Azure Service VNet
For the Centralized deployment, Multicloud Defense Gateway is deployed in a new Service VNet. This VNet is called a Service VNet which will peer with other Spoke(application) VNet to create a Hub-and-Spoke model as shown below:
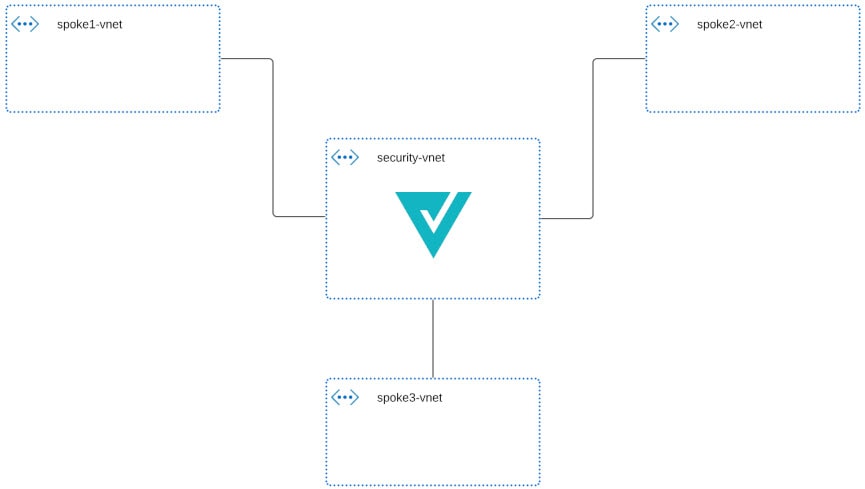
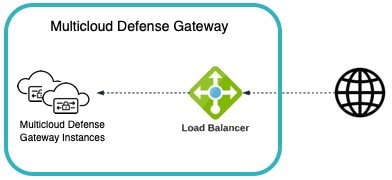
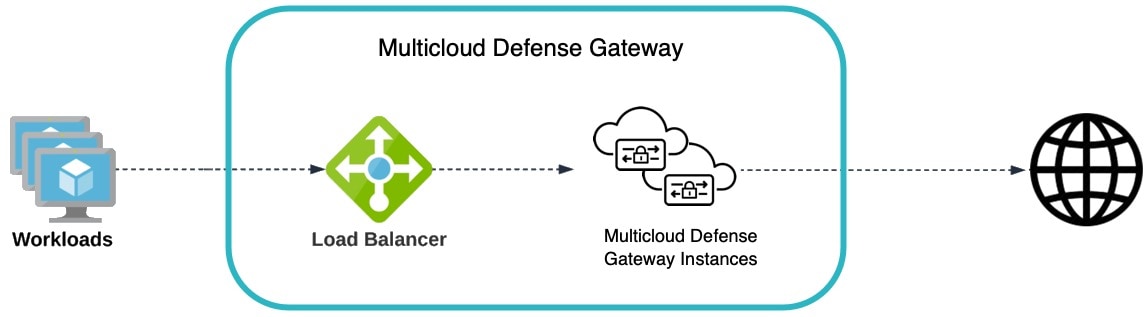
Multicloud Defense orchestrates the creation of the Service VNet and does VNet peering with the Spoke VNets. Multicloud Defense also provides the ability to update the routing in Spoke VNets to route traffic to Service VNet for inspection. For instructions on how to make routing changes with Multicloud Defense in Spoke VNet, see Manage (Protect) Spoke VPCs in Hub Mode.
Create Service VNet
Procedure
|
Step 1 |
Click . |
||||||||||||||||
|
Step 2 |
Click Create Service VPC/VNet. |
||||||||||||||||
|
Step 3 |
Input parameter values:
|

 Feedback
Feedback