
Using a peer-to-peer (P2P) application that bypasses the security controls and introduces risks such as data loss or malware infiltration.
-
Anomalies in traffic, such as significant increase in data exfiltration or unexpected communication with known malicious IP addresses.
-
Traffic originating from a compromised system communicating with other devices.
How Does Cisco Secure Workload Help?
Cisco Secure Workload provides segmentation and microsegmentation policies that allow only the required traffic to conduct business and block all other traffic. This reduces the network's attack surface without disrupting business operations.
The administrator looks at the telemetry data that is gathered by Secure Workload from various resources. The administrator then analyzes the flow and observes granular details of the flow, such as source, destination, port, protocol, and a few other attributes over the lifetime of that flow. Based on the findings, the administrator discovers policies and enforces them. If noncompliant traffic that needs immediate attention is discovered, the administrator creates specific policies to isolate them.
After enforcing the policies, the administrator monitors the flow periodically for noncompliance.
How Does It Work?
Procedure
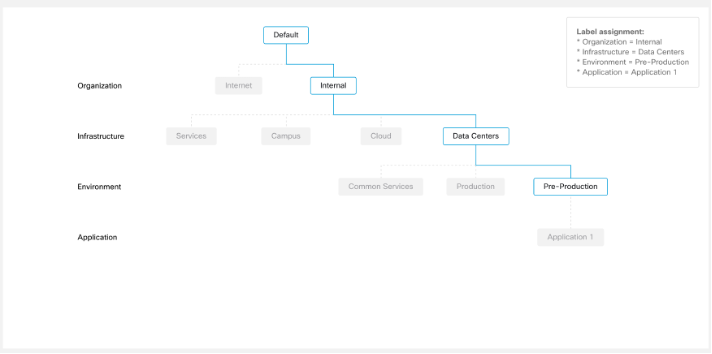
Step 1 | The necessary labels, scopes, and workspaces are created for the workload in the organization. The Quick Start wizard helps you to group and label your workloads to build a hierarchy for your organization. For more information, see the Cisco Secure Workload Quick Start Guide. |
Step 2 | Policies for the workloads are created. For example, setting up common policies to:
|
Step 3 | Automatically discover policies that are based on existing traffic patterns. Discovering policies automatically allows Secure Workload to analyze traffic between workloads, groups workloads based on their behavior, and suggests a set of policies that are intended to allow the traffic that your organization requires, so that you can block all other traffic. See Discovery Policies Automatically. |
Step 4 | Review and analyze the policies that are suggested by Secure Workload. For information about the detailed procedure, see Get Started with Segmentation and Microsegmentation in the Cisco Secure Workload On-Premises User Guide. |
Investigate Escaped Flows to Detect Noncompliant Traffic
According to policy analysis, an Escaped flow in a network is a flow that should be dropped and not allowed further. Escaped flows require special attention because their actual flow disposition differs from the planned action based on the currently analyzed policies. Investigate to ensure that enforcing these policies does not block the required flows and adversely impact your applications.
Escaped flows occur during the policy analysis phase before policy enforcement. However, if preserved rules are enabled, any local rules applied by the customer can create escaped flows.
Procedure
Step 1 | Navigate to Defend > Segmentation. |
Step 2 | Click Manage Policies. |
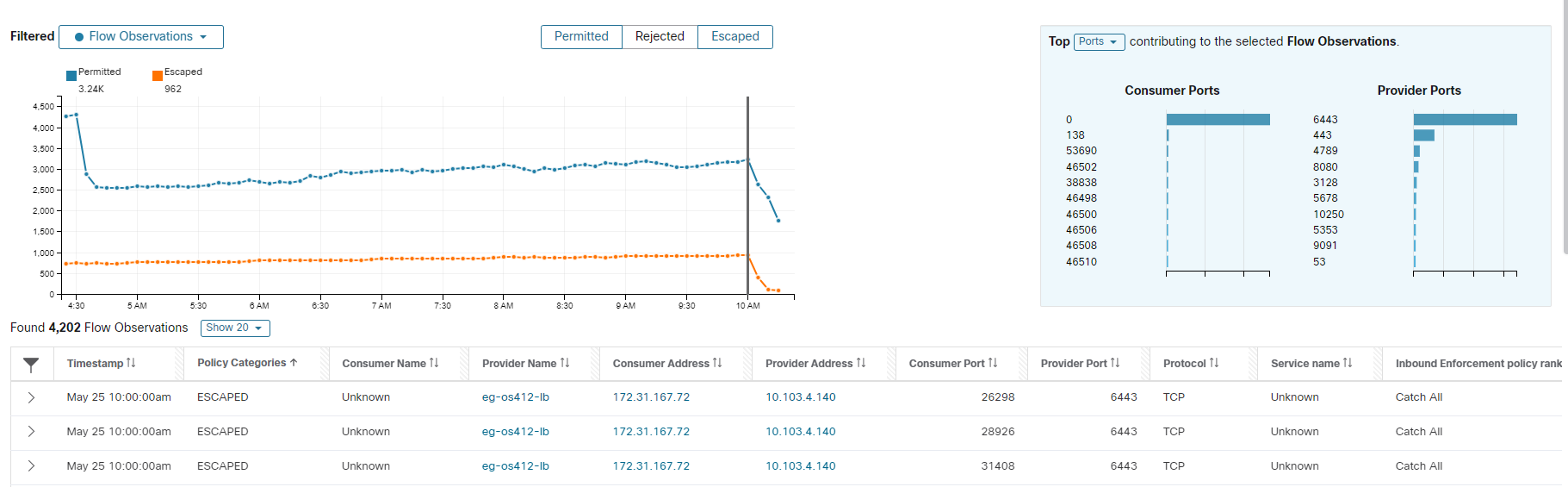
Step 3 | Click Policy Analysis. Permitted, Rejected, and Escaped traffic are displayed. For more information, see the Policy Analysis Results: Understand the Basics in the Policy Analysis Results: Understand the Basics.
