Introduction
This document describes how to configure Firewall Threat Defense (FTD) application-based policy based routing (PBR) for Umbrella SIG.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Access to Umbrella Dashboard
- Admin access to the FMC running 7.1.0+ to deploy the configuration to the FTD version 7.1.0+. PBR based on apps is supported only on version 7.1.0 and higher
- (Preferred) Knowledge on FMC/FTD configuration and Umbrella SIG
- (Optional but highly recommended): Umbrella Root Certificate installed, this is used by SIG when the traffic is either proxied or blocked. For further details of the Root Certificate installation, read more in the Umbrella documentation.
Components Used
The information in this document is based on Cisco Umbrella Secure Internet Gateway (SIG).
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Overview
The information in this document is meant to cover the configuration steps on how to deploy Application-Based PBR on the FTD when establishing a SIG IPsec VTI Tunnel to Umbrella, so you can exclude or include traffic on a VPN based on applications using PBR.
The configuration example described in this article focuses on how to exclude certain applications from the IPsec VPN while sending everything else over the VPN.
Full information about PBR on FMC can be found in the Cisco documentation.
Limitations
Application-Based PBR
1. Start by configuring the IPsec tunnel on the FMC as well as on the Umbrella Dashboard. The instructions of how to perform this configuration can be found in the Umbrella documentation.
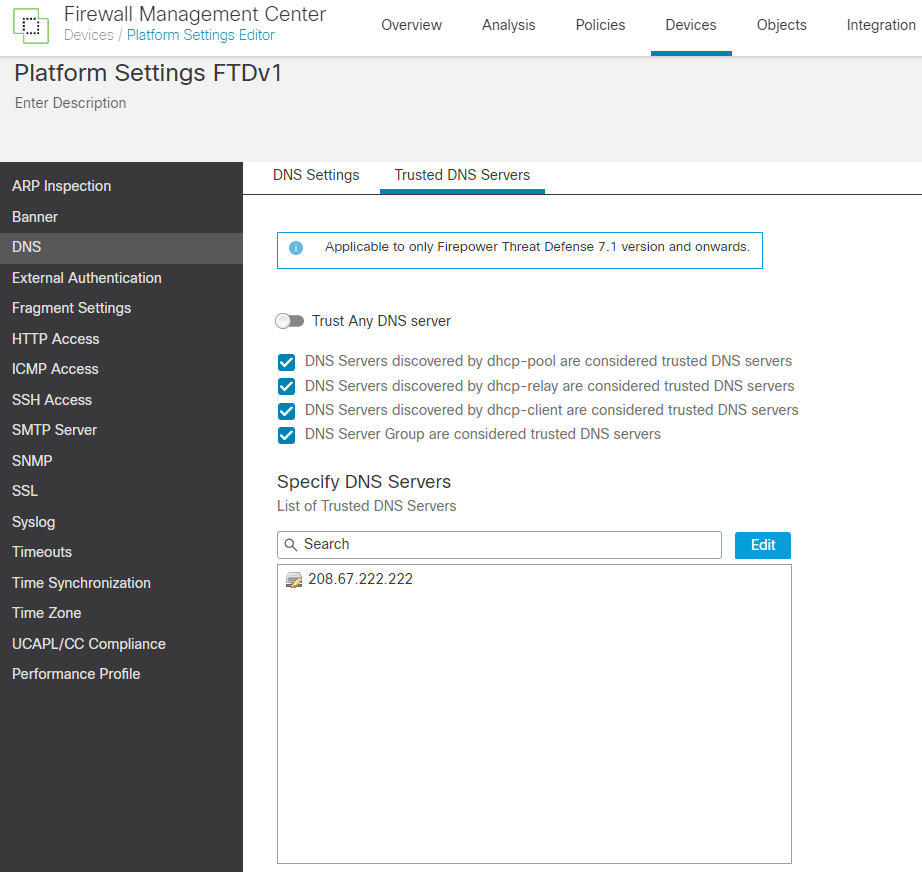
2. Make sure that the DNS server that the end user's device behind the FTD is using is listed as a trusted DNS server under Devices > Platform Settings > DNS > Trusted DNS Servers.
