Overview
This document lists the sizing guidelines for Cisco Identity Services Engine (Cisco ISE).
Change history
This table lists changes to this document since its initial release.
|
Date |
Change |
Location |
|---|---|---|
|
2025-09-24 |
Updated Workload Connector scaling details for Cisco SNS 3815 |
|
|
Updated maximum concurrent active sessions for Cisco ISE 3.5 |
||
|
Updated TACACS+ performance details |
||
|
Updated list of supported AWS instance types |
||
|
2025-07-15 |
Added scaling details for Cisco SNS 3800 appliances |
|
|
2025-04-04 |
Added best practices for optimized performance |
|
|
2025-03-27 |
Added information about the maximum number of validated endpoints in the Cisco ISE database. |
|
|
2024-12-16 |
Added Workload Connector scaling details for Cisco ACI connections |
Cisco ISE and Cisco Application Centric Infrastructure scaling |
|
Added Workload Connector scaling details for Azure, AWS, GCP, and vCenter connections |
Cisco ISE node terminology
A Cisco ISE node provides various services based on the persona that it assumes. The Admin portal displays menu options based on the node's role and persona.
|
Node type |
Description |
|---|---|
|
Policy Administration Node (PAN) |
A Cisco ISE node with the Administration persona allows you to perform all administrative operations and configurations. It serves as a centralized interface for viewing all administrative activities and contextual data. The node synchronizes its configuration with other nodes in the deployment. |
|
Policy Service Node (PSN) |
A Cisco ISE node with the Policy Service persona provides network access, posture, guest access, client provisioning, and profiling services. This persona evaluates the policies and makes all the decisions. |
|
Monitoring Node (MnT) |
A Cisco ISE node with the Monitoring persona collects and stores log messages from all Administration and Policy Service nodes. It provides advanced monitoring and troubleshooting tools for effective network and resource management. The node aggregates and correlates collected data to generate meaningful reports. |
|
pxGrid node |
You can use Cisco pxGrid to share context-sensitive information from Cisco ISE session directory with other network systems such as Cisco ISE ecosystem partner systems and other Cisco platforms. The pxGrid framework can also be used to exchange policy and configuration data between nodes (such as sharing tags and policy objects between Cisco ISE and third-party vendors) and for other information exchanges. |
Cisco ISE deployments
A deployment is one or more Cisco ISE nodes connected together in a cluster (distributed system).
A deployment that has a single Cisco ISE node is called a standalone deployment. This node runs all the personas. Standalone deployment is not recommended for production because redundancy is not provided.
A distributed deployment consists of more than one Cisco ISE node. In this configuration, multiple nodes are set up to improve performance and provide failover support. Administration and monitoring are centralized, while processing is distributed across the Policy Service nodes. You can scale your deployment to meet your performance requirements.
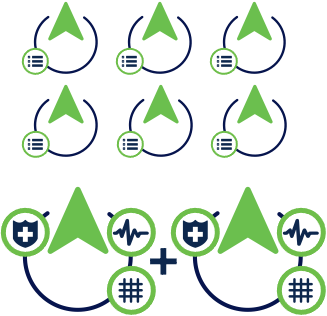
This table lists the types of Cisco ISE deployment.
|
Standalone |
Small deployment |
Medium deployment |
Large deployment |
||
|---|---|---|---|---|---|

|

|
|
|
Sizing guidelines for Cisco ISE deployment
You can choose the right ISE deployment by considering the maximum scale numbers for active endpoints in each deployment type, the scale supported by individual PSN nodes, and other relevant factors described in this section.
Each endpoint with a unique MAC address counts as one active session. Concurrent active sessions are supported for all types of sessions, including Dot1x, MAB, Guest, BYOD, and Posture.
The maximum number of active sessions shown in this table was determined by tests performed under these conditions:
-
Cisco ISE deployments are formed in a single data center deployed in same region, low latency (less than 5 ms) between the ISE internode communications, Dot1x authentications and accounting events generated by endpoints in the range of two to four repetitions per day.
-
The majority of the sessions use RADIUS protocols to authenticate with local ID providers.
ISE deployment scale
These tables show the maximum concurrent active sessions for deployments with different SNS appliances acting as PAN, MnT, or PAN/MnT.
| Deployment | Cisco SNS 3595 | Cisco SNS 3615 | Cisco SNS 3715, 3815 | Cisco SNS 3655 | Cisco SNS 3755, 3855 | Cisco SNS 3695 | Cisco SNS 3795, 3895 |
|---|---|---|---|---|---|---|---|
| Large | 500,000 | Unsupported | Unsupported | 500,000 | 750,000 | 2,000,000 | 2,000,000 |
| Medium | 20,000 | 12,500 | 75,000 | 25,000 | 150,000 | 50,000 | 150,000 |
| Small | 20,000 | 12,500 | 25,000 | 25,000 | 50,000 | 50,000 | 50,000 |
| Deployment | Cisco SNS 3615 | Cisco SNS 3715 | Cisco SNS 3815 | Cisco SNS 3655 | Cisco SNS 3755, 3855 | Cisco SNS 3695 | Cisco SNS 3795, 3895 |
|---|---|---|---|---|---|---|---|
| Large | Unsupported | Unsupported | Unsupported | 500,000 | 750,000 | 2,000,000 | 2,000,000 |
| Medium | Unsupported | Unsupported | 75,000 | 25,000 | 150,000 | 50,000 | 150,000 |
| Small | 12,500 | 25,000 | 25,000 | 25,000 | 50,000 | 50,000 | 50,000 |
 Note |
|
Policy Service Node scale
| PSN Type | Cisco SNS 3595 | Cisco SNS 3615 | Cisco SNS 3715, 3815 | Cisco SNS 3655 | Cisco SNS 3755, 3855 | Cisco SNS 3695 | Cisco SNS 3795, 3895* |
|---|---|---|---|---|---|---|---|
| Dedicated PSN (Cisco ISE node has only PSN persona) | 40,000 | 25,000 | 50,000 | 50,000 | 100,000 | 100,000 | 100,000 |
| Shared PSN (Cisco ISE node has multiple personas) | 20,000 | 12,500 | 25,000 | 25,000 | 50,000 | 50,000 | 50,000 |
*Cisco SNS 3795 and Cisco SNS 3895 are equipped with more RAM and better Disk Read/Write performance. These models are best suited for dedicated PAN, dedicated MnT, or PAN/MnT personas and provide no added value when deployed as a dedicated PSN.
