Introduction
This document describes how to configure a static route-based site to site VPN tunnel on a FTD managed by FDM.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Basic understanding of how a VPN tunnel works.
- Prior knowledge of navigating through the Firepower Device Manager(FDM).
Components Used
The information in this document is based on these software versions:
- Cisco Firepower Threat Defense (FTD) version 7.0 managed by Firepower Device Manager(FDM).
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Route-based VPN allows determination of interesting traffic to be encrypted, or sent over VPN tunnel, and use traffic routing instead of policy/access-list as in Policy-based or Crypto-map based VPN. The encryption domain is set to allow any traffic which enters the IPsec tunnel. IPsec Local and remote traffic selectors are set to 0.0.0.0/0.0.0.0. This means that any traffic routed into the IPsec tunnel is encrypted regardless of the source/destination subnet.
This document focuses on Static Virtual Tunnel Interface (SVTI) configuration.

Note: No additional licensing is needed, Route Based VPN can be configured in Licensed as well as Evaluation Modes. Without crypto compliance (Export Controlled Features Enabled), only DES can be used as an encryption algorithm.
Configuration Steps on FDM
Step 1. Navigate to Device > Site To Site.
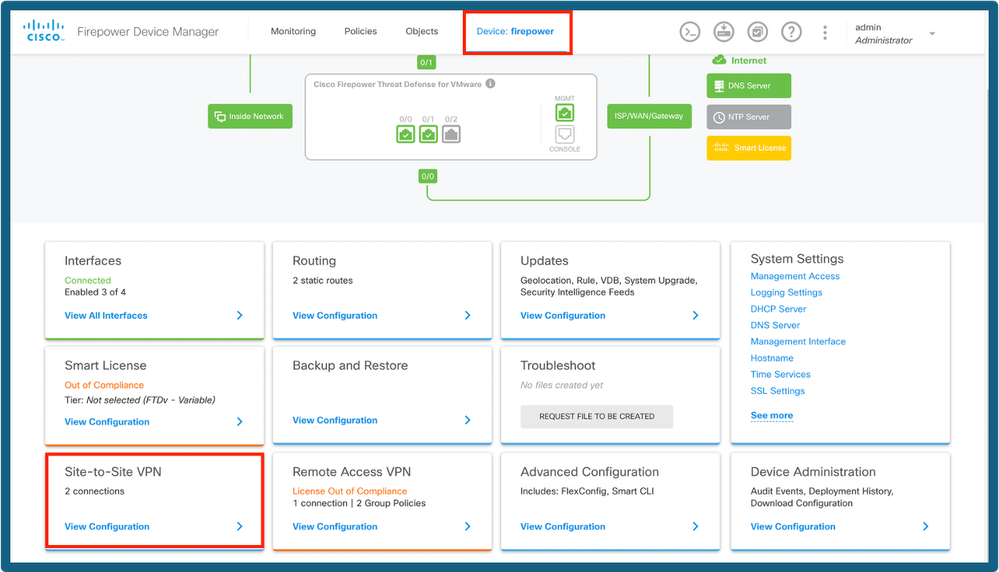 FDM Dashboard
FDM Dashboard
Step 2. Click on the + icon to add a new site to site connection.
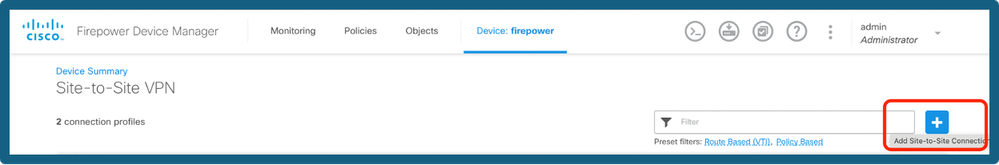 Add S2S Connection
Add S2S Connection
Step 3. Provide a Topology Name and select the Type of VPN as Route Based (VTI).
Click on Local VPN Access Interface, and then click Create new Virtual Tunnel Interface or select one from the list that exists.
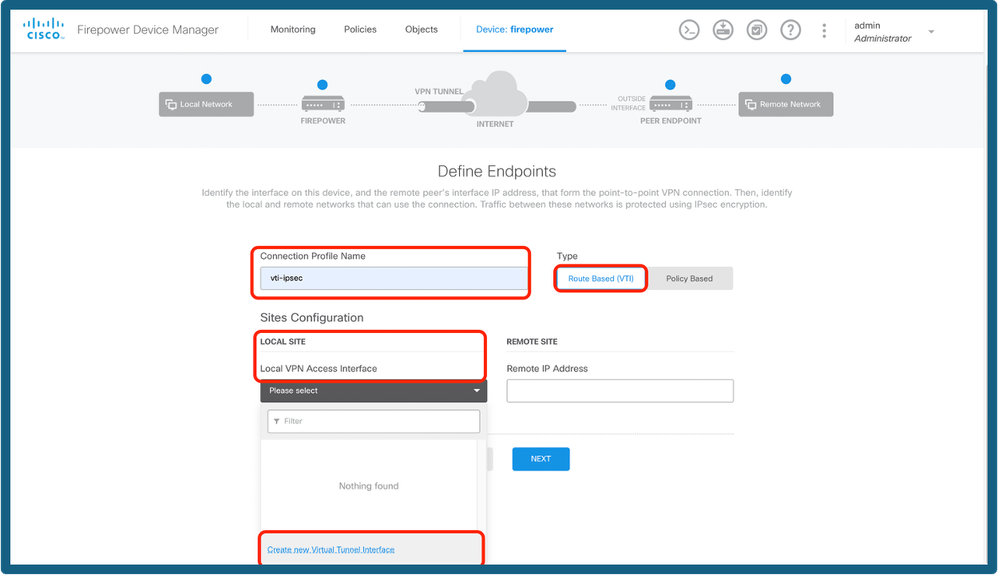 Add Tunnel Interface
Add Tunnel Interface
Step 4. Define the parameters of the New Virtual Tunnel Interface. Click Ok.
