Overview of Cisco Crosswork Data Gateway
Cisco Crosswork Data Gateway is a secure, common collection platform for gathering network data from multi-vendor devices. It is an on-premise application deployed close to network devices and supports multiple data collection protocols including MDT, SNMP, CLI, gNMI, Syslog and NETCONF. The number of Crosswork Data Gateways you need depends on the number of devices supported, the amount of data being processed, the frequency at which it is collected and your network architecture.
When Crosswork Data Gateway is deployed with Cisco Crosswork Infrastructure (also referred to as Cisco Crosswork in this guide), Cisco Crosswork acts as the controller application.
Crosswork Data Gateway uses the following concepts:
-
Crosswork Data Gateway VM - Crosswork Data Gateway VM that you install.
- Crosswork Data Gateway Profile -
Cisco Crosswork Data Gateway supports the following profiles for On-Premise deployment. For information on VM requirements for each profile, see Section: Crosswork Data Gateway Requirements in the Cisco Crosswork Infrastructure 4.1 and Applications Installation Guide.
-
Standard - for use with all Crosswork applications, except Crosswork Health Insights, and Crosswork Service Health (Automated Assurance).
-
Standard Plus - for use with Cisco Evolved Programmable Network Manager.

Note
VMs for this profile are installed using the On-Premise Standard with Extra Resources.
-
Extended - for use with Crosswork Health Insights and Crosswork Service Health (Automated Assurance).
-
-
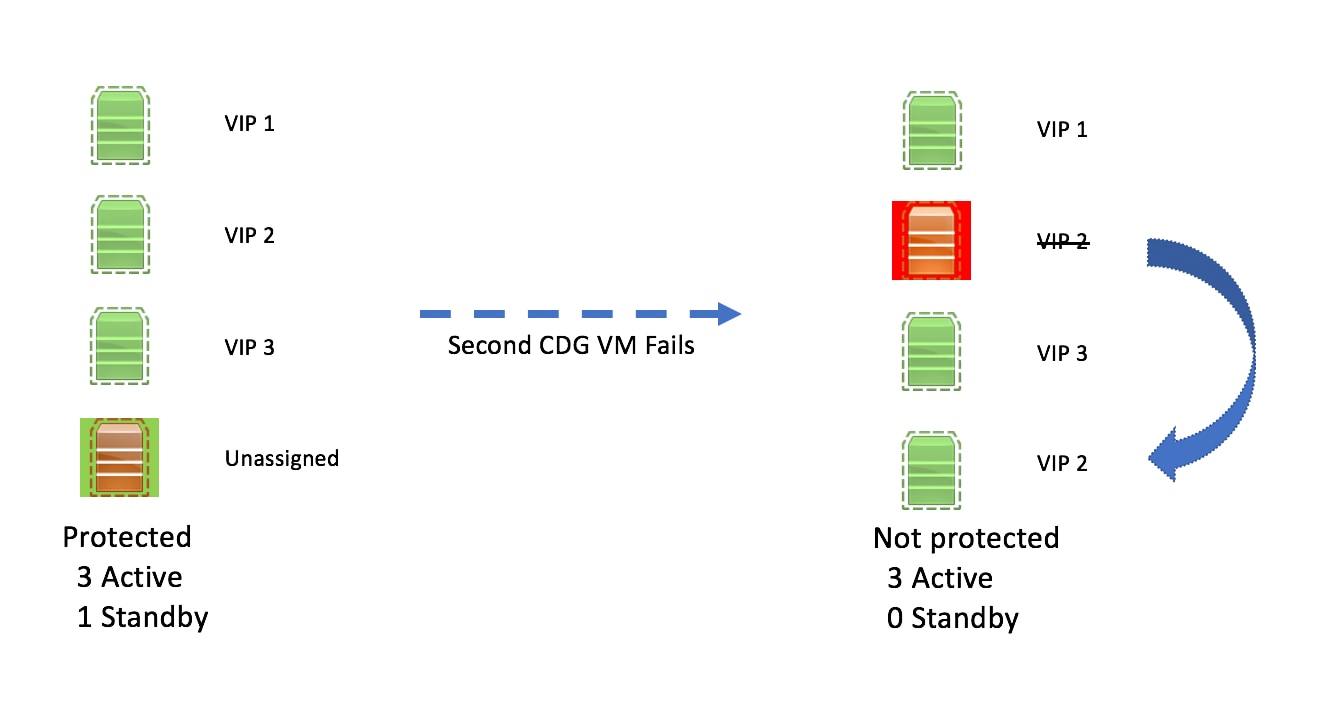
Crosswork Data Gateway Pool - A logical unit of one or more Crosswork Data Gateway VMs with an option to enable high availability. When a Crosswork Data Gateway VM goes down, Cisco Crosswork automatically replaces the VM with a spare VM from the pool to ensure that devices are managed and data collections have minimal disruption.
-
Crosswork Data Gateway- A Crosswork Data Gateway VM that is assigned a virtual IP address when it is added to a Crosswork Data Gateway pool. Operations such as attaching or detaching devices, creating collection jobs happen on the Crosswork Data Gateway.
