Zero Touch Provisioning Concepts
The Cisco Crosswork Zero Touch Provisioning (ZTP) application allows you to ship factory-fresh devices to a branch office or remote location and provision them once physically installed. Local operators can cable these devices to the network without installing an image or configuring them. To use ZTP, you first establish an entry for each device in the DHCP server and in the ZTP application. You can then activate ZTP processing by connecting the device to the network and powering it on or reloading it. The device will download and apply a software image and configurations to the device automatically (you can also apply configurations only). Once configured, ZTP onboards the new device to the Cisco Crosswork device inventory. You can then use other Cisco Crosswork applications to monitor and manage the device.
Cisco Crosswork ZTP uses the following basic terms and concepts:
-
Classic ZTP: A process to download and apply software and configuration files to devices. It uses iPXE firmware and HTTP to boot the device and perform downloads. It's not suitable for use over public networks.
-
Secure ZTP: A secure process to download and apply software images and configuration files to devices. It uses secure transport protocols and certificates to verify devices and perform downloads.
-
PnP ZTP: A secure process to download and apply software images and configuration files to Cisco devices. It uses Cisco Plug and Play (Cisco PnP) to verify devices and perform downloads over a secure, encrypted channel.
-
Evaluation License Countdown: You can use ZTP to onboard devices without licenses for 90 days. After this evaluation period expires, you cannot use ZTP to onboard new devices until you purchase and install a license bundle with enough capacity to cover all prior devices onboarded using ZTP, as well as your projected future needs.
-
Image file: A binary software image file, used to install the network operating system on a device. For Cisco devices, these files are the supported versions of Cisco IOS images. Software image installation is an optional part of ZTP processing. When configured to do so, the ZTP process downloads the image from Cisco Crosswork to the device, and the device installs it. If you must also install SMUs, ZTP can install them as part of configuration processing in Classic and Secure ZTP (SMUs are not supported in PnP ZTP).
-
Cisco Plug and Play (Cisco PnP): Cisco's proprietary zero-touch provisioning solution, bundled in most IOS software images. Cisco PnP uses a software PnP agent and a PnP server to distribute images and configurations to devices. To ensure communications are secure, the server and agent communicate using HTTPS.
-
Configuration file: A file used to set the operating parameters of the newly imaged or re-imaged device. Depending on the ZTP mode you plan to use, the file may be a Python script, Linux shell script, or a sequence of Cisco IOS CLI commands stored as ASCII text (not all of these are supported in all ZTP modes). The ZTP process downloads the configuration file to the newly imaged device, which then executes it. ZTP processing requires configuration files. Secure ZTP also supports up to three different configuration files, which are applied during onboarding in the following order: pre-configuration, day-zero, and post-configuration.
-
Configuration handling method: A Secure ZTP user option. It allows you to specify whether you want to merge a new configuration into the existing device configuration or to overwrite it. It is only available when implementing Secure ZTP.
-
Credential profile: Collections of passwords and community strings that are used to access devices via SNMP, SSH, HTTP, and other network protocols. Cisco Crosswork uses credential profiles to access your devices, automating device access. All credential profiles store passwords and community strings in encrypted format.
-
Bootfile name: The explicit path to and name of a software image that is stored in the ZTP repository. For each device you plan to onboard using ZTP, specify the bootfile name as part of the device configuration in DHCP.
-
HTTPS/TLS: Hypertext Transport Protocol Secure (HTTPS) is a secure form of the HTTP protocol. It wraps an encrypted layer around HTTP. This layer is the Transport Layer Security (TLS) (formerly Secure Sockets Layer, or SSL).
-
iPXE: The open-source boot firmware iPXE is the popular implementation of the Preboot eXecution Environment (PXE) client firmware and boot loader. iPXE allows devices without built-in PXE support to boot from the network. The iPXE boot process is a normal part of Classic ZTP processing only.
-
Owner certificate: The CA-signed end-entity certificate for your organization, which binds a public key to your organization. You install owner certificates on your devices as part of Secure ZTP processing.
