BACnet
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
All protocols implemented in the Active Discovery feature use standard packets commonly used by vendors. The system will never send requests on the network without a clear configuration made by the user. It is possible to schedule requests at a pre-defined frequency.
Discovered devices' responses will depend on the protocol implemented by the manufacturer and the user configuration. Except for what is clearly stated in this documentation, no specific configuration is required on discovered devices. Devices may give an answer by default, but it can vary in the field depending on the configuration.
This annex gives examples of the packets used by Cisco Cyber Vision to discover devices and of typical answers the user can expect.

Without User
With User
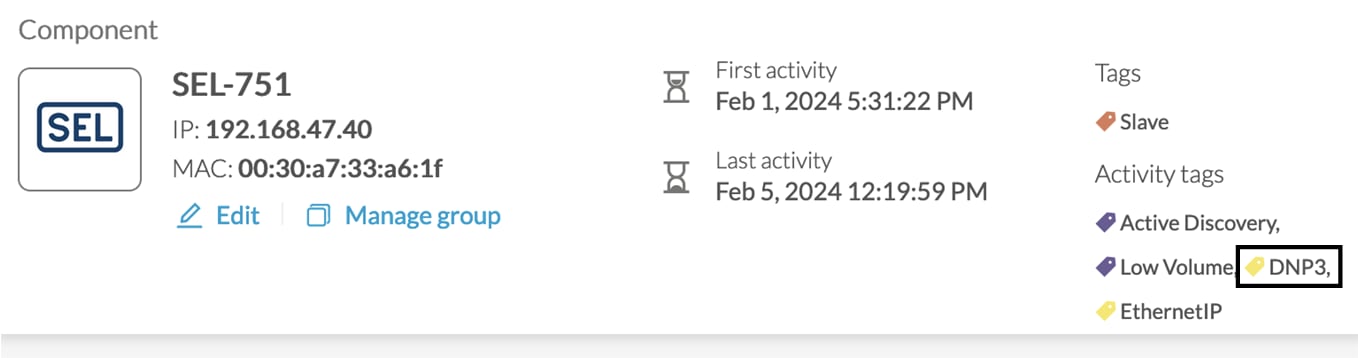
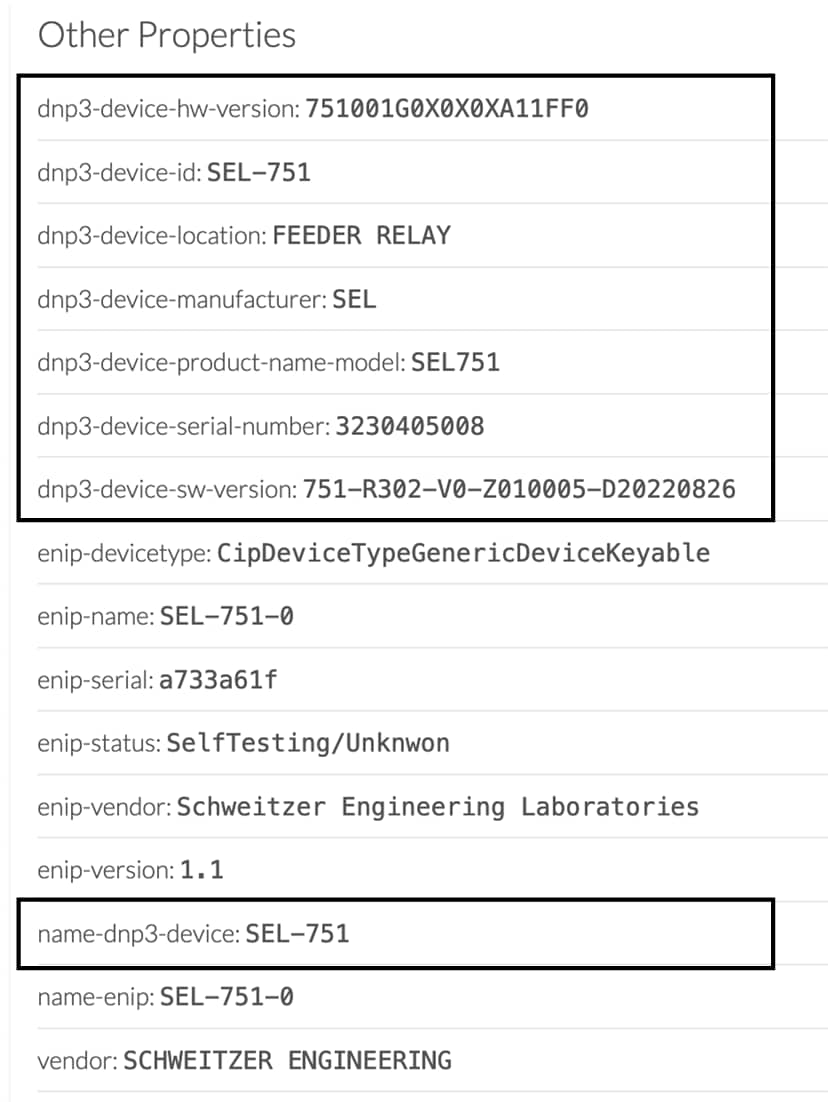
Ethernet/IP Active Discovery can be performed by Cisco Cyber Vision using Broadcast or Unicast mode. In any case, requests sent and component properties collected in return will be the same. The main differences will be:
Broadcast will discover all devices in the local LAN.
