Integrating Your Appliance with Cisco Threat Response
This topic contains the following sections:
Integrating with Cisco Threat Response
You can integrate your appliance with Cisco Threat Response, and perform the following actions in Cisco Threat Response:
-
View the email and web reporting data from multiple appliances in your organization.
-
Identify, investigate and remediate threats observed in the email reports, message tracking and web tracking.
-
Resolve the identified threats rapidly and provide recommended actions to take against the identified threats.
-
Document the threats to save the investigation, and enable collaboration of information among other devices.
To integrate your appliance with Cisco Threat Response, you need to register your appliance with Cisco Threat Response.
You can access Cisco Threat Response using the following URLs:
 Note |
If you access Cisco Threat Response using a regional URL - https://visibility.apjc.amp.cisco.com, the Cisco Threat Response integration with your appliance is not currently supported. |
Before you begin
-
Make sure that you create a user account in Cisco Threat Response with admin access rights. To create a new user account, go to Cisco Threat Response login page using the following URL - https://visibility.amp.cisco.com and click Create a Cisco Security account in the login page. If you are unable to create a new user account, contact Cisco TAC for assistance.
-
Make sure that you enable Cisco Threat Response integration on the Cisco Security Services Exchange (SSE) portal. For more information, go to https://securex.us.security.cisco.com/settings/modules/available, navigate to the module to integrate with Cisco Threat Response, click Add New Module, and see the instructions on the page.
-
Make sure that you open HTTPS (In and Out) 443 port on the firewall for the following FQDNs to register your appliance with Cisco Threat Response:
-
api.eu.sse.itd.cisco.com (applicable for European Union (EU) users only)
-
api-sse.cisco.com (applicable for Americas users only)
-
est.sco.cisco.com (applicable for APJC, EU, and NAM users)
-
For more information, see Firewall Information.
Procedure
| Step 1 |
Log in to your appliance. |
| Step 2 |
Select Networks > Cloud Service Settings. |
| Step 3 |
Click Edit Settings. |
| Step 4 |
Check Enable. |
| Step 5 |
Choose the required Cisco Threat Response server to connect your appliance to Cisco Threat Response. |
| Step 6 |
Submit and commit your changes. |
| Step 7 |
Navigate back to the Cloud Service Settings page after few minutes to register your appliance with Cisco Threat Response. |
| Step 8 |
Obtain a registration token from Cisco Threat Response to register your appliance with Cisco Threat Response. For more information, go to https://securex.us.security.cisco.com/settings/modules/available, navigate to the module to integrate with Cisco Threat Response, click Add New Module, and see the instructions on the page. |
| Step 9 |
Enter the registration token obtained from Cisco Threat Response and click Register. |
| Step 10 |
Add your appliance as an integration module to Cisco Threat Response. For more information, go to https://securex.us.security.cisco.com/settings/modules/available, navigate to the module to integrate with Cisco Threat Response, click Add New Module, and see the instructions on the page. |
You can integrate your appliance with Cisco Threat Response using the following CLI commands:
-
threatresponseconfig—Use this command to configure the Cisco Threat Response feature on your appliance. -
cloudserviceconfig—Use this command to register the Cisco Threat Response feature on your appliance.
What to do next
-
After you add your appliance as an integration module in Cisco Threat Response, you can view the email and web reporting, and message tracking information from your appliance in Cisco Threat Response. For more information, go to https://securex.us.security.cisco.com/settings/modules/available, navigate to the module to integrate with Cisco Threat Response, click Add New Module, and see the instructions on the page.

Note
To deregister your appliance connection from Cisco Threat Response, click Deregister in the Cloud Services Settings page in your appliance.
-
If you want to switch to another Cisco Threat Response server (for example, 'Europe - api.eu.sse.itd.cisco.com'), you must first deregister your appliance from Cisco Threat Response and follow steps 1-9 of the 'Integrating the Appliance with Cisco Threat Response' procedure.
