Introduction
This document describes Security Group Tag (SGT) Inline Tagging Propagation method in Software-Defined Wide-Area Networks (SD-WAN).
Prerequisites
Cisco recommends that you have knowledge of these topics:
- Cisco Catalyst Software-Defined Wide Area Network (SD-WAN)
- Software-Defined Access (SD-Access) Fabric
- Cisco Identify Service Engine (ISE)
Components Used
The information in this document is based on:
- Cisco IOS® XE Catalyst SD-WAN Edges version 17.9.5a
- Cisco Catalyst SD-WAN Manager version 20.12.4.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Cisco TrustSec Integration
SGT Propagation with Cisco TrustSec Integration is supported by the Cisco IOS® XE Catalyst SD-WAN Release 17.3.1a. This feature enables Cisco IOS® XE Catalyst SD-WAN edge devices to propagate Security Group Tag (SGT) inline tags that are generated by Cisco TrustSec-enabled switches in the branches to other edge devices in the Cisco Catalyst SD-WAN network. While Cisco TrustSec-enabled switches does classification and enforcement on the branches, Cisco IOS® XE Catalyst SD-WAN device devices carry the inline tags across the edge devices.
Basic concepts of Cisco Trustsec:
- SGT Bindings: Association between IP and SGT, all bindings are most common configurated and learned directly from the Cisco ISE.
- SGT Propagation: The propagation methods are used to propagate these SGTs between network hops
- SGTACLs Policies: Set of rules that specify the privileges of a traffic source within a trusted network.
- SGT Enforcement: Where the policies are enforced based on the SGT policy.
SGT Propagation Methods
The SGT propagation methods are:
- SGT Propagation Inline Tagging.
- SGT Propagation Security Group Tag Exchange Protocol (SXP)
SGT Propagation with Inline Tagging
With Inline Tagging, a special Ethernet frame is used to propagate these SGTs between network hops. For Inline Tagging Propagation, the branches need to be equipped with Cisco TrustSec-enabled switches that are capable of handling SGT Inline Tagging (Cisco TrustSec Devices).
Example:
- Branch 1 and Branch 2 are equipped with Cisco TrustSec-enabled switches, and these branches are connected to the Cisco IOS XE Catalyst SD-WAN devices.
- The Cisco TrustSec Switch in the branches are performance the Bindings, Propagation and Enforcement.
- The Cisco TrustSec Switch in Branch 1 performs SGT Inline Tagging in the Ethernet CMD frame toward Edge Router 1.
- The Edge Router 1 then de-encapsulates the CMD frame, extracts the SGT, and propagates it over Cisco Catalyst SD-WAN IPSec or GRE tunnels.
- The Edge Router 2 on Cisco Catalyst SD-WAN extracts the SGT from Cisco Catalyst SD-WAN, generates the Ethernet CMD frame, and copies the that is SGT received.
- The Cisco TrustSec switch on Branch 2 inspects the SGT, and looks it up against the destination SGT to determine if the traffic must be allowed or denied (Enformance).
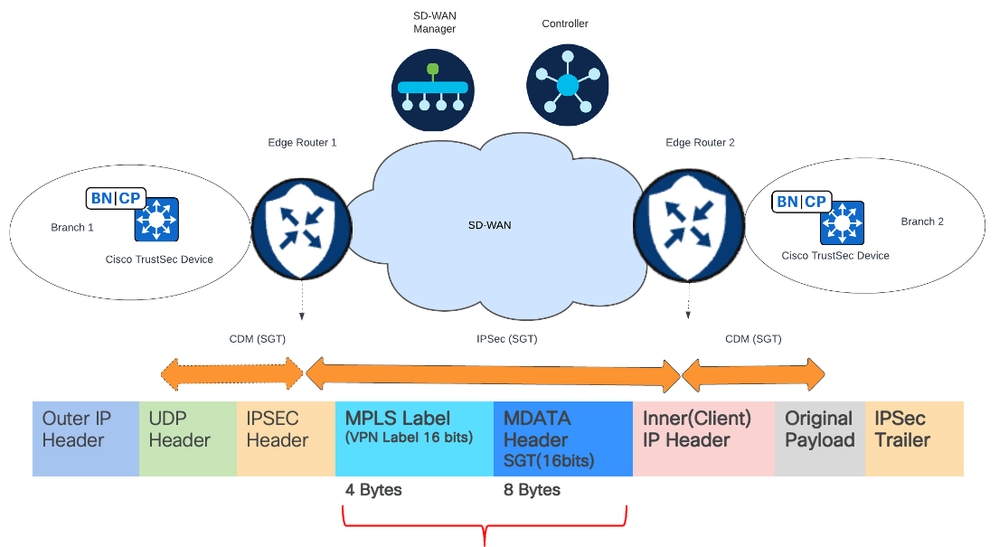 SGT field carried inside the packet that goes accross the Cisco Catalyst SD-WAN packet and an additional eight bytes of data is added to it.
SGT field carried inside the packet that goes accross the Cisco Catalyst SD-WAN packet and an additional eight bytes of data is added to it.
Enable SGT Inline Tagging Propagation in SD-WAN IPSEC tunnels
 Network Diagram for SGT Inlinne Tagging Propagation in SD-WAN IPSEC tunnels
Network Diagram for SGT Inlinne Tagging Propagation in SD-WAN IPSEC tunnels
Step 1. Enable SGT Inline Tagging Propagation on Transport Tunnel Interface (WAN)
- To enable the SGT Inline Tagging Propagation through SD-WAN ipsec tunnels, the Propagation must be enable only in the SD-WAN Tunnel.
