- Overview
- Uploading a Firmware Image to FND
- Uploading a Firmware Image to a Resilient Mesh Endpoint (RME) Group
- Firmware Update Transmission Settings
- Setting the Installation Schedule
- Set a Firmware Backup Image
- Viewing Mesh Device Firmware Image Upload Logs
- Modify Display of Firmware Management Page
- Viewing Firmware Image Files in IoT FND
- Adding a Firmware Image to IoT FND
- Uploading a Firmware Image to a Router Group
- Canceling Router Firmware Image Upload
- Pausing and Resuming Router Firmware Image Uploads
- Installing a Firmware Image
- Stopping Firmware Image Installation
- Pausing and Resuming Router Firmware Image Installation
Managing Firmware Upgrades
This section describes managing firmware upgrade settings in IoT FND, and includes the following sections:
■![]() Working with Resilient Mesh Endpoint Firmware Images
Working with Resilient Mesh Endpoint Firmware Images
■![]() AP800 Firmware Upgrade During Zero Touch Deployment
AP800 Firmware Upgrade During Zero Touch Deployment
■![]() Image Diff Files for IR809 and IR829
Image Diff Files for IR809 and IR829
■![]() Configuring Firmware Group Settings
Configuring Firmware Group Settings
■![]() Working with Router Firmware Images
Working with Router Firmware Images
■![]() Performing CG-OS to Cisco IOS Migrations
Performing CG-OS to Cisco IOS Migrations
Use IoT FND to upgrade the firmware running on routers (CGR1000s, C800s, IR800s), AP800s and Cisco Resilient Mesh Endpoints (RMEs) such as meters and range extenders. IoT FND stores the firmware binaries in its database for later transfer to routers in a firmware group through an IoT FND and IoT-DM file transfer, and to RMEs using IoT FND.
Cisco provides the firmware bundles as a zip file. For Cisco IOS, software bundles include hypervisor, system image and IOx images (for example, Guest-OS, Host-OS).
For Cisco CG-OS, IoT FND automatically unzips the kickstart and system images included in the bundle. Firmware system images are large (approximately 130 MB); kickstart images are approximately 30 MB. Every firmware bundle includes a manifest file with metadata about the images in the bundle. You can pause, stop, or resume the upload process.
Router Firmware Updates
Note: In FND Release 4.6.1 and greater, you can initiate up to 400 downloads of router images in parallel with FND, irrespective of group.
Note: In FND Release 4.6.1 and greater, you can configure the ‘router-files-upload-retries =<value>’ property within cgms.properties to automatically retry a upload of the router firmware, should it fail.
IoT FND updates router firmware in two steps:
1.![]() Uploads the firmware image from IoT FND to the router. Firmware images upload to the flash:/managed/images directory on the router. Note: In some cases the router might be in a Firmware Group. Refer to Configuring Firmware Group Settings
Uploads the firmware image from IoT FND to the router. Firmware images upload to the flash:/managed/images directory on the router. Note: In some cases the router might be in a Firmware Group. Refer to Configuring Firmware Group Settings
Because of their large size, firmware-image uploads to routers take approximately 30 minutes, depending on interface speeds.
Note![]() : If you set the property, collect-cellular-link-metrics, to ‘true’ in cgms.properties, then the following Cellular link quality metrics are collected for CGR1000, IR800 and IR1100, each time you initiate a firmware upload from IoT FND:
: If you set the property, collect-cellular-link-metrics, to ‘true’ in cgms.properties, then the following Cellular link quality metrics are collected for CGR1000, IR800 and IR1100, each time you initiate a firmware upload from IoT FND:
–![]() RSRP: Reference Signal Received Power which is the power of the reference signal
RSRP: Reference Signal Received Power which is the power of the reference signal
–![]() RSRQ: Reference Signal Received Quality or the quality of the reference signal which is the a ratio of RSSI to RSRP
RSRQ: Reference Signal Received Quality or the quality of the reference signal which is the a ratio of RSSI to RSRP
–![]() SINR: Signal-to-Noise Ratio which compares the strength of the signal to the background noise.
SINR: Signal-to-Noise Ratio which compares the strength of the signal to the background noise.
–![]() RSSI: Received Signal Strength Indicator or the strength of the reference signal
RSSI: Received Signal Strength Indicator or the strength of the reference signal
Additionally, the following cgna profile is created on the CGR1240 and activated when the firmware upload is triggered.
Note: On execution of the cgna profile above, the metrics data is persisted in the Metrics_History table in the database and can be collected by using the getMetricHistory NBAPI.
2.![]() Installs the firmware on the device and reloads it.
Installs the firmware on the device and reloads it.
During the firmware install the boot parameters on the routers are updated according to the new image file and the router is reloaded after enabling the cg-nms-register cgna profile.
Note: You must initiate the firmware installation process. IoT FND does not automatically start the upload after the image upload.
When a router contacts IoT FND for the first time to register and request tunnel provisioning, IoT FND rolls the router back to the default factory configuration (ps-start-config) before uploading and installing the new firmware image.
Note: This rollback requires a second reload to update the boot parameters in ps-start-config and apply the latest configuration. This second reload adds an additional 10–15 minutes to the installation and reloading operation.
Upgrading Guest OS Images
Depending on CGR factory configuration, a Guest OS (GOS) may be present in the VM instance. You can install or upgrade Cisco IOS on the CONFIG > Firmware Update page (see Router Firmware Updates). The GOS, hypervisor, and Cisco IOS all upgrade when you perform a Cisco IOS image bundle installation or update.