-
Ownership Voucher: Nonceless audit vouchers that verify that devices onboarded with ZTP are bootstrapping into a domain your organization owns. Cisco supplies OVs in response to requests from your organization.
-
Cisco PnP agent: A software agent embedded in Cisco IOS-XE devices. Whenever a device that supports PnP agent powers up for the first time without a startup configuration file, the agent tries to find a Cisco PnP server. The agent can use various means to discover the server's IP address, including DHCP and DNS.
-
Cisco PnP server: A central server for managing and distributing software images and configurations to Cisco PnP-enabled devices. Cisco Crosswork ZTP has an embedded PnP server, which is configured to communicate with PnP agents using HTTPS.
-
SUDI: The Secure Unique Device Identifier (SUDI) is a certificate with an associated key pair. The SUDI contains the device's product identifier and serial number. Cisco inserts the SUDI and key pair in the device hardware Trust Anchor module (TAm) during manufacturing, giving the device an immutable identity. During Secure ZTP processing, the back-end system challenges the device to validate its identity. The router responds using its SUDI-based identity. This exchange, and the TAm encryption services, permit the back-end system to provide encrypted image and configuration files. Only the validated router can open these encrypted files, ensuring confidentiality in transit over public networks.
-
SUDI Root CA Certificates: A root authority certificate for SUDIs, issued and signed by a Certificate Authority (CA), used to authenticate subordinate SUDI certificates.
-
UUID: The Universal Unique Identifier (UUID) uniquely identifies an image file that you have uploaded to Cisco Crosswork. You use the UUID of the software image file in the DHCP bootfile URL with Classic and Secure ZTP.
-
ZTP asset: ZTP requires access to several types of files and information in order to onboard new devices. We refer to these files and information collectively as "ZTP assets." You load these assets as part of ZTP setup, before initiating ZTP processing.
-
ZTP profile: A Cisco Crosswork storage construct that combines (normally) one image and one configuration into a single unit. Cisco Crosswork uses ZTP profiles to automate imaging and configuration processes. Using ZTP profiles is optional, but we recommended them. They are an easy way to organize ZTP images and configurations around device families, classes, and roles, and help maintain consistent ZTP use.
-
ZTP repository: The location where Cisco Crosswork stores image and configuration files.
Platform Support for ZTP
This topic details Cisco Crosswork Zero Touch Provisioning support for Cisco and third-party software and devices.
Platform Support for Classic ZTP
The following platforms support Classic ZTP:
-
Software: Cisco IOS-XR versions 6.6.3, 7.0.1, 7.0.2, 7.0.12, and 7.3.1 or later.
-
Hardware:
-
Cisco Network Convergence Systems (NCS) 540 Series Routers
-
Cisco NCS 1000-1004 Series Routers
-
Cisco NCS 5500 Series Routers
-
Cisco NCS 8000 and 8800 Series Routers (Spitfire fixed mode)
-
Classic ZTP doesn't support third-party devices or software.
Platform Support for Secure ZTP
The following platforms support Secure ZTP:
-
Software: Cisco IOS-XR version 7.3.1 or later, with the exception of releases 7.3.2 and 7.4.1, which are not supported in this release.
You can upgrade from IOS-XR 6.6.3 to 7.3.1 as a single image installation.
-
Hardware:
-
Cisco Network Convergence Systems (NCS) 540 Series
-
Cisco NCS 1000-1004 Series
-
Cisco NCS 5500 Series
-
Cisco NCS 8000 and 8800 Series (Spitfire fixed mode)
-
Secure ZTP supports provisioning for third-party devices only if the third-party devices:
-
Are 100-percent compliant with the Secure ZTP RFC 8572(https://tools.ietf.org/html/rfc8572).
-
Match Cisco format guidelines for serial numbers in device certificates and ownership vouchers. For details, see the section Secure ZTP: Guidelines for Third-Party Device Certificates and Ownership Vouchers.
Platform Support for PnP ZTP
The following platforms support PnP ZTP:
-
Software: Cisco IOS-XE version 16.12 and 17.4.1.
Version 16.12.5 is the recommended version for customers.