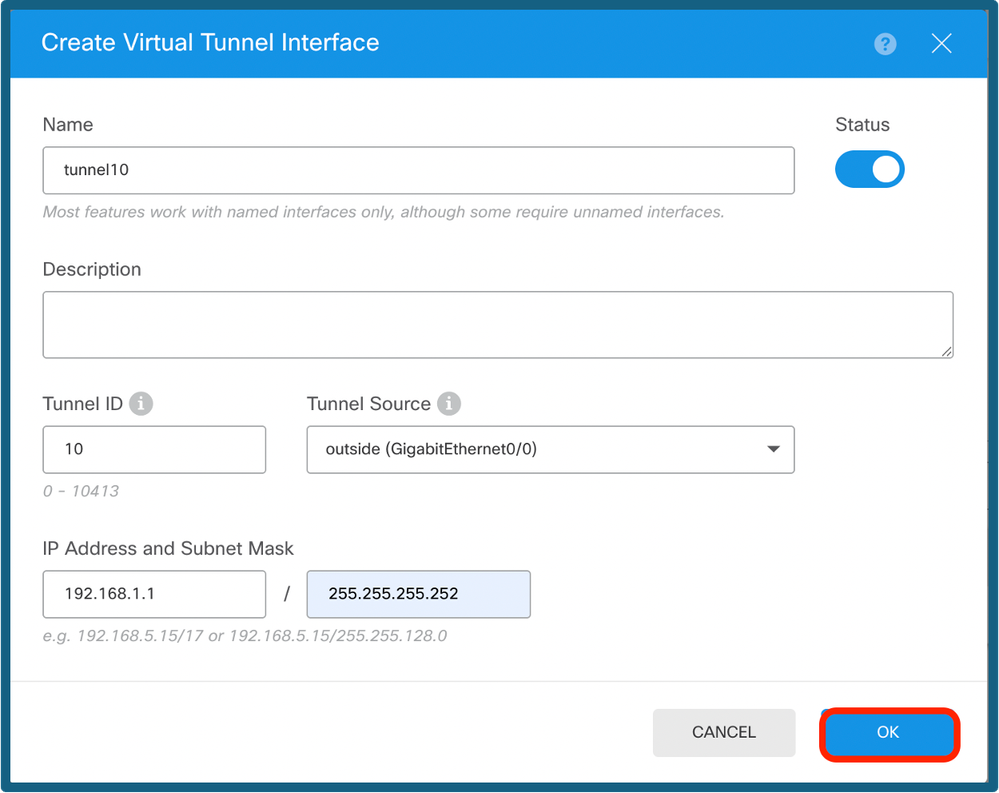 VTI Config
VTI Config
Step 5. Choose the newly created VTI or a VTI that exists under Virtual Tunnel Interface.Provide the Remote IP address.
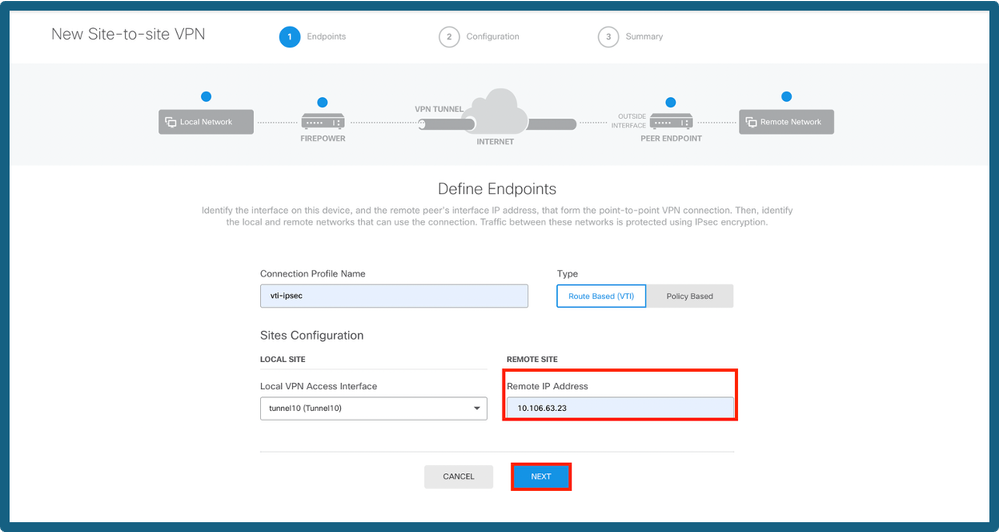 Add Peer IP
Add Peer IP
Step 6. Choose the IKE Version and choose the Edit button to set the IKE and IPsec parameters as shown in the image.
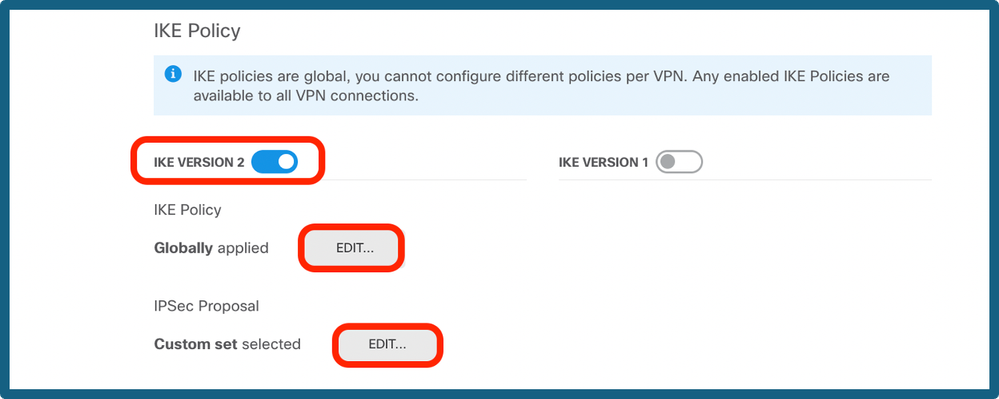 Configure IKE Version
Configure IKE Version
Step 7a. Choose the IKE Policy button as shown in the image and click on ok button or Create New IKE Policy, if you like to create a new policy.