After after any Cisco IOS install or upgrade, when IoT FND discovers a GOS, it checks if the initial communications setup is complete before it performs the required setup. The CGR must have a DHCP pool and GigabitEthernet 0/1 interface configured to provide an IP address and act as the gateway for the GOS. The new GOS image overwrites existing configurations. IoT FND has an internal backup and restore mechanism that ports existing apps to the upgraded Guest OS (see Monitoring a Guest OS in the “Managing Devices” chapter of this User Guide.
See the Cisco 1000 Series Connected Grid Routers Configuration Guides documentation page for information on configuring the CGR.
Note: If IoT FND detects a non-Cisco OS installed on the VM, the firmware bundle will not upload and the Cisco reference GOS will not install.
Upgrading WPAN Images
At the CONFIG > Firmware Update page, you can upload the independent WPAN images (IOS-WPAN-RF, IOS-WPAN-PLC, IOS-WPAN-OFDM, IOS-WPAN-IXM) to IoT FND using the Images sub-tab (left-hand side) and Upload Image button like other image upgrades. This process is known as a non-integrated WPAN firmware upgrade.
Note: The WPAN firmware image integrated with the IOS CGR image option is still supported.
Also, if only the WPAN firmware upgrade from the image bundled with IOS image is desired (for example, when the WPAN firmware upgrade option was not checked during IOS upgrade), the “Install from Router” option is also provided under respective WPAN image types (IOS-WPAN-RF or IOS-WPAN-PLC).
For detailed steps, go to Working with Router Firmware Images.
Changing Action Expiration Timer
You can use the cgnms_preferences.sh script to set or retrieve the action expiration timer value in the IoT FND database:
■![]() set <pkg>actionExpirationTimeoutMins<value>
set <pkg>actionExpirationTimeoutMins<value>
–![]() <pkg> is the preference package (required for set and get operations).
<pkg> is the preference package (required for set and get operations).
–![]() actionExpirationTimeoutMins is the preference key (required for set and get operations).
actionExpirationTimeoutMins is the preference key (required for set and get operations).
–![]() <value> is the preferred value, in minutes (required for set and setCgrActionExpirationTimeout operations).
<value> is the preferred value, in minutes (required for set and setCgrActionExpirationTimeout operations).
■![]() setCgrActionExpirationTimeout <value>
setCgrActionExpirationTimeout <value>
■![]() get <pkg>actionExpirationTimeoutMins
get <pkg>actionExpirationTimeoutMins
■![]() getCgrActionExpirationTimeout
getCgrActionExpirationTimeout
In the following example, the action timer value is retrieved, set, the current value retrieved again, the value removed, and a null value retrieved:
Working with Resilient Mesh Endpoint Firmware Images
This section describes how to add Resilient Mesh Endpoint (RME) firmware images to IoT FND, and how to upload and install the images on routers and addresses the following topics:
■![]() Uploading a Firmware Image to FND
Uploading a Firmware Image to FND
■![]() Uploading a Firmware Image to a Resilient Mesh Endpoint (RME) Group
Uploading a Firmware Image to a Resilient Mesh Endpoint (RME) Group
■![]() Firmware Update Transmission Settings
Firmware Update Transmission Settings
■![]() Setting the Installation Schedule
Setting the Installation Schedule
■![]() Viewing Mesh Device Firmware Image Upload Logs
Viewing Mesh Device Firmware Image Upload Logs
■![]() Modify Display of Firmware Management Page
Modify Display of Firmware Management Page
■![]() Viewing Mesh Device Firmware Image Upload Logs
Viewing Mesh Device Firmware Image Upload Logs
Overview
When you instruct IoT FND to upload a firmware image to the members of an RME firmware group or subnet, IoT FND pushes the image to the group members in the background and tracks the upload progress to ensure that the devices receive the image.
A Resilient Mesh Endpoint (RME) stores three firmware images:
■![]() Uploaded image: Image most recently uploaded.
Uploaded image: Image most recently uploaded.
■![]() Running image: Image that is currently operational.
Running image: Image that is currently operational.
■![]() Backup image: It serves as a golden (fallback) image for the RME if there is an issue with the running image.
Backup image: It serves as a golden (fallback) image for the RME if there is an issue with the running image.
Note: You can initiate up to 3 firmware downloads simultaneously.
Note: IR500s and other RME devices can coexist on a network; however, for firmware management they cannot belong to the same group.
Note: RME devices can report BL/Boot Loader image types to IoT FND, but IoT FND cannot upload boot loader images to devices.
Uploading a Firmware Image to FND
To upload a firmware image to mesh endpoint group members:
1.![]() Choose CONFIG > FIRMWARE UPDATE.
Choose CONFIG > FIRMWARE UPDATE.
2.![]() Select the Images tab (left-pane).
Select the Images tab (left-pane).
3.![]() Select the Endpoint Image type (such as BBU, IOx-IR500 LMAC) to be uploaded.
Select the Endpoint Image type (such as BBU, IOx-IR500 LMAC) to be uploaded.
4.![]() Click on + (plus icon) next to the FIRMWARE IMAGES heading to browse the firmware from your local system.
Click on + (plus icon) next to the FIRMWARE IMAGES heading to browse the firmware from your local system.
5.![]() Browse and click on Add file.
Browse and click on Add file.
IoT FND can upload the following image types to ENDPOINT devices (Firmware Images for Endpoints.)