Unicast will only discover the devices and components which have an IPv4 address.
Unicast will search for, once an EtherNet/IP node is discovered, the devices' content. If a device is a chassis with a backplane, it will be queried and all modules will send their properties.
| # | Name | Cyber Vision Properties | Example |
|
1 |
Vendor ID |
enip-vendor |
Rockwell Automation/Allen-Bradley |
|
2 |
Device Type |
enip-devicetype |
ProgrammableLogicController |
|
3 |
Product Code |
enip-productcode |
235 |
|
4 |
Revision |
enip-version |
33.012 |
|
5 |
Status |
enip-status |
AtLeastOneIOConnectionInRunMode, MinorRecoverableFault, ReservedBits12-15:0x3 |
|
6 |
Serial Number |
enip-serial |
01105356 |
|
7 |
Product Name |
enip-name |
1756-L81ES/B |
A Broadcast Ethernet/IP Active Discovery consists of a packet sent by the sensor which requests EtherNet/IP identities to all devices in the local LAN. For example, a sensor with an Active Discovery IPv4 address 192.168.20.192/24 will send this EtherNet/IP request to the Broadcast address, here 192.168.20.255. All devices in the IPv4 range 192.168.20.0 to 192.168.20.254 will answer with the packet described above (CIP Identity response (0x000c)).
A direct Unicast Ethernet/IP (i.e. no backplane) will consist of the same request but sent directly to the device. When a preset is configured to query EtherNet/IP devices, the system will take the list of components of this preset which have an IPv4 address. Then, the Active Discovery engine will try to reach each IPv4 with this EtherNet/IP identities request. All reachable EtherNet/IP nodes of this list will answer with the packet described above (CIP Identity response (0x000c)).
In both cases (Broadcast and Unicast), the answer will be sent by the discovered devices to the sensor's Active Discovery network interface. The answer will be a UDP packet for the Broadcast request and some TCP packets for the Unicast request.
To browse backplanes, the Active Discovery policy with the Unicast EtherNet/IP protocol enabled needs to have the backplane discovery option set to enabled.
In such case, all EtherNet/IP nodes detected by Active Discovery Ethernet/IP Unicast will be queried again by the sensor. The sensor will try to know the backplane size and then send a request to the different modules (link addresses form 0 to the chassis size). All modules will then send their properties such as the product reference and the firmware version.