 Note |
SNS 3595 is supported in Cisco ISE release 3.2 and earlier versions. |
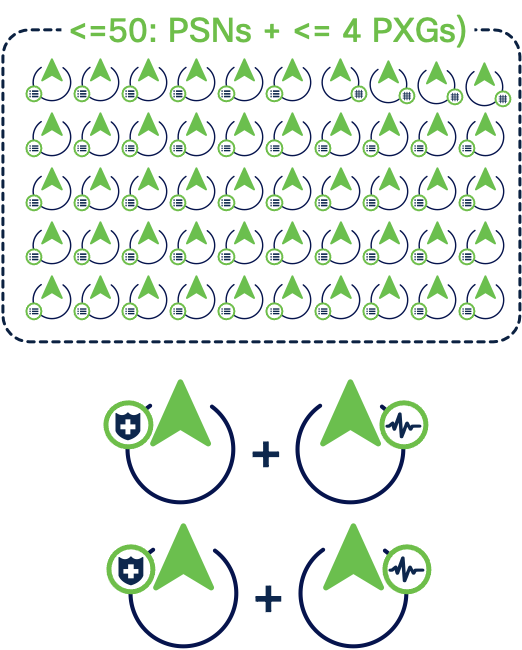
Deployment selection criteria
Consider these points when selecting a deployment:
-
You can choose small deployment for up to 50,000 concurrent active sessions and medium deployment for up to 150,000 concurrent active sessions.
-
For deployments with more than 150,000 concurrent active sessions, a large deployment is required. Register MnT nodes as Dedicated MnT nodes in large deployments.
-
Deploy PSNs closer to workloads and Identity Providers (such as AD, LDAP) for performance-sensitive loads.
-
Group PSNs for similar workloads, such as RADIUS Dot1x, Guest, BYOD, or TACACS+, and distribute traffic through load balancers.
-
For better performance, configure Calling-Station-ID (MAC)-based stickiness in the load balancer.
-
Configure PSNs in node groups if you use services that require URL redirect, such as posture services, guest services, or MDM.
-
Have multiple data centers, and group PSNs per datacenter. Configure RADIUS (primary, secondary, tertiary) failover on NAS devices. For example, if the primary data center (DC-A) fails, 50 percent of NADs can fail over to the secondary data center (DC-B), and the remaining NADs can fail over to the tertiary data center (DC-C).
-
Implement N+1 or N+2 redundancy within a PSN group.
-
Purge guest and inactive endpoints at regular intervals to prevent latency in ISE operations.
-
The maximum concurrent active session values given for each deployment are applicable for connected devices that are generating dot1x authentications up to 4 times a day.
-
For deployments where endpoints generate repeated authentication and accounting events, additional PSNs in the PSN group are required to handle heavy traffic scenarios such as simultaneous login events from a large number of users or Wi-Fi users roaming from one location to another.
-
PSN node variations include TACACS+ PSN, TC-NAC PSN, Guest PSN (GPSN), Cisco TrustSec PSN, Security Group eXchange Protocol PSN, and PassiveID PSN. For better performance, reserve TACACS+, RADIUS, Guest, BYOD workloads to dedicated PSN groups within a deployment.
-
Assign separate Cisco TrustSec PSNs to handle TrustSec functions in TrustSec deployments. This prevents overloading RADIUS PSNs when pushing policies.
-
For large-scale NAC environments with many Device Administration tasks, such as frequent script usage or network management systems, split deployments and use a separate deployment for Device Administration (TACACS+).
RADIUS authentication rates
This table shows the authentication rates for RADIUS protocols when a Cisco ISE node acts as a single dedicated PSN in a deployment.
| Authentication method | Cisco SNS 3615, 3715, 3815 | Cisco SNS 3595 | Cisco SNS 3655, 3755, 3695, 3795, 3855, 3895 |
|---|---|---|---|
| PAP with internal user database | 900 | 1100 | 1300 |
| PAP with Active Directory | 250 | 250 | 300 |
| PAP with LDAP directory | 300 | 300 | 350 |
| PEAP (MSCHAPv2) with internal user database | 150 | 150 | 200 |
| PEAP (MSCHAPv2) with Active Directory | 150 | 150 | 175 |
| PEAP (GTC) with internal user database | 150 | 150 | 250 |
| PEAP (GTC) with Active Directory | 100 | 150 | 175 |
| EAP-FAST (MSCHAPv2) with internal user database | 350 | 400 | 500 |
| EAP-FAST (MSCHAPv2) with Active Directory | 200 | 250 | 300 |
| EAP-FAST (GTC) with internal user database | 350 | 400 | 450 |
| EAP-FAST (GTC) with Active Directory | 200 | 200 | 300 |
| EAP-FAST (GTC) with LDAP directory | 200 | 300 | 300 |
| EAP-TLS with internal user database | 150 | 150 | 200 |
| EAP-TLS with Active Directory | 150 | 150 | 200 |
| EAP-TLS with LDAP directory | 150 | 200 | 200 |
| EAP TEAP with internal user database | 100 | 100 | 200 |
| MAB with internal user database | 500 | 900 | 1000 |
| MAB with LDAP directory | 400 | 500 | 600 |
| EAP-TTLS PAP with Microsoft Entra ID |
30 |
30 |
50 |
|
EAP-TLS with Microsoft Entra ID |
40 |
40 |
50 |
 Note |
|
TACACS+ network devices scaling
This table shows the maximum network device entries in Admin > Network Resources > Network Devices for deployments with different SNS appliances acting as shared or dedicated PAN.