If the devices are using a DNS server that is not listed, the DNS snooping can fail, and therefore the PBR based on apps cannot work. Optionally (but not recommended for security reasons), you can toggle on Trust Any DNS server so that adding the DNS server(s) is required.

Note: If VAs are used as internal DNS resolvers, they must be added as Trusted DNS Servers.
 15669097907860
15669097907860
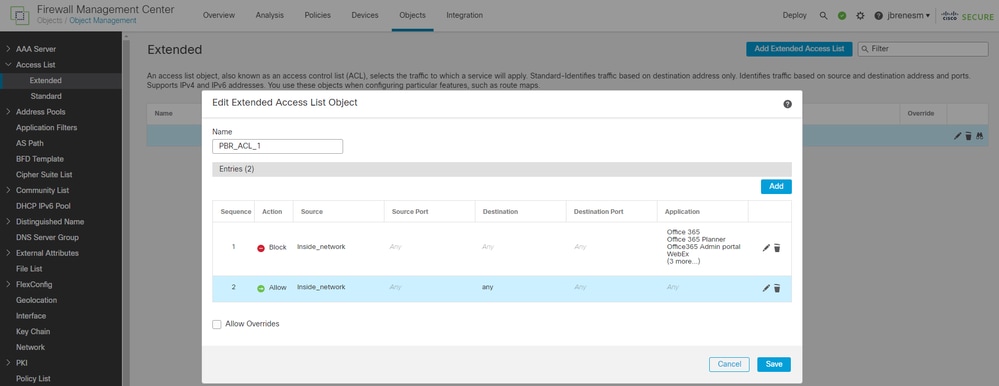
3. Create an extended ACL that can be used by the FTD for the PBR process in order to decide whether traffic is sent to Umbrella for SIG or if it is excluded from the IPsec and not sent to Umbrella at all.
- A deny ACE on the ACL means the traffic is excluded from SIG.
- A permit ACE on the ACL means the traffic is sent over the IPsec and can apply a SIG policy (CDFW, SWG, etc).
This example is excluding the applications "Office365", "Zoom" and "Cisco Webex" with a deny ACE. The rest of the traffic is being sent to Umbrella for further inspection.
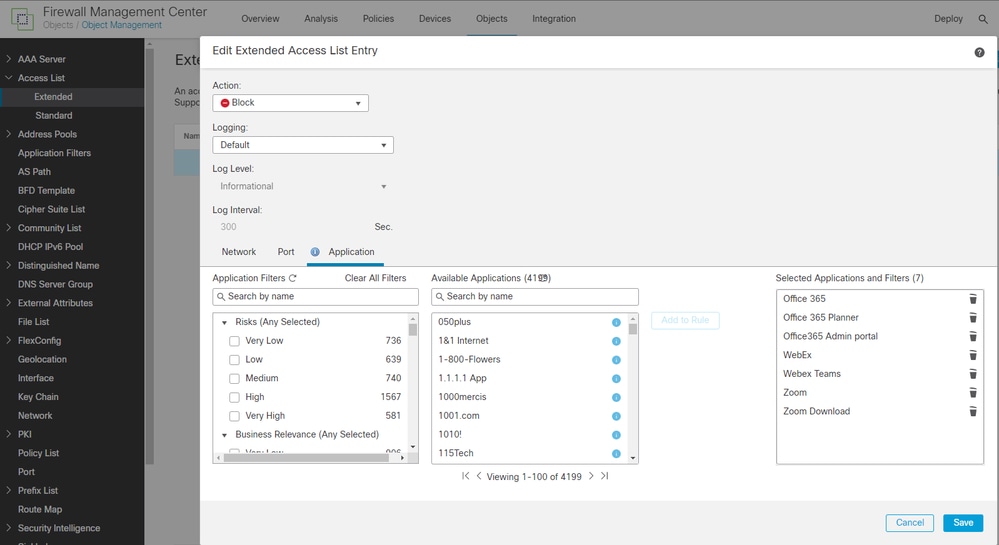
- Go to Object > Object Management > Access List > Extended.
