Introduction
This document describes the deploying of AnyConnect web security module for client based VPN terminating on Cisco Adaptive Security Appliances (ASA).
Prerequisites
Requirements
There are no specific requirements for this document.
Components used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
- Upload the Anyconnect (recommend v4.1+) image on ASA
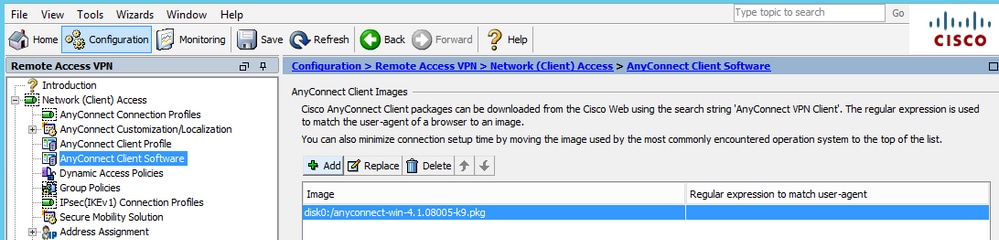
- Enable the VPN profile on ASA, as shown in the image
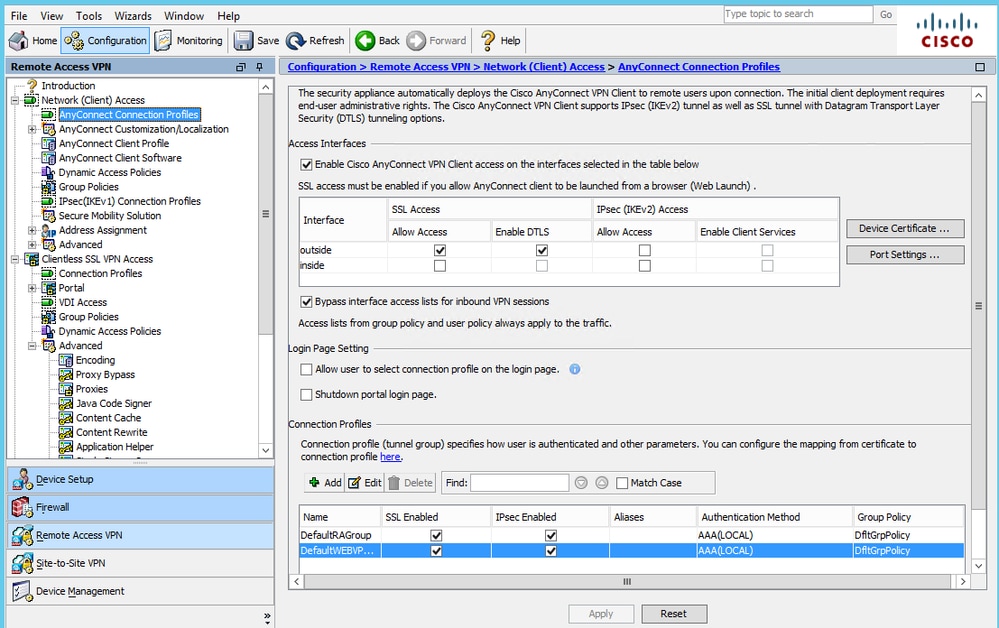
Configure
Anyconnect WebSecurity deployment through ASA
The steps involved in configuration are:
- Configure Anyconnect Websecurity client profile
- Edit Anyconnect VPN group policy
- Set split exclusion for Web Securityand select download Web Security client module