|
Deployment |
Cisco SNS 3615, 3715 |
Cisco SNS 3815 |
Cisco SNS 3655, 3755 |
Cisco SNS 3855 |
Cisco SNS 3695, 3795, 3895 |
|---|---|---|---|---|---|
|
Large |
Unsupported |
Unsupported |
50,000 |
100,000 |
200,000 |
|
Medium |
2500 |
5000 |
25,000 |
50,000 |
50,000 |
|
Small |
1000 |
2500 |
10,000 |
10,000 |
10,000 |
 Note |
|
TACACS+ performance for Policy Service Node
This table shows the maximum TACACS+ TPS processed by dedicated PSNs, including authentication, authorization, or accounting events.
These values are measured per dedicated PSN for PAP and CHAP protocols and apply to both TACACS+ Single Connect and non-Single Connect modes.
|
Scenario |
Cisco SNS 3595, 3615, 3715 |
Cisco SNS 3655, 3695, 3815 |
Cisco SNS 3755, 3795, 3855, 3895 |
|---|---|---|---|
|
TACACS+ AAA events with internal identity store |
2500 |
3000 |
3200 |
|
TACACS+ AAA events with external identity store (AD/LDAP) |
2000 |
2400 |
2500 |
|
TACACS+ TLS 1.3 AAA events with internal identity store |
800 |
1000 |
1500 |
|
TACACS+ TLS 1.3 AAA events with external identity store (AD/LDAP) |
640 |
800 |
1200 |
 Note |
|
TACACS+ performance in Cisco ISE deployment
The MnT nodes process the events from all PSNs and are essential for managing operational data effectively.
In deployments where real-time monitoring of MnT live logs is critical and any latency in live logs or reporting is unacceptable, performance must be governed based on deployment-wide transactions per second, as detailed in this section.
|
Deployment |
Cisco SNS 3615, 3715 |
Cisco SNS 3815 |
Cisco SNS 3655, 3755 |
Cisco SNS 3695, 3855 |
Cisco SNS 3795, 3895 |
|---|---|---|---|---|---|
|
Large (dedicated MnT) |
Unsupported | Unsupported | 1500 | 2000 | 2500 |
|
Medium (MnT shared with PAN persona) |
50 | 100 | 700 | 1000 | 1250 |
|
Small (all persona) |
50 | 100 | 150 | 250 | 300 |
 Note |
|
Scenario-specific authentication rates
This table shows the transactions per second (TPS) when Cisco ISE node is acting as a single dedicated PSN in a deployment for different scenarios.
The authentication values provided in this table may have + or - 5 percent deviation in production environment.
| Scenario | Cisco SNS 3615, 3715, 3815 | Cisco SNS 3595 | Cisco SNS 3655, 3755, 3695, 3795, 3855, 3895 |
|---|---|---|---|
| Posture authentication | 50 | 50 | 60 |
| Guest Hotspot authentication | 75 | 100 | 150 |
| Guest Sponsored authentication | 50 | 75 | 75 |
| BYOD Onboarding single SSID | 10 | 10 | 15 |
| BYOD Onboarding dual SSID | 10 | 15 | 15 |
| MDM | 150 | 200 | 350 |
| Internal CA certificate issuance | 50 | 50 | 50 |
| New endpoints profiled per second/profile updates per second | 200 | 250 | 250 |
| Maximum PassiveID sessions processed per second | 1000 | 1000 | 1000 |
|
Sessions published per second to pxGrid subscribers |
300 | 400 | 400 |
|
RADIUS VPN flow with Duo MFA |
10 |
N/A |
40 |
|
TACACS+ flow with Duo MFA |
20 |
N/A |
20 |
 Note |
Cisco ISE integration with Duo MFA for RADIUS and TACACS+ flows is applicable from Cisco ISE 3.3 Patch 1 onwards. The authentication rates are applicable to deployments, where the latency between Cisco ISE and Duo is 4 or 5 seconds. |
| Scenario | Cisco SNS 3615, 3715, 3815 | Cisco SNS 3595 | Cisco SNS 3655, 3755, 3695, 3795, 3855, 3895 |
|---|---|---|---|
| Time taken to push 300 TrustSec policies to 254 NADs | 50 | 50 | 50 |
| Time taken for 5000 TrustSec policies to download 2GB data via REST API | 50 | 50 | 50 |
| Time taken to connect SXP to SXPSN | 10 | 5 | 5 |
| Time taken for ERS Endpoints Bulk API for 1000 endpoints | 15 | 10 | 10 |
| Time taken for ERS Guest Bulk API for 1000 endpoints | 15 | 10 | 10 |
| Time taken for ERS: Trustsec Bulk API for 1000 endpoints | 200 | 200 | 100 |
|
Time taken for pxGrid ANC APIs to quarantine or unquarantine 10,000 endpoints (with 100 requests per second) |
120 |
120 |
120 |
Cisco ISE deployment scale limits
| Attribute | Maximum limit |
|---|---|
| Maximum pxGrid nodes in Large or Dedicated deployment | 4 |
| Maximum pxGrid subscribers per pxGrid node |
Cisco SNS 3695, 3795, or 3895 as dedicated/shared pxGrid node: 200 Cisco SNS 3655, 3755, or 3855 as dedicated/shared pxGrid node: 50 Cisco SNS 3615, 3715, or 3815 as dedicated/shared pxGrid node: 5 |
| Dedicated PSN with SXP service enabled | 8 nodes, or 4 pairs |
| Maximum ISE SXP peers per PSN with SXP service enabled | 200 |
| Maximum network device entries* | See TACACS+ network devices scaling |
| Maximum network device groups (NDG) | 10,000 |