-
Hardware:
-
Cisco Network Convergence Systems (NCS) 520 Series Routers
-
Cisco Aggregation Services Router (ASR) 903
-
Cisco ASR 907
-
Cisco ASR 920
-
PnP ZTP doesn't support third-party devices or software.
If you plan on using PnP ZTP, check that the minimum license boot-level on each IOS-XE device is set to metroipaccess or advancedmetroipaccess
before you trigger ZTP processing. If the boot level has been set properly, the output of the IOS-XE #sh run | sec license CLI command on the device should contain statements showing either of these two license levels: license boot level advancedmetroipaccess or license boot level metroipaccess. If the command output shows any other license level, especially one lower than these two, the Cisco PnP cryptographic functionality
will not be enabled. This will cause certificate installation to fail, which will then cause PnP ZTP device provisioning to
fail.
Secure ZTP: Guidelines for Third-Party Device Certificates and Ownership Vouchers
Secure ZTP processing for any device starts with a successful HTTPS/TLS handshake between the device and Cisco Crosswork. After the handshake, Secure ZTP must extract a serial number from the device certificate. Secure ZTP then validates the extracted serial number against its internal "allowed" list of serial numbers. You create the allowed list by uploading device serial numbers to Cisco Crosswork. A similar serial-number validation step occurs later, when validating downloads using ownership vouchers.
Unlike Cisco IOS-XR devices, the format of the serial number in third-party vendors' device certificates is not standardized
across vendors. Typically, a third-party vendor's device certificate has a Subject field or section. The Subject contains multiple key-value pairs that the vendor decides upon. One of the key-values pairs is usually a serialNumber key. This key's value contains the actual device serial number as a string, which is preceded by the string SN:. For example: Let's suppose that the third-party device certificate's Subject section contains the following key and value: serialNumber = PID:NCS-5501 SN:FOC2331R0CW. Secure ZTP will take the value after the SN: string and match that to one of the serial numbers in the allowed list.
If the third-party vendor's device certificate has a different format, validation failures can occur. The degree of failure
depends on the degree of difference. The vendor certificate may not match this format at all. The certificate's Subject field may not contain a serialNumber key with a value that contains the SN: string. In this case, Secure ZTP processing falls back to using the whole string value of the serialNumber key (if present) as the device serial number. It will then try to match that value to one in the allowed list of serial numbers.
These two methods – string matching and the fallback – are the only means Secure ZTP has for determining the third-party device's
serial number. If the vendor certificate differs from this expectation sufficiently, Secure ZTP may be unable to validate
the device at all.
Secure ZTP has similar format expectations for ownership vouchers. Cisco tools generate ownership vouchers with filenames
in the format SerialNumber.vcj, where SerialNumber is the device's serial number. Secure ZTP extracts the serial number from the filename and then attempts to match it to one
in the allowed list. For multivendor support, we assume that third-party vendor tools generate OV files with file names in
the same format. If this expectation isn't met, validation failures are likely.
ZTP Implementation Decisions
As a best practice, always choose the most secure implementation for the devices you have. That said, ZTP offers a range of implementation choices and cost vs. benefit tradeoffs worth considering in advance:
-
When to Use Classic ZTP: Classic ZTP is easier to implement than Secure ZTP. It needs no PDC, owner certificates, or ownership vouchers. It’s less subject to processing errors, as device and server verification is less stringent and setup is less complex. It’s your only choice if your Cisco devices run IOS-XR versions earlier than 7.3.1, as Secure and PnP ZTP don't support them. Although Classic ZTP now includes a device serial-number check, it remains insecure at the transport layer. It's not recommended if routes to your remote devices cross a metro or otherwise unsecured network.
-
When to Use Secure ZTP: Use Secure ZTP when you must traverse public networks and you have devices that support Secure ZTP. The additional security that it provides requires a more complex setup than Classic ZTP. This complexity can make processing error-prone if you’re new to the setup tasks. Secure ZTP setup also requires a certificates and ownership vouchers from the device manufacturer. Use it if your devices are from third-party manufacturers, as Classic ZTP doesn't support third-party hardware. Third-party devices and their software must be 100-percent compliant with RFCs 8572 and 8366. Device certificates for third-party devices must contain the device serial number. Third-party ownership vouchers must be in a format that uses the device serial number as the filename. Cisco can’t guarantee Secure ZTP compatibility with all third-party devices. For more details on third-party device support, see Platform Support for ZTP.