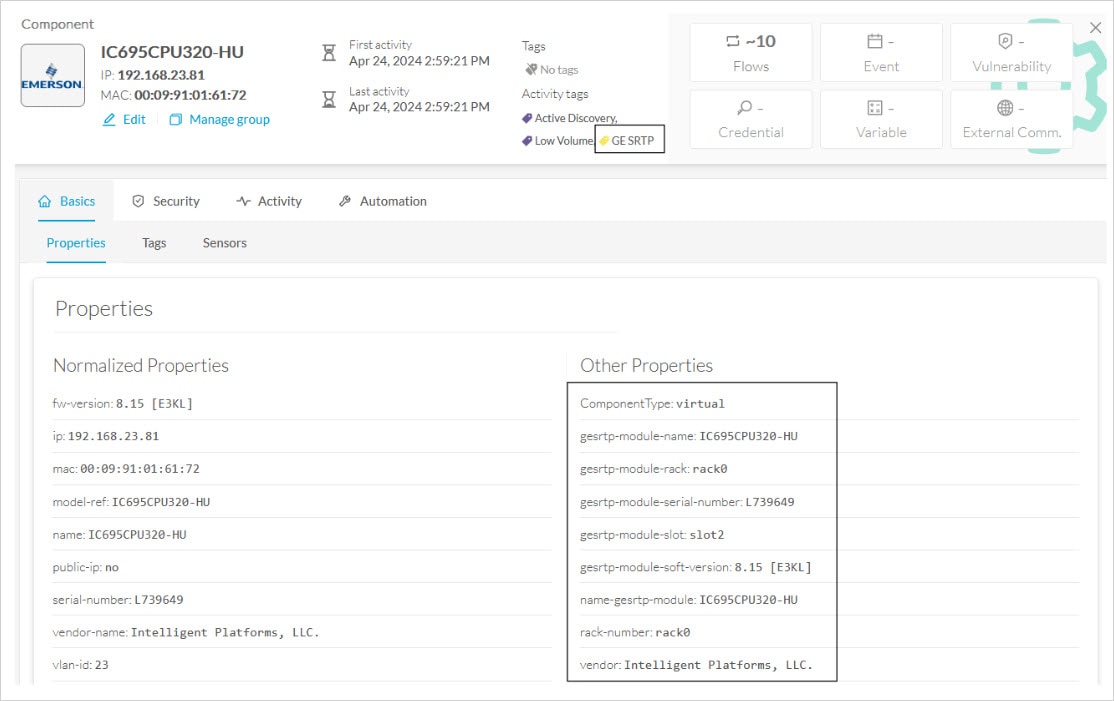


Cisco Cyber Vision Active Discovery can use a Profinet DCP service called Identify Request. This request will be sent by the sensor interfaces defined for Active Discovery. All Profinet devices will answer with a specific Profinet DCP identify response packet.