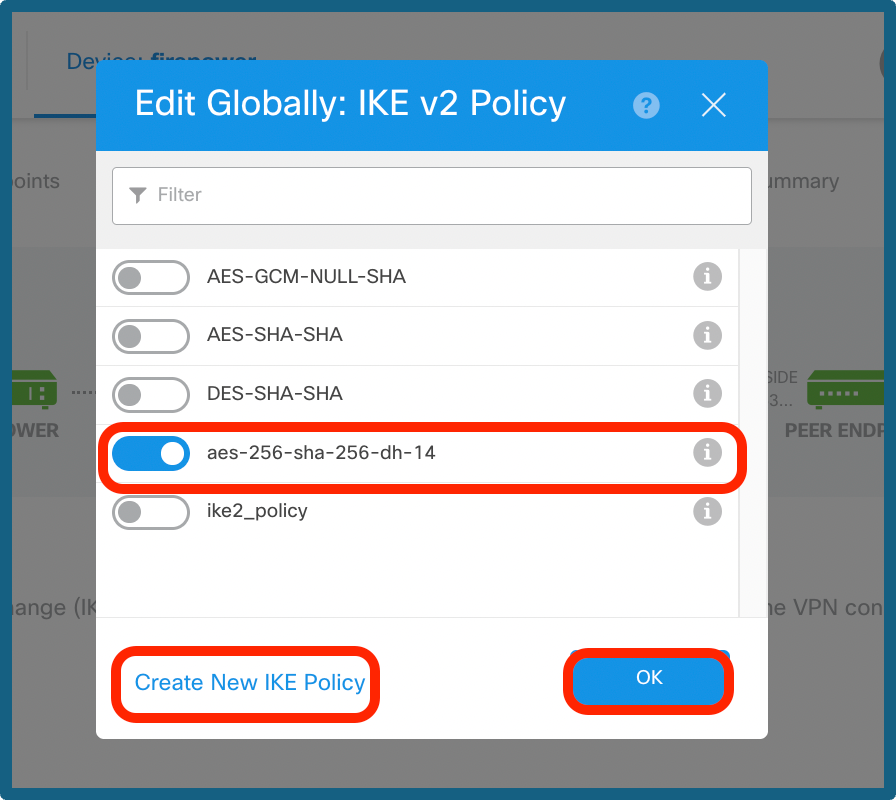 Choose IKE Policy
Choose IKE Policy
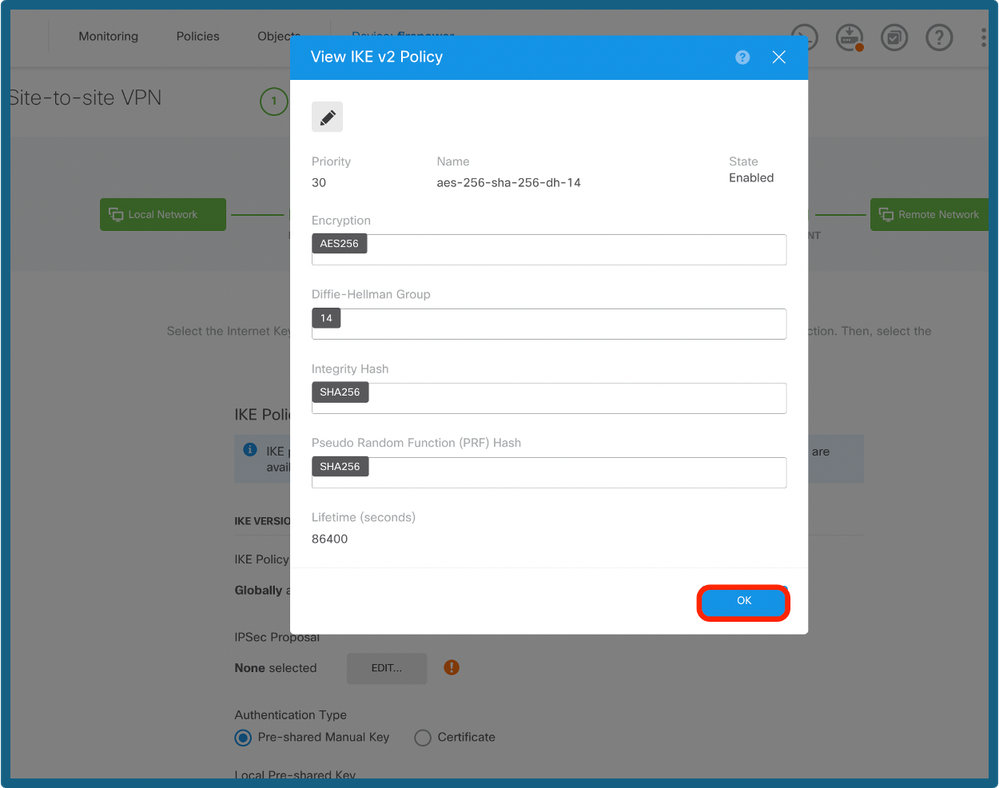 Config of IKE Policy
Config of IKE Policy
Step 7b. Choose the IPSec Policy button as shown in the image and click on ok button or Create New IPsec Proposal, if you like to create a new proposal.
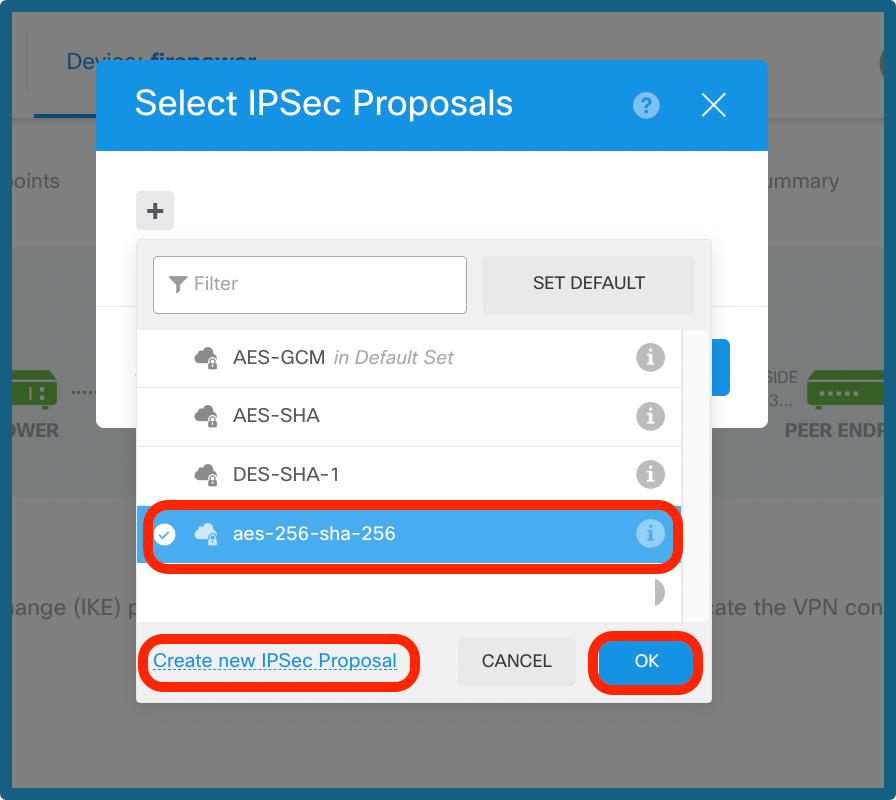 Select IPsec Proposal
Select IPsec Proposal
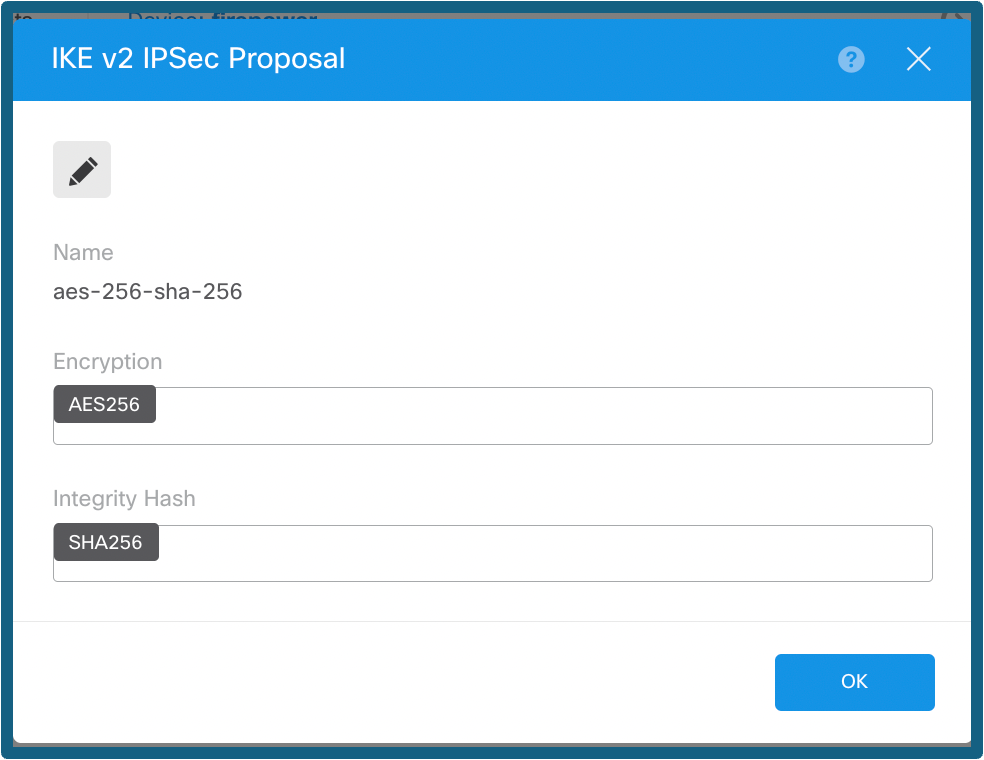 Config of IPsec Proposal
Config of IPsec Proposal
Step 8a. Select the Authentication Type. If Pre-shared Manual Key is used, provide the Local and Remote Pre-shared Key.