-
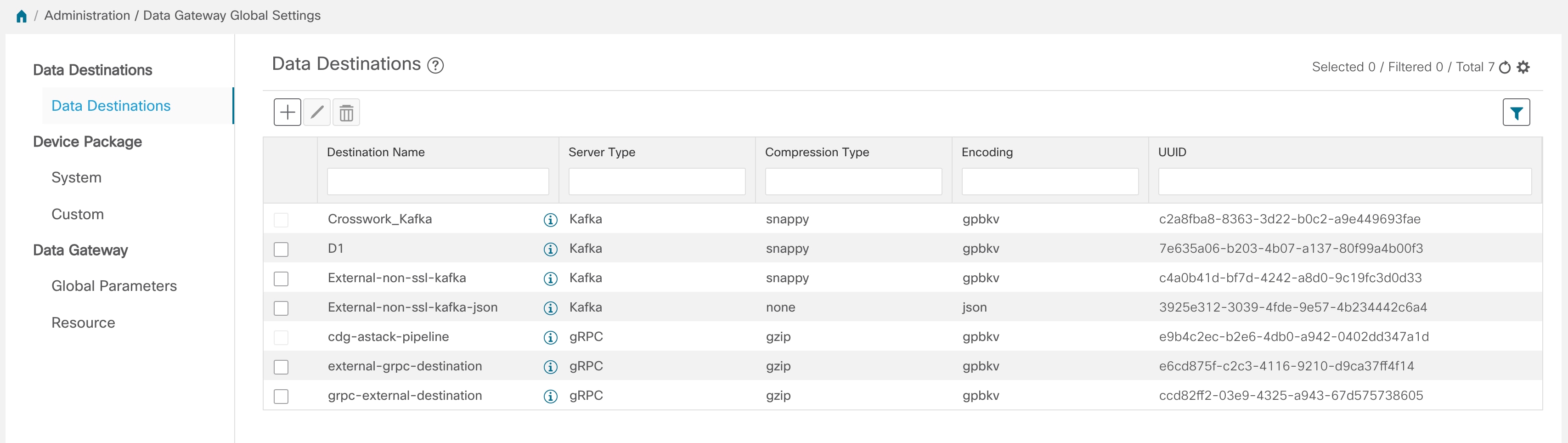
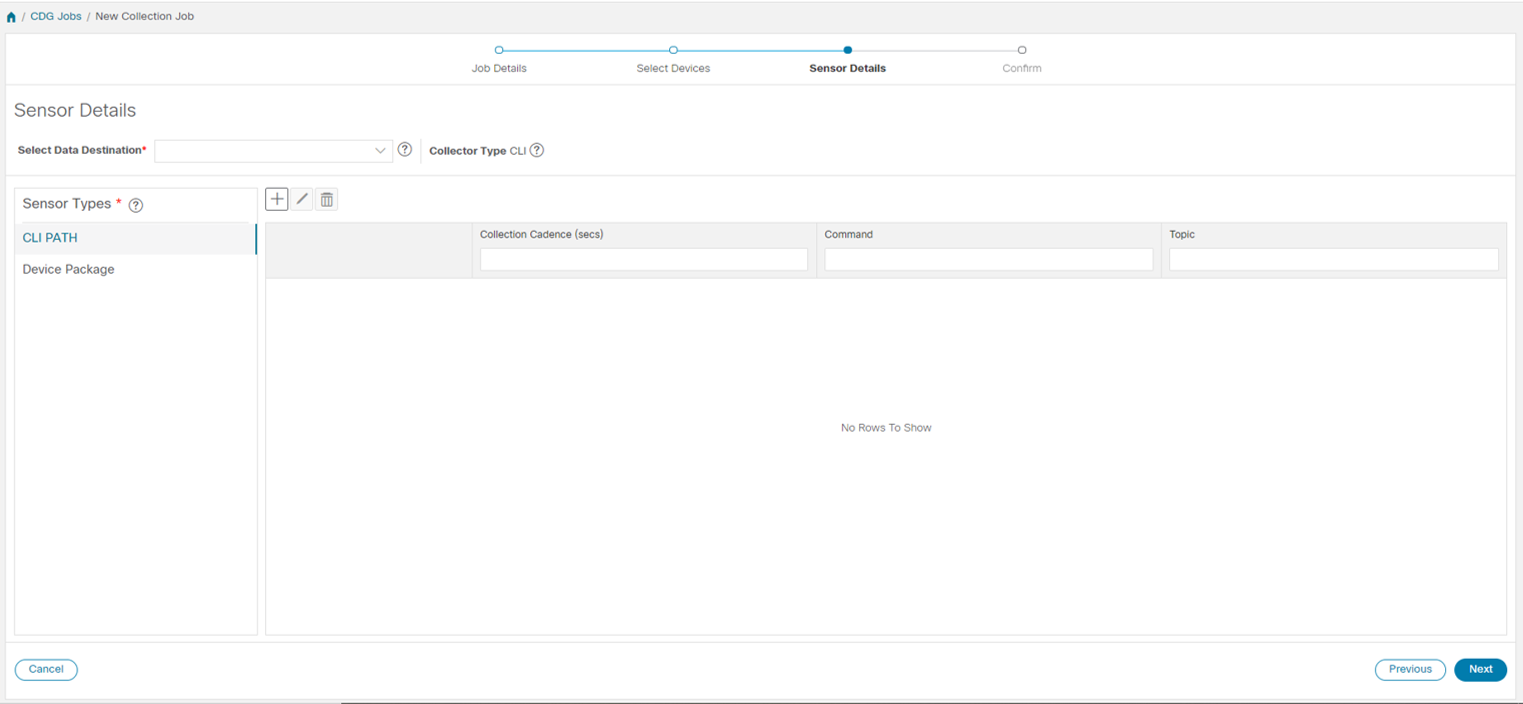
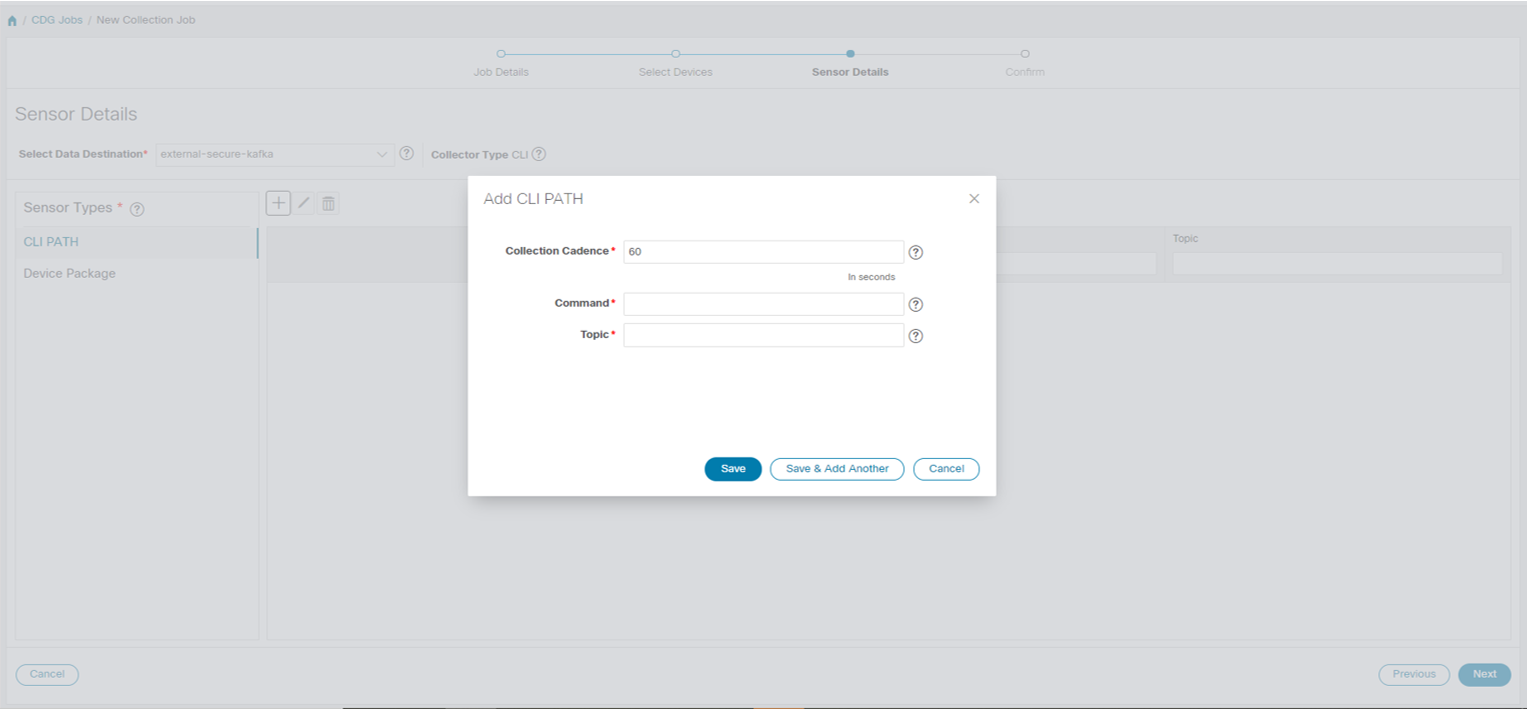
Data Destination - Internal or external recipients of data collected by the Crosswork Data Gateway. By default, Cisco Crosswork is defined as a data destination. Other destinations (external users) can be defined using the Cisco Crosswork UI or APIs.
-
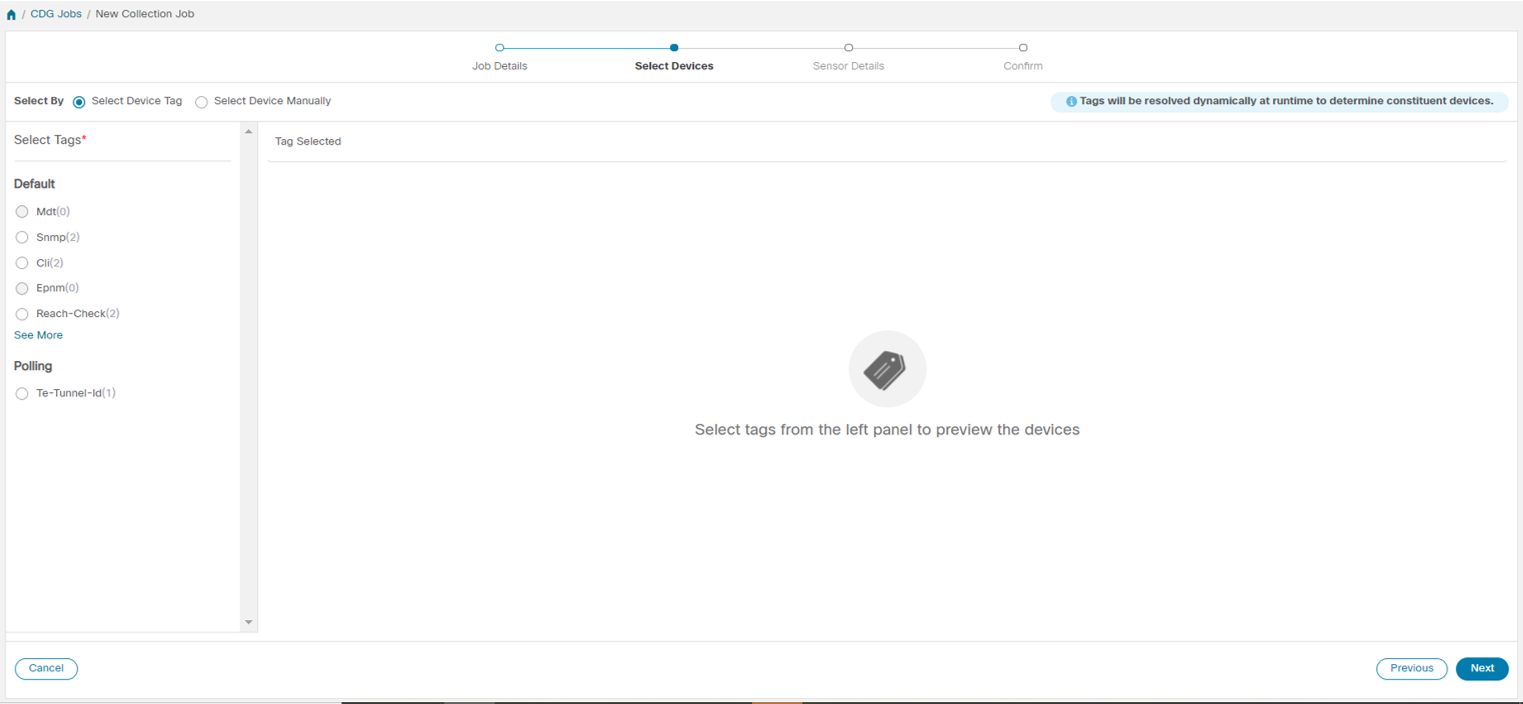
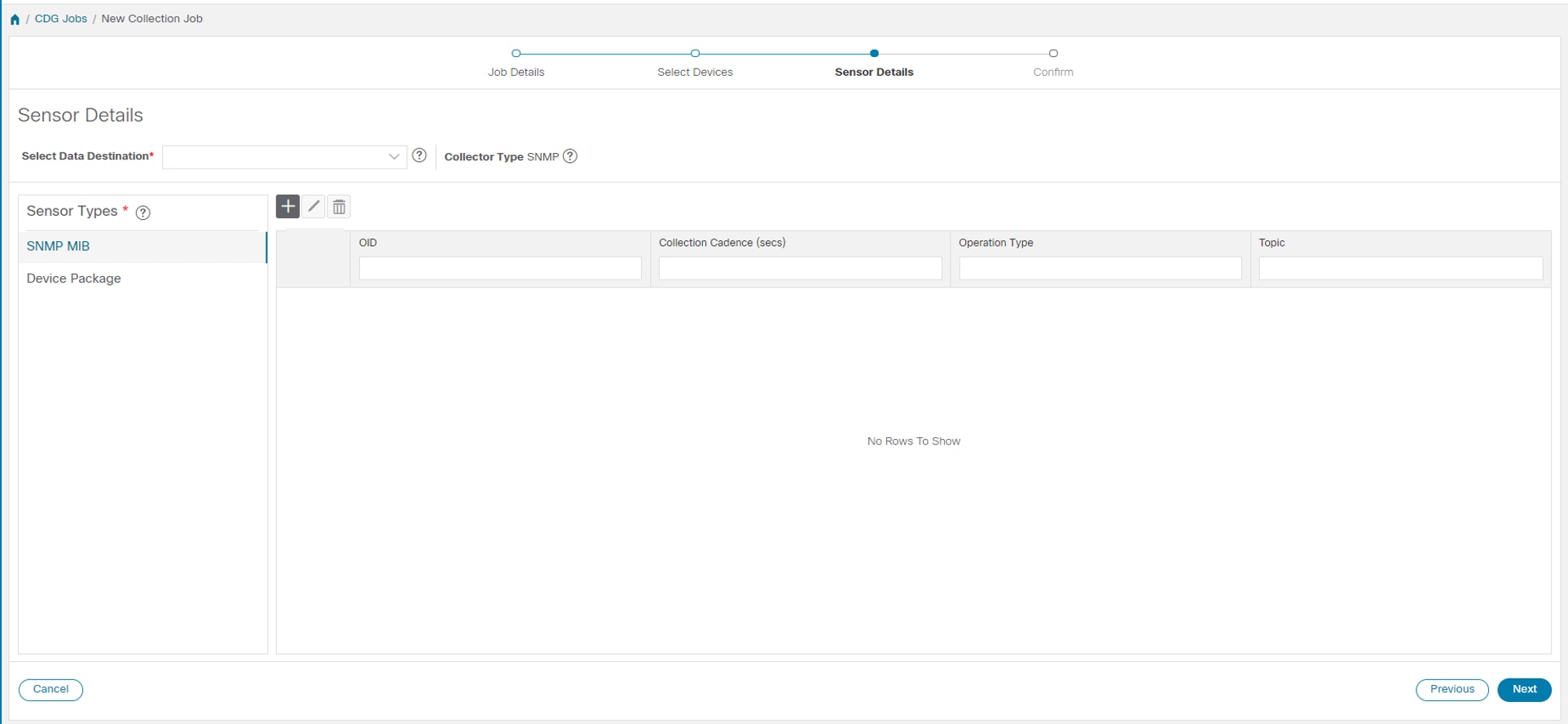
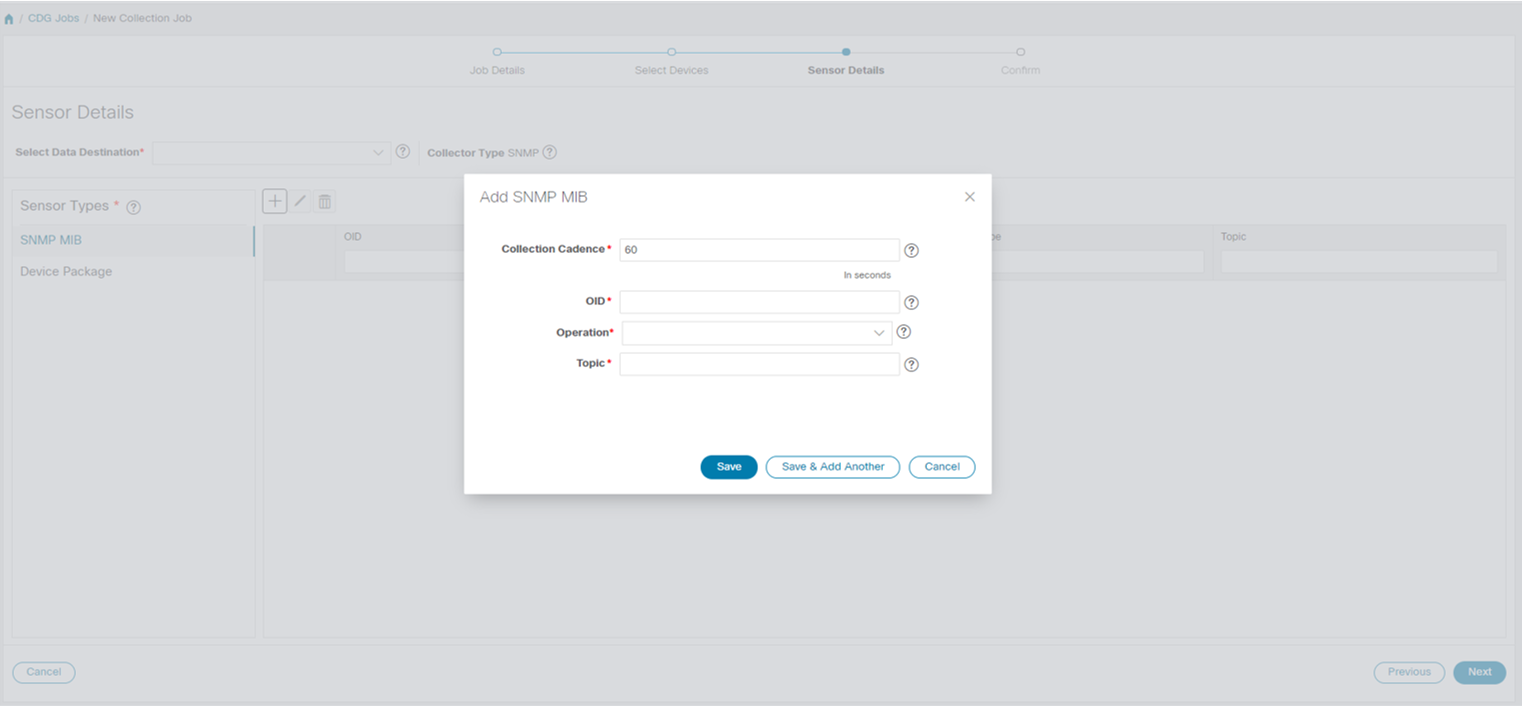
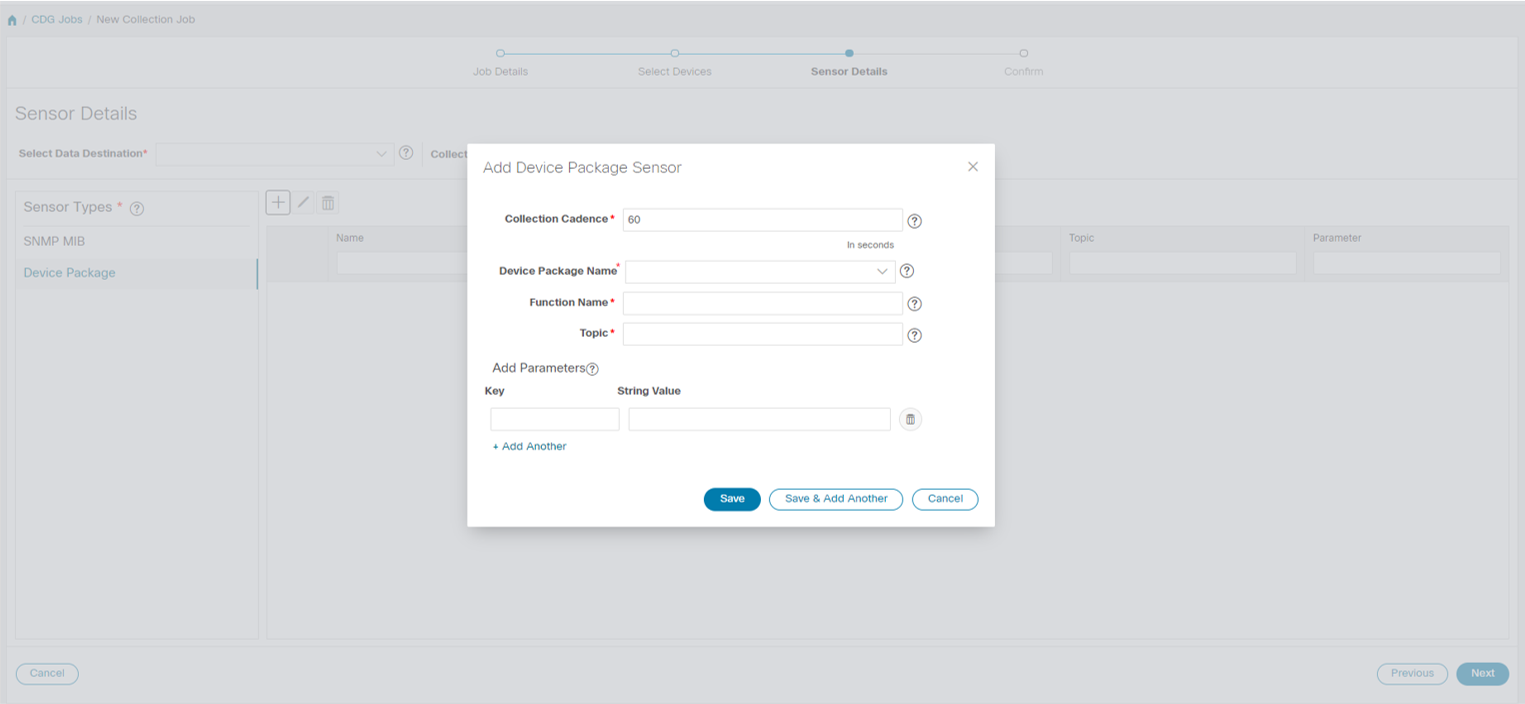
Collection Job - A task that Crosswork Data Gateway has to complete to collect data. Crosswork applications create collection jobs to check device reachability, collect telemetry data needed to determine network and service health. The Cisco Crosswork UI and API allow you to configure collection jobs for non-Crosswork applications.
-
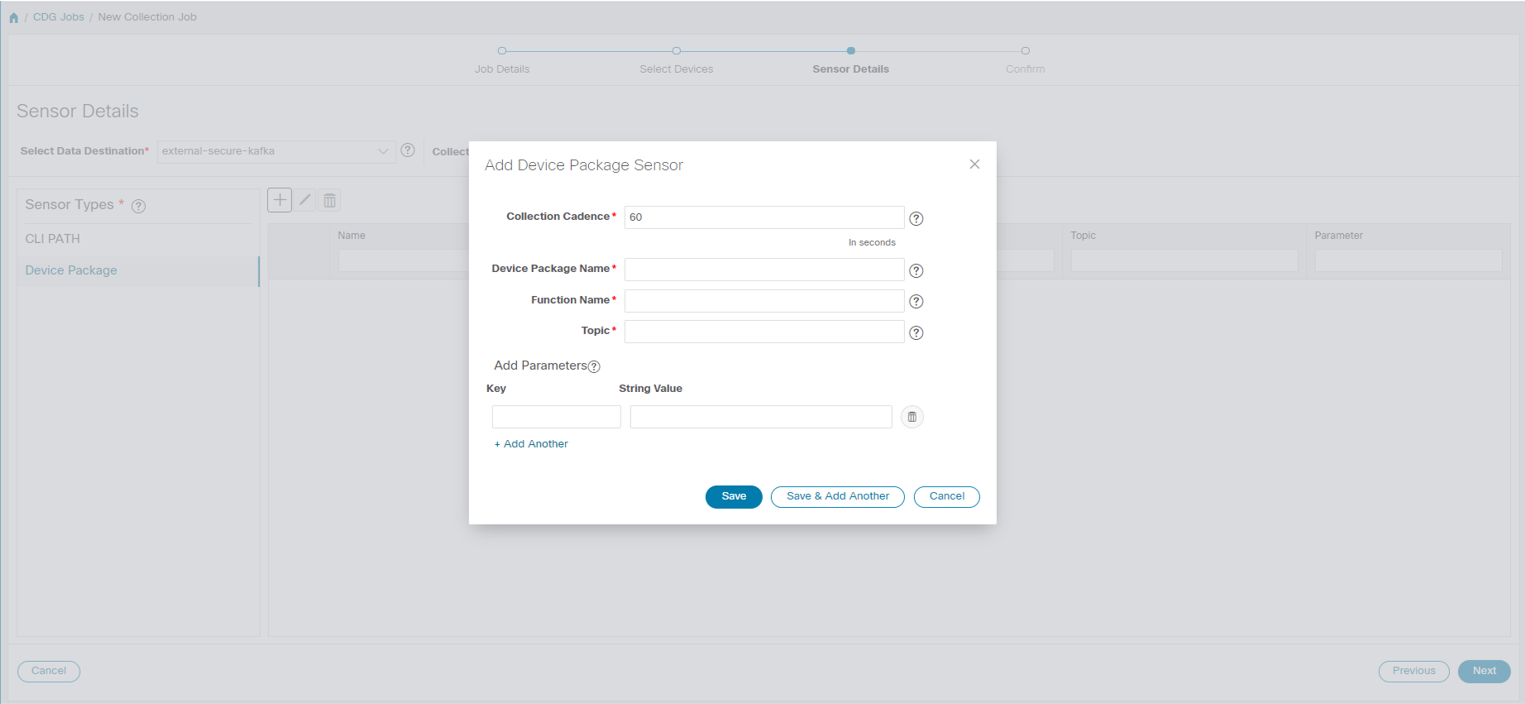
Custom Software Packages - Files and device model definitions to extend device coverage and support data collection from currently unsupported devices.