| Maximum Active Directory forests (Join Points) | 50 |
| Maximum Active Directory controllers (WMI query) | 100 |
| Maximum internal users | 300,000 |
| Maximum internal guests** | 1,000,000 |
| Maximum user certificates | 1,000,000 |
| Maximum server certificates | 1,000 |
| Maximum trusted certificates | 1,000 |
| Maximum concurrent active endpoints/sessions |
Cisco SNS 3695, 3795, or 3895 as dedicated PAN or MnT: 2,000,000 Refer to Sizing guidelines for Cisco ISE deployment for other appliance combinations |
|
Maximum validated endpoints in the Cisco ISE database (including both active and inactive endpoints)*** |
Cisco SNS 3695, 3795, or 3895 as dedicated/shared PAN: 4,000,000 Cisco SNS 3655 as dedicated/shared PAN: 1,000,000 Cisco SNS 3755 or 3855 as dedicated/shared PAN: 1,500,000 Cisco SNS 3715 or 3815 as shared PAN: 50,000 Cisco SNS 3615 as shared PAN: 25,000 |
| Maximum policy sets | 200 |
| Maximum authorization rules**** |
3000 (3,200 authorization profiles) |
| Maximum authentication rules | 1000 |
| Maximum attribute-value (AV) pairs | 64 |
| Maximum user identity groups | 1,000 |
| Maximum endpoint identity groups | 1,000 |
| TrustSec Security Group Tags (SGTs)
TrustSec SGTs on Cisco SNS 3655/3755 and later models from Cisco ISE release 3.4 patch 1 onwards |
10,000
50,000 |
| TrustSec Security Group ACLs (SGACLs) | 1,000 |
| TrustSec IP-SGT Static Bindings (over SSH) | 10,000 |
| Maximum concurrent REST API connections |
ERS API: 100 OpenAPI: 150 |
|
Maximum PassiveID sessions for Large deployment |
Cisco SNS 3695, 3795, or 3895 as PAN, MnT: 2,000,000 Cisco SNS 3595 as PAN, MnT: 500,000 Cisco SNS 3655 as PAN, MnT: 500,000 Cisco SNS 3755 or 3855 as PAN, MnT: 750,000 |
|
Maximum network latency between primary PAN and any other Cisco ISE node including the secondary PAN, MnT, and PSNs |
300 milliseconds |
|
Maximum IPSec tunnels per dedicated PSN |
150 |
|
Maximum PassiveID sessions providers |
|
|
Maximum AD Domain Controllers Maximum REST API Providers Maximum Syslog Providers |
100 50 70 |
|
MnT API Performance |
|
|
MnT API requests per second in Medium deployment |
Cisco SNS 3655, 3755, or 3855: 10 Cisco SNS 3695, 3795, or 3895: 200 |
|
MnT API requests per second for Large deployment |
Cisco SNS 3655, 3755, or 3855: 100 Cisco SNS 3695, 3795, or 3895: 400 |
|
Time taken by MnT API to download 200,000 endpoints in Medium and Large deployments |
40 seconds |
**Having more than 500,000 guest users might create latency in user authentication.
***Sample use case: Cisco SNS 3795 can support a maximum of 2,000,000 active endpoints/sessions (as stated in Sizing guidelines for Cisco ISE deployment). In addition, it can handle a maximum of 2,000,000 inactive endpoints, resulting in a total of 4,000,000 endpoints in the Cisco ISE database for large deployments. For medium deployments, it can handle up to 150,000 active endpoints/sessions and 3,850,000 inactive endpoints. For small deployments it can handle up to 50,000 active endpoints/sessions and 3,950,000 inactive endpoints.
****It is not recommended to have more than 600 authorization rules in a single policy set. Increasing the number of conditions per authorization rule might impact the performance.
Cisco ISE SXP scaling
|
Deployment Type |
Platform |
Max PSNs |
Max ISE SXP bindings |
Max ISE SXP Listener peers |
|---|---|---|---|---|
|
Standalone (all personas on same node) 2 nodes redundant |
3595 | 0 | 20,000 | 30 |
| 3615 | 0 | 12,500 | 30 | |
| 3655, 3715, 3815 | 0 | 25,000 | 40 | |
| 3695, 3755, 3795, 3855, 3895 | 0 | 50,000 | 50 | |
| Unified PAN+MnT on same node and dedicated PSNs | 3595 as PAN and MnT | 6 | 20,000 | 200 |
| 3655 as PAN and MnT | 6 | 25,000 | 200 | |
| 3695 as PAN and MnT | 6 | 50,000 | 200 | |
| 3715 or 3815 as PAN and MnT | 6 | 75,000 | 200 | |
| 3755,3795, 3855, or 3895 as PAN and MnT | 6 | 150,000 | 200 | |
| Dedicated (all personas on dedicated nodes) | 3595 as PAN and MnT | 50 |
350,000 (1 pair) 500,000 (2 pairs) |
200 (1 pair) 400 (2 pairs) |
| 3655 as PAN and MnT | 50 |
350,000 (1 pair) 500,000 (2 pairs) |
200 (1 pair) 400 (2 pairs) |
|
| 3695, 3755, 3795, 3855, or 3895 as PAN and Large MnT | 50 |
350,000 (1 pair) 700,000 (2 pairs) 1,050,000 (3 pairs) 1,400,000 (4 pairs) |
200 (1 pair) 400 (2 pairs) 600 (3 pairs) 800 (4 pairs) |
Cisco ISE pxGrid Direct scaling
This section specifies the time taken for Cisco ISE pxGrid Direct connector integration via URL Fetcher and URL Pusher for different scales of endpoints.