- Edit Anyconnect VPN group policy and select the Web Security client profile
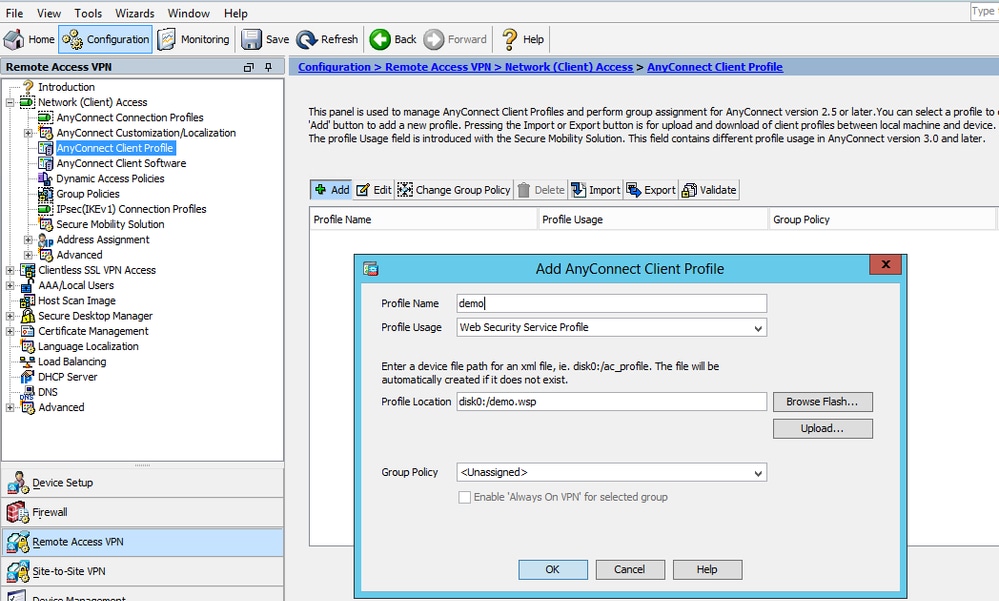
Step 1. Configuring Anyconnect Websecurity Client profile
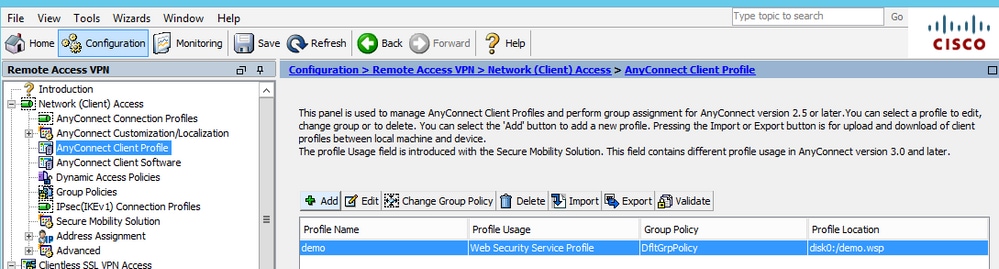
Navigate to Configuration >Remove Access VPN >Network (Client) Access >Anyconnect Client Profile, click on
Add and select the AnyConnect Web Security Client Profile.
Note: The Profile Name is hard-coded on the client side, so regardless of the name configured, the ASA always pushes out Websecurity_serviceprofile.wso to the client.
Note: This is a default profile without authentication license key.
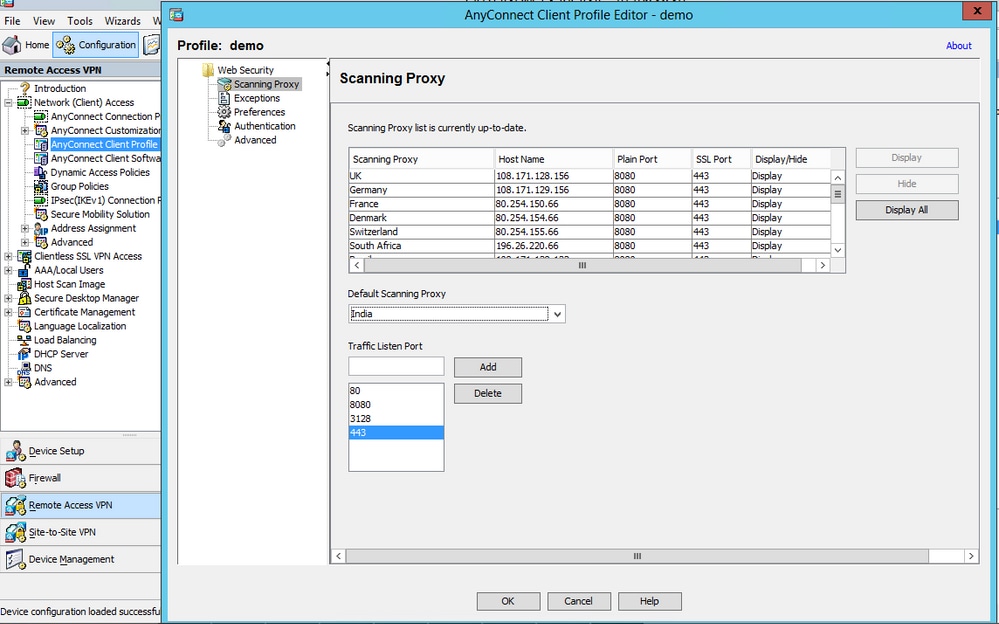
Step 2. Edit the newly created profile to add authentication license key and customize the configuration.