 Note |
This chapter explains only the Cisco Crosswork Data Gateway features that can be accessed via Cisco Crosswork UI. For more information about Cisco Crosswork Data Gateway Base VM and how to manage it, see Appendix A: Configure Crosswork Data Gateway VM. |
Crosswork Data Gateway UI Overview
To open the Cisco Crosswork Data Gateway management view, log in to Cisco Crosswork and choose from the left navigation bar.
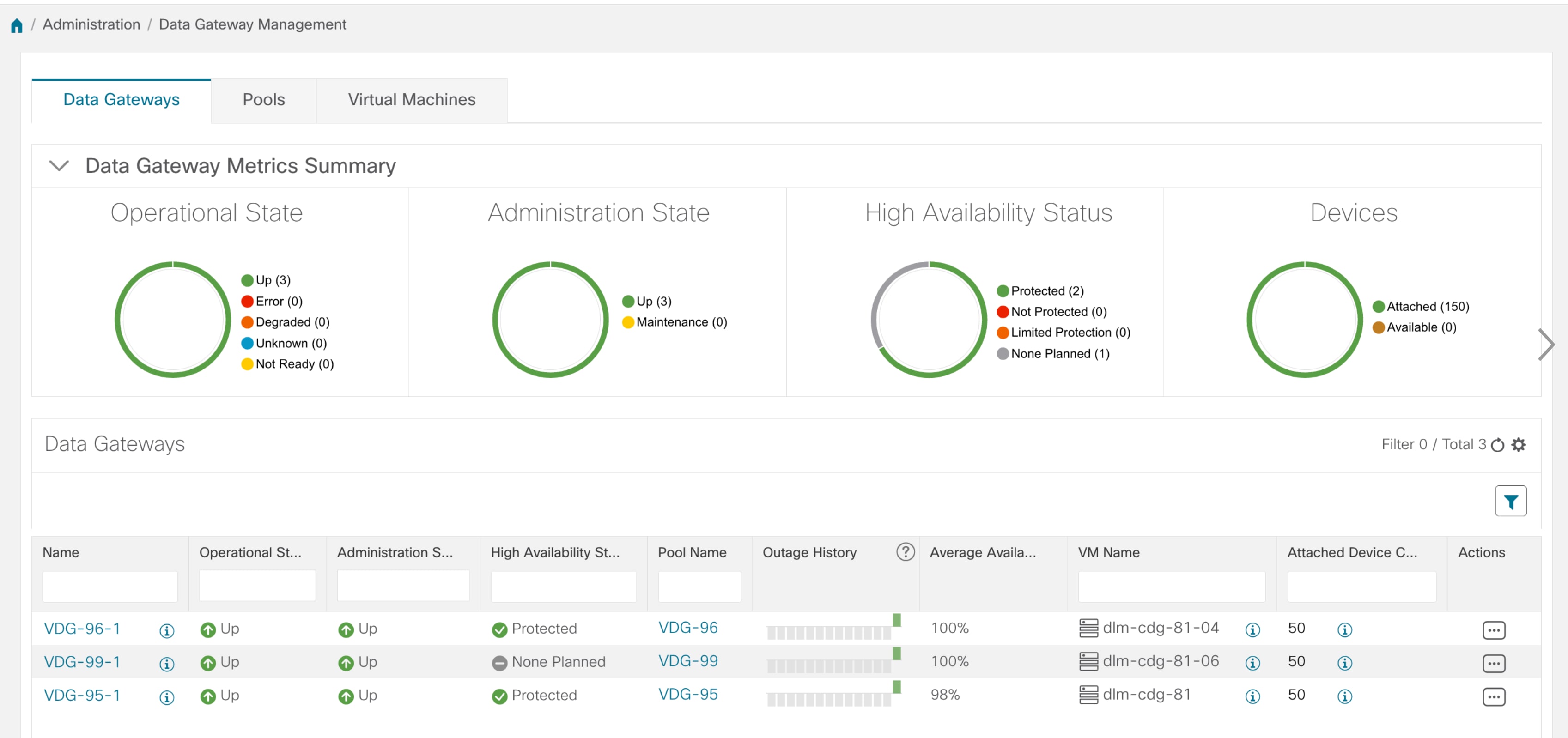
The Data Gateway Management page has three tabs:
-
