|
Step 1
|
enable
|
Enables privileged EXEC mode.
Enter your password if prompted.
|
|
Step 2
|
configure
terminal
Device# configure terminal
|
Enters global configuration mode.
|
|
Step 3
|
aaa new-model
Device(config)# aa new-model
|
|
|
Step 4
|
aaa authentication dot1x {default | listname}
groupgroup-name
Device(config)# aaa authentication dot1x default group ise
|
Creates a series of authentication methods that are used to determine user privilege to access the privileged command level
so that the device can communicate with the AAA server.
|
|
Step 5
|
aaa authorization network {default | listname}group
group-name
Device(config)# aaa authentication network default group coa-ise
|
Creates a series of authentication methods that are used to determine user privilege to access the privileged command level
so that the device can communicate with the AAA server.
|
|
Step 6
|
dot1x system-auth-control
Device(config)# dot1x system-auth-control
|
Globally enables 802.1X port-based authentication.
|
|
Step 7
|
dot1x system-auth-control
Device(config)# dot1x system-auth-control
|
Globally enables 802.1X port-based authentication.
|
|
Step 8
|
aaa group server radius
{radius | tacacs+} group-name
Device(config)# aaa group server radius coa-ise
|
Defines the AAA server group with a group name. Example: Device(config)# aaa group server radius group1 • All members of a
group must be the same type, that is, RADIUS or TACACS+. This command puts the device in server group RADIUS configuration
mode.
|
|
Step 9
|
radius server
server-name
Device(config)# radius server cts
|
Specifies the name for the RADIUS server.
|
|
Step 10
|
server
ip-address [ auth-portport-number [ acct-portport-number
Device(config-sg-radius)# address ipv4 %{ise.ip} auth-port 1812 acct-port 1813
|
Specifies the name for the RADIUS server.
|
|
Step 11
|
pac key
encyrption-key
Device(config-sg-radius)# pac key 0 cisco123
|
Specifies the PAC encryption key (overrides the default).
|
|
Step 12
|
policy-map type control subscribercontrol-policy-name
Device(config)# policy-map type control subscriber simple_dot1x
|
Defines a control policy for subscriber sessions.
|
|
Step 13
|
event
event-name[match-all | match-first]
Device(config-event-control-policymap)# event session-started match-all
|
Specifies the type of event that triggers actions in a control policy if conditions are met.
|
|
Step 14
|
priority-number class
{control-class-name | always}[do-all | do-until-failure | do-until-success]
Device(config-event-control-policymap)# 10 class always do-until-failur
|
Associates a control class with one or more actions in a control policy.
|
|
Step 15
|
action-number authenticate using
{dot1x | mab | webauth}aaa {authc-list authc-list-name | authz-list authz-list-name]} [merge] [parameter-map map-name] [priority priority-number]
[replace | replace-all] [retries number {retry-time seconds}
Device(config-event-control-policymap)# 10 authenticate using dot1x
|
Optional) Initiates the authentication of a subscriber session using the specified method.
|
|
Step 16
|
interface
interface-id
Device(config)# interface gigabitethernet0/1
|
Enter the interface to be added to the VLAN.
|
|
Step 17
|
switchport access vlan
vlan-id
Device(config-if)# switchport access vlan 22
|
Assign the port to a VLAN. Valid VLAN IDs are 1 to 4094
|
|
Step 18
|
switchport access mode
Device(config-if)# switchport mode access
|
Assign the port to a VLAN. Valid VLAN IDs are 1 to 4094
|
|
Step 19
|
access-session closed
Device(config-if)# access-session closed
|
The access-session closed command closes access to a port, preventing clients or devices from gaining network access before authentication is performed.
|
|
Step 20
|
access-session port-control
{auto | force-authorized | force-unauthorized }
Device(config-if)# access-session port-control auto
|
Sets the authorization state of a port.
|
|
Step 21
|
policy-map type control subscribercontrol-policy-name
Device(config-if)# policy-map type control subscriber simple_coa
|
Defines a control policy for subscriber sessions.
|
|
Step 22
|
dot1x pae [supplicant | authenticator | both ]
Device(config-if)# dot1x pae authenticator
|
Sets the Port Access Entity (PAE) type.
-
supplicant—The interface acts only as a supplicant and does not respond to messages that are meant for an authenticator.
-
authenticator-—The interface acts only as an authenticator and does not respond to any messages meant for a supplicant.
-
both—The interface behaves both as a supplicant and as an authenticator and thus does respond to all dot1x messages.
|
|
Step 23
|
end
|
Exits Cisco TrustSec manual interface configuration mode and enters privileged EXEC mode.
|
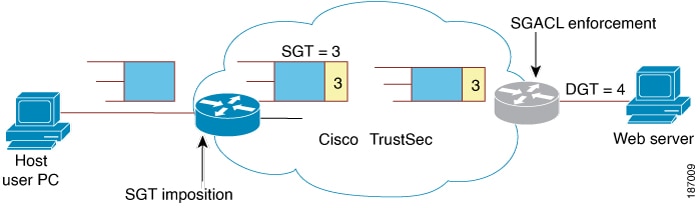
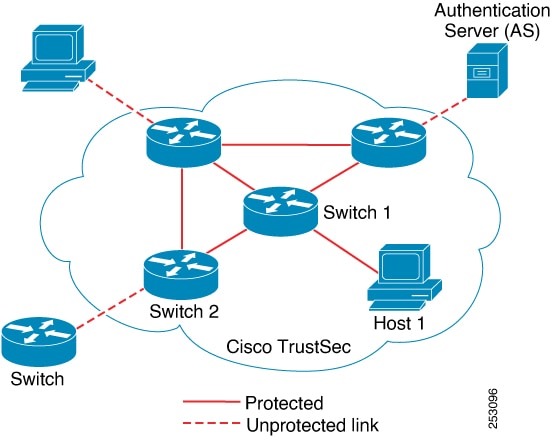

 Feedback
Feedback