-
When to Use PnP ZTP: Use PnP ZTP when you want a secure provisioning setup for Cisco IOS-XE devices that support the Cisco PnP protocol. Less complicated to set up than Secure ZTP, but only slightly more complicated than Classic ZTP, it's your best choice when your network devices happen to meet these base requirements.
-
Use ZTP With Imaged Devices: There’s no need to specify a software image when you use any of the ZTP modes. This feature allows you the option of shipping to your remote location one or more devices on which you have already installed a software image. You can then connect to these devices and trigger ZTP processing remotely. Depending on how you set up things, you can apply:
-
A configuration only
-
One or more images or SMUs, with more configurations.
Secure ZTP offers more flexibility with pre-imaged devices because it offers pre-configuration, day-zero, and post-configuration script execution capability. While both Classic and Secure ZTP modes can chain configuration files, Classic ZTP's ability to execute additional scripts will be limited to the support for script execution allowed on specific devices. PnP ZTP can only execute CLI commands, which doesn't allow for script execution.
In all cases, the result is to onboard the device. Once onboarded to Cisco Crosswork, you will want to avoid using ZTP to configure the device again (see Reconfigure Onboarded ZTP Devicesfor details).
-
-
Organize Configurations: Keep your configurations as consistent as possible across devices. Consistency makes solving problems easier. It minimizes the amount of extra configuration you must perform to bring new devices online. It also reduces the number of "special" things to keep in mind when it comes time to reconfigure or upgrade your devices. Start by ensuring that all devices from the same device family and with similar roles have the same or similar basic configurations.
How you define the role that a device plays depends on your organization, its operational practices, and the complexity of your network environment. For example: Suppose that your organization is a financial services enterprise. It has three types of branches: Sidewalk ATMs, retail branches open during standard business hours, and private trading offices. You could define three sets of basic profiles covering all the devices at each type of branch. You can map your configuration files to each of these profiles.
Another method of enforcing consistency is to develop basic script configurations for similar types of devices, then use the script logic to call, or chain, other scripts for devices with special roles. If you’re using Classic ZTP, the script is in the specified configuration file. To extend our example, that script would apply a common configuration, then download and apply other scripts depending on the branch type. If using Secure ZTP, you have even more flexibility, as you can specify pre-configuration and post-configuration scripts in addition to the day-zero configuration script.
ZTP Processing Logic
Cisco Crosswork ZTP processing differs depending on whether you choose to implement Classic ZTP, Secure ZTP, or PnP ZTP.
The following illustrations and text provide details on each step of ZTP processing for each ZTP mode.
Once initiated by a device reset or reload, the ZTP process proceeds automatically. Crosswork also updates the Zero Touch Devices window with status messages showing the state each device reaches as it is processed. The three figures indicate each of these state transitions with blocks in shades of green on the left side of each diagram (the Onboarded is not shown, as reaching the Onboarding state only happens at the end of ZTP processing).
As indicated in the figures, the configuration scripts you use with ZTP must report device state changes to Cisco Crosswork using Cisco Crosswork API calls. If your configurations fail to do this, Crosswork can't register state changes when they occur, resulting in failed ZTP provisioning and onboarding. To see examples of these calls, select , then click Download Sample Script.