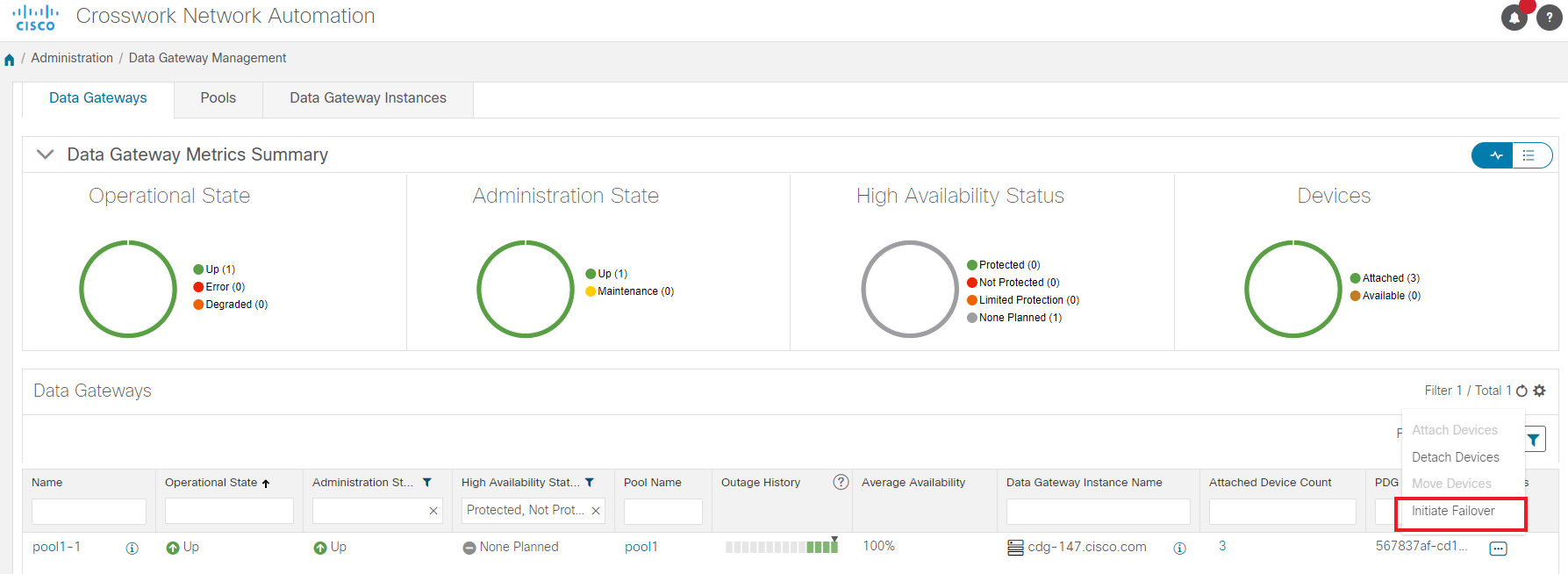
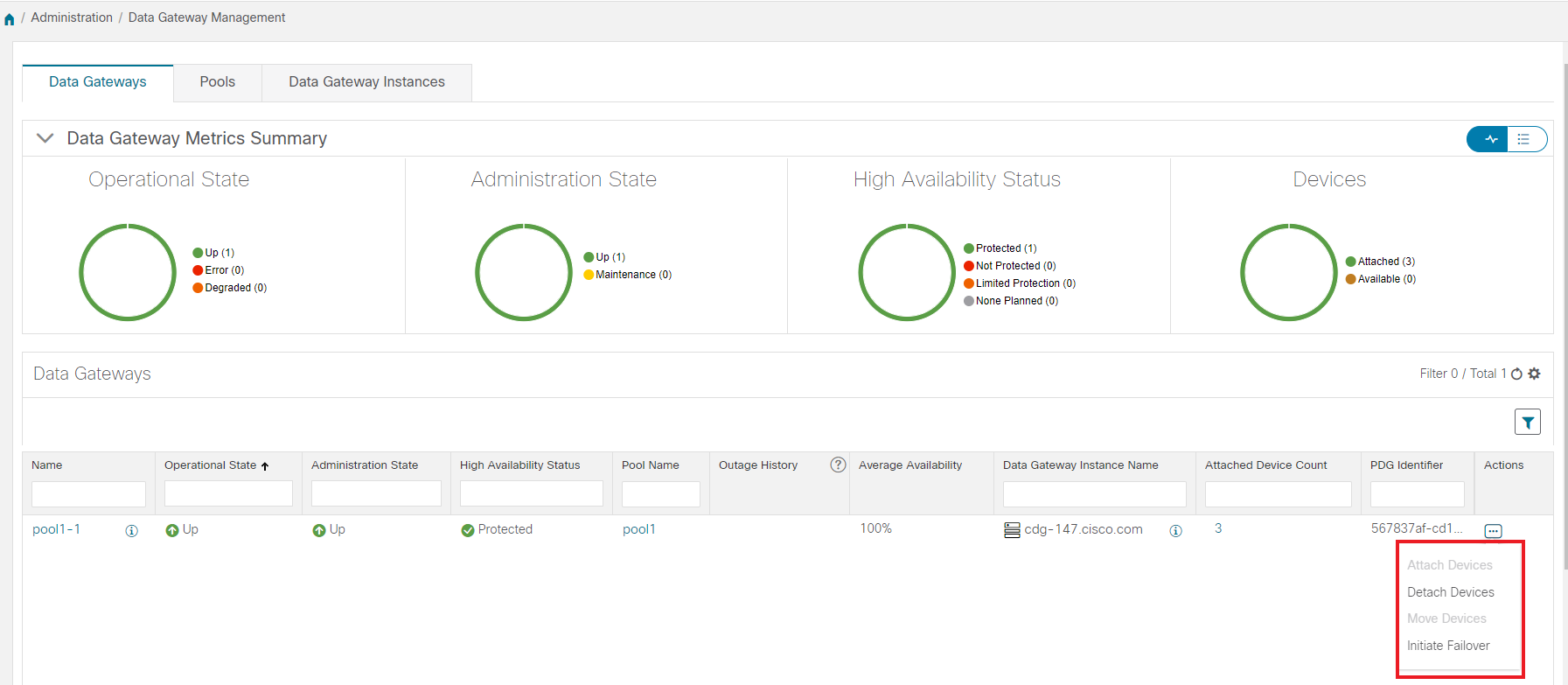
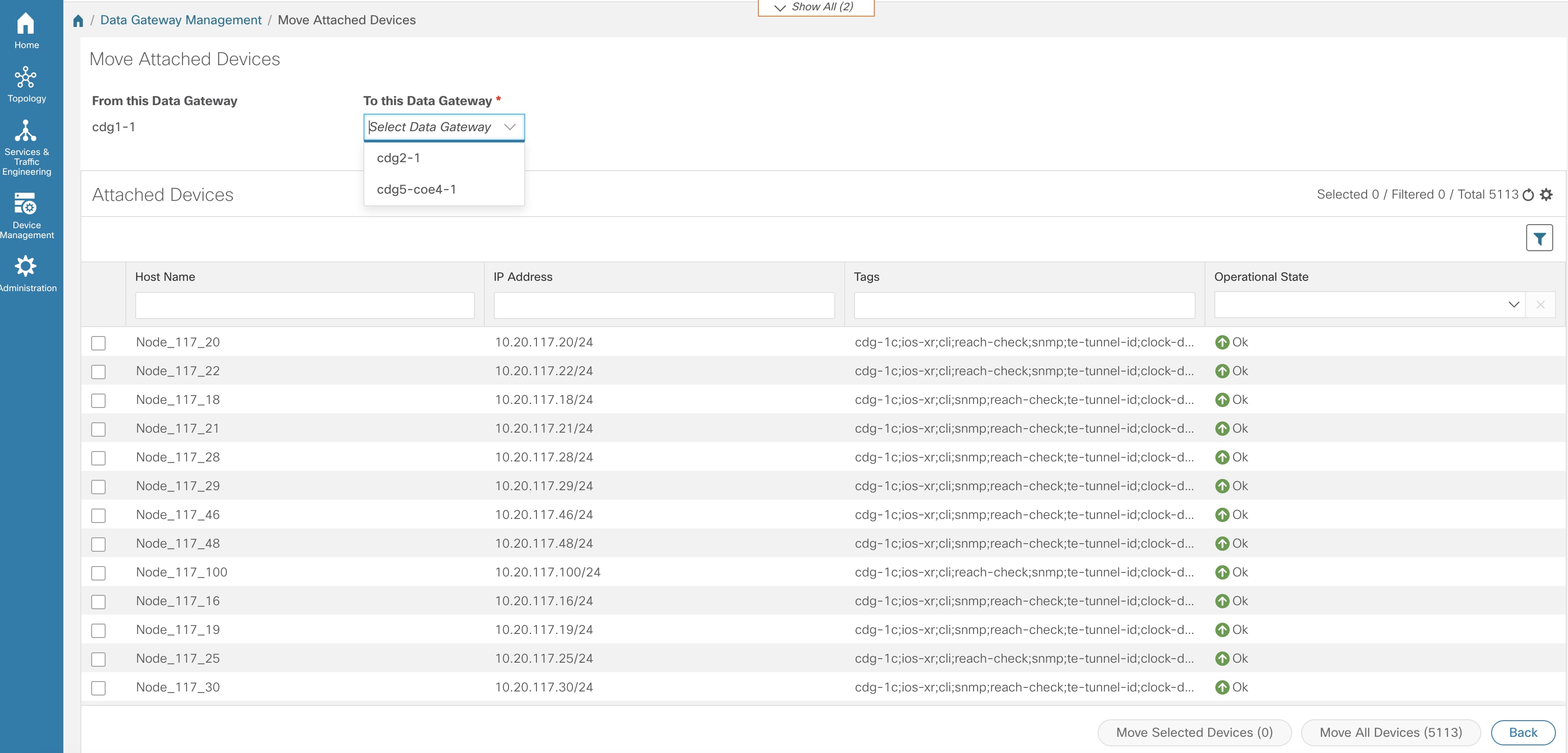
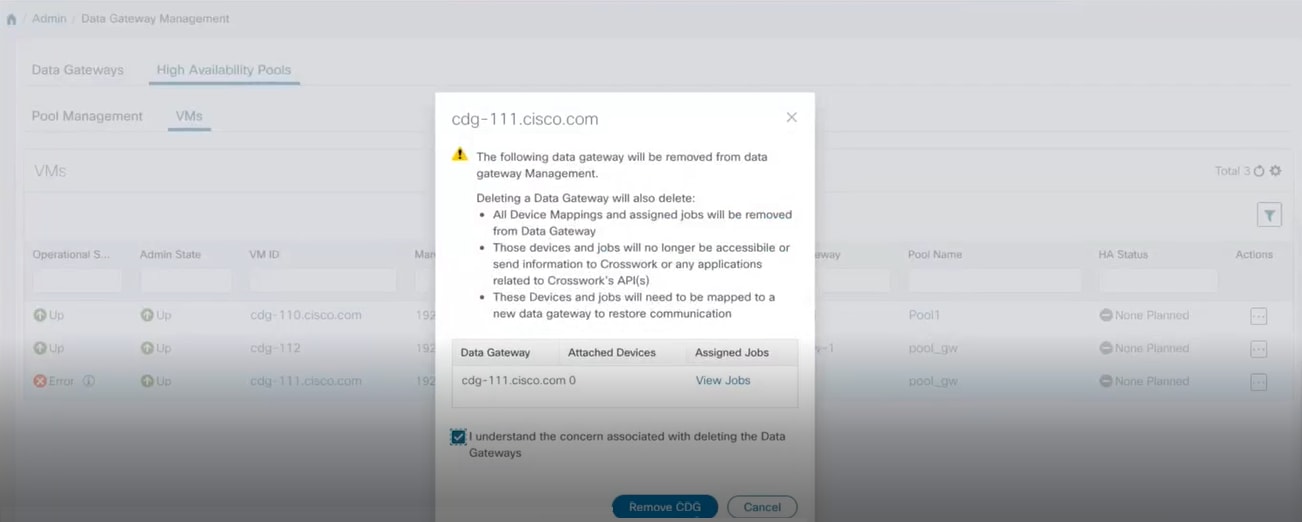
Data Gateways: Displays details of the virtual Cisco Crosswork Data Gateways in the network. You can attach or detach devices to the Data Gateway from this tab.
-
Pools: Manage Cisco Crosswork Data Gateway pools.
-
Virtual Machines: Manage physical Cisco Crosswork Data Gateway VMs.
The following table explains the various fields in the Data Gateway Management page.