Step 8b. (Optional) Choose the Perfect Forward Secrecy settings. Configure the IPsec Lifetime Duration and Lifetime Size, and then click on next.
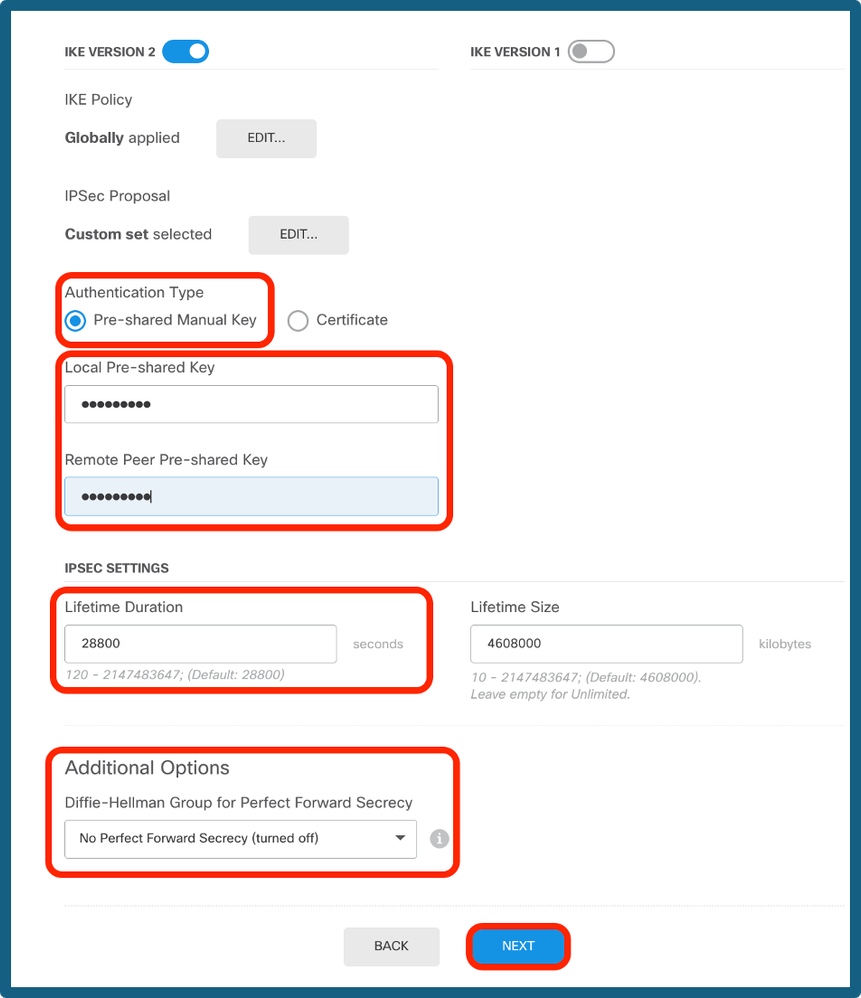 PSK and Lifetime Config
PSK and Lifetime Config
Step 9. Review the configuration and click on Finish.
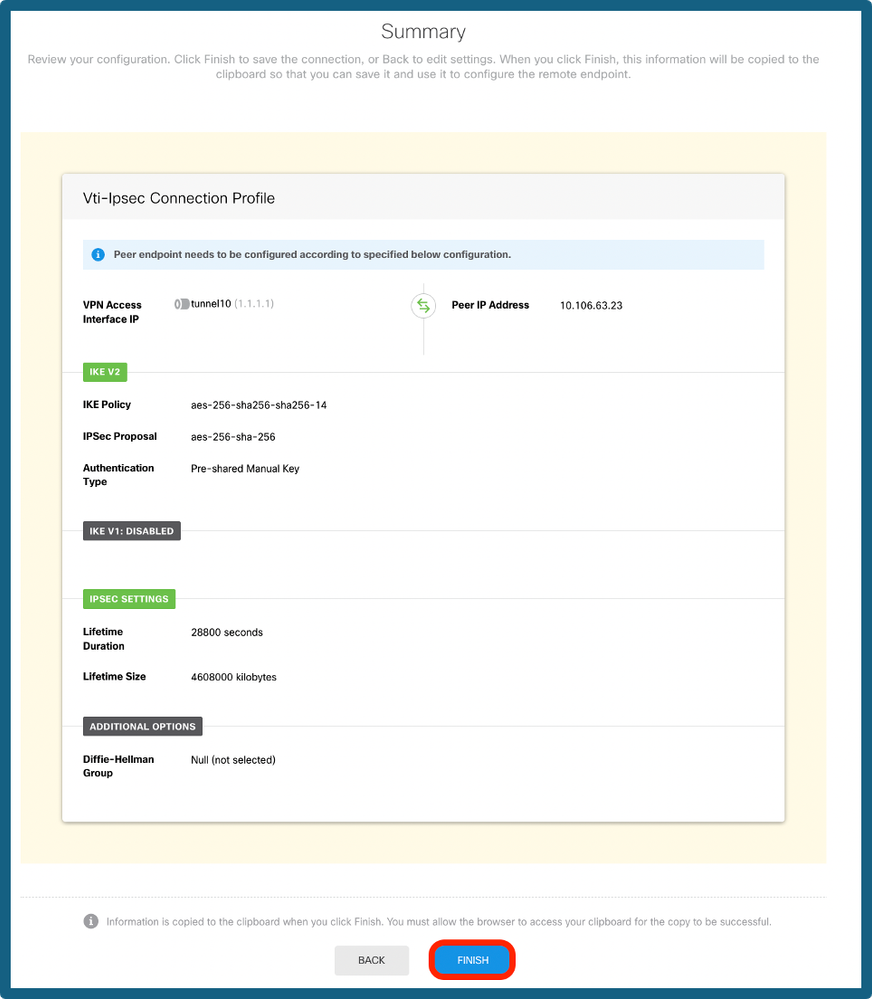 Configuration Summary
Configuration Summary
Step 10a. Navigate to Objects > Security Zones and then click on + icon.