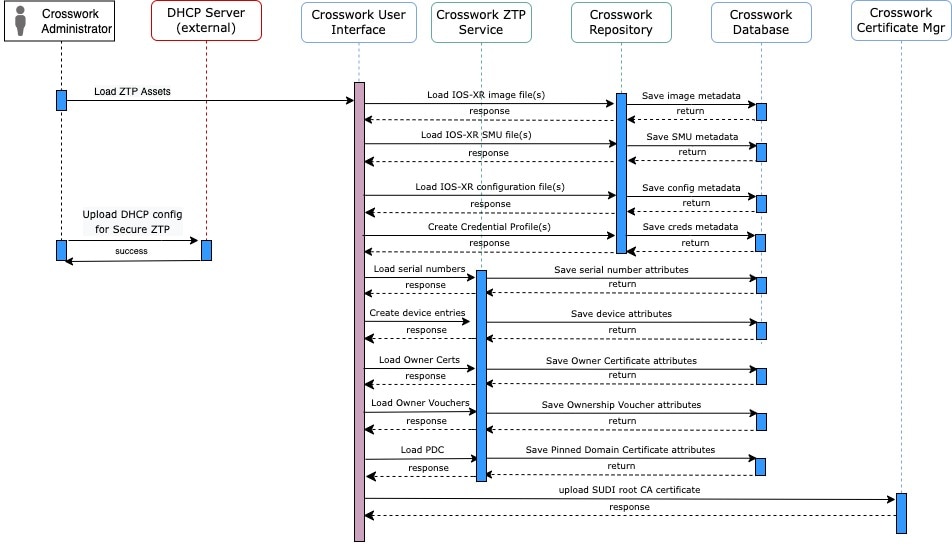
Classic ZTP Processing
The following illustration shows the process logic that Classic ZTP uses to provision and onboard devices.
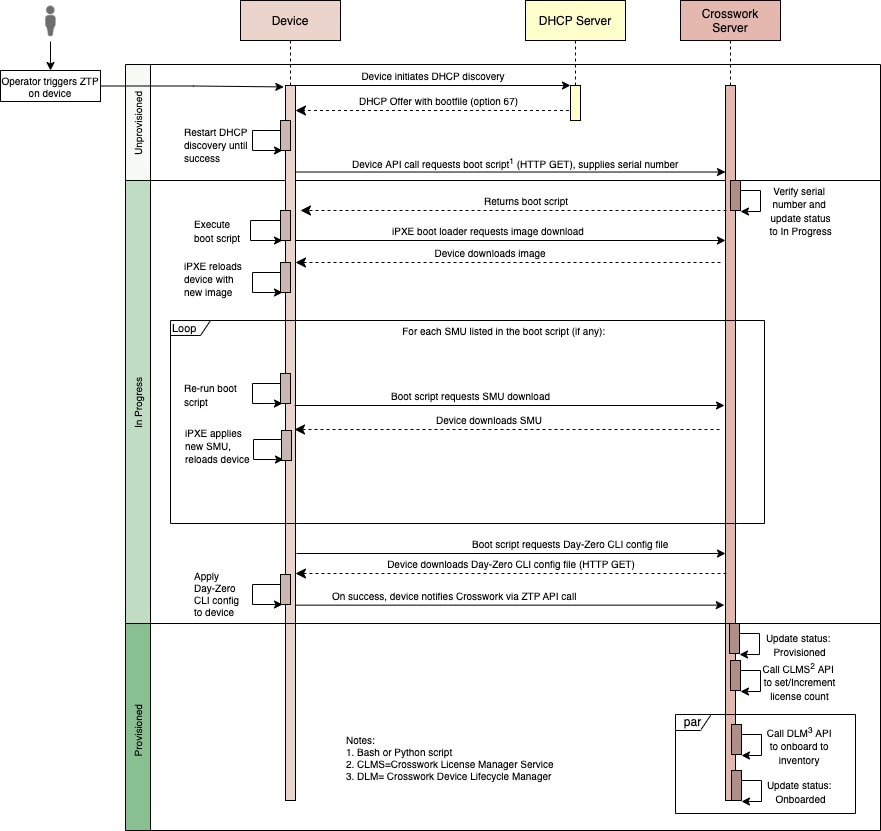
The DHCP server verifies the device identity based on the device serial number, then offers downloads of the boot file and image. Once ZTP images the device, the device downloads the configuration file and executes it.
Secure ZTP Processing
The following illustration shows the process logic that Secure ZTP uses to provision and onboard devices.
