How change of authorization reauthentication work
Summary
Change of authorization reauthentication enables dynamic policy changes in AAA sessions after initial authentication.
-
When a policy changes for a user or user group in AAA, administrators can send RADIUS CoA packets from the AAA server.
-
The AAA server, such as Cisco Identity Services Engine, uses CoA packets to reinitialize authentication and apply the new policy.
-
The RADIUS interface provides various primitives that can be used during a CoA event.
-
These primitives and their functions are essential for effectively applying new policies to users or groups during a session.
Workflow
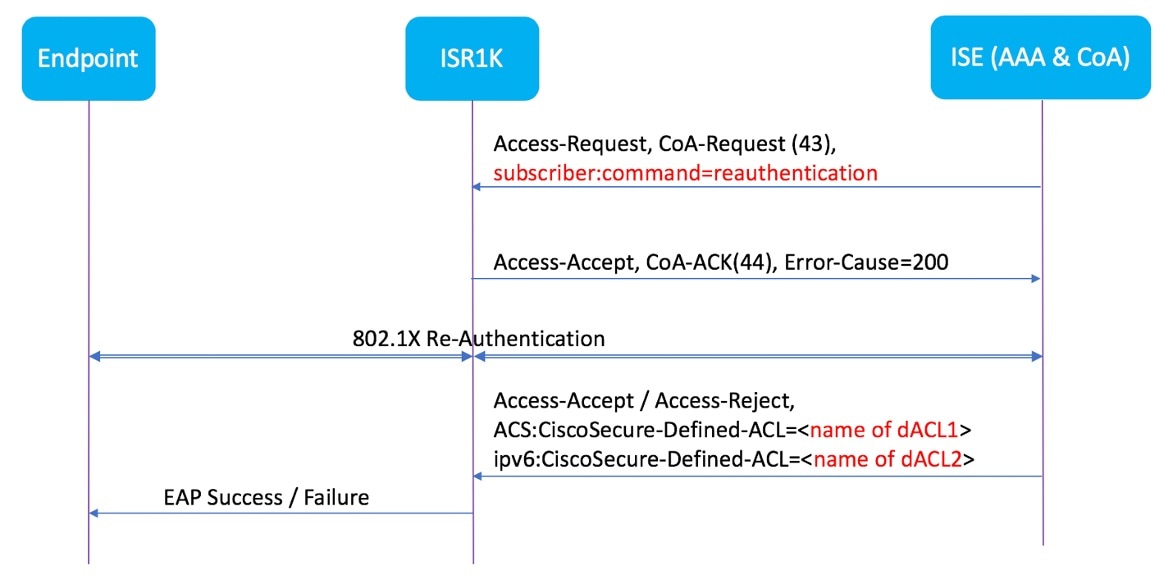
- The administrator changes a user or user group policy in the AAA system.
- The AAA server sends a RADIUS CoA packet to the network device, specifying policy updates.
- The device receives the CoA packet and reinitializes authentication, applying the new policy.
- The RADIUS interface returns either a CoA-ACK (acknowledgement) or CoA-NAK (nonacknowledgement) as a response.
Result
By default, the RADIUS interface is enabled on the device. However, some basic configuration is required for the following attributes:
-
Security and Password
-
Accounting
-
CoA acknowledgement (ACK) [CoA-ACK]
-
CoA nonacknowledgement (NAK) [CoA-NAK]
What’s next
After posture assessment is succeessful, full network access is pushed down to the device for specific client through CoA re-authentication command based on its compliance state derived from last assessment. It is optional to enforce downloadable ACLs with Permit-ALL or limited access to certain resources to corresponding clients. Per-session CoA requests are supported for session identification, session termination, host reauthentication, port shutdown, and port bounce. This model comprises one request (CoA-Request) and two possible response codes:
 Feedback
Feedback