|
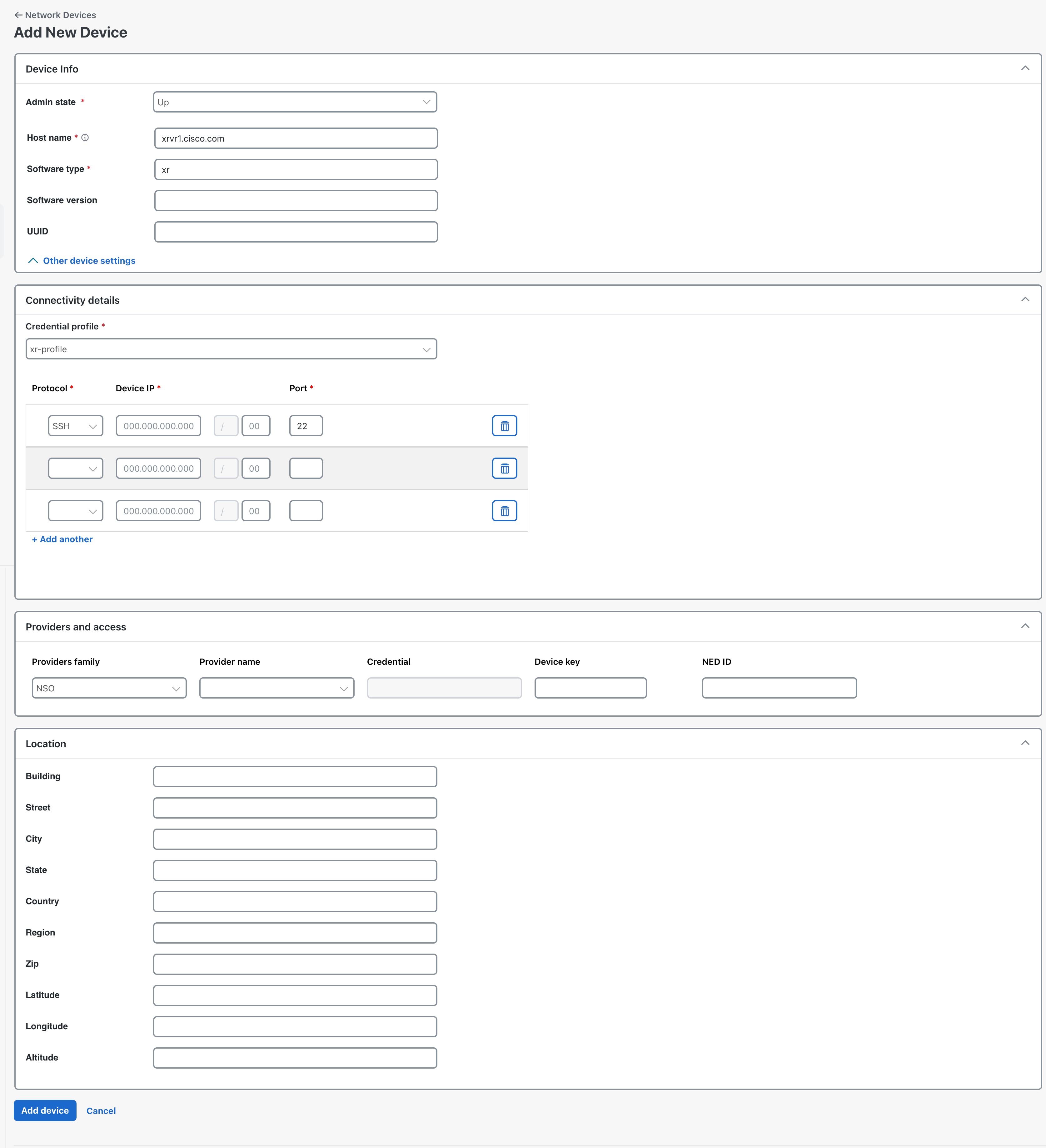
Device info
Provide basic device information.
|
|
Admin state *
|
The management state of the device. Options are:
|
|
Host name *
|
The hostname of the device.
|
|
Software type *
|
Enter the software type of the device (such as IOS-XE).
|
|
Software version
|
Software version of the operating system.
|
|
UUID
|
Universally unique identifier (UUID) for the device.
|
|
Connectivity details
Provide basic connectivity information.
|
|
Credential profile *
|
The name of the credential profile to be used to access the device for data collection and configuration changes. For example:
nso-51.
|
| Protocol * |
The connectivity protocols used by the device. Choices are: SSH, NETCONF, and HTTP.
To add more connectivity protocols for this device, click + Add another at the end of the last row in the Connectivity Details panel. To delete a protocol you have entered, click  shown next to that row in the panel. shown next to that row in the panel.
You can enter as many sets of connectivity details as you want, but only one set for each protocol. You must enter details
for at least SSH and HTTP.
|
| Device IP * |
Enter the device's IP address (IPv4 or IPv6) and subnet mask.
Please ensure that the subnets chosen for the IP networks (including devices and destinations) do not have overlapping address
space (subnets/supernets) as it may result in unpredictable connectivity issues.
|
| * Port |
The port used for this connectivity protocol. Each protocol is mapped to a port, so be sure to enter the port number that
corresponds to the protocol you chose. The standard port assignments for each protocol are:
-
SSH: 22
-
NETCONF: 830
-
HTTP: 80
|
| Timeout (sec) |
The elapsed time (in seconds) before communication attempts using this protocol will time out. The default value is 30 seconds.
For XE devices using NETCONF, the recommended minimum timeout value is 90 seconds. For all other devices and protocols, the
recommended minimum timeout value is 60 seconds.
|
|
Providers and access
Give information about the access provider.
|
|
Providers family
|
Provider type used for topology computation. Choose a provider from the list (the default is NSO and should be the only option).
|
|
Provider name
|
Provider name used for topology computation. Choose a provider from the list.
|
|
Credential
|
The credential profile used for the provider. This field is read-only and is autopopulated based on the provider you select.
|
|
Device key
|
The host name used for the provider.
|
|
NED ID
|
The ID of the Cisco NSO Network Element Driver (NED) used to manage the device. For example: cisco-iosxr-cli-7.61.
|
|
Location
Provide location information for the device.
|
|
Building
|
The name or number of the building where the device is located
|
|
Street
|
The street address where the device is located.
|
|
City
|
The name of the city where the device is located.
|
|
State
|
The name of the state, district or province where the device is located.
|
|
Country
|
The name of the nation or country where the device is located.
|
|
Region
|
Where applicable, the name of the geographical region where the device is located.
|
|
Zip
|
The zip or postal code of the device location.
|
|
Latitude
|
The geographical latitude of the device location, entered in Decimal Degrees (DD) format.
|
|
Longitude
|
The geographical longitude of the device location, entered in Decimal Degrees (DD) format.
|
|
Altitude
|
The altitude at which the device is located, in feet or meters. For example, 123m.
|


 Feedback
Feedback