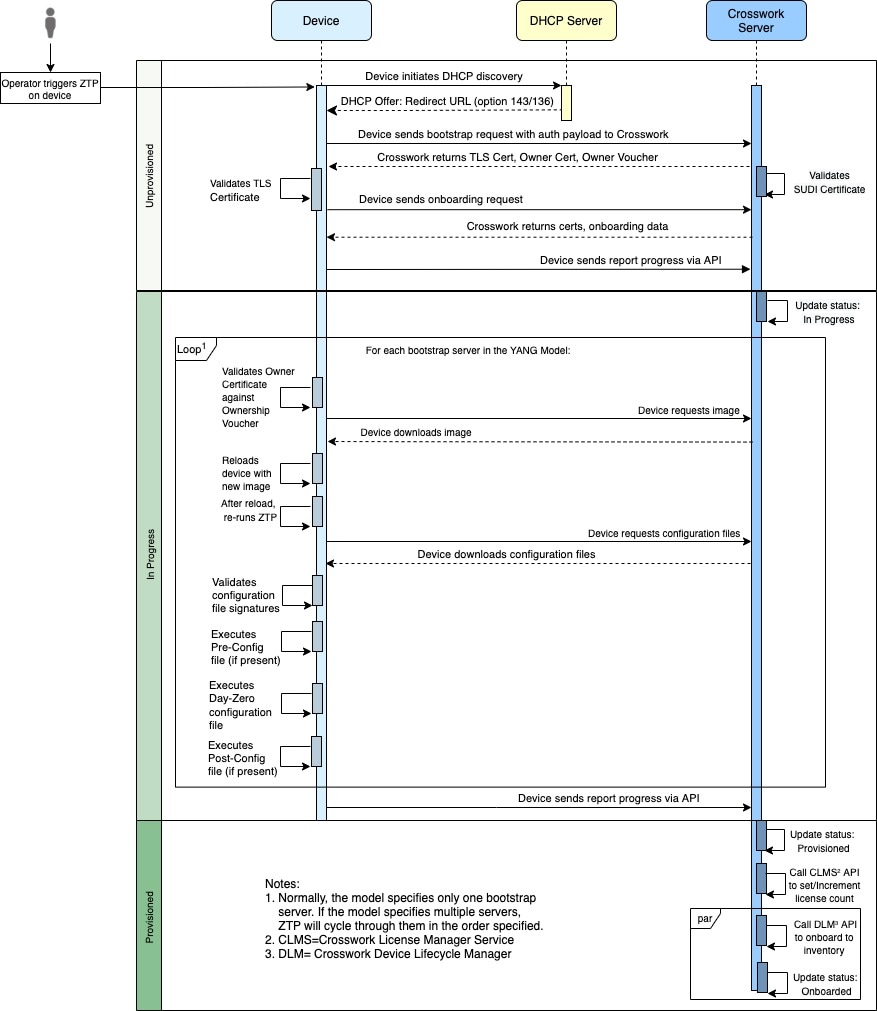
The device and the ZTP bootstrap server authenticate each other using the Secure Unique Device Identifier (SUDI) on the device and server certificates over TLS/HTTPS. Over a secure HTTPS channel, the bootstrap server lets the device download signed image and configuration artifacts. These artifacts must adhere to the RFC 8572 YANG schema. Once the device installs the new image (if any) and reloads, the device downloads configuration scripts and executes them.
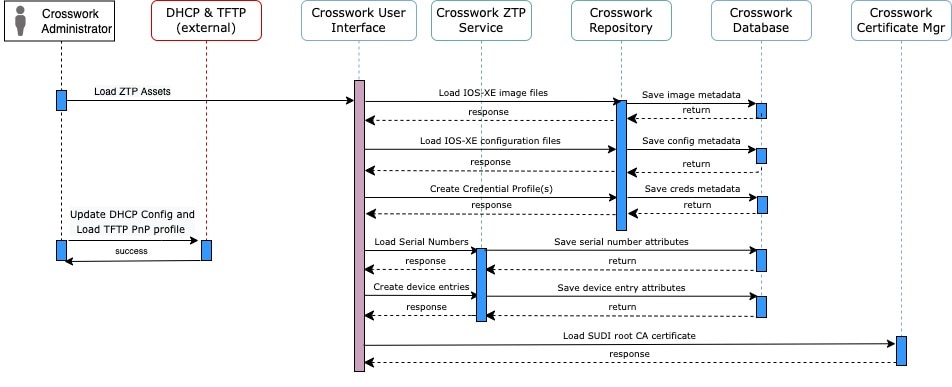
PnP ZTP Processing
The following illustration shows the process logic that PnP ZTP uses to provision and onboard devices.
