Create a Connector
A connector is an interface with a cloud service. The connector retrieves network information from the cloud service so the network information can be used in access control policies on the FMC.
We support the following:
|
CSDAC version/platform |
A.W.S. |
Git- Hub |
Google Cloud |
Azure |
Azure Service Tags |
Microsoft Office 365 |
VMware vCenter |
|---|---|---|---|---|---|---|---|
|
Version 1.1 (on-premises) |
Yes |
No |
No |
Yes |
Yes |
Yes |
Yes |
|
Version 2.0 (on-premises) |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Cloud-delivered (Cisco Defense Orchestrator) |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
No |
See one of the following sections for more information.
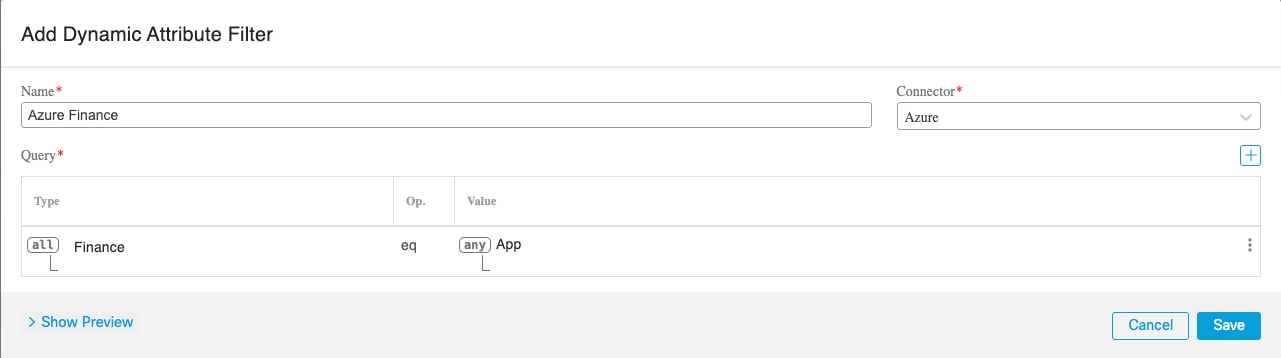
Create an Azure Service Tags Connector
This topic discusses how to create a connector for Azure service tags to the FMCfor use in access control policies. The IP addresses association with these tags are updated every week by Microsoft.
For more information, see Virtual network service tags on Microsoft TechNet.
Procedure
| Step 1 |
Log in to the FMC. |
||||||||||||||||
| Step 2 |
Click . |
||||||||||||||||
| Step 3 |
Click Connectors. |
||||||||||||||||
| Step 4 |
Do any of the following:
|
||||||||||||||||
| Step 5 |
Enter the following information.
|
||||||||||||||||
| Step 6 |
Click Save. |
||||||||||||||||
| Step 7 |
Make sure Ok is displayed in the Status column. |
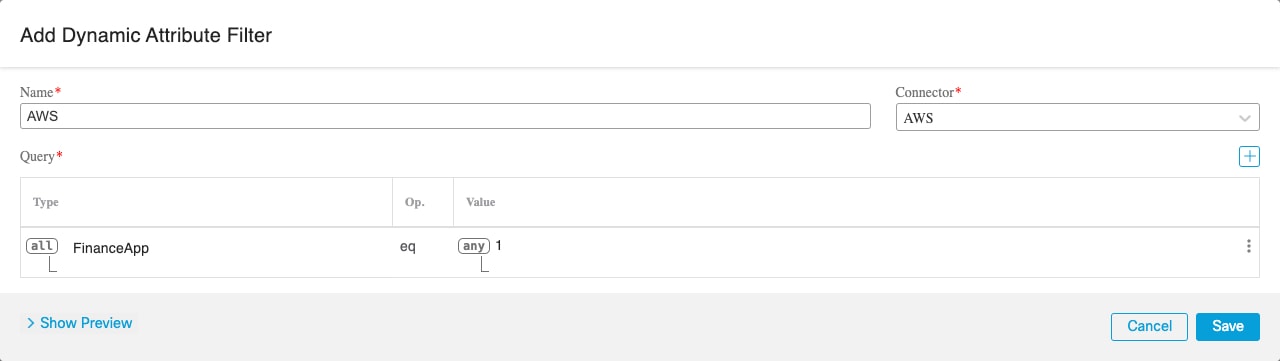
Create an Office 365 Connector
This task discusses how to create a connector for Office 365 tags to send data to the FMC for use in access control policies. The IP addresses associated with these tags are updated every week by Microsoft. You do not have to create a dynamic attributes filter to use the data.
For more information, see Office 365 URLs and IP address ranges on docs.microsoft.com.