|
Field |
Description |
||
|---|---|---|---|
|
Operational State |
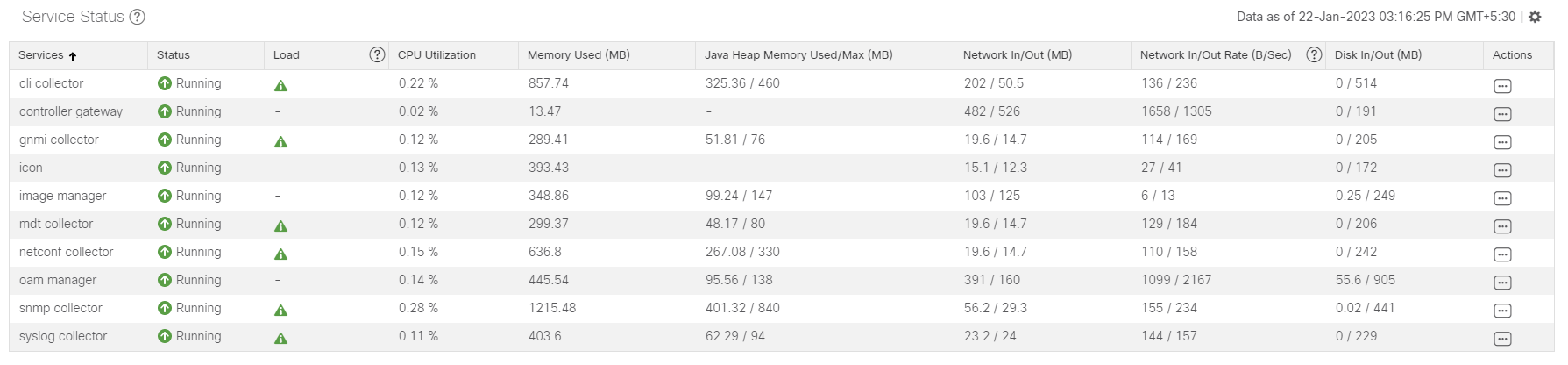
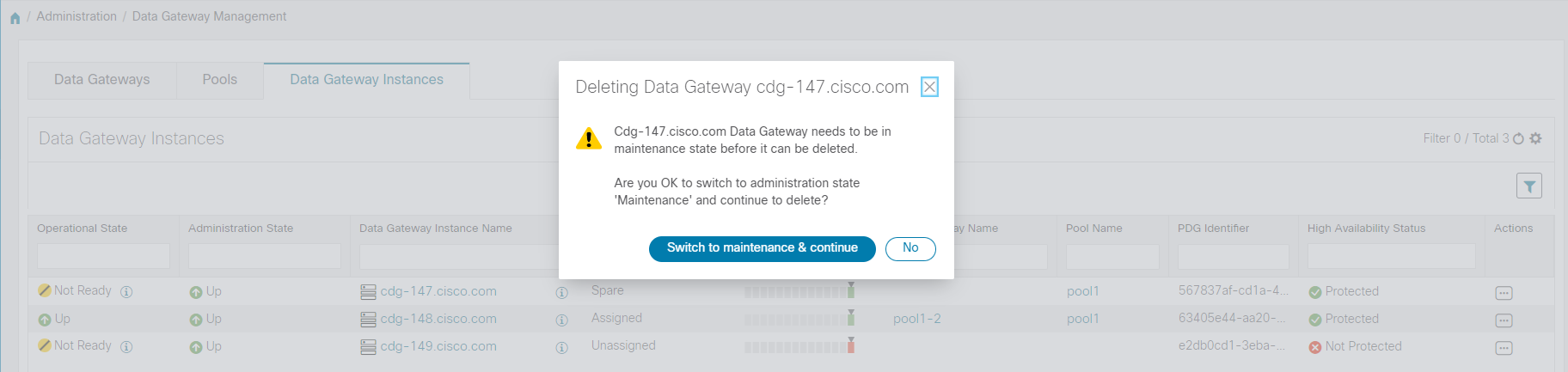
Operational state of the Cisco Crosswork Data Gateway VM. A Crosswork Data Gateway VM has following operational states:
|
||
|
Admin State |
Administration state of the Cisco Crosswork Data Gateway VM.
|
||
|
Virtual Machine Name |
Name of the Cisco Crosswork Data Gateway VM. Clicking the info icon next to the name displays the enrollment details of each VM. This includes details such as, the
|
||
|
IPv4 Mgmt.IP Address |
Management IPv4 address of the Cisco Crosswork Data Gateway VM. |
||
|
IPv6 Mgmt.IP Address |
Management IPv6 address of the Cisco Crosswork Data Gateway VM. |
||
|
Role |
Shows the role of the Cisco Crosswork Data Gateway VM. It can be either:
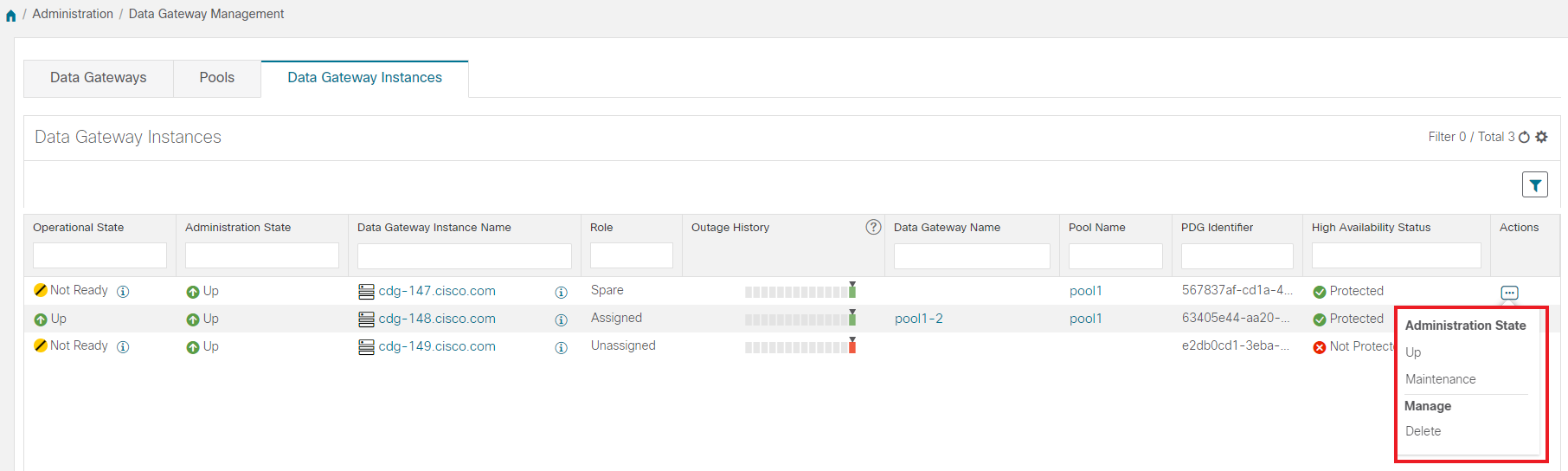
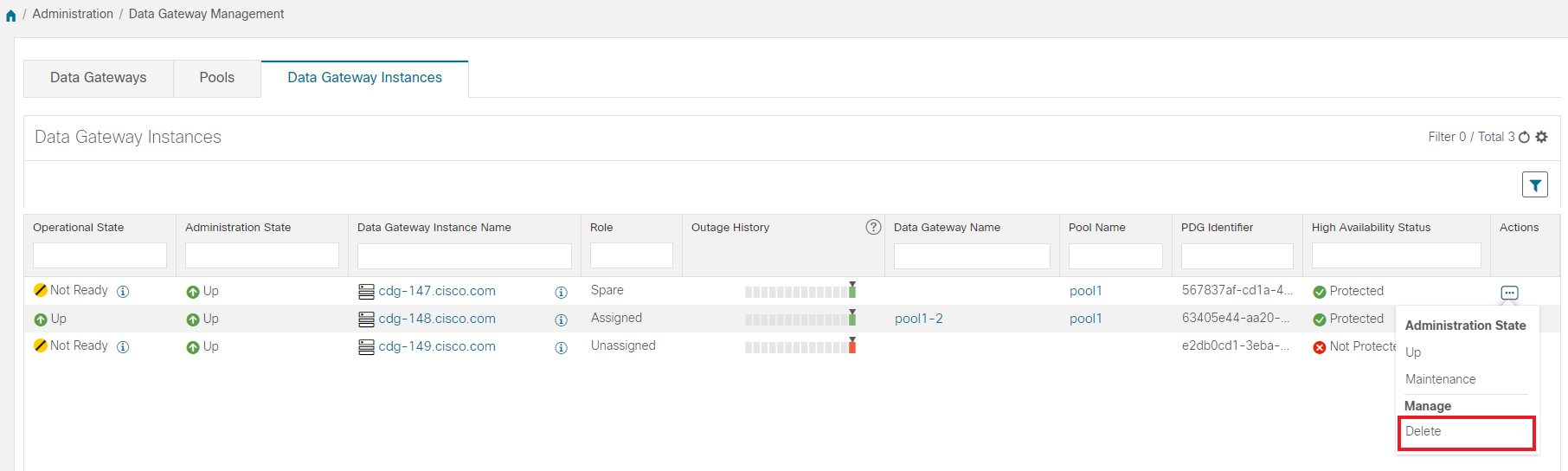
Cisco Crosswork Data Gateway VMs that have the Role as Unassigned need to be assigned to a Crosswork Data Gateway pool before they can used. |