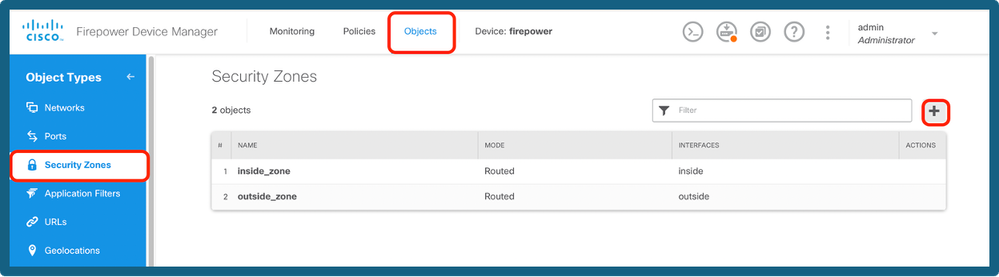 Add a Security Zone
Add a Security Zone
Step 10b. Create a zone, and select the VTI interface as shown below.
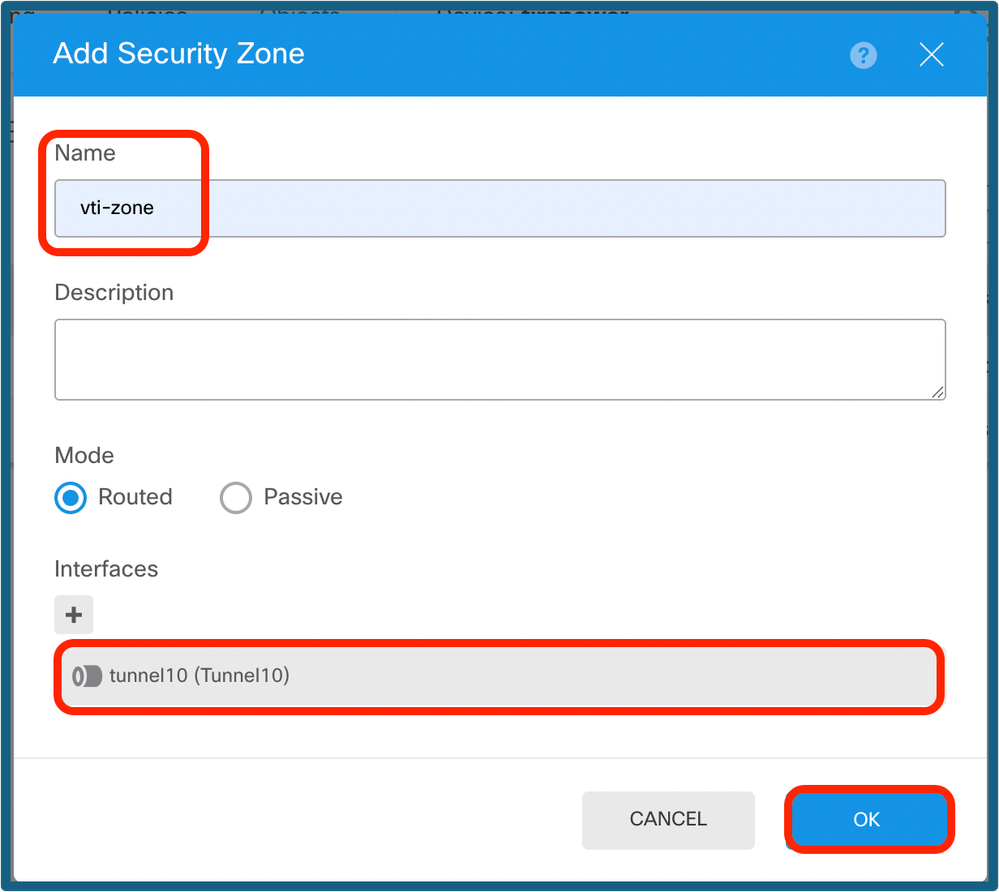 Config of Security Zone
Config of Security Zone
Step 11a. Navigate to Objects > Networks, click on + icon.
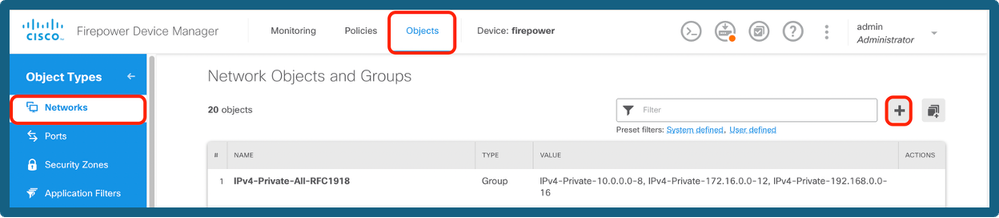 Add Network Objects
Add Network Objects
Step 11b. Add a host object, and create a gateway with tunnel ip of peer end.
