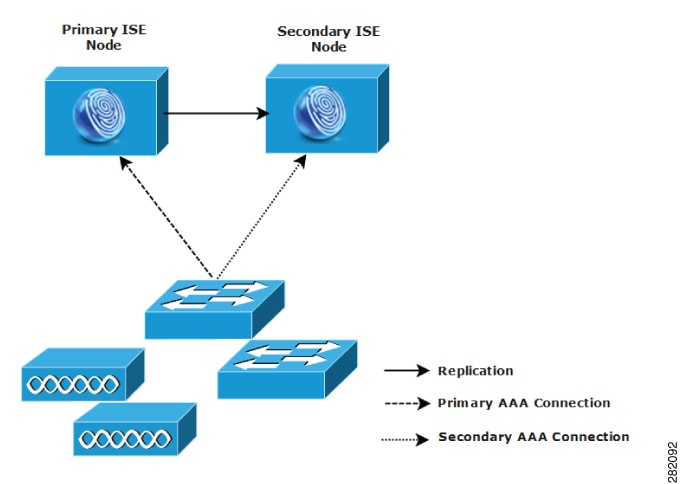
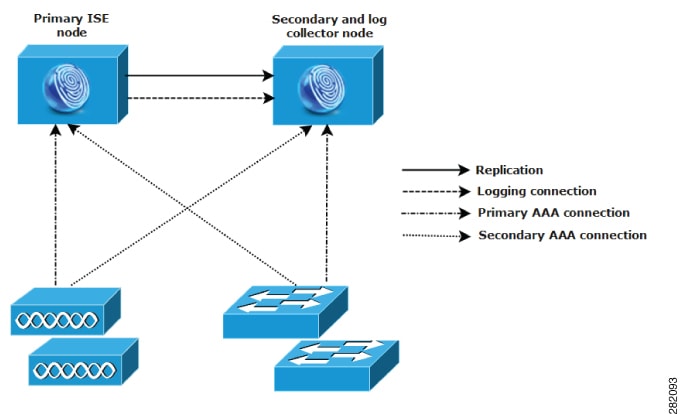
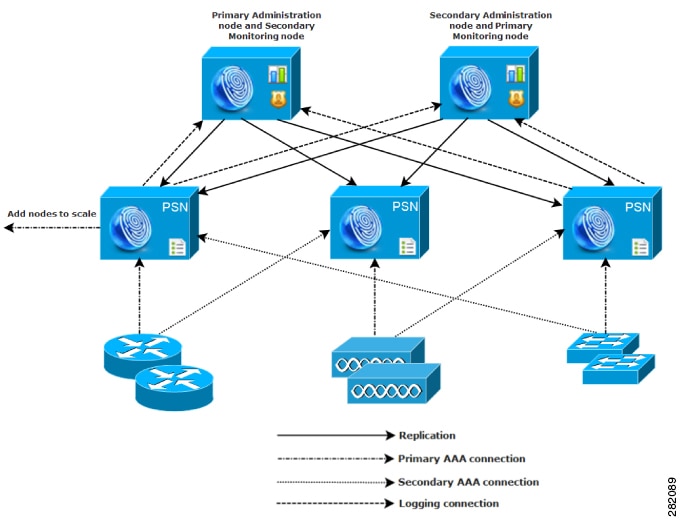
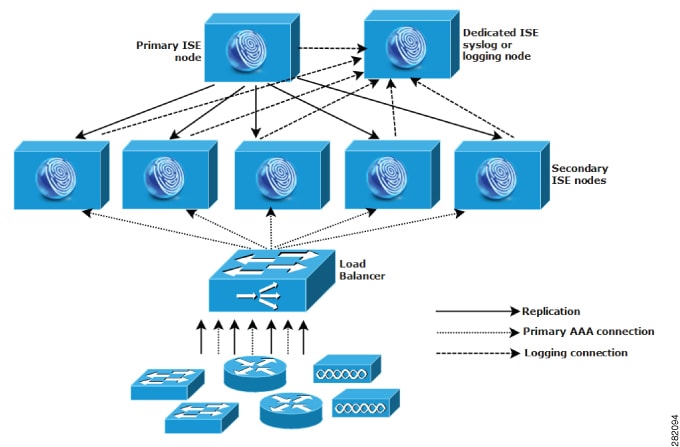
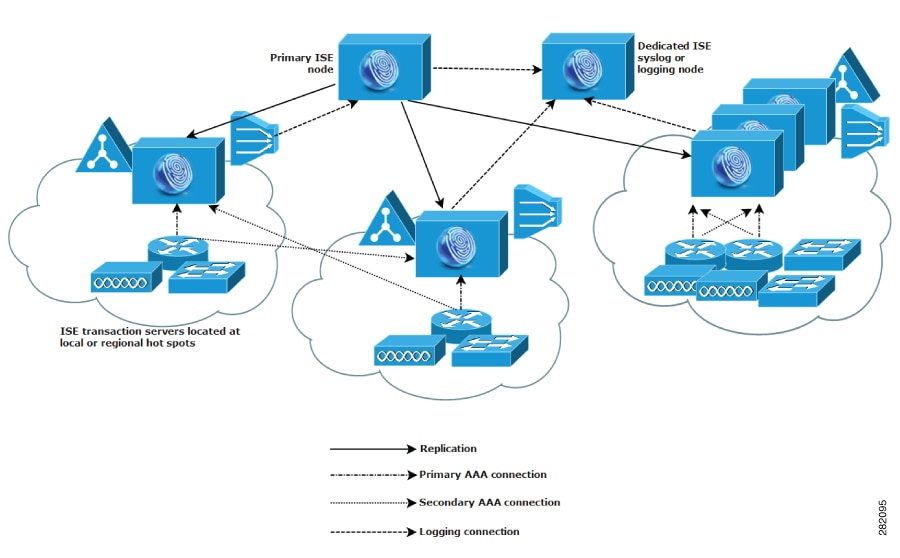
Cisco ISE network architecture
Cisco ISE architecture includes these components:
-
Nodes and persona types
A Cisco ISE node can assume any or all of these personas:
-
Administration
-
Policy Service
-
Monitoring
-
pxGrid
-
-
Network resources
-
Endpoints
The policy information point is where external information is communicated to the Policy Service persona. For example, external information might be a Lightweight Directory Access Protocol (LDAP) attribute.

 Feedback
Feedback