|
Scenario |
Cisco ISE 3.2 Patch 2/3.3 |
Cisco ISE 3.4 and later |
|---|---|---|
|
Time taken in minutes to download and replicate 500,000 endpoints with total data size of 500 MB from configuration management database (CMDB) server to all PSN nodes |
120 |
20 |
|
Time taken in minutes to download and replicate 1,000,000 endpoints with total data size of 1 GB from CMDB server to all PSN nodes |
360 |
30 |
|
Time taken in minutes to download and replicate 2,000,000 endpoints with total data size of 2 GB from CMDB server to all PSN nodes |
480 |
60 |
 Note |
|
|
Scenario |
Time in minutes |
|---|---|
|
Time taken to download and replicate 500,000 endpoints data to all PSN nodes |
30 |
The data presented in this table is based on these conditions:
-
Number of requests: 1
-
Endpoints per request: 10,000
-
Attributes per endpoint: 17
-
Total payload: <= 5 MB
-
Inter-request delay: 30 seconds between each request
Best practices for optimized performance
-
Ensure that the total request payload size is not more than 5 MB. You might see this error when this limit is exceeded:
"Response: Size limit exceeded 5 MB, Bad Request"
-
It is recommended to maintain a 30-second delay between each request. Insufficient delay between requests may lead to rate-limiting errors (for example, "Response: Too Many Requests").
-
Monitor response errors and adjust payload size and request frequency accordingly.
 Note |
|
Cisco ISE and Cisco Application Centric Infrastructure scaling
The context learned from Cisco Application Centric Infrastructure (Cisco ACI) can be shared with Cisco Catalyst Center, network devices, SD-WAN components, and any other pxGrid subscribers. This section describes the scale and performance limits when Cisco ISE is integrated with Cisco ACI.
This table describes supported Cisco ACI cluster scale for different Cisco ISE clusters and maximum SXP bindings supported for respective deployments.
| Deployment type | Maximum ACI clusters | Maximum SXP bindings |
| Small deployment with Cisco SNS 3615 or 3715 as PAN or MnT | 3 | For lab purposes only |
| Small deployment with Cisco SNS 3655, 3755, 3695, 3795, 3815, 3855, or 3895 as PAN or MnT | 3 | 40,000 |
| Medium deployment with Cisco SNS 3655, 3755, 3855 or Cisco SNS 3695, 3795, 3895 as PAN and MnT | 10 | 200,000 |
| Large deployments with Cisco SNS 3655 or 3755 as PAN and MnT | 20 | 400,000 |
| Large deployments with Cisco SNS 3695 or 3795 as PAN and MnT | 75 | 1,400,000 |
Note these points while integrating Cisco ISE with Cisco ACI:
-
It is recommended to integrate scaled ACI Fabric during off-peak hours. If the RADIUS traffic rate is high in the Cisco ISE deployment, TrustSec traffic enforcement might be delayed.
-
Maximum SXP binding values specified in this table are applicable for both deployments using only IPv4 addresses and deployments using a combination of IPv4 and IPv6 addresses.
-
Time taken for an ACI connection with 20,000 to 32,000 endpoints to reach the Connected state can be up to 5 minutes and time taken to download the bindings can be up to 10 minutes.
-
The initial time taken to download EPG endpoints or create SXP bindings can increase if the overall load on the Cisco ISE system is increased.
-
The total number of SXP bindings in the Cisco ISE deployment must not exceed 1,400,000. This count includes:
-
SXP bindings created by SGT assignment in authorization policies for RADIUS workload
-
SXP bindings received from SXP speakers
-
SXP bindings from IP-EPG mappings learned from Cisco ACI or SXP bindings created for workloads from all the Workload Connections
-
SXP bindings created by evaluating the Inbound SGT Domain rules
-
SXP bindings created by the Workload Classification rules
-
These are few examples for calculating the number of Cisco ACI connections that can be integrated with Cisco ISE based on scale:
Example 1
If the total number of SXP bindings created by SGT assignment in an authorization policy for RADIUS workload is 1,000,000, the total number of ACI connections that can be created is:
-
If each ACI Fabric has 20,000 endpoints to be shared with Cisco ISE, total number of ACI Fabrics that can be integrated = (1,400,000-1,000,000) / 20,000 = 20
-
If each ACI Fabric has 32,000 endpoints to be shared with Cisco ISE, total number of ACI connections that can be integrated = (1,400,000-1,000,000) / 32,000 = 12 or 13
Example 2
If the total number of SXP bindings created by SGT assignment in an authorization policy for RADIUS workload is 50,000, the total number of ACI connections that can be created is:
-
If each ACI Fabric has 20,000 endpoints to be shared with Cisco ISE, the total number of ACI connections that can be integrated = (1,400,000-50,000) / 20,000 = 67 or 68
-
If each ACI Fabric has 32,000 endpoints to be shared with Cisco ISE, the total number of ACI connections that can be integrated = (1,400,000-50,000) / 32000 = 42
Example 3
In a small deployment with Cisco SNS 3655/3755/3695/3795 as PAN/MnT, if the:
-
Total number of SXP bindings created by SGT assignment in an authorization policy for RADIUS workload is 10,000
-
Total SXP bindings for this deployment is 40,000
-
Total ACI Connections is 3
Maximum endpoints per ACI connection = (Total SXP bindings in deployment - Total SXP bindings)/Number of connectors for deployment = (40,000-10,000)/3 = 10,000
Cisco ISE Workload Connector scaling
From Cisco ISE release 3.4 patch 1, Cisco ISE can be integrated with these Workload Connectors, in addition to Cisco ACI:
-
AWS
-
Azure
-
GCP
-
vCenter
| Deployment type | Platform | Maximum Workload Connectors* | Maximum Workload SGT bindings |
| Small | Cisco SNS 3615, 3715, 3815 | 1 | For lab purposes only |
| Cisco SNS 3815, Cisco SNS 3655, 3755, 3855, or Cisco SNS 3695, 3795, 3895 | 3 | 10,000 | |
| Medium | Cisco SNS 3655, 3755, 3855 or Cisco SNS 3695, 3795, 3895 | 10 | 20,000 |
| Large | Cisco SNS 3655, 3755, 3855 | 40 | 20,000 |
| Cisco SNS 3695, 3795, 3895 | 50 | 20,000 |
*This could be a combination of different workload connections like AWS, GCP, Azure, and vCenter, or of same type. For example, if the maximum workload connection value is specified as 10, this deployment can include 3 GCP connections, 4 AWS connections, and 3 Azure connections, or 10 Azure connections.