 Note |
After you have integrated your appliance with Cisco Threat Response, you do not need to integrate your Email Security appliance with Cisco Threat Response because the email and web reporting features are centralized. |
Integrating the Appliance with Cisco Threat Response using CLI
This section contains the following CLI commands:
threatresponseconfig
Description
The threatresponseconfig command is used to:
-
Enable the Cisco Threat Response feature on your appliance.
-
Disable the Cisco Threat Response feature on your appliance.
Usage
Commit: This command requires a 'commit'.
Cluster Management: This command is restricted to the machine mode.
Batch Command: This command supports a batch format.
Examples
In the following example, you can use the threatresponseconfig command to enable the Cisco Threat Response feature on your appliance.
mail1.example.com> threatresponseconfig
Choose the operation you want to perform:
- ENABLE - To enable the Cisco Threat Response feature on your appliance.
[]> enable
The Cisco Threat Response feature is currently enabled on your appliance. Use the
cloudserviceconfig command to register your appliance with the Cisco Threat
Response portal.
mail1.example.com> commit
Please enter some comments describing your changes:
[]>
Changes committed: Mon Nov 19 10:04:35 2018 GMT
In the following example, you can use the threatresponseconfig command to disable the Cisco Threat Response feature on your appliance.
mail1.example.com> threatresponseconfig
Choose the operation you want to perform:
- DISABLE - To disable the Cisco Threat Response feature on your appliance.
[]> disable
The Cisco Threat Response feature is currently disabled on your appliance.
mail1.example.com> commit
Please enter some comments describing your changes:
[]>
Changes committed: Mon Nov 19 10:04:35 2018 GMT
cloudserviceconfig
Description
The cloudserviceconfig command is used to:
-
Register your appliance with the Cisco Threat Response portal.
-
Deregister your appliance from the Cisco Threat Response portal.
-
Choose the Cisco Threat Response server to connect your appliance to the Cisco Threat Response portal.
Usage
Commit: This command does not require a 'commit'.
Cluster Management: This command is restricted to the machine mode.
Batch Command: This command supports a batch format.
Examples
In the following example, you can use the cloudserviceconfig command to register your appliance with the Cisco Threat Response portal.
mail1.example.com> cloudserviceconfig
Choose the operation you want to perform:
- REGISTER - To register the appliance with the Cisco Threat Response portal.
-SETTRS - Set the Threat Response Server to connect to the Cisco Threat Response portal.
[]> register
Enter a registration token key to register your appliance with the Cisco Threat
Response portal.
[]> de7c55f3ff0absdfsf4a25aae94dfb064642
The appliance registration is in progress.
In the following example, you can use the cloudserviceconfig command to choose the Cisco Threat Response server to connect your appliance to the Cisco Threat Response portal.
mail1.example.com> cloudserviceconfig
Choose the operation you want to perform:
- DEREGISTER - To deregister the appliance from the Cisco Threat Response
portal.
-SETTRS - Set the Threat Response Server to connect to the Cisco Threat Response portal.
[]> settrs
Available list of Threat Response Servers:
1.
2. EUROPE (api.eu.sse.itd.cisco.com)
3.AMERICAS (api-sse.cisco.com)
Enter threat response server to connect to the Cisco Threat Response portal.:
[]> 2
Selected threat response server is api.eu.sse.itd.cisco.com.
Make sure you run "commit" to make these changes active.
mail1.example.com> commit
Please enter some comments describing your changes:
[]>
Changes committed: Mon Jum 19 10:04:35 2019 GMT
In the following example, you can use the cloudserviceconfig command to deregister your appliance from the Cisco Threat Response portal.
mail1.example.com> cloudserviceconfig
The Content Security Management appliance is successfully registered with the
Cisco Threat Response portal.
Choose the operation you want to perform:
- DEREGISTER - To deregister the appliance from the Cisco Threat Response
portal.
-SETTRS - Set the Threat Response Server to connect to the Cisco Threat Response portal.
[]> deregister
Do you want to deregister your appliance from the Cisco Threat Response portal.
If you deregister, you will not be able to access the Cloud Service features. [N]> yes
The Content Security Management appliance deregistration is in progress.