- Define the source network and ports as you normally would, and then add the applications to participate on the PBR.
 15669947000852
15669947000852
The first ACE can "deny" for those applications mentioned earlier, and the second ACE is a permit to send the rest of the traffic over the IPsec.
 15670006987156
15670006987156
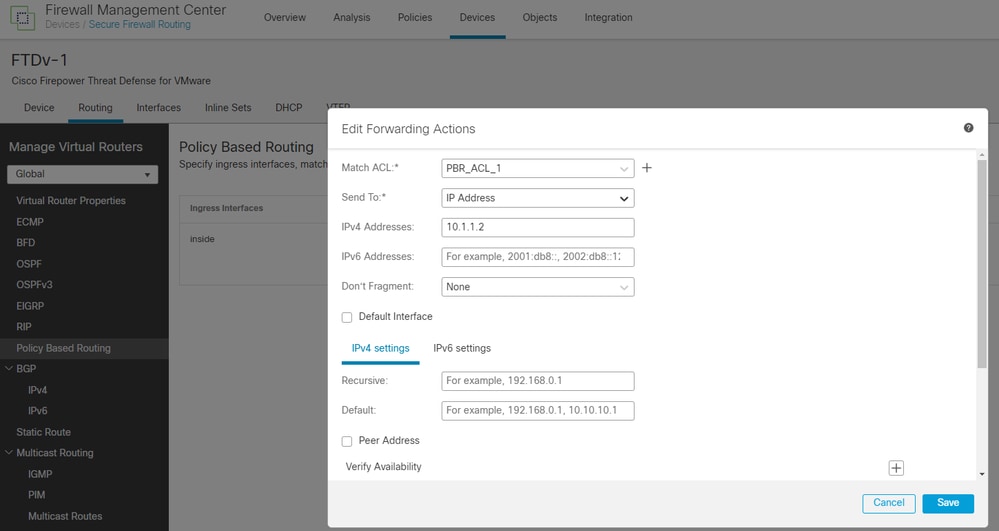
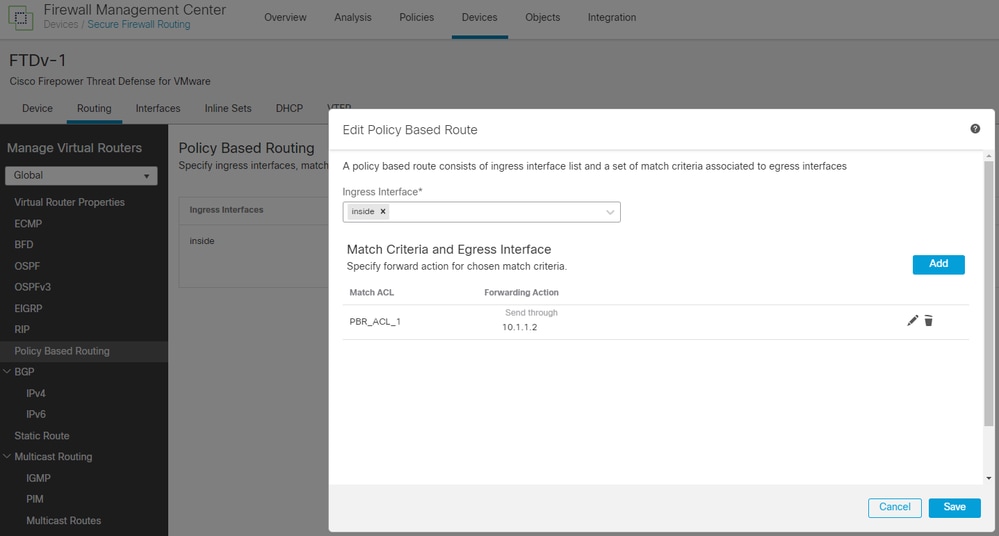
4. Create the PBR under Devices > Device Management > [select the FTD Device] > Routing > Policy Based Routing.
- Ingress Interface: The interface where the local traffic is coming from.
