Access Hosted Cisco Global Launchpad
You can access Cisco Global Launchpad with Cisco DNA Portal.
If you are new to Cisco DNA Portal, you must create a Cisco account and a Cisco DNA Portal account. Then you can log in to Cisco DNA Portal to access Cisco Global Launchpad.
If you are familiar with Cisco DNA Portal and have a Cisco account and a Cisco DNA Portal account, you can directly log in to Cisco DNA Portal to access Cisco Global Launchpad.
Log In to the Cisco DNA Portal with Cisco
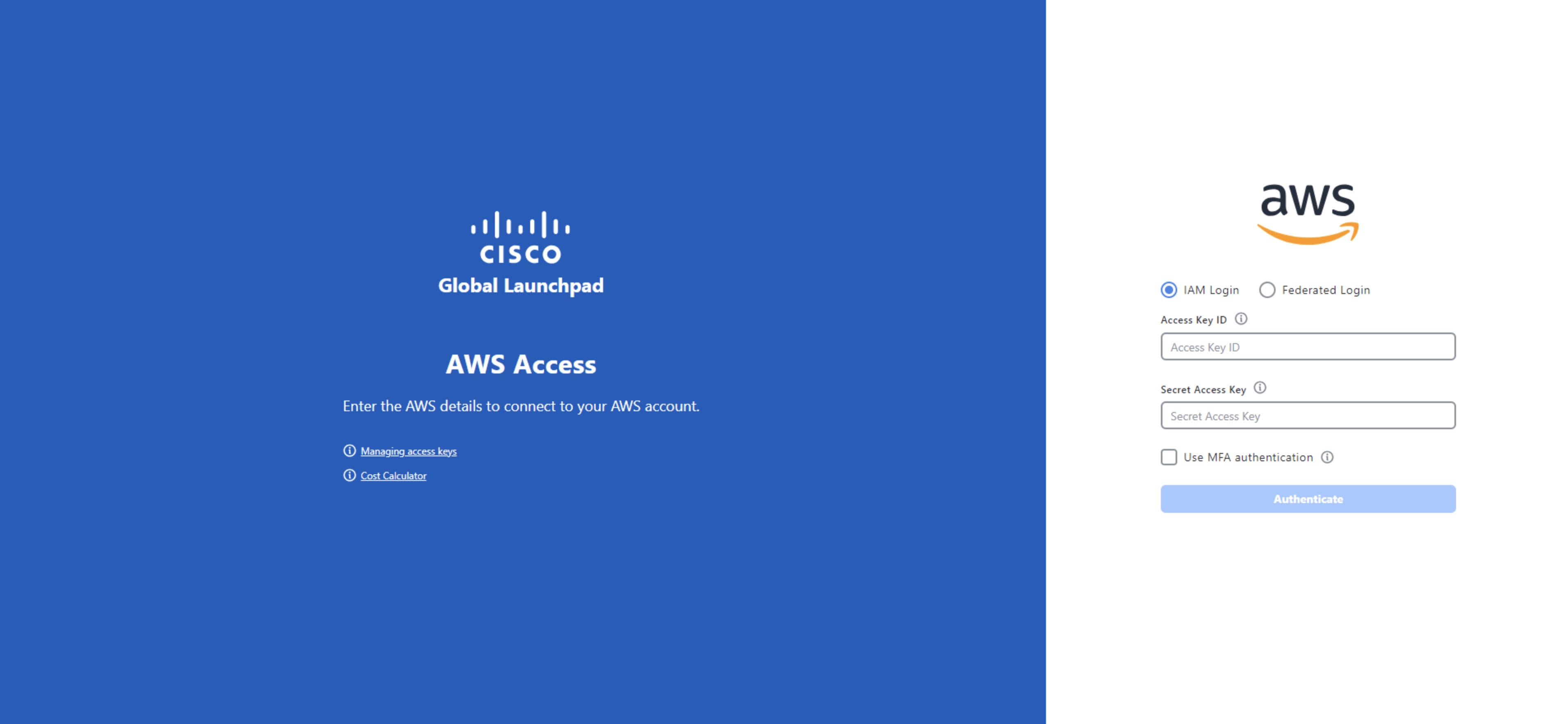
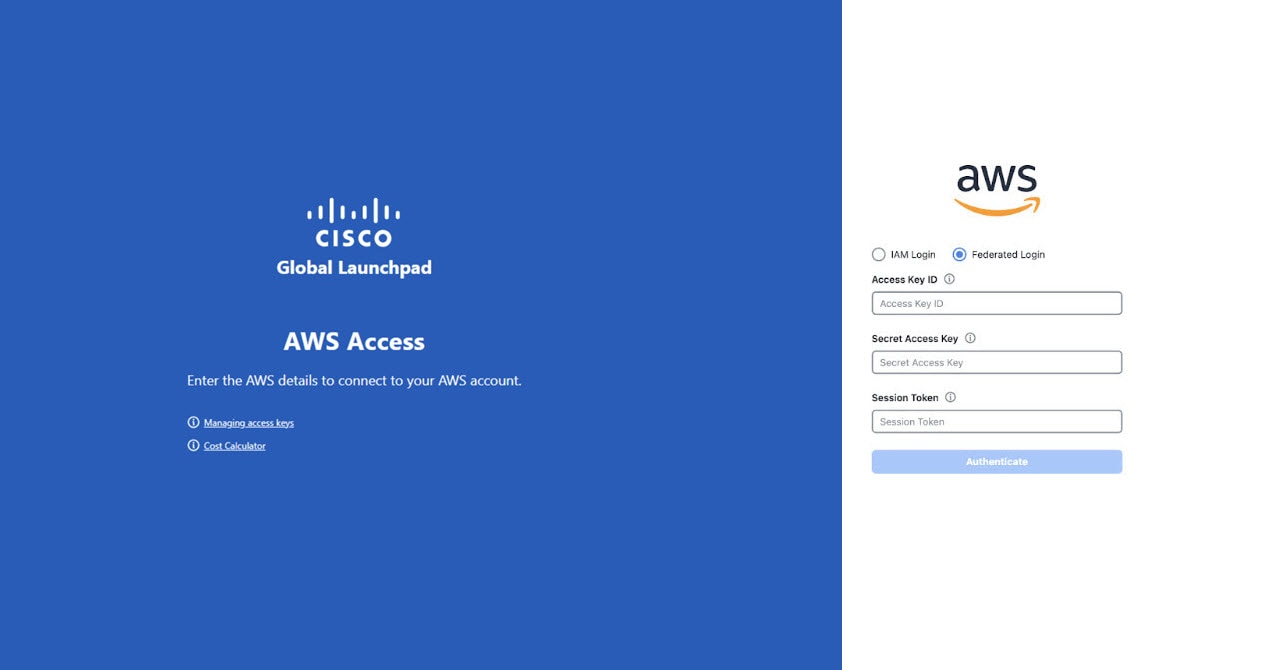
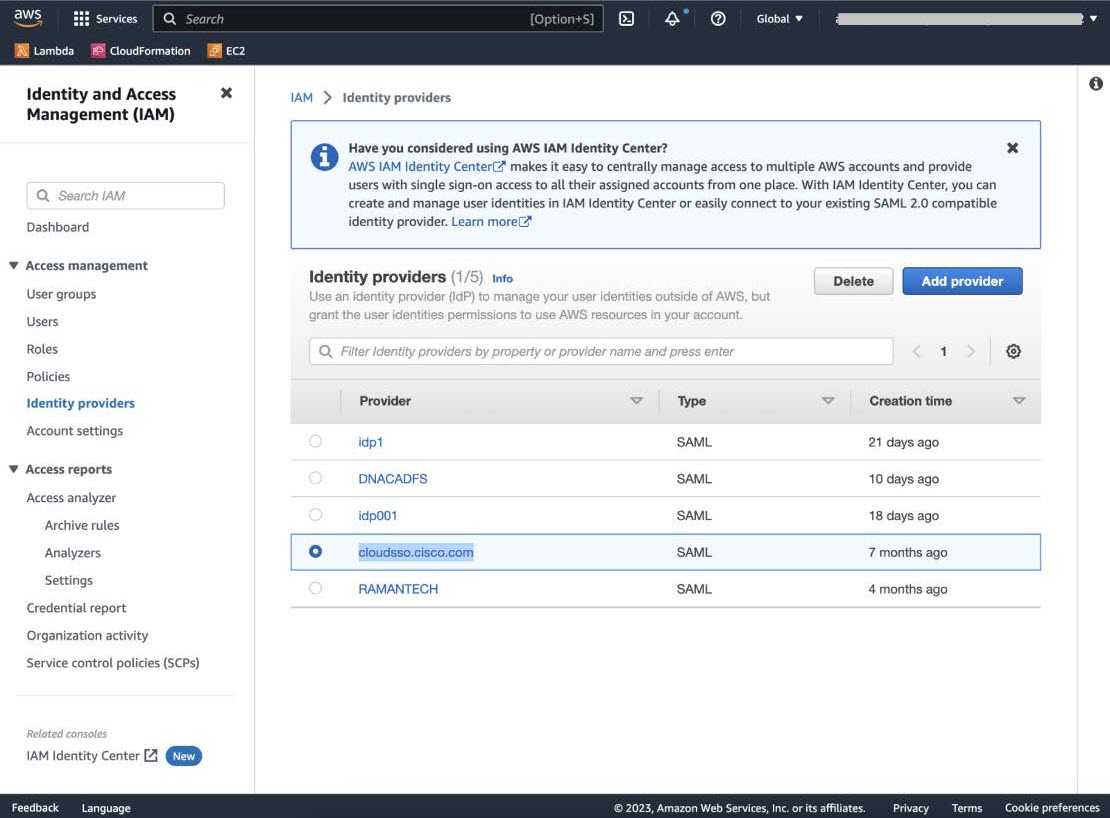
To access Cisco Global Launchpad through the Cisco DNA Portal, you must log in to the Cisco DNA Portal.
Procedure
|
Step 1 |
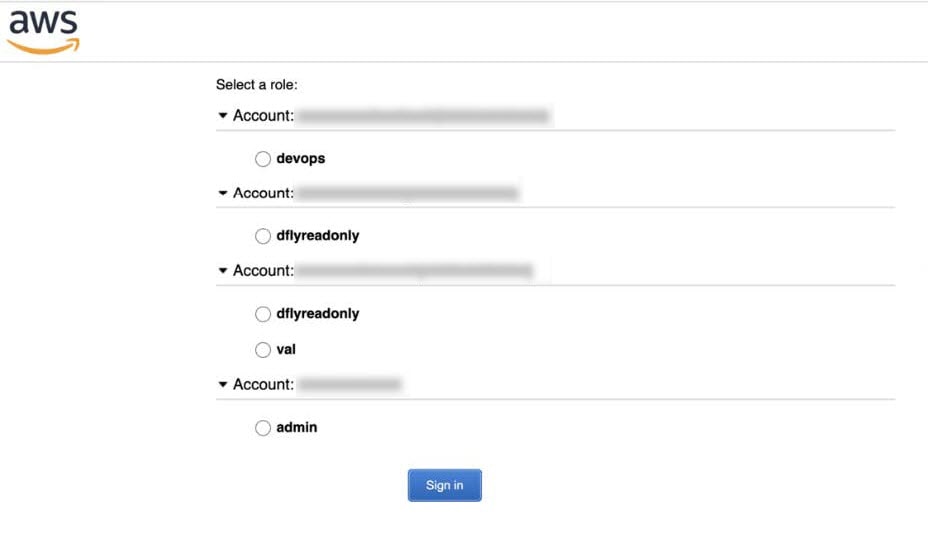
In your browser, enter: dna.cisco.com/valaunchpad The Cisco DNA Portal login window is displayed. |
|
Step 2 |
Perform one of these actions:
|
|
Step 3 |
Enter your Cisco account email in the Email field, and click Next. |
|
Step 4 |
Enter your Cisco account password in the Password field, and click Log in. The VA Launchpad page appears. |

 Feedback
Feedback