For endpoints with Power line communication (PLC) radio only. |
|
Figure 1 Using IoT FND to Upload Images to an Endpoint
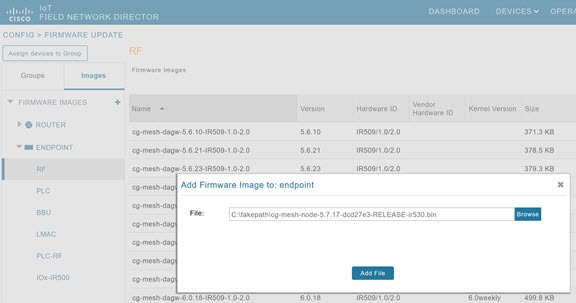
Uploading a Firmware Image to a Resilient Mesh Endpoint (RME) Group
To upload a firmware image to mesh endpoint group members:
1.![]() Choose CONFIG > FIRMWARE UPDATE.
Choose CONFIG > FIRMWARE UPDATE.
2.![]() Click the Groups tab (left-pane)
Click the Groups tab (left-pane)
3.![]() Select the Endpoint firmware group to update.
Select the Endpoint firmware group to update.
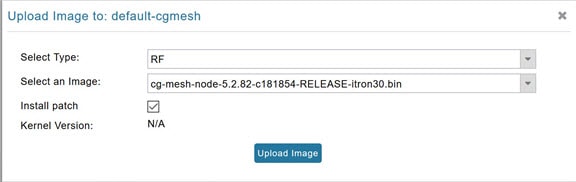
4.![]() In the right panel, select Firmware Management and then click the Upload Image button. In the entry panel that appears, do the following:
In the right panel, select Firmware Management and then click the Upload Image button. In the entry panel that appears, do the following:
a.![]() From the Select Type drop-down menu, choose the firmware type for your device.
From the Select Type drop-down menu, choose the firmware type for your device.
b.![]() From the Select an Image drop-down menu, choose the firmware bundle to upload.
From the Select an Image drop-down menu, choose the firmware bundle to upload.
d.![]() (Optional) Check the Install patch box, if you choose to install only the patch of the new image (Check Install Patch Item to ONLY Install the Patch Rather than the Full Image)
(Optional) Check the Install patch box, if you choose to install only the patch of the new image (Check Install Patch Item to ONLY Install the Patch Rather than the Full Image)
Figure 2 Check Install Patch Item to ONLY Install the Patch Rather than the Full Image
IoT FND adds the image to the list of images in the Firmware Management pane and starts the upload process in the background. A bar chart displays the upload progress (percentage complete). See Firmware Update - Percentage Complete (top-portion of screen) and Firmware Update - Upload Summary (bottom-portion of screen).
Note: Click the Sync Membership button (Figure 3) to ensure that FND and the member endpoint firmware group information is the same.
Figure 3 Firmware Update - Percentage Complete (top-portion of screen)
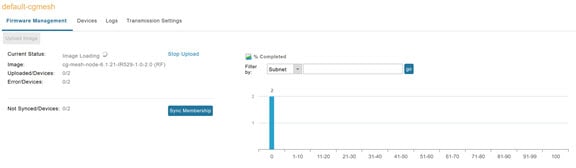
Figure 4 Firmware Update - Upload Summary (bottom-portion of screen)
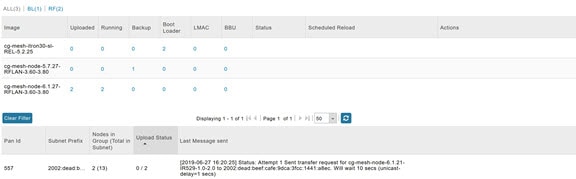
Actions Supported and Information Displayed at the Firmware Management Pane
At the Firmware Management pane, you can filter the display by Subnet, PanID or Group when you are in the Devices tab.
For every image in the list, IoT FND displays the information noted in Image Information Displayed by IoT FND.
Specifies the number of devices that uploaded the image. Click the number to display a list of these devices. |
|
Specifies the number of devices running this image. Click the number to display a list of these devices. |
|
Specifies the number of devices using this image as a backup. Click the number to display a list of these devices. |
|
| Schedule Install and Reload —Schedule the installation date and time of the loaded image and the reboot of the endpoint by selecting the Calendar icon. 
Set as Backup —Set the firmware backup image by selecting the clock icon with reverse arrow 
See Setting the Installation Schedule for complete steps. |
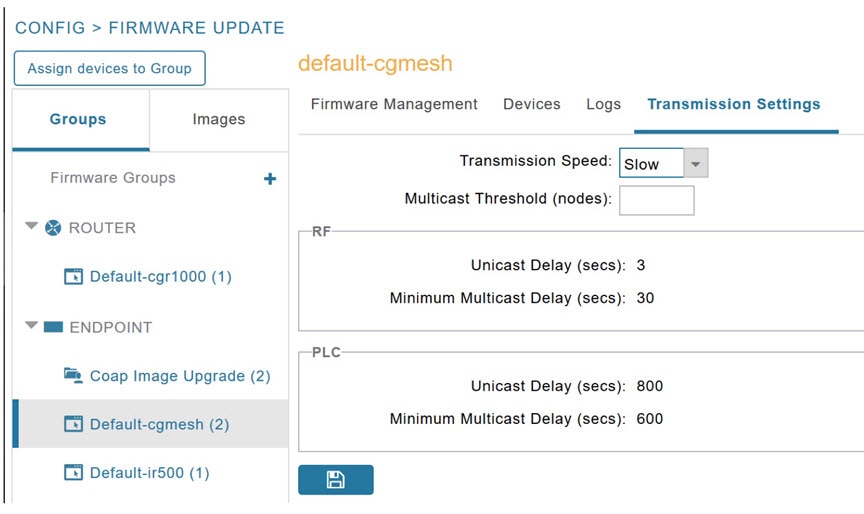
Firmware Update Transmission Settings
You can configure the Transmission Speed for pacing mesh firmware downloads at the Transmission Settings tab (CONFIG > FIMRWARE UPDATE page). See CONFIG > FIRMWARE UPDATE.