||
|
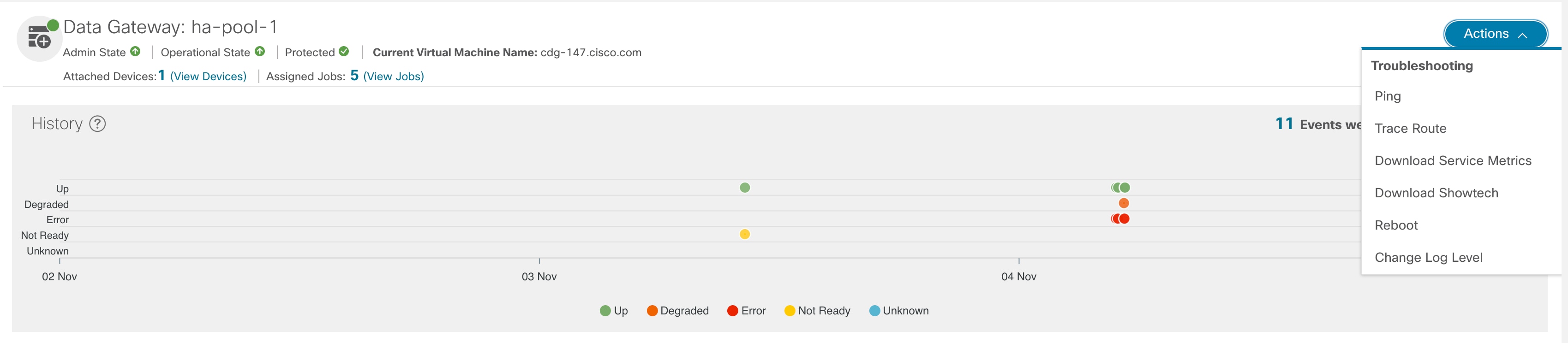
Outage History |
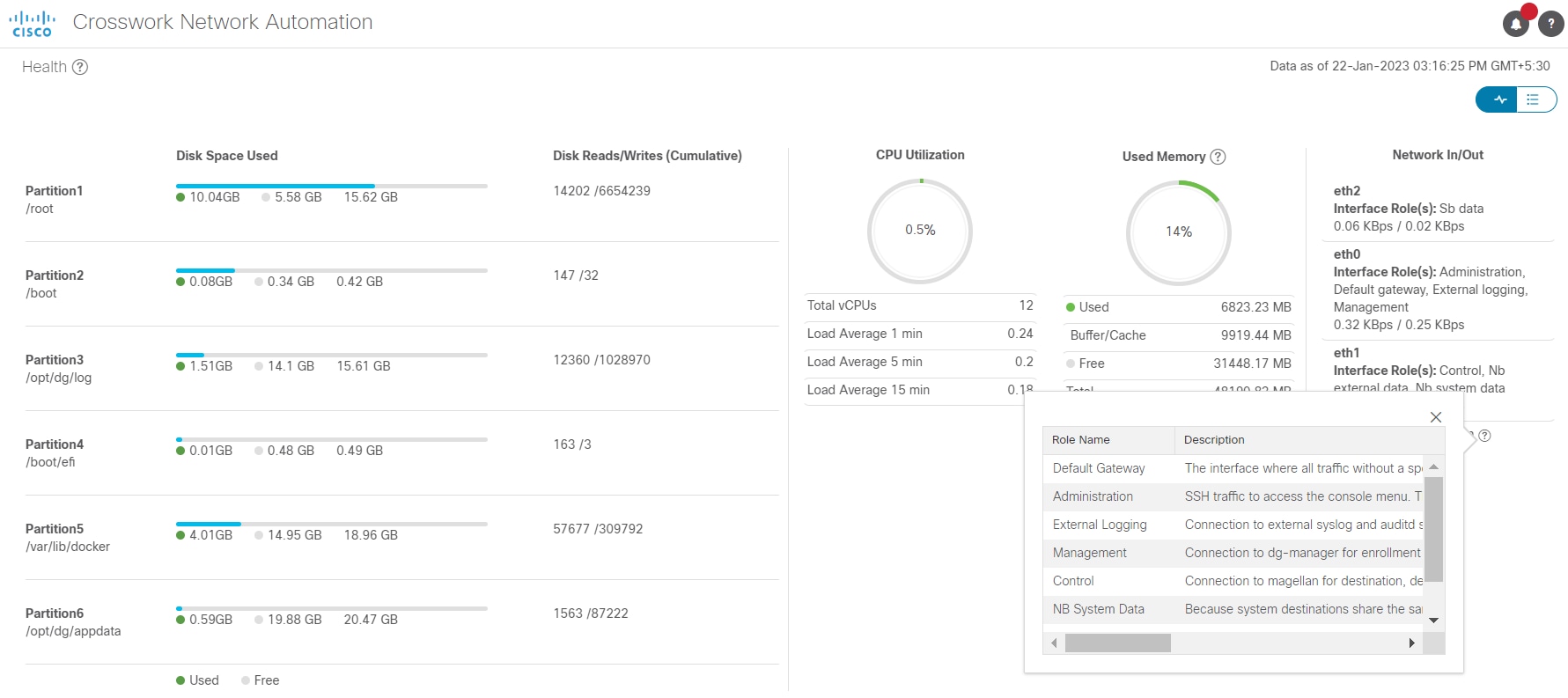
Outage history of the Cisco Crosswork Data Gateway VM over a period of 14 days. State aggregation for a day is done in the order of precedence as Error , Degraded, Up, Unknown and Not Ready. For example, if the Crosswork Data Gateway VM went Unknown to Degraded to Up, color is displayed as Degraded (orange) for that day as Degraded takes precedence over Up and Unknown. If the Crosswork Data Gateway was in Error state at any time during that day, the tile is Red. If the Data Gateway was not in Error but in Degraded State anytime of the day, the tile is Orange. If the DG was not in Error or Degraded state and was only Up, then the tile is Green. |
||
|
Pool Name |
Name of the Crosswork Data Gateway pools to which the Crosswork Data Gateway VM has been assigned. |
||
|
Data Gateway Name |
Name of the Cisco Crosswork Data Gateway that is created automatically when you add a Crosswork Data Gateway VM to a pool. |