Deployment requirements while integrating Cisco ISE with Cisco ACI and Workload Connectors
-
Small or medium deployments with Cisco SNS 3615 or 3715 acting as PAN/MnT are not recommended for production use.
-
Instances of the SXP persona must be configured as dedicated nodes for optimal performance in Medium and Large deployments.
-
When Inbound SGT domain rules are configured, additional SXP bindings might be created for specific endpoints.
-
While creating the Outbound SGT Domain rules, ensure that the maximum number of SGTs from all the rules and filters does not exceed 500. For example, if there are 5 Outbound SGT Domain rules, the number of SGTs per rule can be up to 100. It is recommended to have less than 10 Outbound SGT Domain rules in a deployment.
-
The maximum number of SXP bindings includes:
-
SXP bindings created by SGT assignment in authorization policies for RADIUS workload
-
SXP bindings received from SXP speakers
-
Static IP-SGT bindings
-
SXP bindings from IP-EPG mappings learned from Cisco ACI or SXP bindings created for workloads from all the Workload Connections
-
SXP bindings created by evaluating the Inbound SGT domain rules
-
SXP bindings created by the Workload Classification rules
-
-
It is strongly recommended to add scaled workload connections to Cisco ISE during the off-peak hours. If the RADIUS traffic rate is high in the Cisco ISE deployment, SXP binding creation might be delayed.
Configuration best practices
This section lists the best practices recommended while configuring the network devices and Cisco ISE for better performance.
Some of the factors that affect authentications are:
-
Network adapter disconnecting or reconnecting and leading to new authentication process
-
Network switches configured with very less session time
-
Network switches configured with frequent accounting interim updates
-
Power outages
-
Automated scripts requiring mass reboot of systems
These events result in new authentication (Access-Request), accounting-interim update, or accounting stops.
|
Attribute |
Recommendation |
|---|---|
|
Profiling probes |
If you are not using the profiling feature, turn off all the profiling probes. |
|
Endpoint Attribute filter |
This filter is disabled by default. We recommend that you enable this filter. |
|
MnT suppression |
Ensure that the Suppress Repeated Passed and Failed Clients option in the RADIUS Settings page is enabled. This option is enabled by default. |
|
EAP-FAST reconnect and session resume |
Enable this option in the Policy > Results > Allowed Protocols > Allow EAP-FAST page. This helps client devices to reduce the load on Cisco ISE for EAP. In case of BYOD flow where remote management of client device is not possible, this feature has minimal impact. |
|
DNS caching |
If Remote Logging Targets (Administration > System > Logging > Remote Logging Targets) are used with FQDN, DNS caching must be enabled. Set Time To Live value as 180 by using this command in the command line interface: |
|
Attribute |
Recommendation |
|---|---|
|
RADIUS timeout |
Recommended range is from 5 to 10 seconds. This range will help the endpoints to boot without causing the DHCP requests to expire and will also avoid latency between Cisco ISE and network devices. |
|
RADIUS interim accounting |
This option must be disabled or set to more than 24 hours for wireless and wired devices. This limits the interim accounts from the network devices when there is no significant change in the network. This also limits the incoming data to Cisco ISE, thereby reducing the RADIUS accounting updates and logs and allowing PSNs to effectively process the new incoming authentication requests. If the ratio of authentication to accounting interim updates is more than 1:5, we strongly recommended that you check the network connectivity and the network device configuration for accounting updates. You must update the configuration to reduce the frequent interim updates from the network access devices. If you have enabled automated turning off for the network devices in large scale, we recommend that you do this operation in batches. In addition, ensure that each batch does not include more than 500 devices. Otherwise, this operation might cause delay in incoming authentications. |
|
Client exclusion |
This configuration is applicable for wireless IOS devices. Set the value to 60 seconds. |
|
Session timeout |
Recommended value is more than 24 hours for both wired and wireless devices, unless your security policy dictates that you must perform authentication more frequently. |
|
Inactivity timeout |
Set the value to 300 seconds or more. This helps reduce the number of reauthentication requests. |
|
RADIUS device sensor |
If profiling is required, use the device sensor instead of other probes. While using the device sensor, other probes can be disabled for wireless devices. |
|
RADIUS Dead Timer |
Recommended range is from 10 to 15 minutes. This ensures that the RADIUS server marked down is not used for the specified interval. |
|
Guest Anchoring |
If WLAN is anchored, RADIUS accounting must be disabled in the WLAN settings on the anchor controller. |
|
Polling interval for SNMP |
We recommend that you set the SNMP Polling Interval value (Administration > Network Resources > Network Devices > Add > SNMP Settings) to 8 hours or higher to reduce performance impact due to large number of SNMP events. Setting a lower value might create large profiling events and impact system performance. |
|
Single Connect mode |
If you are using TACACS+ with TLS 1.3 protocol, enable the Administration > Network Resources > Network Devices > TACACS Authentication Settings > Enable Single Connect Mode option. This allows the events to be sent on an already established TLS channel, thereby improving the performance. |
Cisco ISE hardware appliances
Cisco SNS hardware appliances support the Unified Extensible Firmware Interface (UEFI) secure boot feature. This feature ensures that only a Cisco-signed Cisco ISE image can be installed on the Cisco SNS hardware appliances, and prevents the installation of any unsigned operating system even with physical access to the device.