1.![]() Select the Transmission Speed. Options are Slow (default), Medium, Fast or Custom.
Select the Transmission Speed. Options are Slow (default), Medium, Fast or Custom.
Note![]() : The Slow setting is recommended as the initial setting. You can increase the Slow setting to Medium (or even Fast) if the following conditions exist:
: The Slow setting is recommended as the initial setting. You can increase the Slow setting to Medium (or even Fast) if the following conditions exist:
–![]() The slow setting does not cause any issues in the database and it is able to handle the workload presented without raising any alarms.
The slow setting does not cause any issues in the database and it is able to handle the workload presented without raising any alarms.
–![]() There is a need to improve on the time taken to do the firmware download.
There is a need to improve on the time taken to do the firmware download.
2.![]() Configure the minimum number of nodes necessary to enable the Multicast firmware upload.
Configure the minimum number of nodes necessary to enable the Multicast firmware upload.
Note![]() : For Custom Transmission Speed, you will have to specify Multicast Threshold, Unicast Delay and Minimum Multicast Delay values. See Definitions of variables seen on the CONFIG > FIRMWARE UPDATE > Transmissions Settings page for definitions for terms on the CONFIG > FIRMWARE UPDATE > Transmissions Settings page.
: For Custom Transmission Speed, you will have to specify Multicast Threshold, Unicast Delay and Minimum Multicast Delay values. See Definitions of variables seen on the CONFIG > FIRMWARE UPDATE > Transmissions Settings page for definitions for terms on the CONFIG > FIRMWARE UPDATE > Transmissions Settings page.
Figure 5 CONFIG > FIRMWARE UPDATE
Setting the Installation Schedule
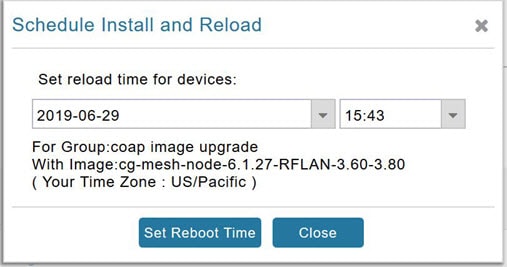
To set the installation schedule for an image:
1.![]() Click the Schedule install and Reload button (Calendar icon), See Actions summary in Image Information Displayed by IoT FND.
Click the Schedule install and Reload button (Calendar icon), See Actions summary in Image Information Displayed by IoT FND.
2.![]() In the page that appears (Schedule and Install and Reload Page), specify the date and time for the installation of the image and rebooting of device.
In the page that appears (Schedule and Install and Reload Page), specify the date and time for the installation of the image and rebooting of device.
Figure 6 Schedule and Install and Reload Page
Set a Firmware Backup Image
To set an image as a firmware image backup:
1.![]() Click the Set as Backup button. (See the icon in the Actions summary in Image Information Displayed by IoT FND).
Click the Set as Backup button. (See the icon in the Actions summary in Image Information Displayed by IoT FND).
Viewing Mesh Device Firmware Image Upload Logs
■![]() To sync the group members in the same firmware group, click Sync Membership button (Firmware Update - Percentage Complete (top-portion of screen)).
To sync the group members in the same firmware group, click Sync Membership button (Firmware Update - Percentage Complete (top-portion of screen)).
■![]() To view members devices, click the Devices tab. (Firmware Update - Percentage Complete (top-portion of screen))
To view members devices, click the Devices tab. (Firmware Update - Percentage Complete (top-portion of screen))
■![]() To view log files for the group, click the Logs tab. (Firmware Update - Percentage Complete (top-portion of screen))
To view log files for the group, click the Logs tab. (Firmware Update - Percentage Complete (top-portion of screen))
Modify Display of Firmware Management Page
You can filter the Firmware Management page display by Subnet, PanId or Group in the Devices tab.
Click the Sync Membership button to ensure that the information for FND and the member endpoint firmware group is the same.
Figure 7 CONFIG > FIRMWARE UPDATE

AP800 Firmware Upgrade During Zero Touch Deployment
During the PnP bootstrapping, whenever an access point (AP) or router sends the firmware request, FND will need to make the choice as to whether Unified Firmware or Autonomous Firmware is updated on the AP to make it accessible to the Cisco Wireless LAN Controller (WLC) after a firmware upgrade.
Note: Once you set up the DHCP server on a Cisco IOS router, WLC generally handles the software updates for the AP.
Allows you to set the desired firmware that will update an IR829 or C800 router during ZTD.
There are two possible firmware options:
■![]() Option 1: Set the ‘unified’ version (k9w8: the factory-shipped version) as the desired firmware.
Option 1: Set the ‘unified’ version (k9w8: the factory-shipped version) as the desired firmware.
■![]() Option 2: Set the autonomous firmware as the desired firmware version.
Option 2: Set the autonomous firmware as the desired firmware version.
During the ZTD process, the firmware upgrade of an access point (AP) or embedded AP on an IR829 or C800 router will upgrade using the firmware version you define as the autonomous firmware.