|
Step 4 | Investigate Escaped flows to determine noncompliant traffic. 1. Click the violation type Escaped. Escaped flows can occur for many reasons other than noncompliant traffic. Eliminate these possibilities before investigating the actual traffic:
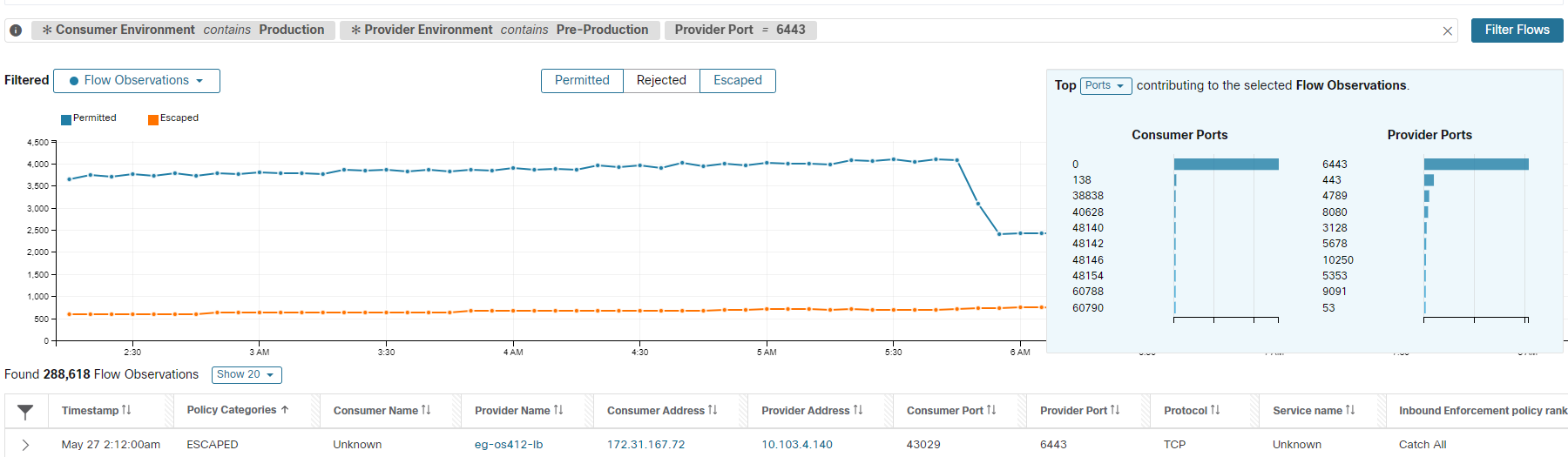
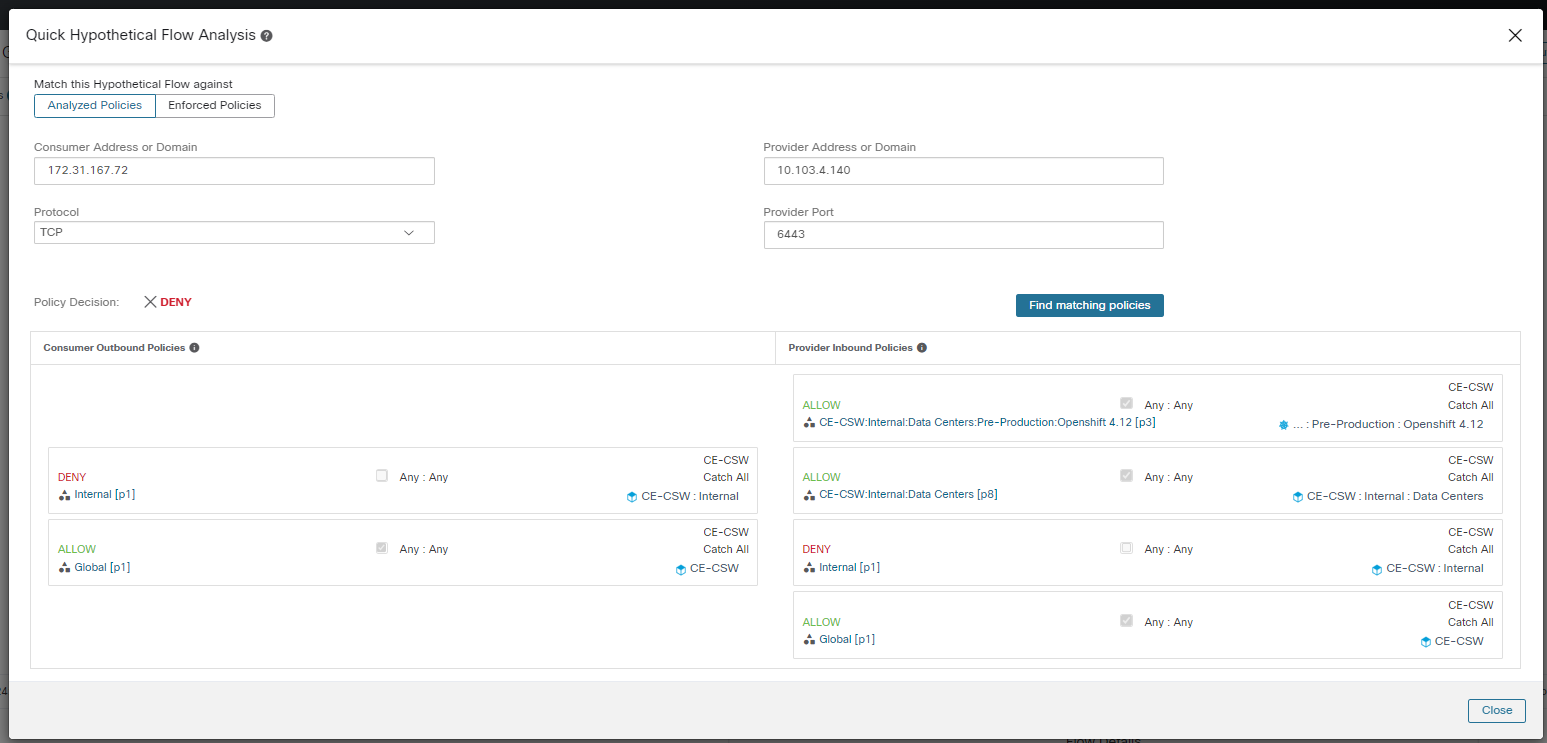
After you eliminate the above reasons, start investigating the flow for noncompliant traffic: 2. Use Filter Flows to filter using the consumer and provider names. If the flow is legitimate, but does not have explicit Allow policies, add appropriate explicit policies in the corresponding inbound or outbound scopes. If the flow is suspicious, identify it quickly, and investigate the details further. To focus on these flows, apply filters based on the
|
Step 5 | If the traffic is intended to be noncompliant, it needs to be denied. Enforce the policies and the traffic will be denied, go to Step 8. |
Step 6 | After analyzing the policies, update the policies based on your analysis. If the traffic is noncompliant do the following:
|
Step 7 | You can iteratively discover policies, as required. Each time you rediscover policies, you must review and analyze them. Before you rerun automatic policy discovery, ensure that you approve the policies and clusters that you want to retain. |
