Feature Information for PfRv3 Zero SLA Support
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
PfRv3 Path of Last Resort Support |
15.5(3)M |
The PfRv3 Path of Last Resort is a route used by the device when a service provider cannot be reached or the exits are out of bandwidth. The following commands were modified or added by this feature: domain path isp-name, show domain default vrf border, show domain default vrf master. |
|
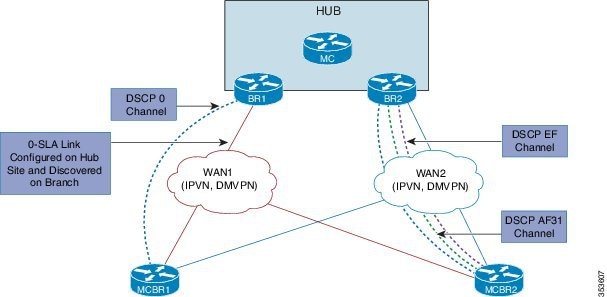
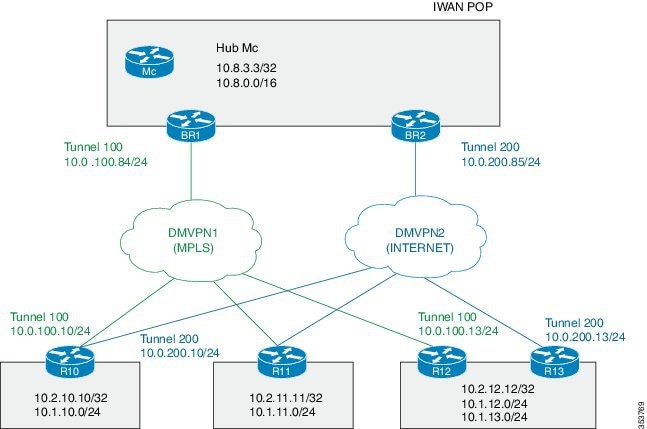
Performance Routing v3 Zero SLA Support |
15.5(1)T Cisco IOS XE Release 3.14S |
The Performance Routing v3 Zero SLA Support enables users to reduce probing frequency on various ISP links. The following command was modified by this feature:domain (interface configuration). |

 Feedback
Feedback