Procedure
| Step 1 |
Log in to the dynamic attributes connector. |
||||||||||||||
| Step 2 |
Log in to the FMC. |
||||||||||||||
| Step 3 |
Click . |
||||||||||||||
| Step 4 |
Click Connectors. |
||||||||||||||
| Step 5 |
Do any of the following:
|
||||||||||||||
| Step 6 |
Enter the following information.
|
||||||||||||||
| Step 7 |
Click Save. |
||||||||||||||
| Step 8 |
Make sure Ok is displayed in the Status column. |
vCenter Connector—About User Permissions and Imported Data
The Cisco Secure Dynamic Attributes Connector imports dynamic attributes from vCenter to the FMC for use in access control policies.
Dynamic attributes imported
We import the following dynamic attributes from vCenter:
-
Operating system
-
MAC address
-
IP addresses
-
NSX tags
Minimum permissions required
The Cisco Secure Dynamic Attributes Connector requires a user at minimum with the Read Only permission to be able to import dynamic attributes.
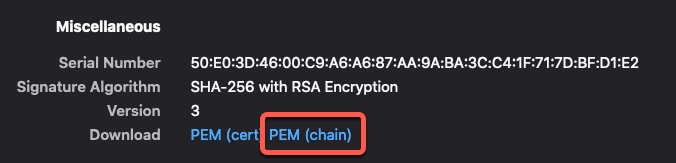
Fetch a Certificate Authority (CA) Chain for a vCenter Connector
This topic discusses how to automatically fetch the certificate authority chain for a connector or an adapter. The certificate authority chain is the root certificate and all subordinate certificates; it is required to connect securely with vCenter or the FMC.
The dynamic attributes connector enables you to automatically fetch the certificate authority chain but if this procedure does not work for some reason, see Manually Get a Certificate Authority (CA) Chain.
Procedure
| Step 1 |
Log in to the dynamic attributes connector. |
| Step 2 |
Do any of the following:
|
| Step 3 |
In the Name field, enter a name to identify the connector or adapter. |
| Step 4 |
In the Host field, enter the connector or adapter's host name or IP address without the scheme (such as https:// ). For example, myvcenter.example.com or 192.0.2.100:9090 The host name or IP you enter must exactly match the Common Name of the CA certificate used to securely connect to it. No other information is required to fetch the certificate CA chain. |
| Step 5 |
Click Fetch. |
| Step 6 |
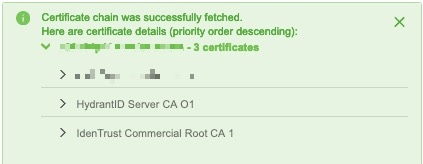
(Optional.) Expand the certificates in the certificate CA chain to verify them. |
Example
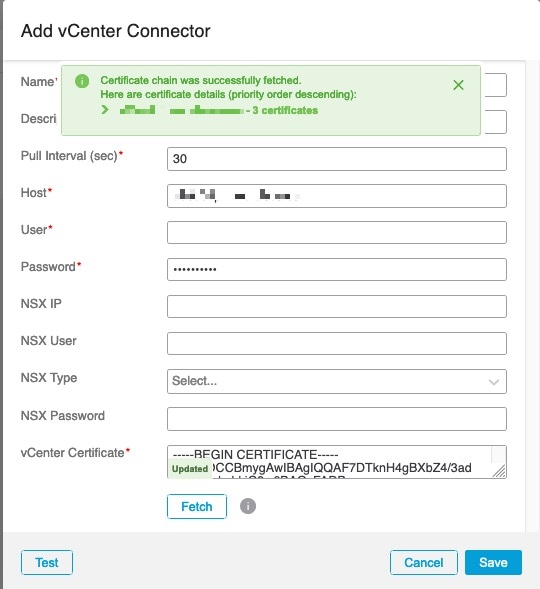
Expanding the certificate CA chain at the top of the dialog box displays the certificates similar to the following.
Create a vCenter Connector
This task discusses how to create a connector for VMware vCenter to send data to the FMC for use in access control policies.
Before you begin
If you use non-trusted certificates to communicate with vCenter, see Manually Get a Certificate Authority (CA) Chain.
Procedure
| Step 1 |
Log in to the dynamic attributes connector. |
||||||||||||||||||||||||
| Step 2 |
Log in to the FMC. |
||||||||||||||||||||||||
| Step 3 |
Click Connectors. |
||||||||||||||||||||||||
| Step 4 |
Click . |
||||||||||||||||||||||||
| Step 5 |
Do any of the following:
|
||||||||||||||||||||||||
| Step 6 |
Enter the following information.
|
||||||||||||||||||||||||
| Step 7 |
Click Save. |
 )
) )
) )
)

 )
) )
)
 Feedback
Feedback