Information About Deploying Cisco SD-WAN Controllers in Azure
Minimum supported controller images: Cisco vManage Release 20.6.1, Cisco Catalyst SD-WAN Control Components Release 20.6.1, and Cisco SD-WAN Validator Release 20.6.1
You can deploy the following Cisco SD-WAN Controllers in an Azure environment: Cisco SD-WAN Manager, Cisco SD-WAN Controller, and Cisco SD-WAN Validator.
The following illustration shows the architecture of the Azure region, virtual network, security group, and so on, and it shows where the Cisco SD-WAN Controllers function within the architecture.
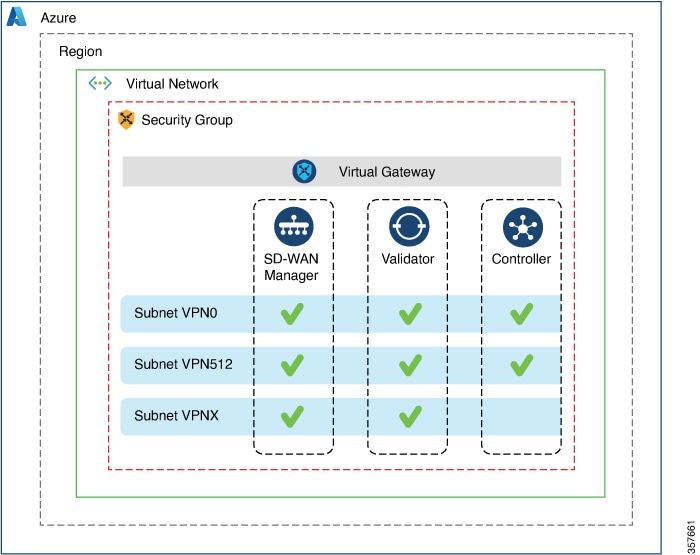
Benefits of Deploying Cisco SD-WAN Controllers in Azure
-
Set-up cost: Requires low initial set-up cost, as compared with on-premises hosting, as there is no requirement to purchase additional data center infrastructure
-
Deployment: Ease of cloud-based deployment
-
Management: Ability to manage devices worldwide
-
Stability: Because of its reliability, Azure hosting provides a stable environment for Cisco SD-WAN Controllers.
-
Security: Azure provides a secure hosting environment.
-
Scaling: Azure provides an easy path to increasing the scale of your Cisco Catalyst SD-WAN network.

 Feedback
Feedback