Overview
-
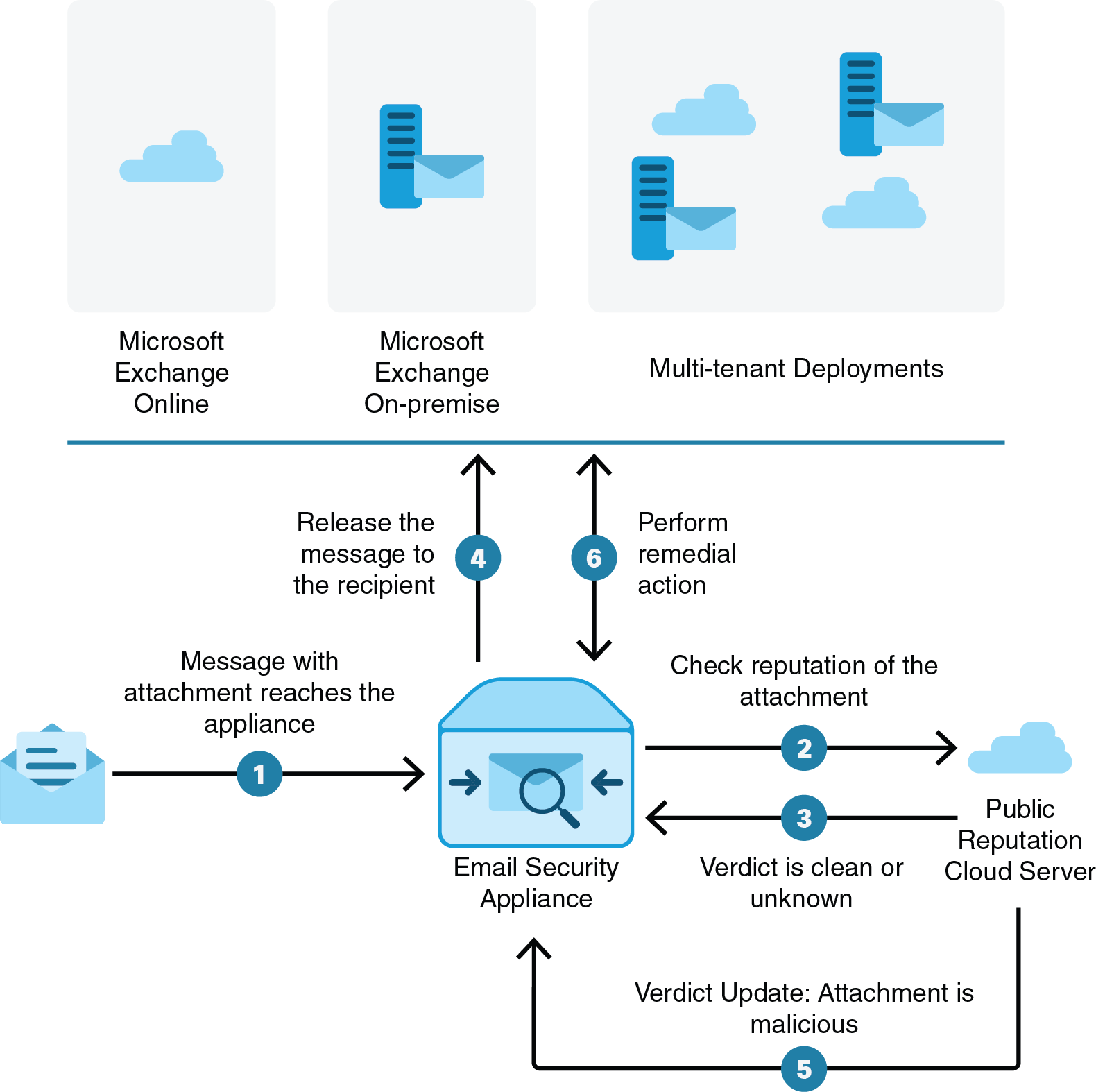
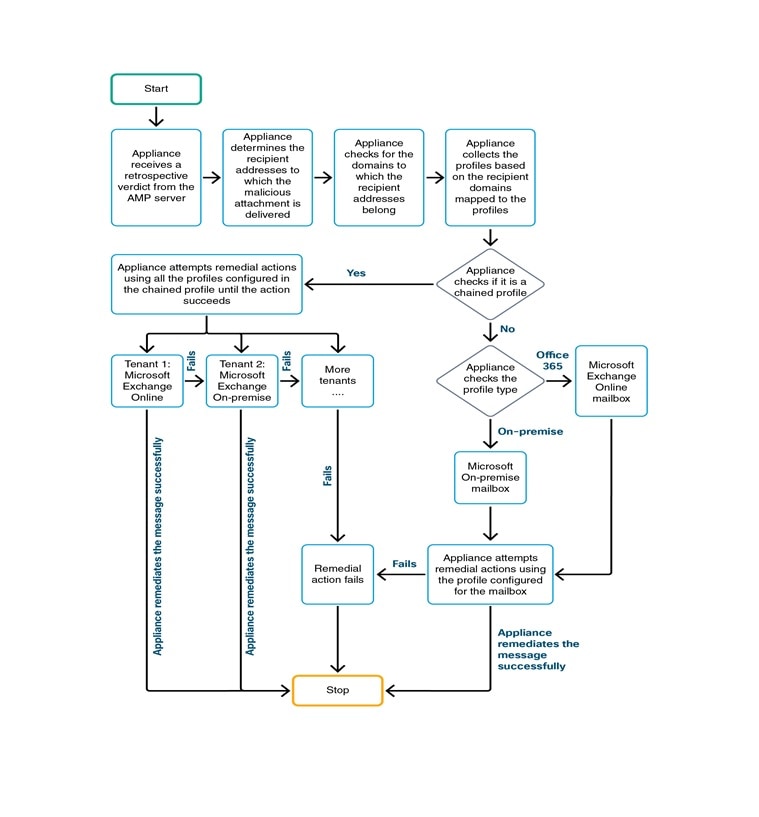
automatically remediate the messages when the AMP sends the retrospective alert to your appliance
-
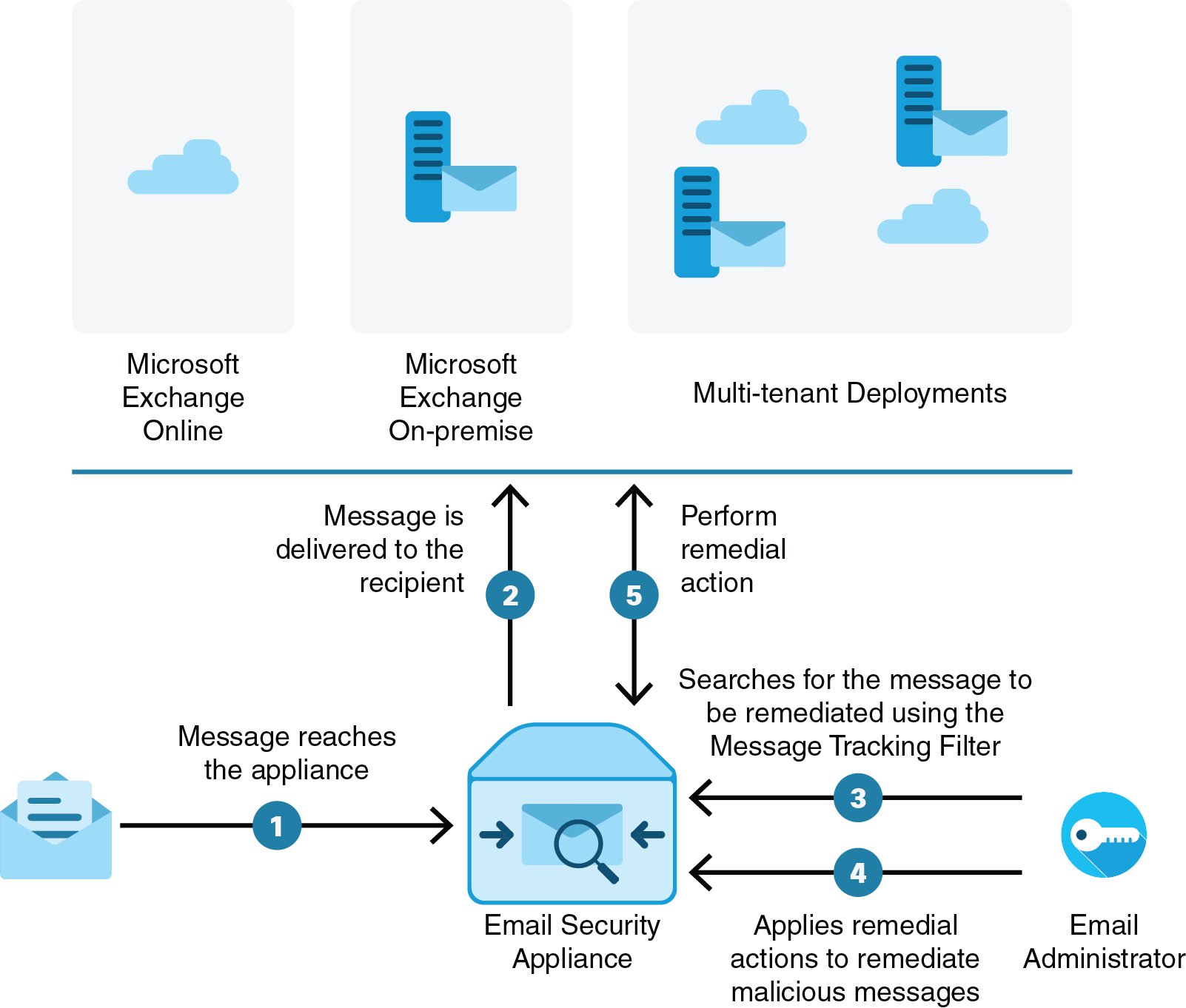
manually search and remediate the messages using the Message Tracking filter
You can also use the Message Tracking page to search and remediate the messages that are delivered to the user mailbox. The Message Tracking page is a unified place to search for all messages delivered to the mailboxes. From the search result, you can choose the messages you want to remediate and apply the action you want to perform on the messages.
The appliance can perform remedial actions(manually or automatically) on the messages in the following mailbox deployments:
-
Microsoft Exchange online – mailbox hosted on Microsoft Office 365
-
Microsoft Exchange on-premise – a local Microsoft Exchange server
-
Hybrid/Multiple tenant configuration – a combination of mailboxes configured across Microsoft Exchange online and Microsoft Exchange on-premise deployments

 Feedback
Feedback