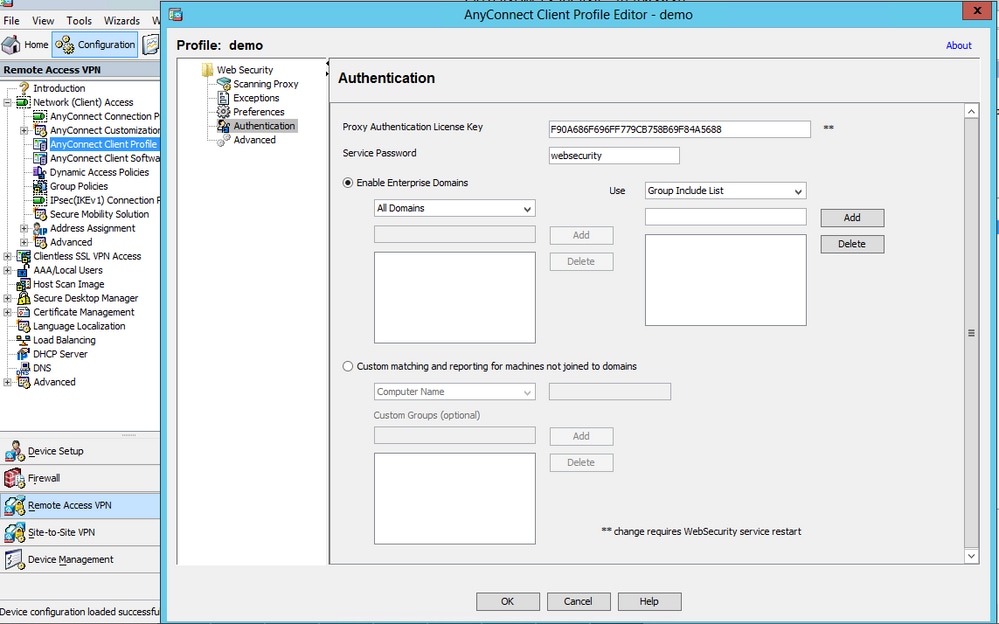
Step 3. Set split exclusion for Web Security and select download Web security client module
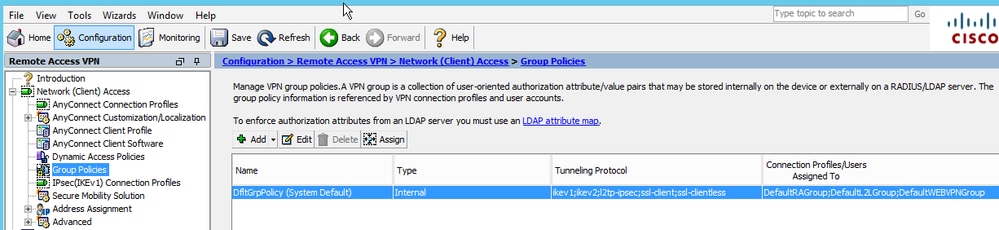
Edit Anyconnect VPN group policy, as shown in the image.
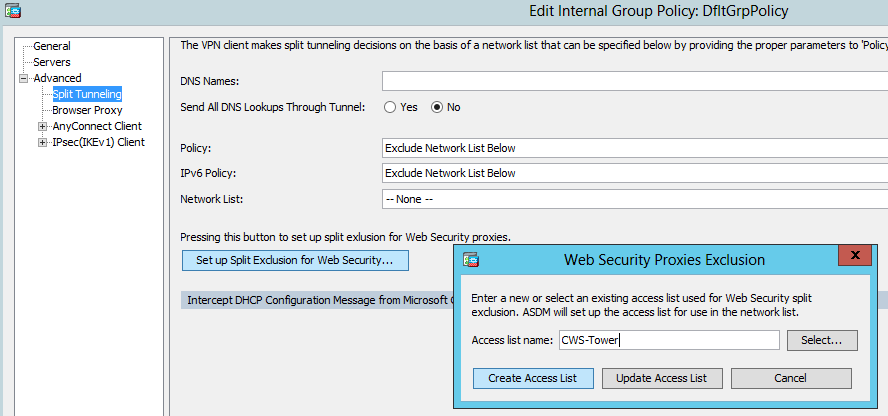
As shown in the image, set up split exclusion for Web Security.