| Specifications | Cisco SNS 3615 | Cisco SNS 3595 | Cisco SNS 3655 | Cisco SNS 3695 |
|---|---|---|---|---|
|
Processor |
Intel Xeon 2.10 GHz 4110 |
Intel Xeon 2.60 GHz E5-2640 |
Intel Xeon 2.10 GHz 4116 |
Intel Xeon 2.10 GHz 4116 |
|
Cores per Processor |
8 Cores and 16 Threads |
8 Cores and 16 Threads |
12 Cores and 24 Threads |
12 Cores and 24 Threads |
|
Memory |
32 GB (2x16 GB) |
64 GB (4x16 GB) |
96 GB (6x16 GB) |
256 GB (8x32 GB) |
|
Storage |
1 x 600-GB 6 Gb SAS 10K RPM |
4 x 600-GB 6 Gb SAS 10K RPM |
4 x 600-GB 6 Gb SAS 10K RPM |
8 x 600-GB 6 Gb SAS 10K RPM |
|
Hardware RAID |
— |
Level 10 Cisco 12G SAS Modular RAID Controller |
Level 10 Cisco 12G SAS Modular RAID Controller |
Level 10 Cisco 12G SAS Modular RAID Controller |
|
Network Interfaces |
2 X 10 Gbase-T 4 x 1 GBase-T |
6 x 1 GBase-T |
2 X 10 Gbase-T 4 x 1 GBase-T |
2 X 10 Gbase-T 4 x 1 GBase-T |
|
Power Supplies |
1 x 770W |
2 x 770W |
2 x 770W |
2 x 770W |
| Specifications | Cisco SNS 3715 | Cisco SNS 3755 | Cisco SNS 3795 |
|---|---|---|---|
|
Processor |
Intel Xeon 2.1 GHz 4310 |
Intel Xeon 2.3 GHz 4316 |
Intel Xeon 2.3 GHz 4316 |
|
Cores per processor |
12 Cores and 24 Threads |
20 Cores and 40 Threads |
20 Cores and 40 Threads |
|
Memory |
32 GB 2 x 16GB |
96 GB 6 x 16GB |
256 GB 8 x 32GB |
|
Storage |
1 60012G SAS 10K RPM SFF HDD Or 800 GB 2.5in Enterprise Performance 12G SAS SSD (3x endurance) |
4 60012G SAS 10K RPM SFF HDD Or 800 GB 2.5in Enterprise Performance 12G SAS SSD (3x endurance) |
8 60012G SAS 10K RPM SFF HDD Or 800 GB 2.5in Enterprise Performance 12G SAS SSD (3x endurance) |
|
Hardware RAID |
Level 0 |
Level 10 Cisco 12G SAS Modular RAID Controller |
Level 10 Cisco 12G SAS Modular RAID Controller |
|
Network interface |
2 x 10Gbase-T 4 x 10GE SFP |
2 x 10Gbase-T 4 x 10GE SFP |
2 x 10Gbase-T 4 x 10GE SFP |
|
Power supplies |
1 x 1050W |
2 x 1050W |
2 x 1050W |
|
TPM chip |
Yes |
Yes |
Yes |
 Note |
|
|
Specifications |
Cisco SNS 3815 |
Cisco SNS 3855 |
Cisco SNS 3895 |
|---|---|---|---|
|
Processor |
AMD 9115 2.6 GHz |
AMD 9224 2.5 GHz |
AMD 9224 2.5 GHz |
|
Cores per processor |
16 cores and 32 threads |
24 cores and 48 threads |
24 cores and 48 threads |
|
Memory |
64 GB 2 x 32 GB |
128 GB 4 x 32 GB |
256 GB 8 x 32 GB |
|
Storage |
1 960 GB NVMe Or 960 GB SSD Self Encrypted Drive Or 1.6 TB SSD Self Encrypted Drive FIPS Certified |
1 for PSN only or 4 for PAN/MnT 960 GB NVMe Or 1 for PSN only or 4 for PAN/MnT 960 GB SSD Self Encrypted Drive Or 1 For PSN only or 4 for PAN/MnT 1.6 TB SSD Self Encrypted Drive FIPS Certified |
8 960 GB NVMe Or 960 GB SSD Self Encrypted Drive Or 1.6 TB SSD Self Encrypted Drive FIPS Certified |
|
Hardware Redundant Array of Independent Disks (RAID) |
Level 0 Cisco 24G Tri-Mode M1 RAID Controller for SED and SED FIPS only |
Level 0 for PSN only with NVMe Level 10 for PAN/MnT or when using SED or SEF-FIPS Cisco 24G Tri-Mode M1 RAID controller |
Level 10 Cisco 24G Tri-Mode M1 RAID controller |
|
Network interface |
2 x 10Gbase-T 4 x 10GE SFP |
2 x 10Gbase-T 4 x 10GE SFP |
2 x 10Gbase-T 4 x 10GE SFP |
|
Power supplies |
1 or 2 x 1200 W |
2 x 1200 W |
2 x 1200 W |
|
Trusted Platform Module (TPM) chip |
Yes |
Yes |
Yes |
 Note |
|
Cisco ISE virtual machine and cloud platforms
Cisco ISE can be installed on VMware servers, KVM hypervisors, Hyper-V (Windows Server and Azure Stack HCI), and Nutanix AHV. To achieve performance and scalability comparable to Cisco ISE hardware appliances, virtual machines must be allocated system resources equivalent to the Cisco SNS appliances.