To define the Autonomous Firmware for an IR829 or C800 router:
1.![]() Choose CONFIG > DEVICE CONFIGURATION.
Choose CONFIG > DEVICE CONFIGURATION.
2.![]() Select the desired router: Default-ir800 or C800 (left-pane).
Select the desired router: Default-ir800 or C800 (left-pane).
3.![]() Check the installed firmware version, BEFORE upload. if equal to the latest version, skip firmware upgrade.
Check the installed firmware version, BEFORE upload. if equal to the latest version, skip firmware upgrade.
4.![]() Before you upload the software to the router, check the image and version:
Before you upload the software to the router, check the image and version:
a) If the router image version is equal to the latest version, skip upgrade.
b) If router image, has the latest
5.![]() Select Edit AP Configuration Template tab (right-pane).
Select Edit AP Configuration Template tab (right-pane).
6.![]() Enter the following text in the right-pane:
Enter the following text in the right-pane:
7.![]() Click disk icon (bottom of page) to save the commands in the configuration template.
Click disk icon (bottom of page) to save the commands in the configuration template.
8.![]() Once you set up the DHCP server on a Cisco IOS router,
Once you set up the DHCP server on a Cisco IOS router,
Mesh Firmware Migration (CG-OS CG4 platforms only)
Note: Mesh Firmware Migration to Cisco Resilient Mesh is not supported for CGRs running CG-OS version CG4(4).
IoT FND allows you to update earlier versions of CGR firmware to allow Cisco Resilient Mesh networking using the following IoT FND North Bound APIs:
■![]() startReprovisionByEidListAbridged
startReprovisionByEidListAbridged
■![]() startReprovisionByGroupAbridged
startReprovisionByGroupAbridged
See the North Bound API User Guide for the Cisco IoT Field Network Director, Releases 3.x and 4.x for usage information.
Image Diff Files for IR809 and IR829
To reduce file size that transfers across network for IR809 and IR829, you can send a partial image.
At the Upload Image page, select type: IOS-IR800
Check box for option: “install patch for IOS and hypervisor from this bundle.”
Gateway Firmware Updates
At the CONFIG > FIRMWARE UPDATE page, you can add or delete the IC3000 firmware image.
At the Images tab on that page, expand the Gateway icon and click on IC3000 to see a list of available IC3000 images.
Configuring Firmware Group Settings
This section describes how to add, delete, and configure firmware groups, and includes the following topics:
■![]() Assigning Devices to a Firmware Group
Assigning Devices to a Firmware Group
Note: Upload operations only begin when you click the Resume button.
When you add routers or RMEs to IoT FND, the application sorts the devices into the corresponding default firmware group: default- <router> or default-cgmesh. Use these groups to upload and install firmware images on member devices. Add firmware groups to manage custom sets of devices. You can assign devices to firmware groups manually or in bulk. Before deleting a firmware group, you must move all devices in the group to another group. You cannot delete non-empty groups.
Note: When creating firmware groups note the guidelines:
■![]() CGRs, IR800s, and C800s can coexist on a network; however, for firmware management, they cannot belong to the same firmware group.
CGRs, IR800s, and C800s can coexist on a network; however, for firmware management, they cannot belong to the same firmware group.
■![]() IR500s and other RMEs devices can coexist on a network; however, for firmware management, they cannot belong to the same group.
IR500s and other RMEs devices can coexist on a network; however, for firmware management, they cannot belong to the same group.
The Groups tab on the CONFIG > Firmware Update page displays various device metrics.
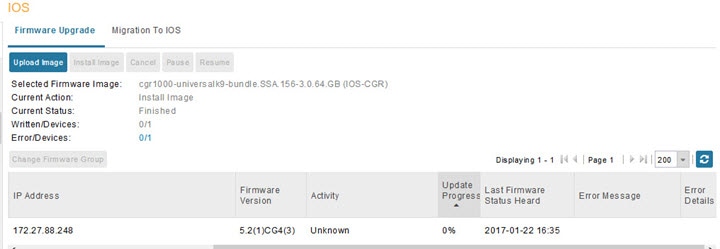
Tip: At the Firmware Update page, click the Error/Devices link (not shown) in Firmware Update Page – Viewing Errored Devices to apply a filter. Click the Clear Filter to revert to an unfiltered view of the selected device group.
Figure 8 Firmware Update Page – Viewing Errored Devices
Adding Firmware Groups
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Groups pane, select one of the following: Default-cgr1000, Default-c800, Default-ir500, Default-ir800, Default-cgmesh or Default-sbr.
In the Groups pane, select one of the following: Default-cgr1000, Default-c800, Default-ir500, Default-ir800, Default-cgmesh or Default-sbr.
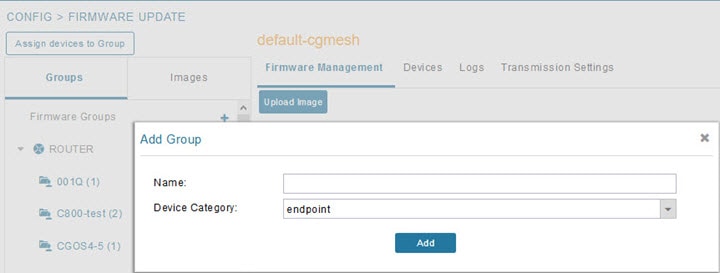
4.![]() Click + next to Firmware Groups heading in the Groups pane to Add Group.
Click + next to Firmware Groups heading in the Groups pane to Add Group.