The request is sent by the sensor MAC address to a specific Ethernet Multicast address: 01:0e:cf:00:00:00. This Profinet DCP Multicast address will allow Cisco Cyber Vision to join all Profinet nodes on the local LAN. The answer of each node will be a specific Profinet DCP packet sent to the sensor MAC address.
The information collected are:
The IP address + mask.
The Manufacturer name.
The name of the station.
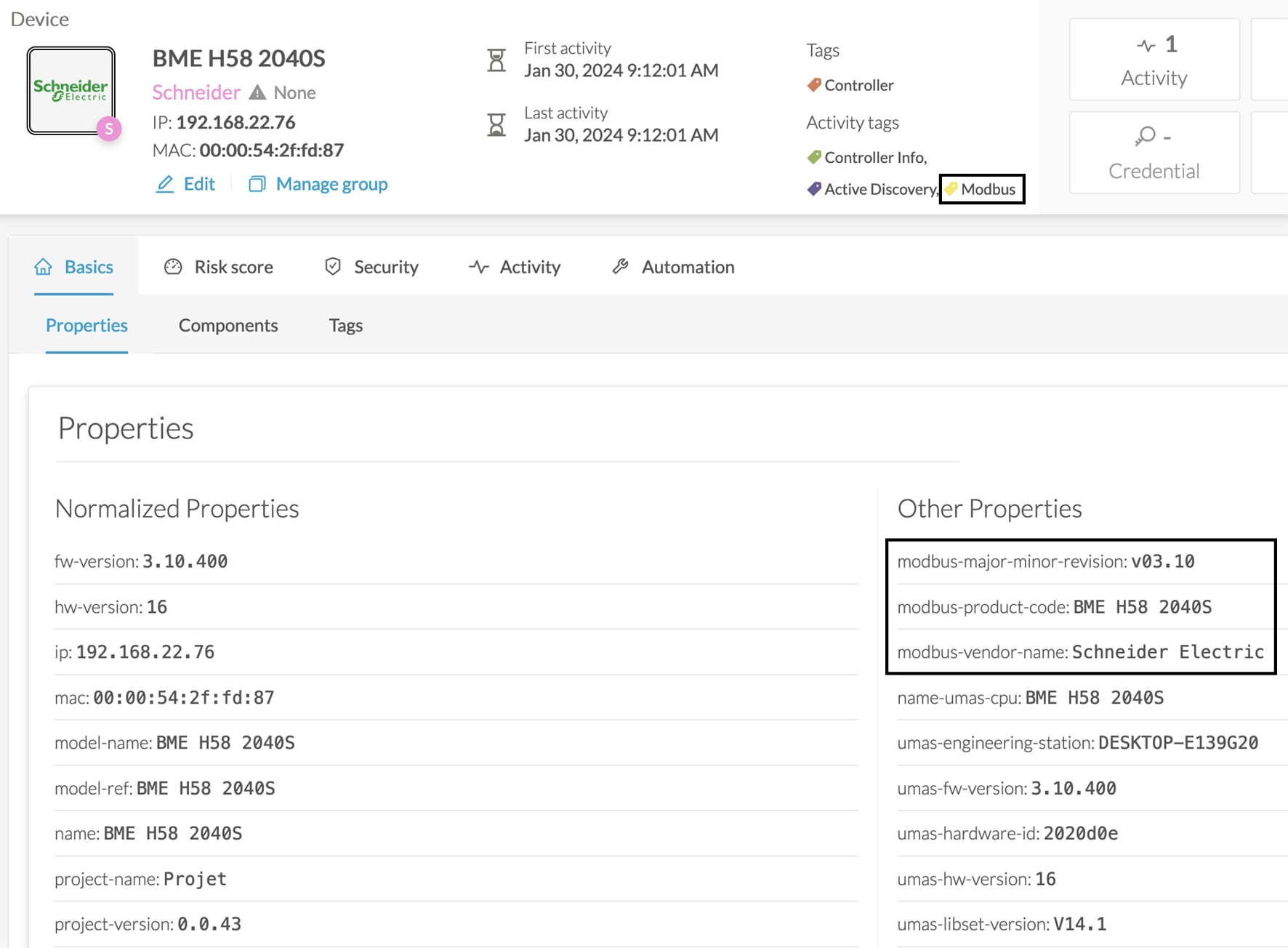
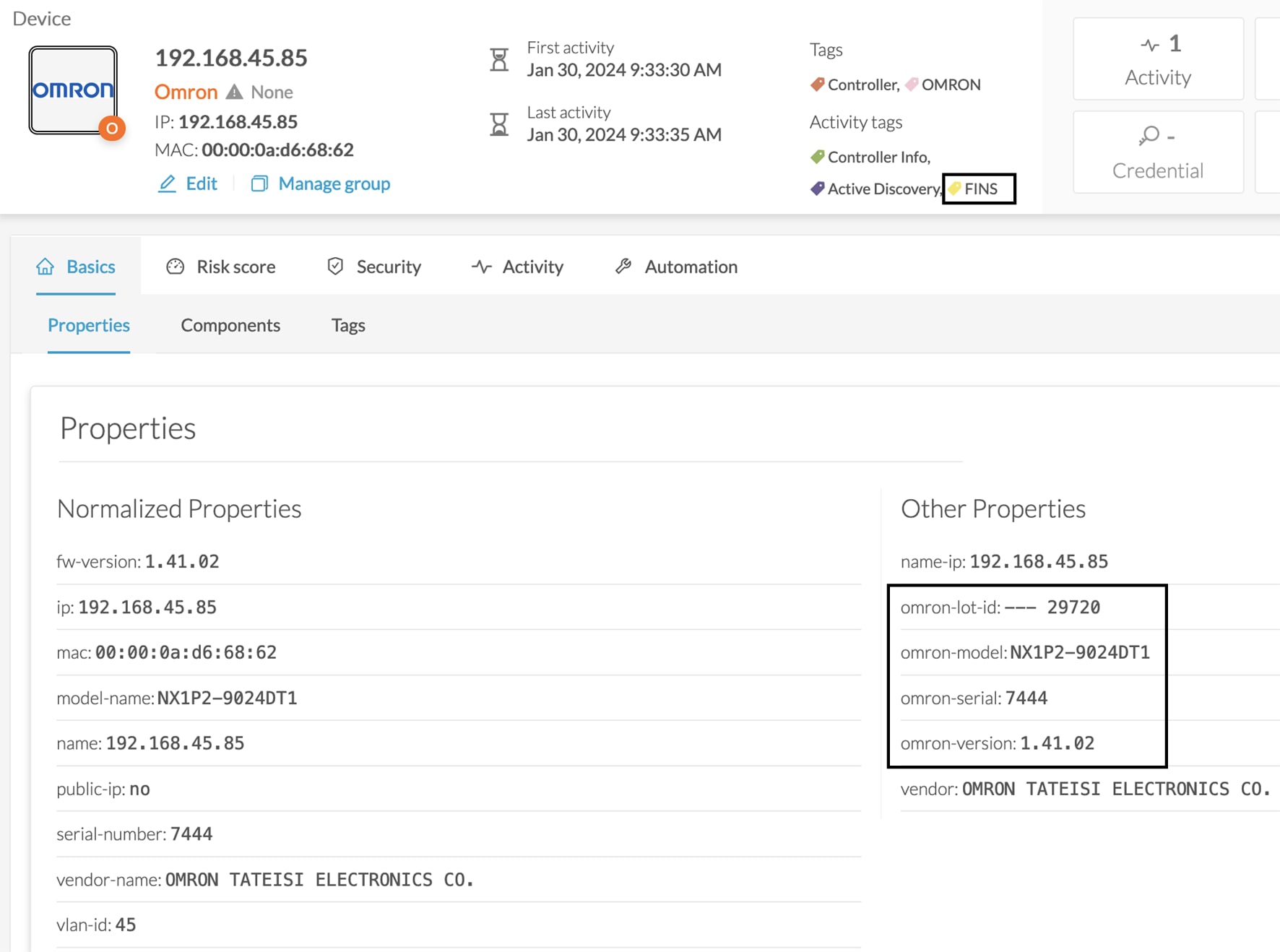
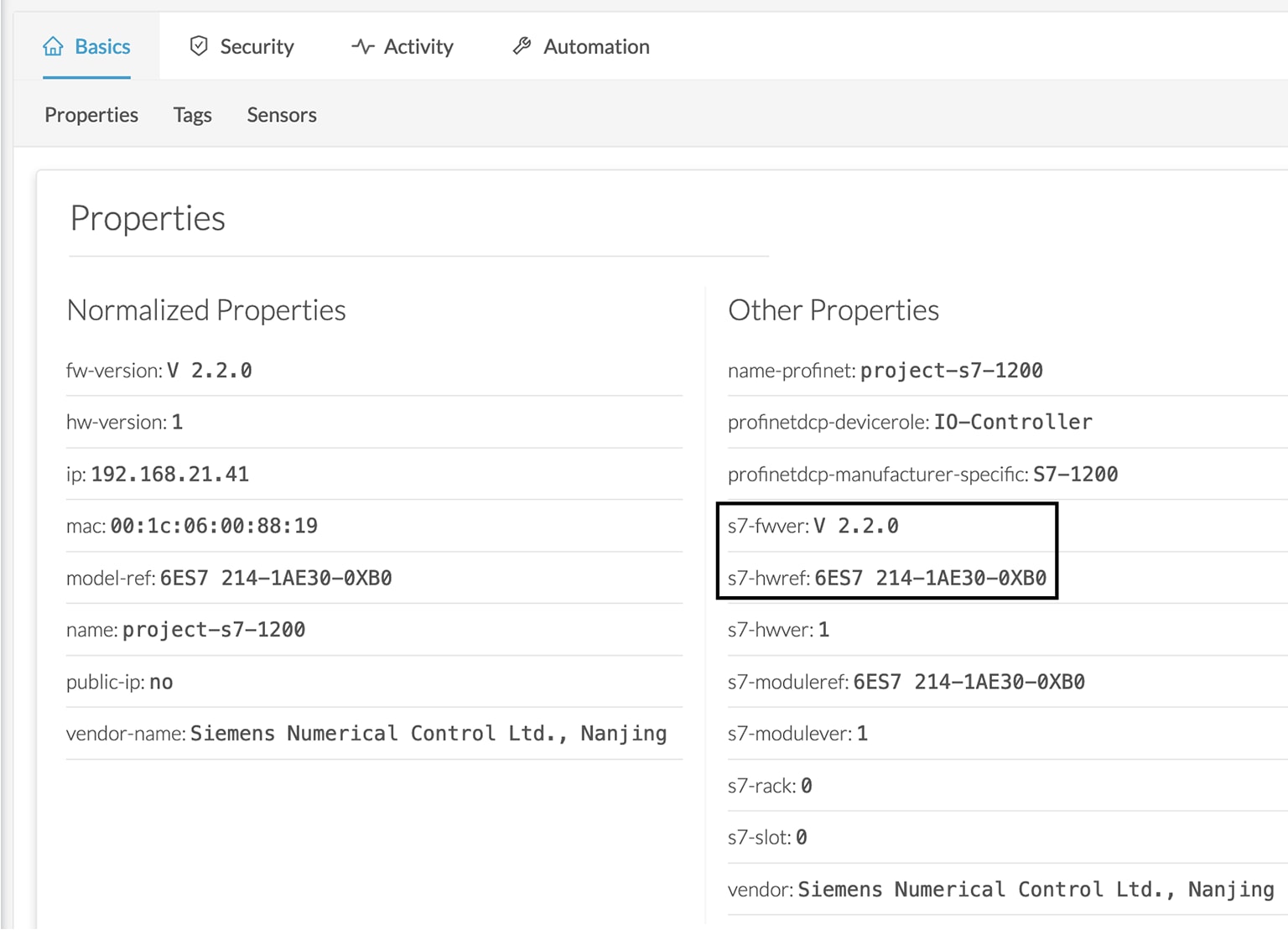
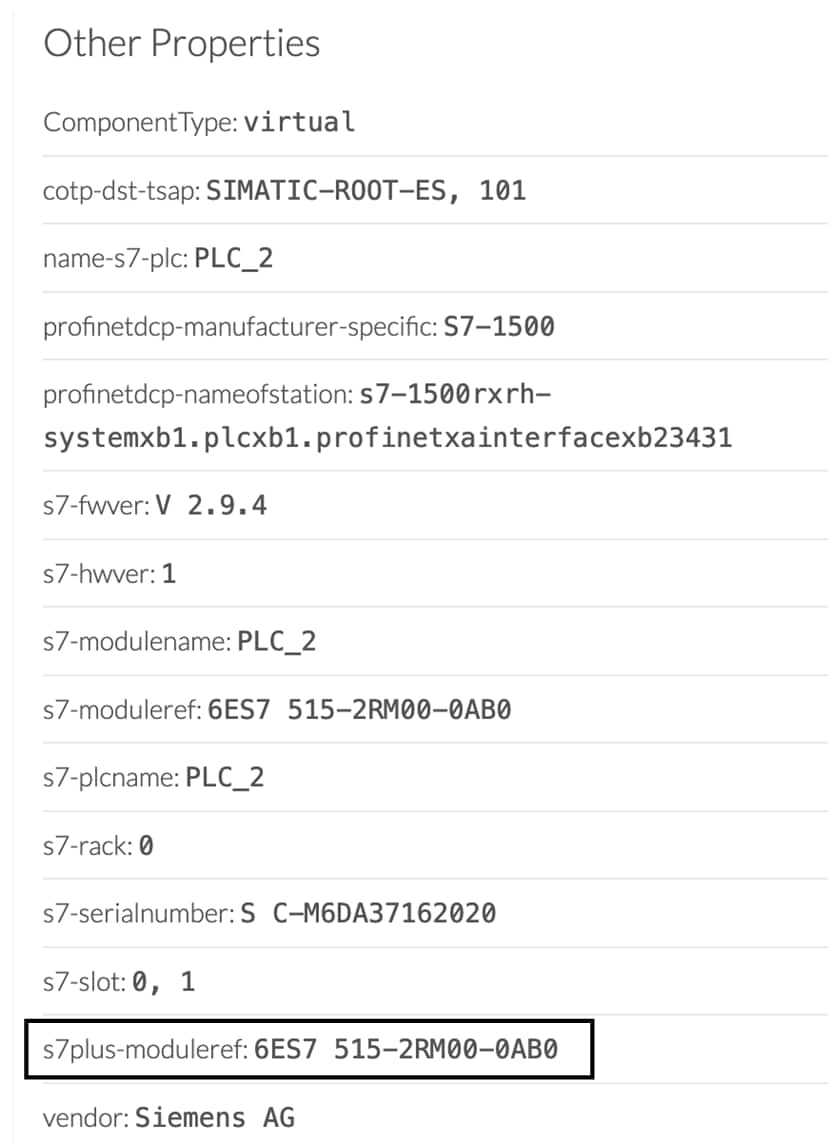
Cyber Vision Active Discovery can use a request on the protocol S7 discovery with a command: "identification". This request will be sent by the sensor interfaces defined for Active Discovery. All S7 devices will answer with a specific S7 Discovery identification response packet.