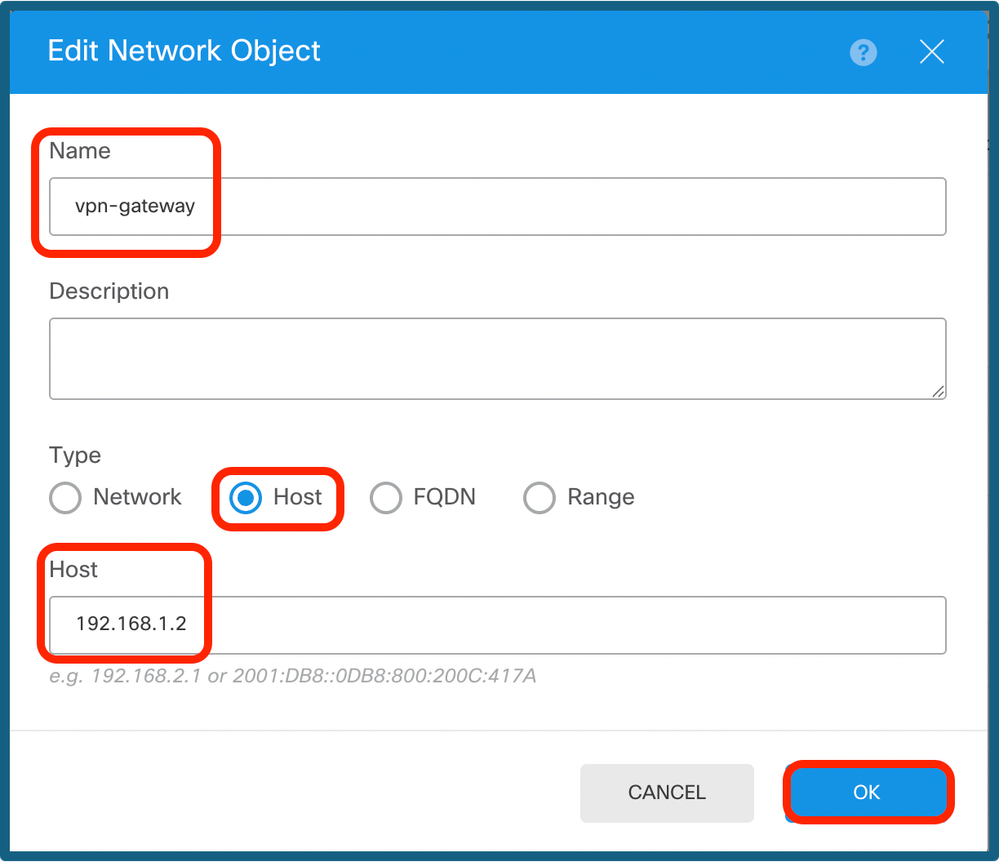 Configure VPN Gateway
Configure VPN Gateway
Step 11c. Add the remote subnet and the local subnet.
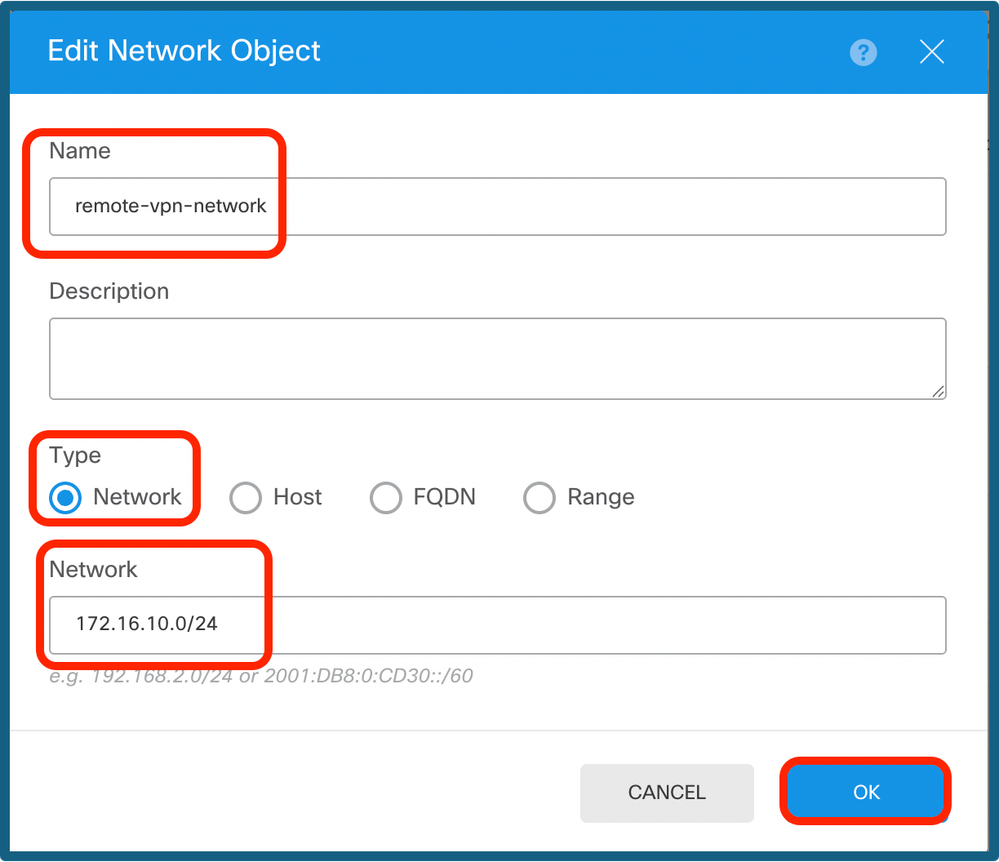 Remote IP Config
Remote IP Config
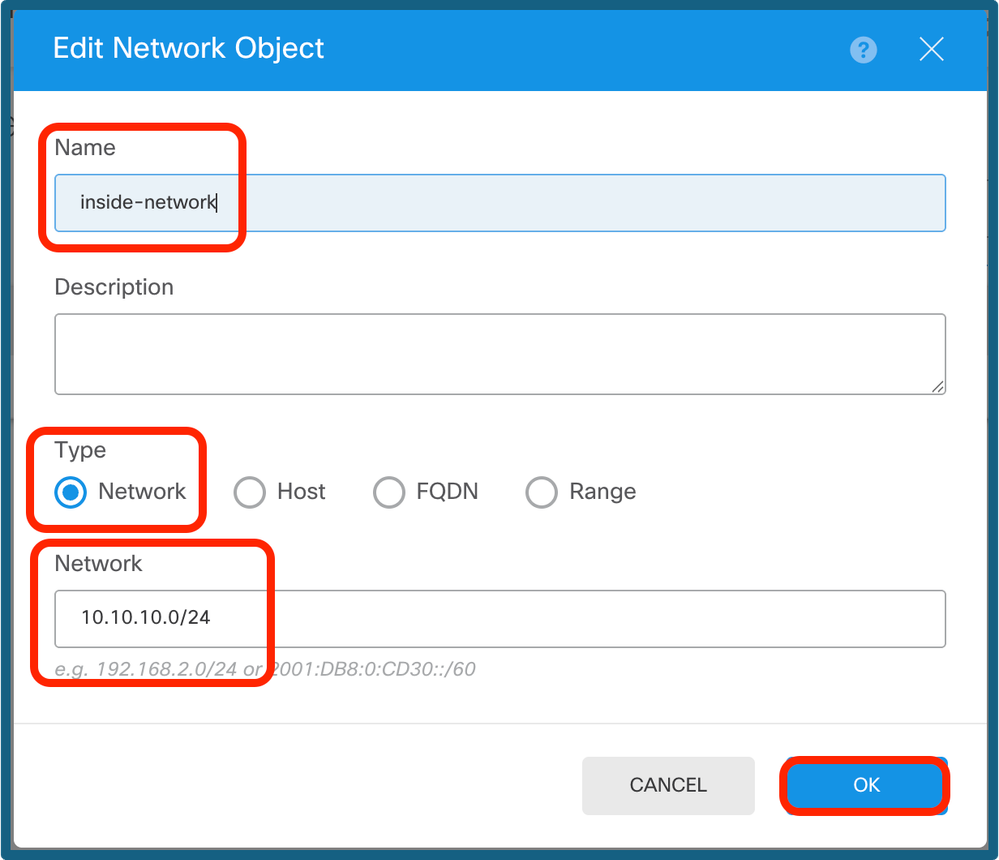 Local IP Config
Local IP Config
Step 12. Navigate to Device > Policies, and configure the Access Control Policy.