5.![]() In the Add Group dialog box, enter the name of the firmware group. Device Category options depend on the device type you select in step In the Groups pane, select one of the following: Default-cgr1000, Default-c800, Default-ir500, Default-ir800, Default-cgmesh or Default-sbr.
In the Add Group dialog box, enter the name of the firmware group. Device Category options depend on the device type you select in step In the Groups pane, select one of the following: Default-cgr1000, Default-c800, Default-ir500, Default-ir800, Default-cgmesh or Default-sbr.
The new group label appears under the corresponding device type in the Firmware Groups pane.
To assign devices to the new group, see Assigning Devices to a Firmware Group.
Assigning Devices to a Firmware Group
This section describes moving devices, and includes the following topics:
Moving Devices to Another Group Manually
To manually move devices to a group:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Firmware Groups pane, select the desired firmware group based on device type.
In the Firmware Groups pane, select the desired firmware group based on device type.
Note: If this is an ENDPOINT firmware group, click the Devices![]() tab above the main pane.
tab above the main pane.
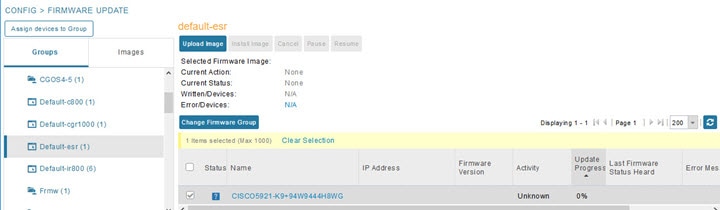
4.![]() Check the check boxes of the devices that you want to move.
Check the check boxes of the devices that you want to move.
5.![]() Click Change Firmware Group. to open a pop up window.
Click Change Firmware Group. to open a pop up window.
6.![]() From the Firmware Group drop-down menu, choose the firmware group to which you want to move the devices or enter a new group name.
From the Firmware Group drop-down menu, choose the firmware group to which you want to move the devices or enter a new group name.
Moving Devices to Another Group In Bulk
To move devices from one group to another in bulk:
1.![]() Create a CSV or XML file listing devices that you want to move using the format shown in the following examples:
Create a CSV or XML file listing devices that you want to move using the format shown in the following examples:
Note: Each file can only list one device type.
2.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
4.![]() Click Assign devices to Firmware Group button (found above Groups tab).
Click Assign devices to Firmware Group button (found above Groups tab).
5.![]() In the window that appears, click Browse and locate the device list CSV or XML file.
In the window that appears, click Browse and locate the device list CSV or XML file.
6.![]() From the Group drop-down menu, choose the destination group.
From the Group drop-down menu, choose the destination group.
IoT FND moves the devices listed in the file from their current group to the destination group.
Renaming a Firmware Group
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Firmware Groups pane, select the firmware group to rename.
In the Firmware Groups pane, select the firmware group to rename.
4.![]() Move the cursor over the group and click the Edit Group Name pencil icon.
Move the cursor over the group and click the Edit Group Name pencil icon.

5.![]() In the Rename Group window, enter the new name and then click OK.
In the Rename Group window, enter the new name and then click OK.
Note: When you enter an invalid character entry (such as, @, #, !, or +) within the Rename Group field, IoT FND displays a red alert icon, highlights the field in red, and disables the OK![]() button.
button.
Deleting Firmware Groups
Note: Before deleting a firmware group, you must move all devices in the group to another group. You cannot delete non-empty groups.
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Firmware Groups pane, select a firmware group to display a list of all possible firmware images for that group in the right pane.
In the Firmware Groups pane, select a firmware group to display a list of all possible firmware images for that group in the right pane.
4.![]() Check the box next to the firmware group that you want to delete.
Check the box next to the firmware group that you want to delete.
5.![]() Click Clear Selection that appears above the entry (yellow bar).
Click Clear Selection that appears above the entry (yellow bar).
Working with Router Firmware Images
This section describes how to add router firmware images to IoT FND and how to upload and install the images on routers, and includes the following topics:
■![]() Viewing Firmware Image Files in IoT FND
Viewing Firmware Image Files in IoT FND
■![]() Adding a Firmware Image to IoT FND
Adding a Firmware Image to IoT FND
■![]() Uploading a Firmware Image to a Router Group
Uploading a Firmware Image to a Router Group
■![]() Canceling Router Firmware Image Upload
Canceling Router Firmware Image Upload
■![]() Pausing and Resuming Router Firmware Image Uploads
Pausing and Resuming Router Firmware Image Uploads
■![]() Stopping Firmware Image Installation
Stopping Firmware Image Installation
■![]() Pausing and Resuming Router Firmware Image Installation
Pausing and Resuming Router Firmware Image Installation
Viewing Firmware Image Files in IoT FND
You can display firmware image information from the Images pane in the CONFIG > Firmware Update page. Select ROUTER or ENDPOINT to display all firmware images for those devices in the IoT FND database. Select the firmware image type to refine the display (see CONFIG > Firmware Update Images Pane).
Figure 9 CONFIG > Firmware Update Images Pane
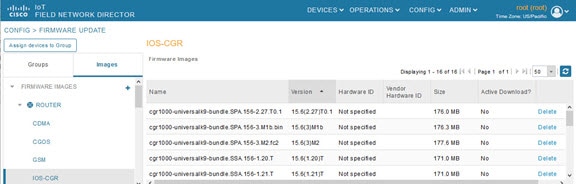
For every image in the list, IoT FND provides this information:
|
|
|
|---|---|
| The version of the firmware bundle. Click the arrowhead icon to switch between ascending and descending listing of the firmware version. |
|
Adding a Firmware Image to IoT FND
Before you can upload and install a firmware image on a device, add the image file (as a zip archive) to IoT FND. IoT FND stores the image in its database.