The request is sent by the sensor MAC address to the Ethernet broadcast address: ff:ff:ff:ff:ff:ff. The answer of each S7 protocol capable node will be a specific S7 discovery packet sent by the device MAC address to the sensor MAC address.
The information collected are:
The model name.
The name of the device.
The Active Discovery engine uses a specific S7 Unicast command to request properties from S7-compatible devices, such as:
Hardware reference
Firmware version
For the ICMPv6 Active Discovery protocol, the Cisco Cyber Vision sensor will use an ICMPv6 Echo request (ping) to the all-nodes link-local scope multicast address. The sensor will thus ping all IPv6 nodes on the local link. All reachable nodes will answer back with their link-local IPv6 address and their MAC address.
Cisco Cyber Vision sensors use a specific ICMPv6 packet, echo request (type 128) to the address ff02::1 (All nodes on the local network segment) with a hop limit of 1.
The different nodes will answer with a ICMPv6 Neighbor solicitation (type 135 ) to the Solicited-Node Multicast address which has the form ff02::1::ff with the least-significant 24 bits of the sensor IPv6 Unicast address.
Cisco Cyber Vision sensor can use the SNMP protocol to collect network devices information.
SNMP Active Discovery results highly depend on the configuration, type and version of the queried devices. Some devices might respond without any specific configuration, others might need complex configurations, and others not respond at all.
While doing SNMP Active Discovery, the sensor will try to read some generic and vendor-specific values. The generic values will be used by the sensor to build extra queries based on vendors and hardware models.
Generic values collected are:
| Property | Description |
| snmp-sys-descr | Description |
| snmp-sys-name | Name |
The Cisco Cyber Vision sensor Active Discovery supports:
SNMP Version 2c (SNMPv2c) with a fallback in SNMP Version 1 (SNMPv1).
SNMP Version 3 (SNMPv3).
SNMPv3 Active Discovery is able to provide authentication and encryption.
All SNMP versions will give the same results in the Cisco Cyber Vision application. They are important regarding data access. The subsequent section describes the SNMP results with different types of network devices.