Performing Threat Analysis using Casebooks
The casebook and pivot menu are widgets available in Cisco Threat Response.
Casebook - It is used to record, organize, and share sets of observables of interest primarily during an investigation and threat analysis. You can use a casebook to get the current verdicts or dispositions on the observables. For more information, see the Cisco Threat Response documentation at https://visibility.amp.cisco.com/#/help/casebooks.
Pivot Menu - It is used to pivot an observable to a new case, an existing case, or to other devices registered in Cisco Threat Response (for example, AMP for Endpoints, Cisco Umbrella, Cisco Talos Intelligence, and so on) to investigate for threat analysis. For more information, see the Cisco Threat Response documentation at https://visibility.amp.cisco.com/#/help/pivot-menus.
The Content Security Management appliance now includes the casebook and pivot menu widgets. You can perform the following actions in your appliance using the casebook and pivot menu widgets:
-
Add an observable to a casebook to investigate for threat analysis.
-
Pivot an observable to a new case, an existing case, or other devices registered in Cisco Threat Response (for example, AMP for Endpoints, Cisco Umbrella, Cisco Talos Intelligence, and so on) to investigate for threat analysis.
The following is a list of observables supported for this release:
-
IP addresses
-
Domains
-
URLs
-
File Hashes (SHA-256 only)
 Note |
|
Related Topics
Obtaining Client ID and Client Password Credentials
You need the client ID and client password to access the casebook and pivot menu widgets on your appliance.
Before you begin
Make sure that you meet all the prerequisites mentioned in the ‘Before you begin’ section of Integrating with Cisco Threat Response
Procedure
| Step 1 |
Log in to the new web interface of your appliance. For more information, see Accessing the Web Interface. |
||
| Step 2 |
Click the Casebook
|
||
| Step 3 |
Add a new API Client. |
||
| Step 4 |
Enter the client ID and client password obtained in Step 3 in the ‘Login to use Casebook/Pivot Menu’ dialog box in your appliance. |
||
| Step 5 |
Select the required Cisco Threat Response server in the ‘Login to use Casebook/Pivot Menu’ dialog box. |
||
| Step 6 |
Click Authenticate.
|
What to do next
Add an observable to a casebook to investigate for threat analysis. See Adding Observable to Casebook for Threat Analysis.
Adding Observable to Casebook for Threat Analysis
Before you begin
Make sure that you obtain the client ID and client password to access the casebook and pivot menu widgets on your appliance. For more information, see Obtaining Client ID and Client Password Credentials.
Procedure
| Step 1 |
Log in to the new web interface of your appliance. For more information, see Accessing the Web Interface. |
| Step 2 |
Navigate to the Email Reporting or Web Reporting page, click on the pivot menu 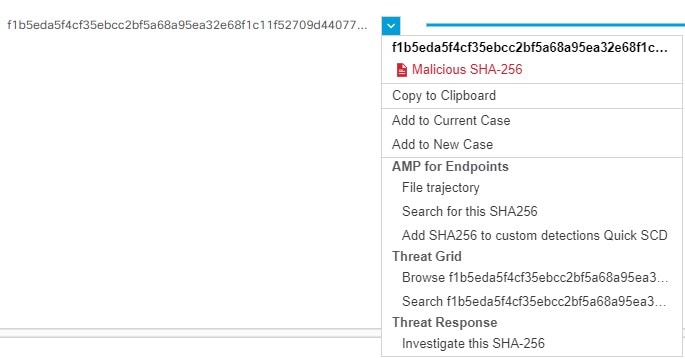
|
| Step 3 |
Click the Casebook
|
| Step 4 |
(Optional) Click |
| Step 5 |
Click Investigate this Case to investigate the observable for threat analysis. For more information, see the Cisco Threat Response documentation at https://visibility.amp.cisco.com/#/help/introduction. |
 button.
button.
 button to add a title, description, or notes to the casebook.
button to add a title, description, or notes to the casebook.
 Feedback
Feedback