||
|
High Availability Status |
High availability status of a Crosswork Data Gateway could be either:
|
||
|
Average Availability |
Value indicating the health of the Cisco Crosswork Data Gateway VM. This percentage is calculated as the total time (in milliseconds) a Crosswork Data Gateway was in UP state over the time between start time of first event and end time of last event .
|
||
|
VM ID |
VM ID of the Cisco Crosswork Data Gateway VM. |
||
|
Attached Device Count |
Number of devices attached to the Cisco Crosswork Data Gateway pool. |
||
|
Unique Identifier |
Unique identifier of the Cisco Crosswork Data Gateway VM. |
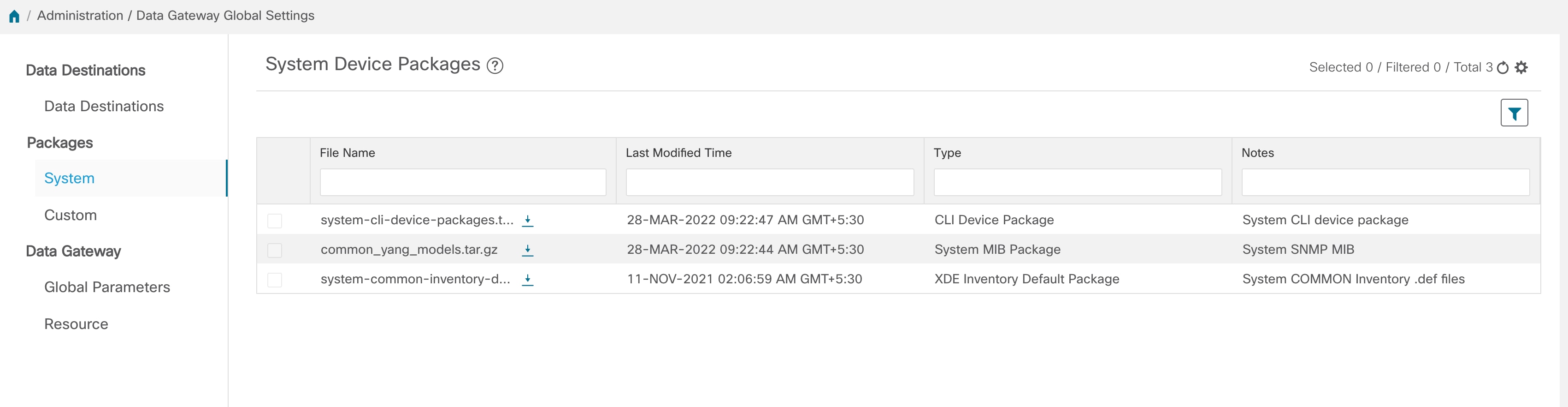
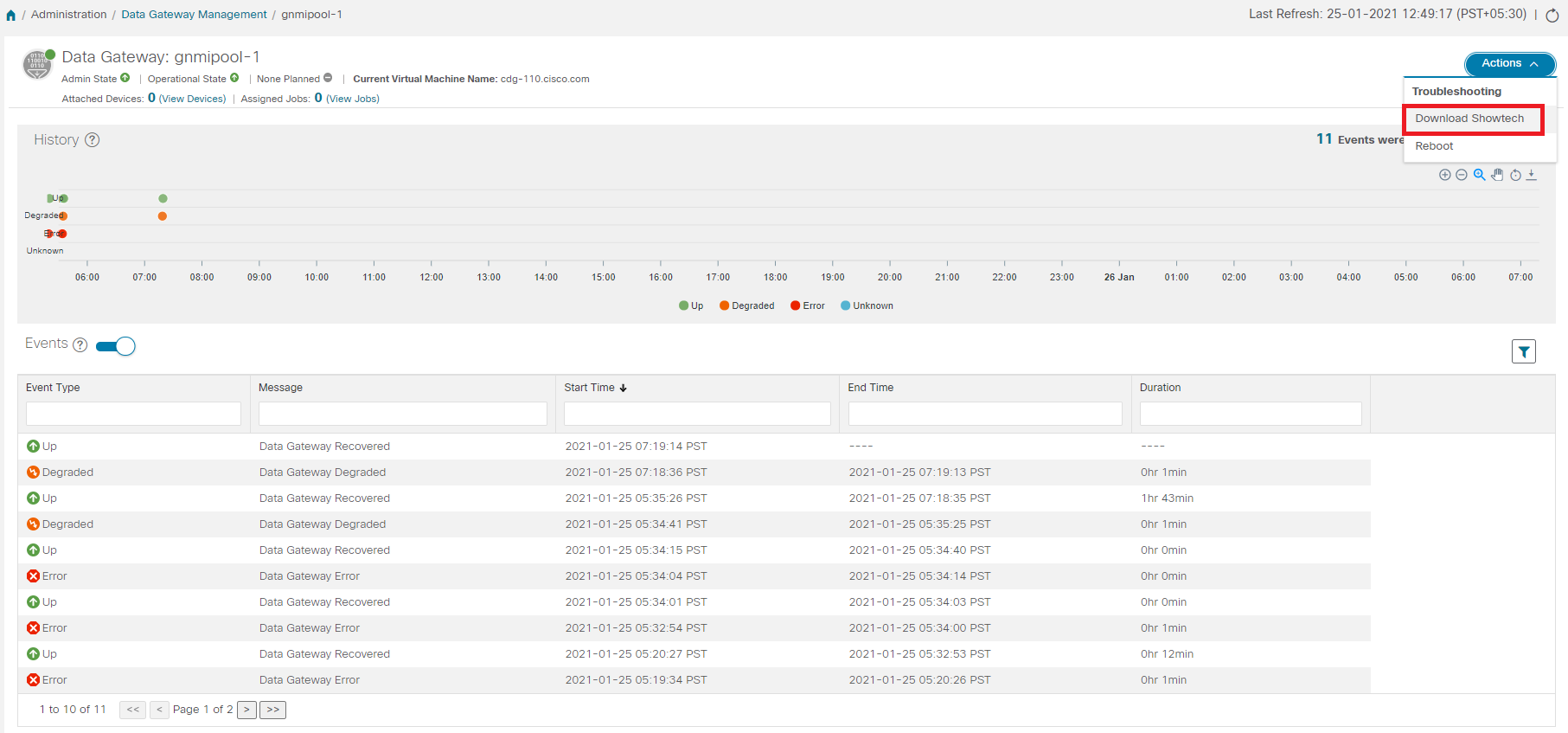
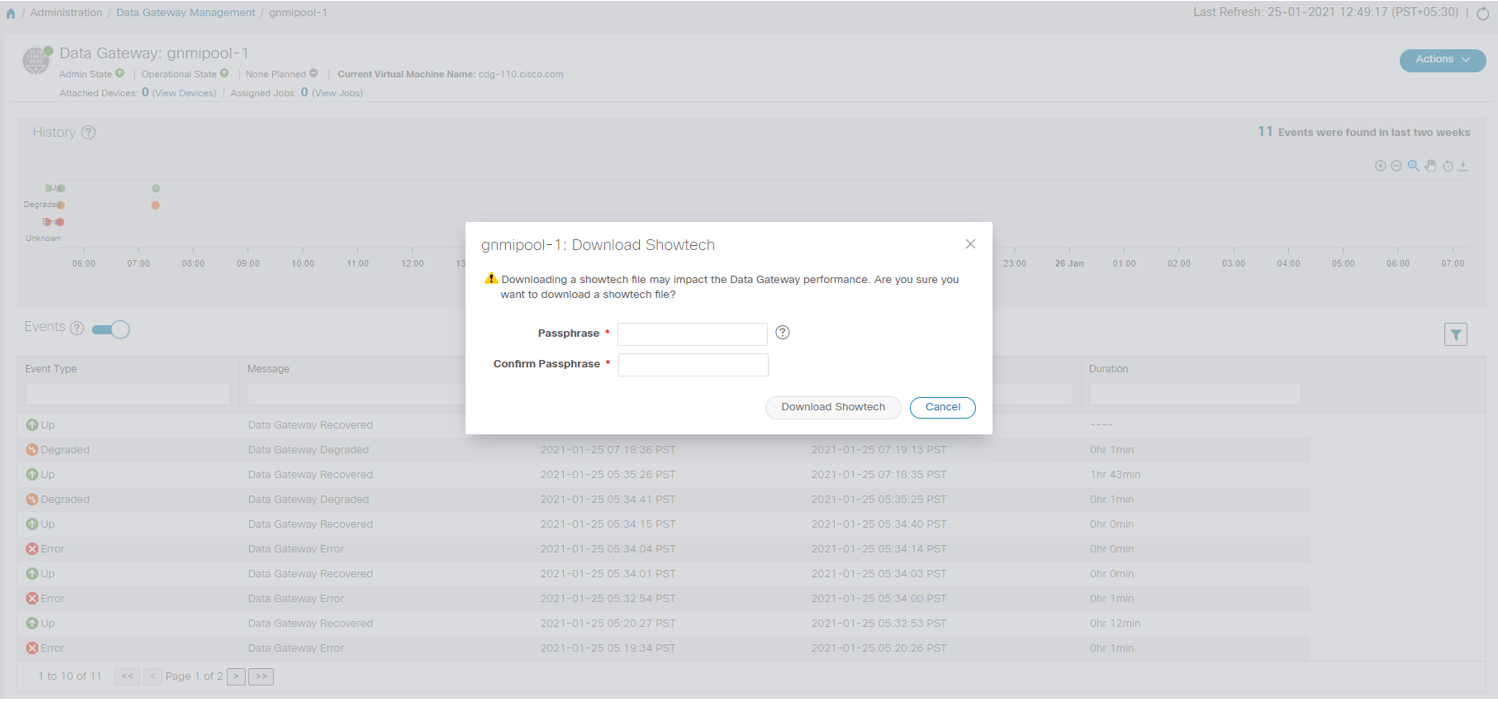
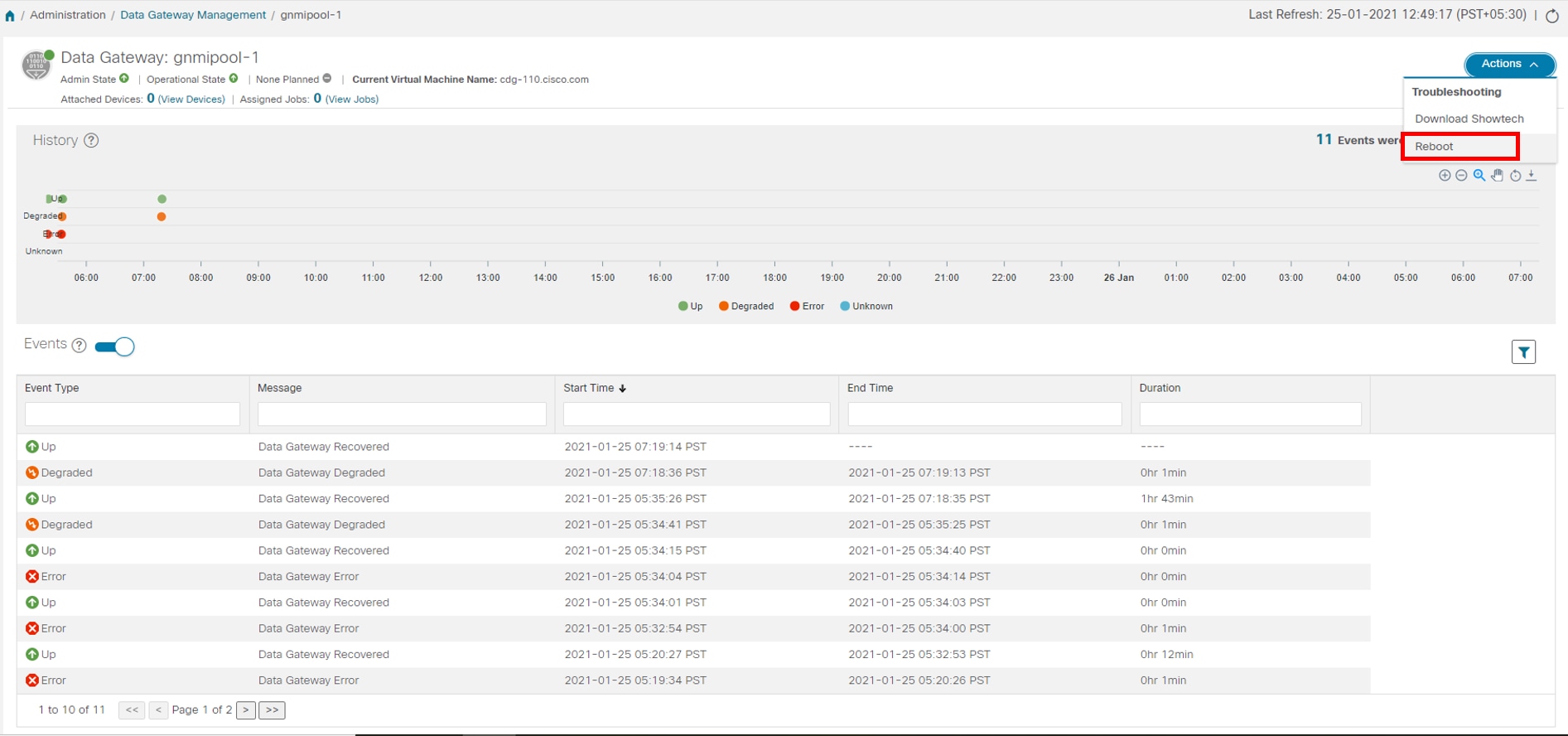
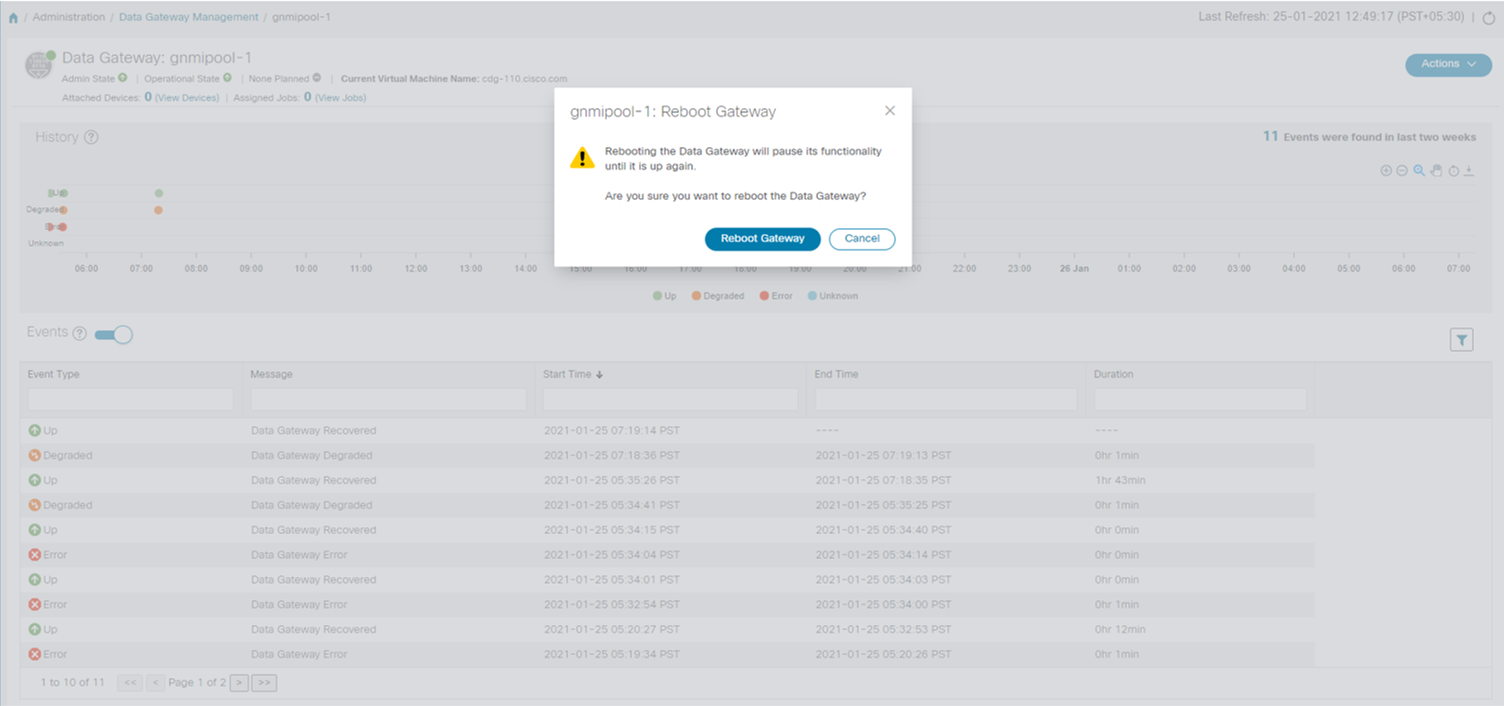
 button next to its name in the File Name column.
button next to its name in the File Name column.

 Feedback
Feedback