Subscribing to the CCR
The procedures for subscribing to the CCR vary depending on the release of the Cisco Cloud APIC software:
-
For releases up to 25.0(3), Cisco Cloud APIC uses the CSR 1000v as the cloud services router, so refer to the procedures in Subscribing to the Cisco Cloud Services Router 1000V.
-
For release 25.0(3) and later, Cisco Cloud APIC uses the CCR 8000v as the cloud services router, so refer to the procedures in Subscribing to the Cisco Cloud Router 8000V.
Subscribing to the Cisco Cloud Services Router 1000V
You must subscribe to the Cisco Cloud Services Router (CSR) 1000V - Bring Your Own License (BYOL) for Maximum Performance. To subscribe through the Microsoft Azure Marketplace:
Procedure
| Step 1 |
In the Azure Marketplace search text field, type Cisco Cloud Services Router (CSR) 1000V and select the option that appears. |
||||||||||
| Step 2 |
Click the Cisco Cloud Services Router (CSR) 1000V option. You should be redirected to the Cisco Cloud Services Router (CSR) 1000V page in the Microsoft Azure Marketplace. |
||||||||||
| Step 3 |
Locate the Select a software plan drop-down menu. If you do not see the Select a software plan drop-down menu in the main page, you might have to click the Plans + Pricing tab, if that option is available, to access the Select a software plan drop-down menu. |
||||||||||
| Step 4 |
In the Select a software plan drop-down menu, locate the area that lists the Cisco CSR 1000V Bring Your Own License options. 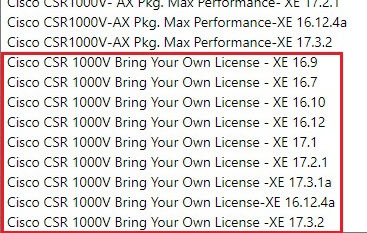
|
||||||||||
| Step 5 |
Select the appropriate option, depending on the Cisco Cloud APIC software release:
|
||||||||||
| Step 6 |
Locate the Want to deploy programmability? field and click Get Started. |