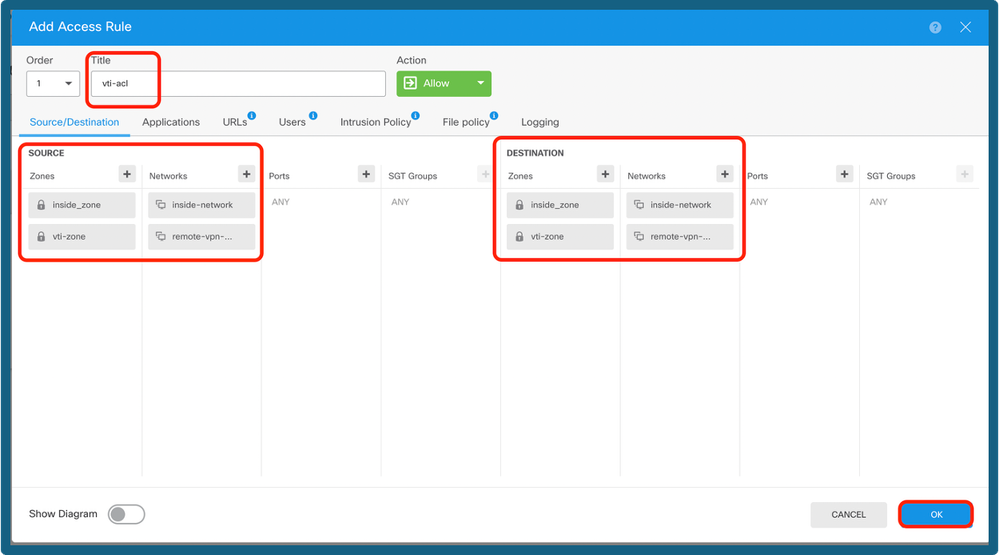 Add Access Control Policy
Add Access Control Policy
Step 13a. Add the routing over the VTI tunnel. Navigate to Device > Routing.
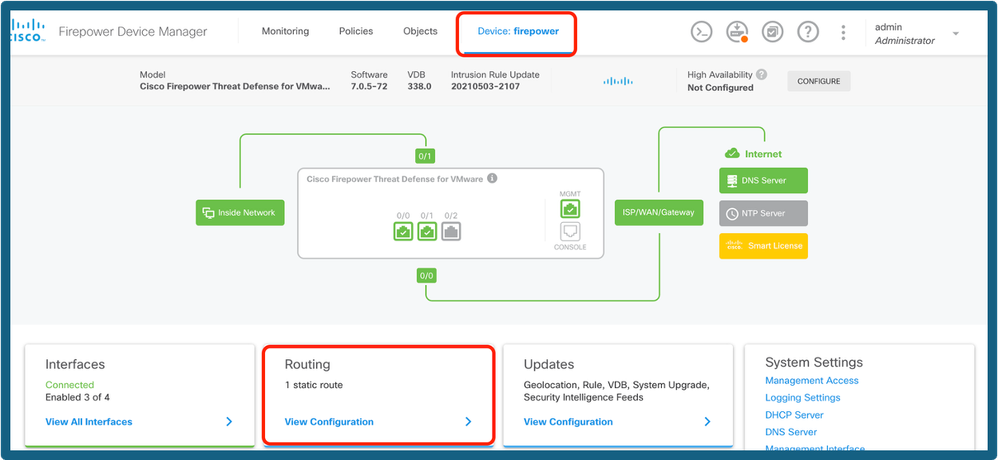 Select Routing
Select Routing
Step 13b. Navigate to Static Route under the Routing tab. Click + icon.
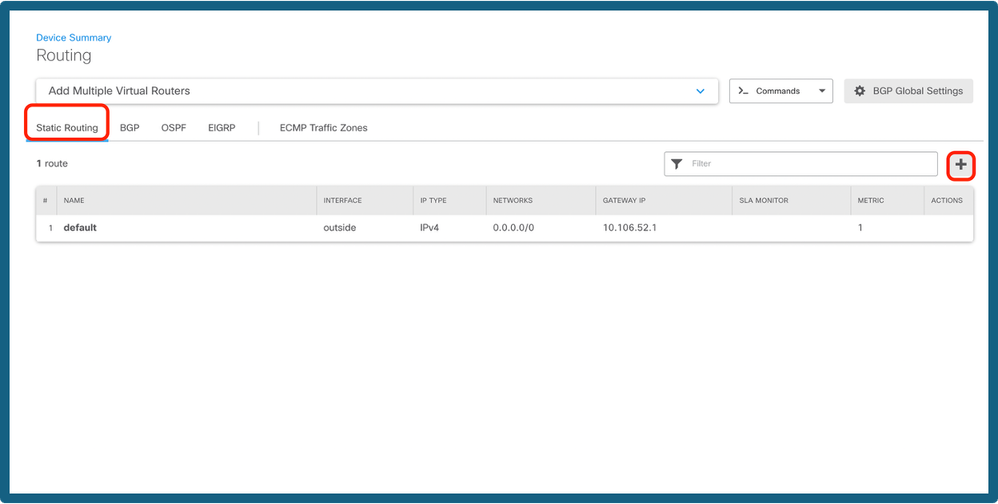 Add Route
Add Route
Step 13c. Provide the Interface, choose the Network, provide the Gateway. Click OK.