Note: Do not unzip the image file. IoT FND unzips the file.
To add a firmware image to IoT FND:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
2.![]() Click the Images tab (CONFIG > Firmware Update Images Pane).
Click the Images tab (CONFIG > Firmware Update Images Pane).
3.![]() In the Images pane, select ROUTER, ENDPOINT or GATEWAY, and the type of device group.
In the Images pane, select ROUTER, ENDPOINT or GATEWAY, and the type of device group.
4.![]() Click the + icon to select an image found to the right of the Firmware Images heading.
Click the + icon to select an image found to the right of the Firmware Images heading.
5.![]() Click Browse to locate the firmware image. Select the image, then click Add File.
Click Browse to locate the firmware image. Select the image, then click Add File.
The image appears in the Firmware Images panel (CONFIG > Firmware Update Images Pane).
| ■ |
| Firmware images with a download in progress (with Yes in the Active Download? column) cannot be deleted. |
| ■ |
Uploading a Firmware Image to a Router Group
When you upload a firmware image to router firmware group members, IoT FND pushes the image to the group members in the background and tracks the upload progress to ensure that the devices receive the image.
On routers, firmware image upload and installation requires 200 MB of free disk space. IoT FND stores image files in the.../managed/images directory on the router.
Note: If there is not enough disk space on the router for the firmware image, the IoT FND initiates disk cleanup process on the router and removes the following files, sequentially, until there is enough disk space to upload the new image:
■![]() Unused files in the.../managed/images directory that are not currently running or referenced in the before-tunnel-config, before-registration-config, express-setup-config, and factory-config files for IOS CGRs; golden-config, ps-start-config, express-setup-config, or factory-config for CG-OS CGRs
Unused files in the.../managed/images directory that are not currently running or referenced in the before-tunnel-config, before-registration-config, express-setup-config, and factory-config files for IOS CGRs; golden-config, ps-start-config, express-setup-config, or factory-config for CG-OS CGRs
■![]() Unused.gbin and.bin files from the bootflash directory in CG-OS CGRs
Unused.gbin and.bin files from the bootflash directory in CG-OS CGRs
If there is still not enough space, you must manually delete unused files on the router.
To upload a firmware image to router group members:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Groups pane, select the router firmware group that you want to update.
In the Groups pane, select the router firmware group that you want to update.
Note: CGR groups can include devices running Cisco IOS and CG-OS. Therefore, Cisco IOS software images only upload to devices running Cisco IOS (C5921s, IR800s, ISR800s, CGR1000s); only CGRs accept CG-OS images.
IoT FND displays the firmware image type applicable to the router:
|
|
|
|
|---|---|---|
| Image (Cisco IOS only) loads to IR807 within the IR800 firmware group. |
||
| LoRaWAN IXM module when operating as an interface for Cisco IR809. |
||
4.![]() Click Upload Image to open the entry panel.
Click Upload Image to open the entry panel.
5.![]() From the Select Type: drop-down menu, choose the firmware type for your device.
From the Select Type: drop-down menu, choose the firmware type for your device.
6.![]() From the Select an Image: drop-down menu, choose the firmware bundle to upload.
From the Select an Image: drop-down menu, choose the firmware bundle to upload.
For some software bundles, you also have the option to select one or more of the following options (as noted in parenthesis next to the options listed below):
–![]() Install Guest OS from this bundle (IOS-CGR, IOS-IR800)
Install Guest OS from this bundle (IOS-CGR, IOS-IR800)
–![]() Clean LoRaWAN application data on the install (LORAWAN)
Clean LoRaWAN application data on the install (LORAWAN)
–![]() Install WPAN firmware from this bundle (IOS-CGR)
Install WPAN firmware from this bundle (IOS-CGR)
IoT FND starts the upload process. After the image uploads, install the image as described in Installing a Firmware Image.
Canceling Router Firmware Image Upload
You can stop the image upload process to firmware router groups at any time. Stopping the upload can take a few minutes. When you cancel the image upload, the image upload process immediately stops currently running tasks, and blocks all queued tasks.
Note: Running tasks do not complete, leaving partial files on the disk and sets the firmware group status to CANCELING until you complete the upload operation.
To stop firmware image uploading to a group:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
Pausing and Resuming Router Firmware Image Uploads
You can pause the image upload process to router firmware groups at any time, and resume it later.
Note: The image upload process does not immediately pause; all queued (but not running) operations pause, but currently running tasks complete. The status changes to PAUSING until the active operations complete.
To pause firmware image upload:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Groups pane, select the firmware group.
In the Groups pane, select the firmware group.
The Status column displays PAUSING until the active upload operations complete. No new upload operations start until you click the Resume button.
To resume the upload process, click Resume.
Note: If a IoT FND server goes down while the firmware image is being uploaded to devices, the server resumes the upload process for the scheduled devices after the server comes up. For IoT FND server clusters, if one server goes down during the upload process, another server in the cluster resumes the process.
Installing a Firmware Image
To install an image on devices in a router firmware group:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Groups pane, select the firmware group.
In the Groups pane, select the firmware group.
Note: IoT FND recognizes devices as firmware-specific, and uploads the proper image to selected devices.