The Cisco Cyber Vision SNMP Active Discovery with Schneider Electric PLC requests generic values (snmp-sys-descr and snmp-sys-name).
The Cisco Cyber Vision SNMP Active Discovery with Siemens PLC requests generic values (snmp-sys-descr and snmp-sys-name).
The Cisco Cyber Vision SNMP Active Discovery with Rockwell Automation PLC requests generic values (snmp-sys-descr and snmp-sys-name).
The Cisco Cyber Vision SNMP Active Discovery with Moxa switches requests generic values (snmp-sys-descr and snmp-sys-name) with the addition of:
| Property | Description |
| snmp-moxapriv-model-name | Model |
| snmp-moxapriv-fw-version | Firmware version |
The Cisco Cyber Vision SNMP Active Discovery with Siemens switches requests generic values (snmp-sys-descr and snmp-sys-name) with the addition of:
| Property | Description |
| snmp-siemens-scalence-model-ref | Model |
| snmp-siemens-scalence-model-version | Firmware version |
The Cisco Cyber Vision SNMP Active Discovery with Hirschmann switches requests generic values (snmp-sys-descr and snmp-sys-name) with the addition of:
| Property | Description |
| snmp-hmpriv-mgmt-model-ref | Model |
| snmp-hmpriv-mgmt-fw-version | Firmware version |
| snmp-hm2-indus-model-ref | Model |
| snmp-hm2-indus-fw-version | Firmware version |
| snmp-hm-disc-fw-version | Model |
| snmp-hm-disc-model-ref | Firmware version |
The Cisco Cyber Vision SNMP Active Discovery with Cisco Hardware demands some specific configurations on the device side and requests generic values (snmp-sys-descr and snmp-sys-name) with the addition of:
| Property | Description |
| snmp-ent-physical-model-name | Model |
| snmp-ent-physical-entry | Description |
| snmp-ent-physical-serial-number | Serial number |
| snmp-probe-software-rev | Firmware version |
The Cisco Cyber Vision SNMP Active Discovery with Microsoft Windows stations demands a specific operating system configuration and requests generic values (snmp-sys-descr and snmp-sys-name) with the addition of:
| Property | Description |
| snmp-primary-domain-name | Domain name of the machine |
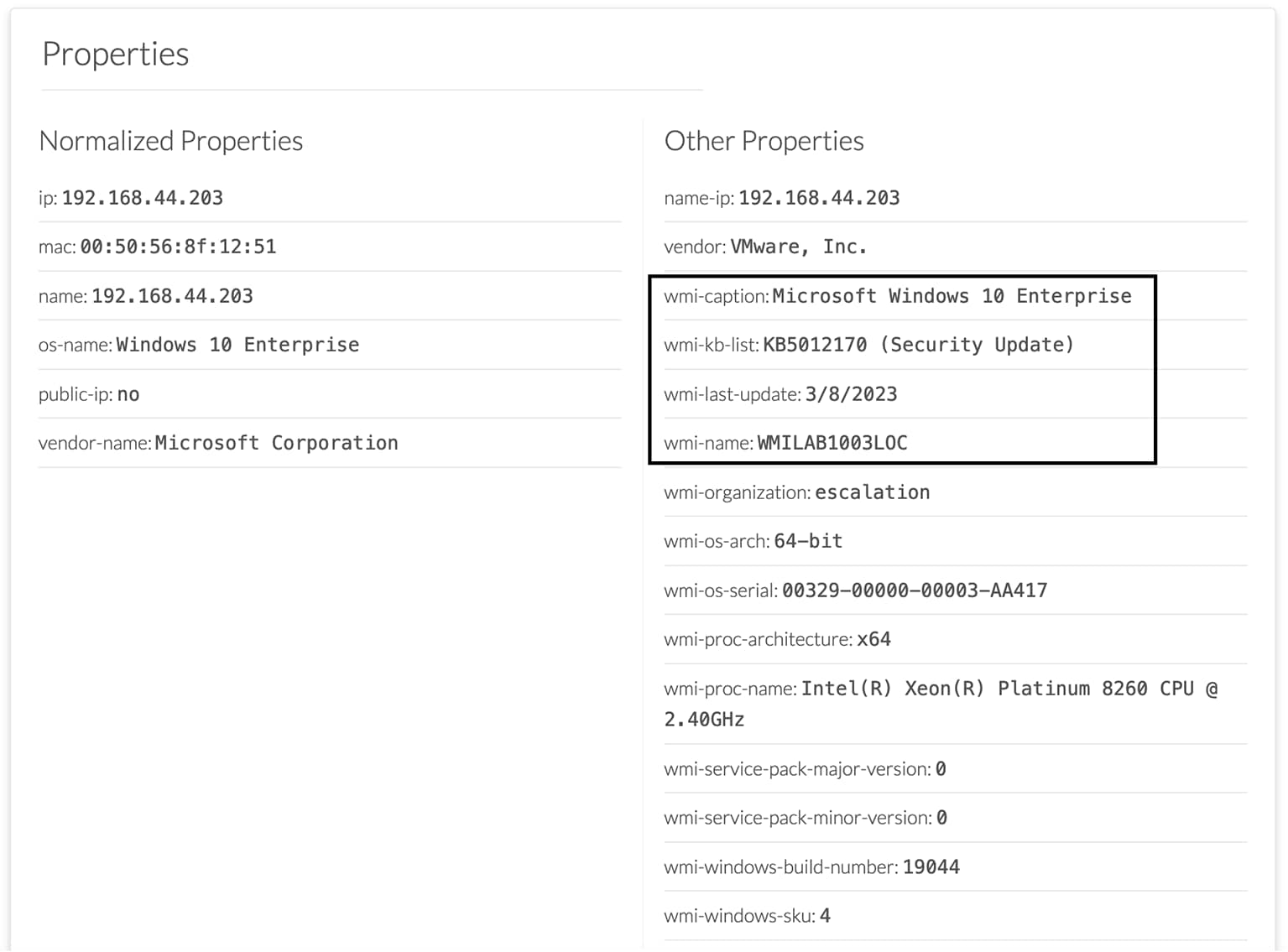
WMI is used to collect the following Windows hosts' properties.
wmi-caption: operating system's name and version
wmi-kb-list: security updates installed in the host
wmi-last-update: latest update date
wmi-name: host name