||||||||||
| Step 7 |
In the Configure Programmability Deployment page, scroll down to your subscription and, in the Status column, change the status from Disable to Enable for your subscription. |
||||||||||
| Step 8 |
Click Save. |
What to do next
Subscribing to the Cisco Cloud Router 8000V
You must subscribe to the Cisco Cloud Router (CCR) 8000V - Bring Your Own License (BYOL) for Maximum Performance. To subscribe through the Microsoft Azure Marketplace:
Procedure
| Step 1 |
In the Azure Marketplace search text field, type Cisco Catalyst 8000V Edge Software and select the option that appears. |
||||
| Step 2 |
Click the Cisco Catalyst 8000V Edge Software option. You should be redirected to the Cisco Catalyst 8000V Edge Software page in the Microsoft Azure Marketplace. |
||||
| Step 3 |
Locate the Select a software plan drop-down menu. If you do not see the Select a software plan drop-down menu in the main page, you might have to click the Plans + Pricing tab, if that option is available, to access the Select a software plan drop-down menu. |
||||
| Step 4 |
In the Select a software plan drop-down menu, select the appropriate option, depending on the Cisco Cloud APIC software release:
|
||||
| Step 5 |
Locate the Want to deploy programmability? field and click Get Started. |
||||
| Step 6 |
In the Configure Programmability Deployment page, scroll down to your subscription and, in the Status column, change the status from Disable to Enable for your subscription. |
||||
| Step 7 |
Click Save. |

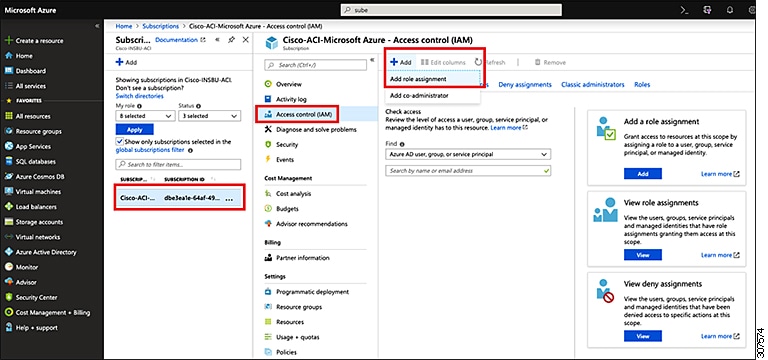
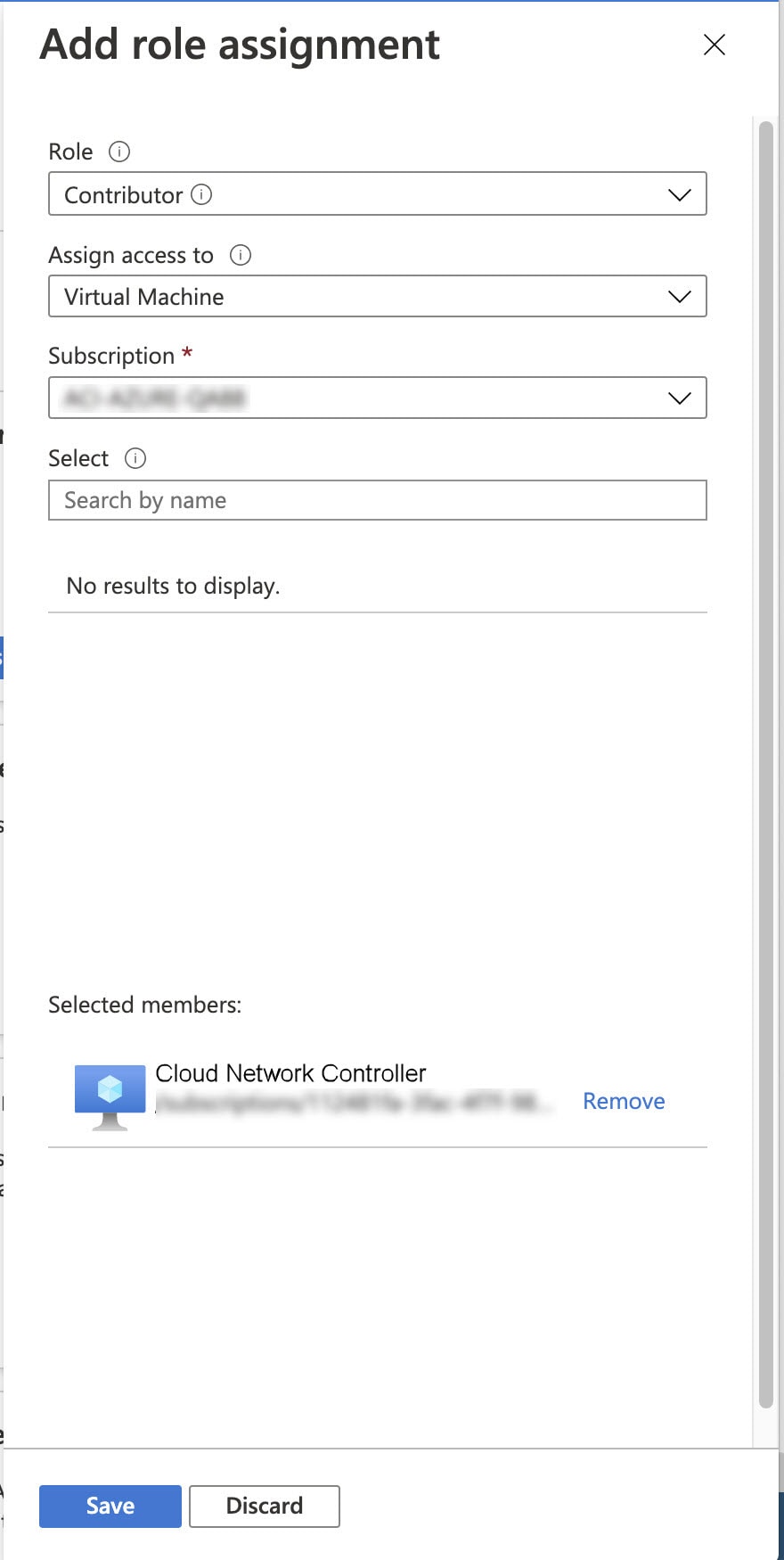
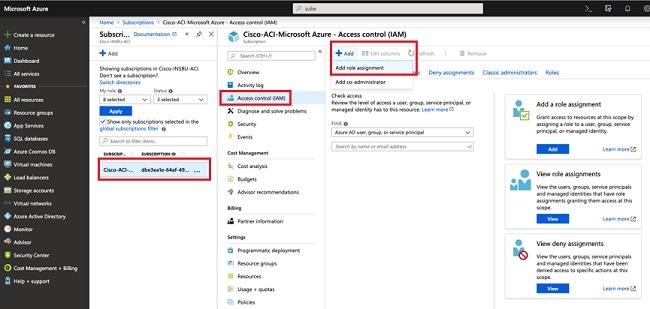
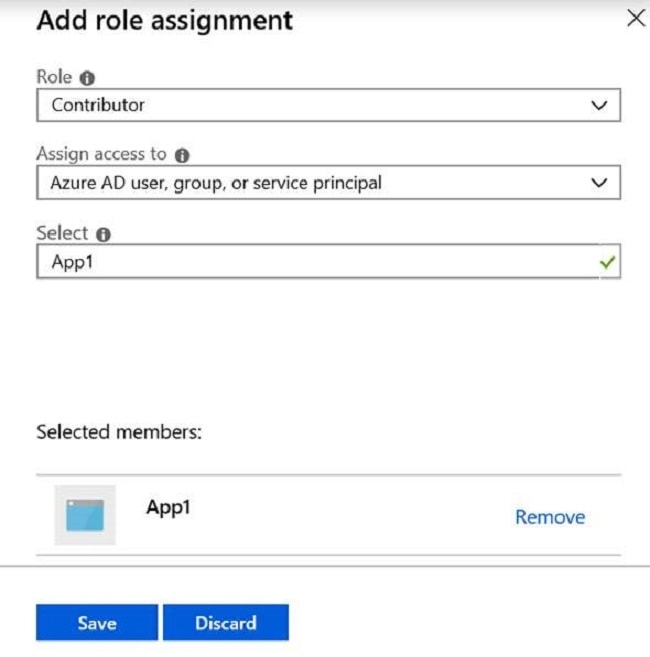
 Feedback
Feedback