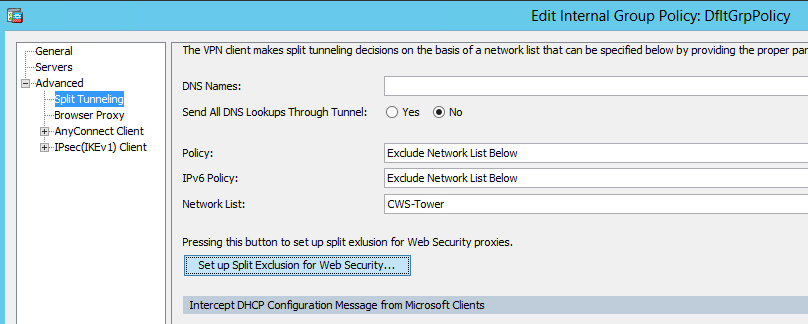
Select download Web Security client module, as shown in the image.

Step 4. Download Web security client profile
Edit Anyconnect VPN group policy > Client Profiles to Download > Add, now choose the created Profile (as in Step 1)
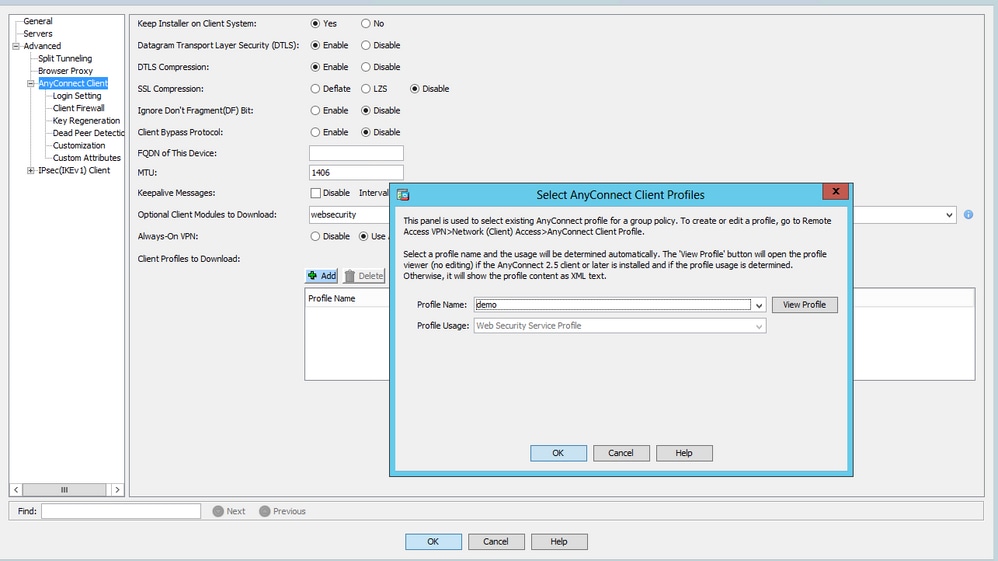
Click OK and apply the changes.
Verify
When you connect to Anyconnect VPN, ASA will push the Anyconnect webscurity module through VPN as shown in the image.