Step 8 | When you are ready, enforce policies. After you determine that the policies associated with a workspace (and hence, the associated scope) are appropriate and will block unwanted traffic while not interrupting essential services, you can enforce those policies. You can iteratively enforce policies, for example, you may choose to initially enforce only the manually created policies in the scopes near the top of your tree and, over time, enforce the discovered policies in the scopes lower in the tree. For more information, see Enforce Policies. |
What's next
You can configure alerts to notify any noncompliant traffic, policy violations or other critical issues. Cisco Secure Workload provides various alert types. For more information, see Configure Alerts.
The segmentation compliance score on the security dashboard provides a high-level view of the permitted and rejected traffic. For more information, see View Security Dashboard.
Conclusion
This use case shows how an administrator uses Cisco Secure Workload effectively to identify and isolate noncompliant traffic.
This helps the financial company to be compliant with regulations, protect sensitive data, and prevent financial loss because of malicious activities.
Full Cisco Trademarks with Software License
THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
All printed copies and duplicate soft copies of this document are considered uncontrolled. See the current online version for the latest version.
Cisco has more than 200 offices worldwide. Addresses and phone numbers are listed on the Cisco website at www.cisco.com/go/offices.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: https://www.cisco.com/c/en/us/about/legal/trademarks.html. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1721R)