- Matching ACL: Extended ACL created on previous step, ACL "PBR_ACL_1".
- Send To: IP Address
- IPv4 Addresses: Next-hop when the PBR finds a permit statement, so the traffic is routed to the IP you add here. In this example, this is Umbrella's IPsec IP. If your VTI VPN's IP is 10.1.1.1, then the Umbrella's IPsec IP would be anything inside that same network (10.1.1.2 for example).
 15670209158036
15670209158036
 15670247521556
15670247521556
5. Deploy the changes on the FMC.
Verification
On the testing PC located behind the FTD, check:
- On the FTD's CLI, you can run a few commands to confirm the configuration was properly pushed and working:
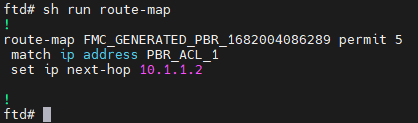
show run route-map (checks the PBR configuration):
 15670322054036
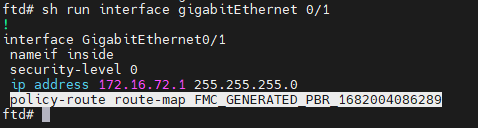
15670322054036show run interface gigabitEthernet 0/1 (checks the PBR is applied to the proper interface)
 15678344219540
15678344219540show run access-list PBR_ACL_1, show object-group id FMC_NSG_17179869596 (confirms the domains added to the ACL for exclusion)
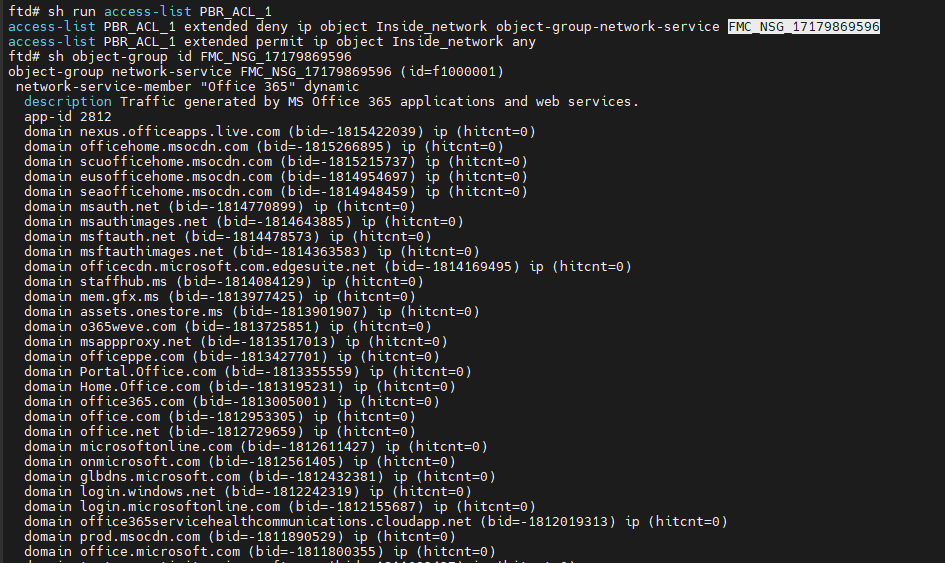 15670420887316
15670420887316
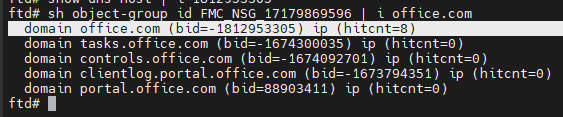 15670635784852
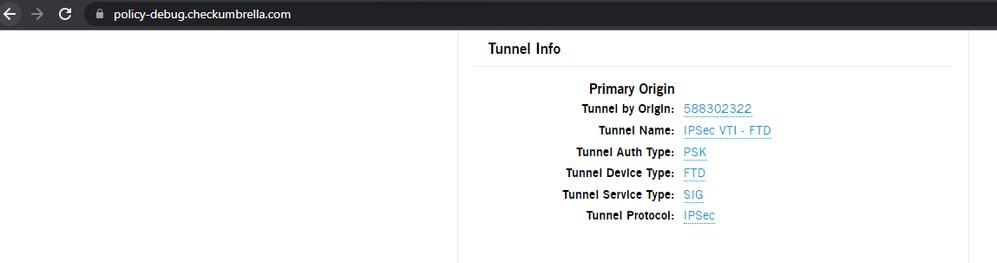
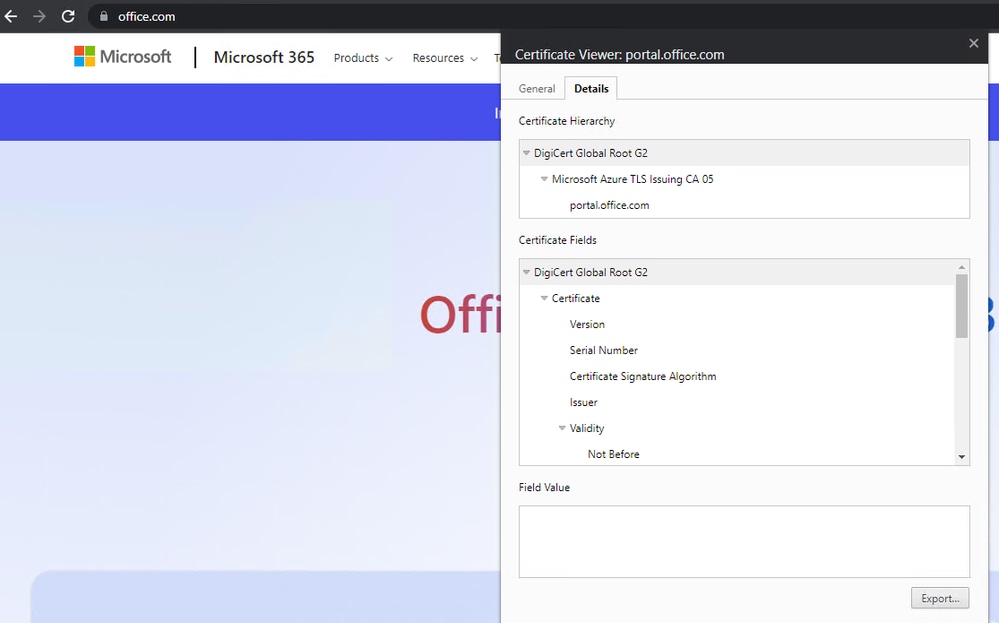
15670635784852packet-tracer input inside tcp 172.16.72.10 1234 fqdn office.com 443 detailed (verifies the outside interface is used as output and not the VTI one)
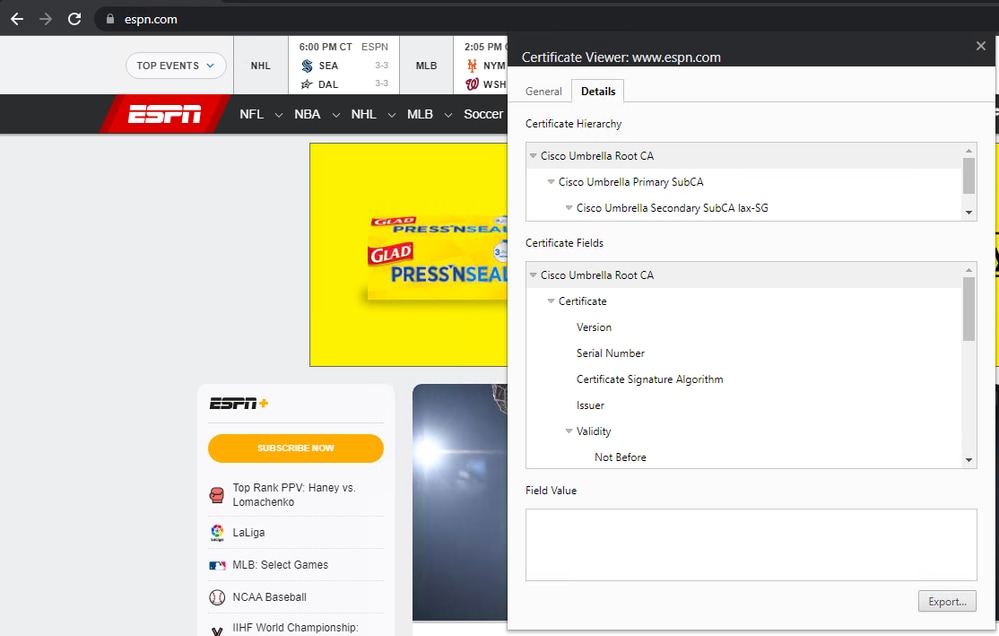
- On the Umbrella Dashboard, under activity search, you can see that web traffic going to office.com was never sent to Umbrella, while traffic going to espn.com was sent.