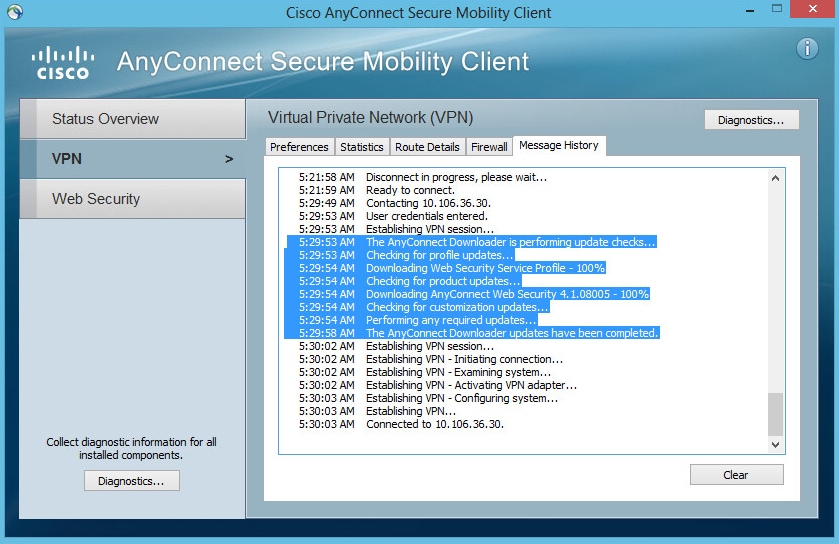
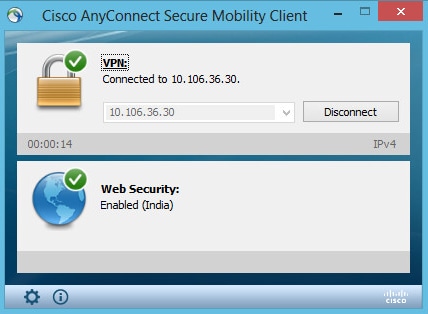
If you are already logged in, its recommended to log off and then log in back for the functionality to be enabled.
Upgrade/Downgrade Anyconnect version
The deployment functionality remains unaltered if the version is upgraded. However, downgrade is not possible. So, with the current example of 4.1.x, it can be upgraded to version 4.2
The steps involved are as follows:
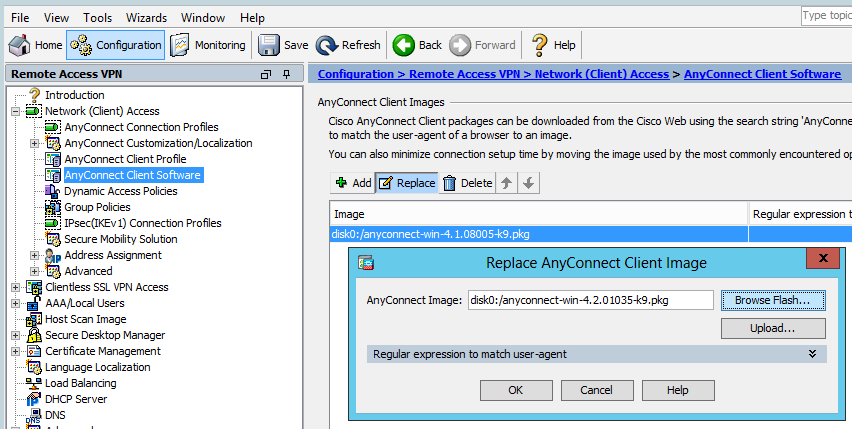
Step 1. Upload the latest Anyconnect package 4.2 to flash and replace 4.1 with latest file.
Under Anyconnect Client Software > Replace, and then choose the recent image file.
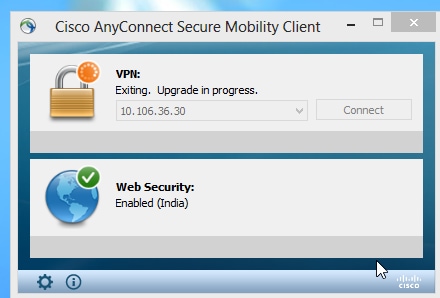
Step 2. When you re-connect to Anyconnect VPN, ASA will push the latest Anyconnect module through VPN with no alterations to the web security profile.
Note: Downgrade is not supported.
Troubleshoot
This section provides information you can use in order to troubleshoot your configuration.
Using DART to Gather Troubleshooting Information:
DART is the AnyConnect Diagnostics and Reporting Tool that you can use to collect data useful for troubleshooting AnyConnect installation and connection problems. DART supports Windows 7, Windows Vista, Windows XP, Mac version 10.5 and 10.6, and Linux Redhat. The DART wizard runs on the computer that runs AnyConnect. It assembles the logs, status, and diagnostic information for Cisco Technical Assistance Center (TAC) analysis and does not require administrator privileges.
Although DART does not rely on any component of the AnyConnect software to run, yet you can launch it from AnyConnect, it will collect the AnyConnect log file, if it is available. Currently, DART is available as a standalone installation, or the administrator can push this application to the client PC as part of the AnyConnect dynamic download infrastructure. Once installed, the end user can start the wizard from the Cisco folder available through the Start button.


















 Feedback
Feedback