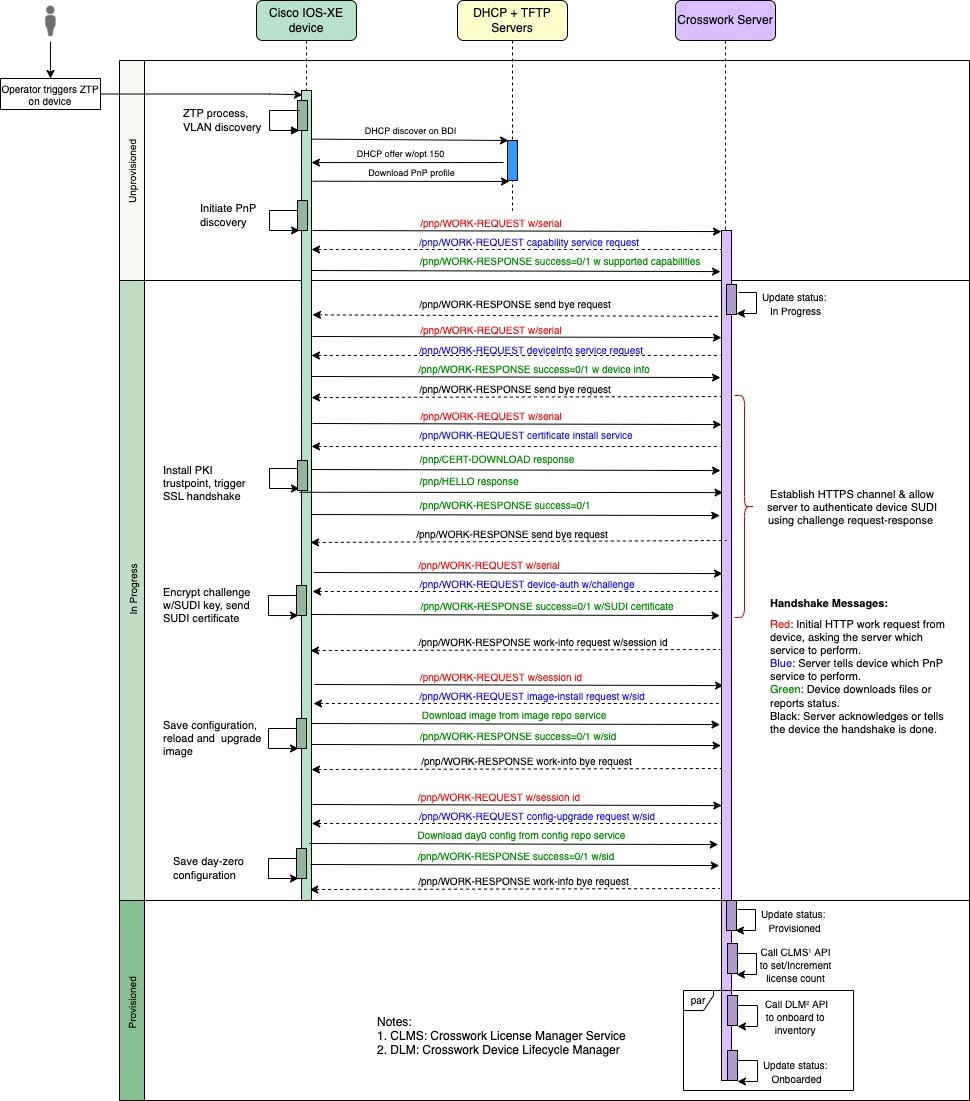
Once an operator triggers PnP ZTP processing, the device performs VLAN discovery and creates a BDI interface, on which DHCP discovery is initiated. As part of the DHCP discovery, the device also fetches the external TFTP server IP address using the DHCP Option 150 configuration. The device downloads the PnP Profile from the TFTP server without authentication and copies it to the device's running configuration. The PnP Profile is a CLI text file. The profile activates the device's PnP agent and sends work requests to the embedded Crosswork PnP server over HTTP on port 30620. The PnP server then validates the device's serial number against Crosswork's "allowed" list of serial numbers (previously uploaded to Crosswork) and then initiates a PnP capability service request. A successful PnP work response from the device changes the device provisioning status from Unprovisioned to In Progress. Thereafter, the PnP server initiates a series of service requests, including requests for device information, certificate installation, image installation, configuration upgrade, and so on. Each of these service requests involves a four-way handshake between the PnP server and PnP agent. As part of certificate-install request, Crosswork PnP server shares its certificate with the device. Successful installation of this trustpoint on the device changes the PnP profile configuration to start using HTTPS and port 30603 on Crosswork. Subsequent image and config download requests use HTTPS to secure transactions. There is currently no SUDI certificate authentication support on the device. Once the device downloads and installs a new image (if any) and reloads, the PnP process will continue to download CLI configuration files and apply them to device running configuration. The device status is then set to Provisioned and the;license count is updated in Crosswork. The device status is then set to Onboarded, and the device stops communicating with the PnP server.