4.![]() In the Images pane, select a device subgroup (such as IOS-CGR, IOS-WPAN-RF, CDMA) to refine the display to those device types.
In the Images pane, select a device subgroup (such as IOS-CGR, IOS-WPAN-RF, CDMA) to refine the display to those device types.
This step above is necessary because IoT FND recognizes devices as firmware-specific and ensures the system uploads the proper image to selected devices.
5.![]() At the CONFIG > Firmware Update page, click the Groups tab; and, then Install Image on the Firmware Upgrade tab.
At the CONFIG > Firmware Update page, click the Groups tab; and, then Install Image on the Firmware Upgrade tab.
IoT FND sends commands to install the uploaded image and make it operational.
IoT FND starts the installation or reloading process.
Note: If you restart IoT FND during the image installation process, IoT FND restarts the firmware installation operations that were running prior to IoT FND going offline.
You can pause or stop the installation operation as described in:
■![]() Stopping Firmware Image Installation
Stopping Firmware Image Installation
■![]() Pausing and Resuming Router Firmware Image Installation
Pausing and Resuming Router Firmware Image Installation
Note: The firmware installation operation can time out on some routers. If routers are not heard from for more than an hour, IoT FND logs error messages.
Stopping Firmware Image Installation
You can stop firmware image installation at any time. When you stop image installation, the running version of the firmware remains in place.
Note: Stopping the installation cancels all queued tasks. Currently running tasks complete.
To stop firmware image installation to devices in a firmware group:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
3.![]() In the Groups pane, select the firmware group.
In the Groups pane, select the firmware group.
Pausing and Resuming Router Firmware Image Installation
You can pause the firmware image installation process at any time.
Note: Pausing the installation pauses all queued tasks. Currently running tasks complete.
To pause firmware image installation to devices in a firmware group:
1.![]() Choose CONFIG > Firmware Update.
Choose CONFIG > Firmware Update.
2.![]() In the Groups pane, select the firmware group.
In the Groups pane, select the firmware group.
3.![]() In the Firmware Upgrade window, click Pause button.
In the Firmware Upgrade window, click Pause button.
Performing CG-OS to Cisco IOS Migrations
You can upgrade CGRs from CG-OS to IOS in bulk or by device. The migration package is in the IoT Field Network Director installation package, and is available in the Select IOS Image menu.
Note: The Migration to IOS button is disabled if all CGRs in the group are IOS.
For CG-OS CGRs that you are migrating, modify the device configuration properties CSV or XML file to include the following IOS properties (see Changing Device Configuration Properties):
This example preserves tunnels during migration:
Note: You can only migrate from CG4(3) to the minimum IOS image for that device. Refer to Table 4 for minimum IOS image requirements.
To add CGR IOS images to IoT Field Network Director and upload and install the migration image on CGRs:
1.![]() Select CONFIG > Firmware Update, and click the Migration to IOS tab.
Select CONFIG > Firmware Update, and click the Migration to IOS tab.
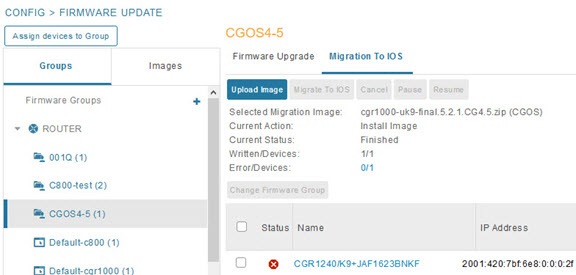
2.![]() In the Groups pane, select a CGR (or a group of CGRs) running CGOS4(5) software.
In the Groups pane, select a CGR (or a group of CGRs) running CGOS4(5) software.
3.![]() Select the Cisco IOS software image to upload to the CGR(s), and click Upload Image (right-pane).
Select the Cisco IOS software image to upload to the CGR(s), and click Upload Image (right-pane).
4.![]() Click OK to begin the upload.
Click OK to begin the upload.
Upload progress appears in the device list.
5.![]() Upload the following properties files (see Installing Cisco IoT FND in the appropriate Cisco IoT FND 4.3 and greater installation guide):
Upload the following properties files (see Installing Cisco IoT FND in the appropriate Cisco IoT FND 4.3 and greater installation guide):
–![]() Cisco IoT Field Network Director Installation Guide-Oracle Deployment, Releases 4.3.x, 4.4.x, 4.5.x and 4.6.x
Cisco IoT Field Network Director Installation Guide-Oracle Deployment, Releases 4.3.x, 4.4.x, 4.5.x and 4.6.x
–![]() Cisco IoT Field Network Director Post-Installation Guide - Release 4.3.x (Tunnel Provisioning and High Availability) and greater
Cisco IoT Field Network Director Post-Installation Guide - Release 4.3.x (Tunnel Provisioning and High Availability) and greater
6.![]() Click the Migrate To IOS button.
Click the Migrate To IOS button.
7.![]() Click Yes to confirm and begin the migration process.
Click Yes to confirm and begin the migration process.
The Update Progress displays as a percentage during the software image upload. If an upload fails, error messages and error details also appear for the software image. You can cancel, pause, or resume the migration process.
Tip: If any routers fail to upgrade, restart migration on the group. IoT Field Network Director skips routers that were successfully upgraded.
Interface Names After Migration
IoT Field Network Director preserves metrics for the various interfaces and associated properties during migration. CG-OS-to-IOS Interface Migration Map maps CG-OS interfaces to the corresponding IOS interfaces to preserve metrics.
 Feedback
Feedback