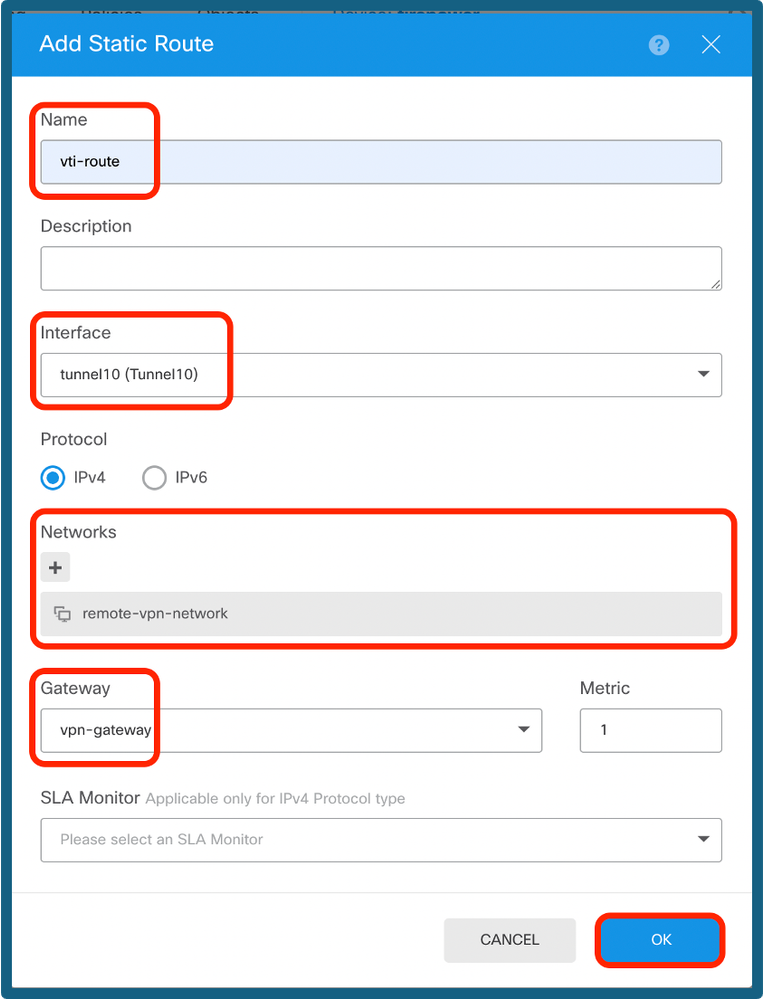 Configure Static Route
Configure Static Route
Step 14. Navigate to Deploy. Review the changes then click on Deploy Now.
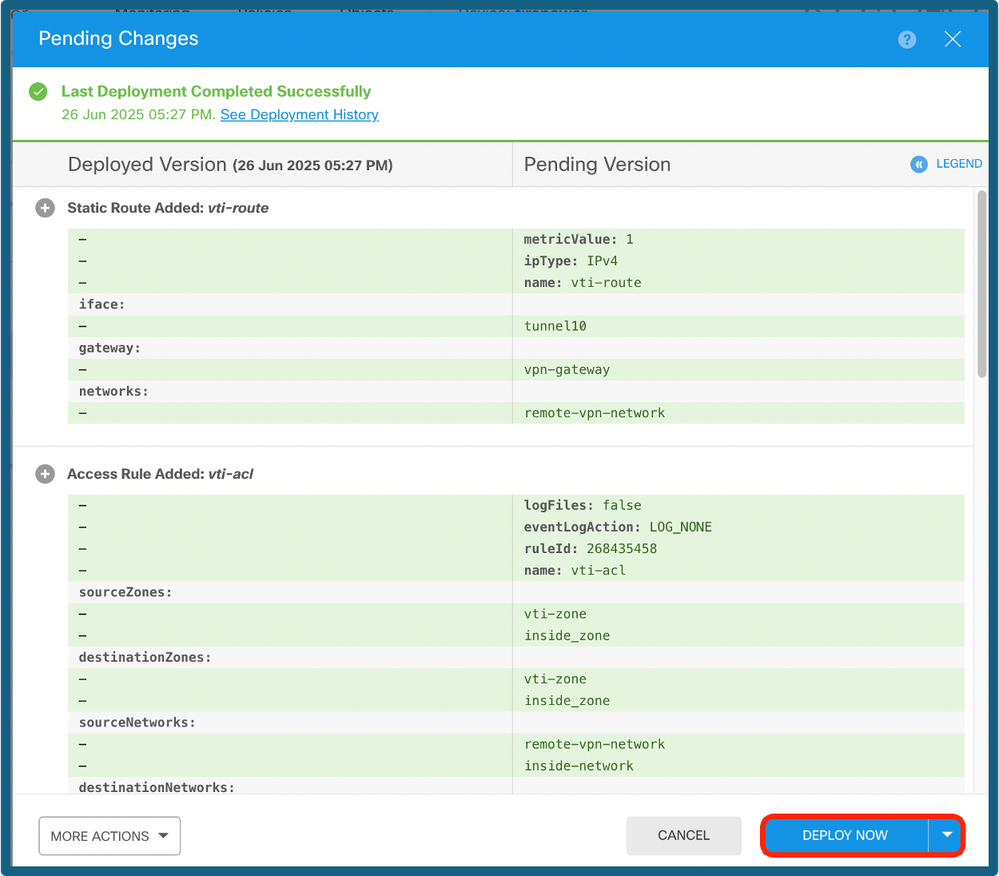 Deploy the Config
Deploy the Config
Verify
Once the deployment is complete, you can verify the tunnel status on CLI by using commands:
- show crypto ikev2 sa
- show crypto ipsec sa <peer-ip>
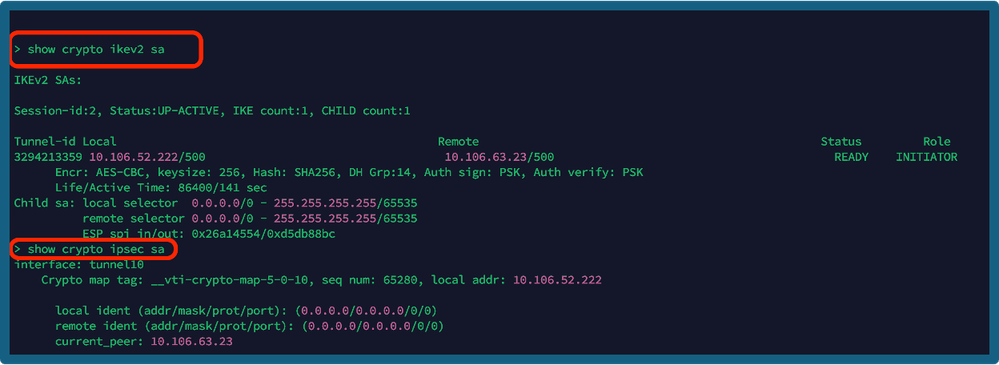 Show Commands
Show Commands
Related Information
For further information regarding Site-to-Site VPNs on the FTD managed by FDM, you can find the full configuration guide here:
FTD Managed by FDM Configuration Guide


























 Feedback
Feedback