ZTP and Evaluation Licenses
All Cisco Crosswork applications can be used for 90 days without a license. Any time users log into the system, Crosswork displays a banner showing the number of days left in the trial period. When the trial expires, the banner will indicate it. At that point, no more devices will be able to complete the ZTP onboarding process. ZTP licensing follows a consumption-based model with licenses sold in blocks. In order to regain the ability to onboard devices using ZTP, you must install a license block that covers both the number of devices you onboarded during the trial period as well as the new devices you expect to onboard with ZTP in the future. For example: If you onboard 10 devices during the trial and then install a license bundle for 10 devices on day 91, you have no licenses left to use, and must install at least one more license block before onboarding another device. You can add more license blocks as needed. Operators should monitor license consumption to avoid running out of licenses unexpectedly. To see how many licenses you have used and are still available, check the Cisco Smart Licensing Site.
Your onboarded ZTP devices are always associated with either:
-
A serial number, or
-
The values of the Option 82 location ID attributes (remote ID and circuit ID).
Serial numbers and location IDs form an "allowed" list. ZTP uses this list when deciding to onboard a device and assign it a license. If you delete an onboarded ZTP device from inventory, and then onboard it again later, use the same serial number or location ID. If you use a different serial number or location ID, you may consume an extra license. The current release provides no workaround for this scenario. In any case, you can't have two different ZTP devices with the same serial number or location ID active at the same time.
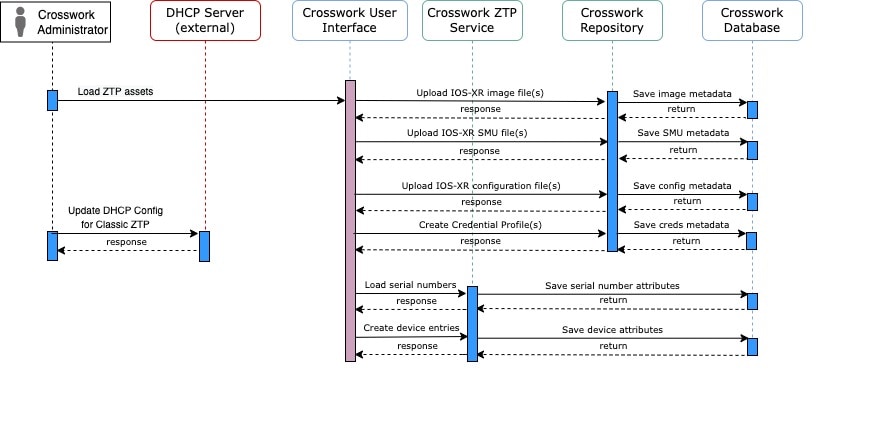
 next to
next to  in the
in the 
 Feedback
Feedback