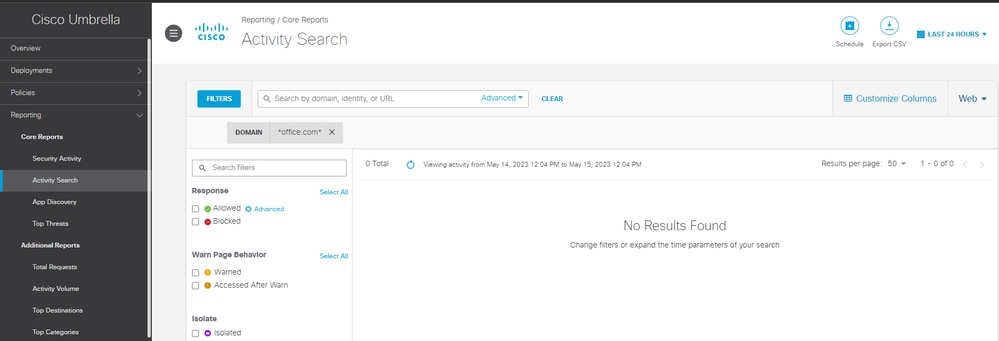 15671098042516
15671098042516
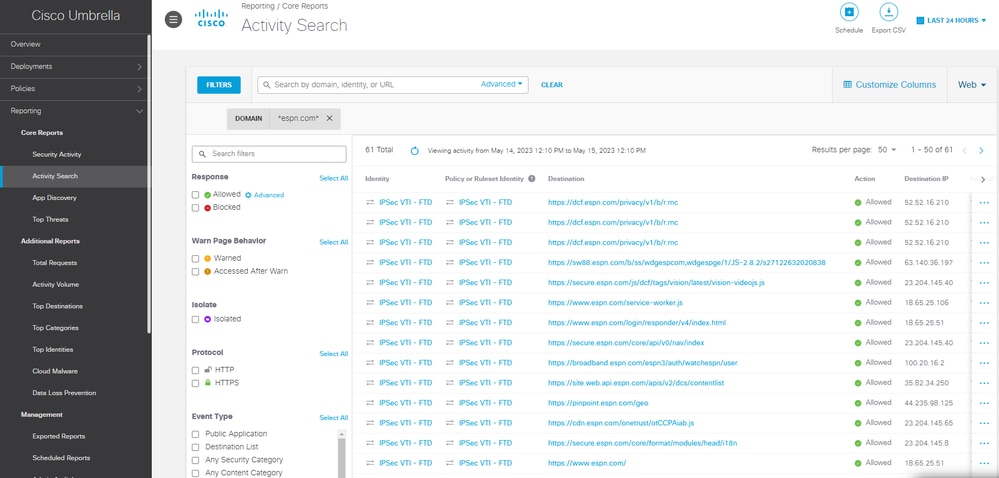 15671302832788
15671302832788














 Feedback
Feedback