It is recommended that you reserve CPU and memory resources that match the resource allocation. Failure to do so may significantly impact Cisco ISE performance and stability.
For a VM deployment, the number of cores is twice the number of cores in a physical appliance due to hyperthreading. For example, in case of a small network deployment, allocate 16 vCPU cores to meet the CPU specification of SNS 3615, which has 8 CPU cores or 16 threads.
Deploy dedicated VM resources and do not share or oversubscribe resources across multiple guest VMs.
Cisco ISE is now available from the cloud, enabling you to scale your Cisco ISE deployments quickly and easily to meet changing business needs.
Cisco ISE is available as an Infrastructure as Code solution, helping you to rapidly deploy network accesses and control services anywhere.
Extend the Cisco ISE policies in your home network to new remote deployments securely through Amazon Web Services (AWS), Azure Cloud Services, or Oracle Cloud Infrastructure (OCI). AWS supports Cisco ISE release 3.1 and later releases.
OCI and Azure Cloud support is available from Cisco ISE release 3.2 and later releases.
See Deploy Cisco ISE Natively on Cloud Platforms and respective cloud documentations for resource specifications of supported instances.
This table describes matrix of VM specification, cloud instances to their equivalent Cisco SNS appliances.
| Models | Cisco SNS 3615 | Cisco SNS 3595 | Cisco SNS 3655 | Cisco SNS 3695 | Cisco SNS 3715 | Cisco SNS 3755 | Cisco SNS 3795 |
|---|---|---|---|---|---|---|---|
|
VM Specification |
16vCPU 32 GB |
16vCPU 64 GB |
24vCPU 96 GB |
24vCPU 256 GB |
24vCPU 32GB |
40vCPU 96GB |
40vCPU 256GB |
|
AWS |
c5.4xlarge* |
m5.4xlarge |
c5.9xlarge* m5.8xlarge |
m5.16xlarge |
c5.9xlarge* m5.8xlarge |
— |
m5.16xlarge |
|
c7i.4xlarge*** |
— |
m7i.8xlarge*** |
m7i.16xlarge*** |
m7i.8xlarge*** |
— |
m7i.16xlarge*** |
|
|
Azure |
Standard_F16s_v2* |
Standard_D16s_v4 |
Standard_F32s_v2* Standard_D32s_v4 |
Standard_D64s_v4 |
Standard_F32s_v2* Standard_D32s_v4 |
— |
Standard_D64s_v4 |
|
OCI |
Optimized3.Flex* (8 OCPU** and 32 GB) |
Standard3.Flex (8 OCPU and 64 GB) |
Optimized3.Flex (16 OCPU and 64 GB)* Standard3.Flex (16 OCPU and 128 GB) |
Standard3.Flex (16 OCPU and 256 GB) |
Optimized3.Flex (16 OCPU and 64 GB)* Standard3.Flex (16 OCPU and 128 GB) |
— |
Standard3.Flex (32 OCPU and 256 GB) |
*This instance is compute-optimized and provides better performance compared to the general purpose instances.
**In OCI, you choose CPU in terms of Oracle CPU (OCPU). Each OCPU provides CPU capacity equal to one physical core of an Intel Xeon processor with hyper-threading enabled. Each OCPU equals two hardware execution threads known as vCPUs.
***Cisco ISE release 3.5 and later supports M7i and C7i instance types on AWS.
 Note |
|
Extra Small form factor for Cisco ISE VM and cloud instances
Extra Small VM specification is available only on virtualization platforms such as VMware, KVM, Hyper-V, Nutanix AHV hypervisors, and Cloud instances.
This form factor is not supported for SNS appliances.
|
Virtual Machines |
Specifications |
|---|---|
|
VM |
8 vCPU 32GB RAM |
|
AWS |
m5.2xlarge m7i.2xlarge |
|
Azure |
Standard_D8s_v4 |
|
OCI |
Standard3.Flex (4 OCPU and 32 GB) |
Extra Small form factor supports these two deployment types:
-
PSNLite: The node can be deployed as a dedicated PSN persona in a deployment supporting up to 500,000 sessions.
Performance for RADIUS and TACACS+ authentication is around 50 percent of that of Cisco SNS 3615. For example, if the RADIUS authentication rate of Cisco SNS 3615 for PEAP-MSCHAP2 with internal user database is 150, this value will be 75 (50% of 150) for the PSNLite.
-
ISELite: The node can be deployed as a standalone Cisco ISE node. It is not recommended to use ISELite for Small (HA) deployments.
ISELite is optimized to run only for small office scenario supporting up to a maximum of 1000 concurrently active endpoints with an optimal RADIUS performance at 50 TPS.
ISELite is recommended only for RADIUS or TACACS+ traffic. It is not recommended to enable advanced services like SXP, PassiveID, pxGrid Direct, pxGrid Cloud, TC-NAC, Log Analytics, and Cisco AI Analytics on an ISELite node.
Ensure that the Log Analytics option (under Operations > System 360) is disabled in the ISELite node.
| Name | Deployment type | Storage | Maximum concurrent active sessions | Notes |
| PSNLite | Dedicated PSN only | 300 GB | 12000 | Supported from Cisco ISE 3.2 onwards |
| ISELite | Standalone Cisco ISE node | 600 GB | 1000 | Supported from Cisco ISE 3.4 onwards |
 Feedback
Feedback