- Log in Cisco Catalyst SD-WAN Manager GUI.
- Navigate to Configuration > Templates > Feature Template > Cisco VPN Interface Ethernet (VPN0) > Click on Tunnel.
 Tunnel section
Tunnel section
- Identify CTS SGT Propagation > Select ON
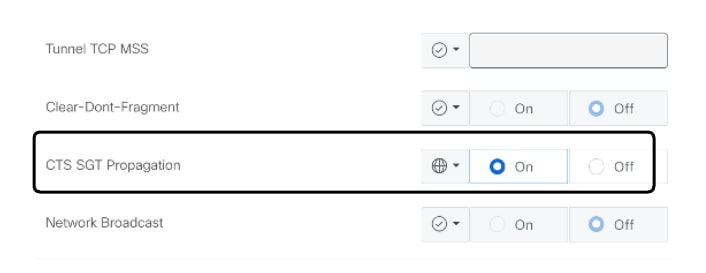 Tunnel configuration
Tunnel configuration
CLI command equivalent:
interface Tunnel0
ip unnumbered GigabitEthernet0/0/0
no ip redirects
ipv6 unnumbered GigabitEthernet0/0/0
no ipv6 redirects
cts manual
tunnel source GigabitEthernet0/0/0
tunnel mode sdwan
Note: Starting 20.6 / 17.6.1 release, SGT Propagation (Inline Tagging) is disable by default on SD-WAN tunnels.
Note: When CTS SGT Propagation is enabled, it momentarily causes the interface to flap.
Note: When CTS SGT Propagation is enabled it in the physical WAN interface could cause connectivity issues like packet drops if the next hop is not able to de-encapsulates the CMD frame that include the SGT.
Step 2. Enable SGT Inline Tagging Propagation on Services Interface (LAN)
- Navigate to Configuration > Templates > Device Template > Service VPN
- Identify the LAN interfaces feature templates for physical Interface and subInterfaces > Cisco VPN Interface Ethernet (Service VPN)
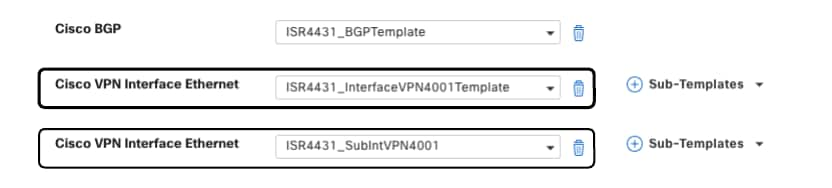 Cisco VPN Interface Feature Template (LAN)
Cisco VPN Interface Feature Template (LAN)
- Navigate to Cisco VPN Interface Ethernet (Service VPN) feature template, Click on TrustSec
 TrustSec section
TrustSec section
- Identify Enable SGT Propagation > Select ON
- Identify Propagate > Select ON
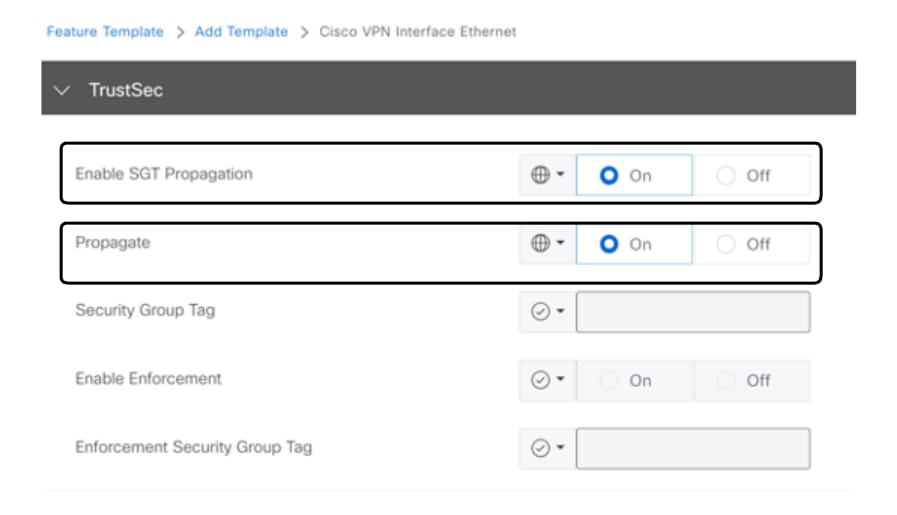 TrustSec configuration
TrustSec configuration
CLI command equivalent:
interface GigabitEthernet0/0/3 <<< Physical Interface
vrf forwarding 4001
no ip address
no ip redirects
ip mtu 1500
load-interval 30
negotiation auto
cts manual
arp timeout 1200
interface GigabitEthernet0/0/3.3 <<< Sub-Interface
encapsulation dot1Q 3
vrf forwarding 4001
ip address 192.168.253.2 255.255.255.252
no ip redirects
ip mtu 1500
cts manual
policy static sgt 999 trusted
arp timeout 1200
Note: On a Cisco IOS® XE Catalyst SD-WAN device, Cisco TrustSec must be enabled on the physical interface and on all the subinterfaces.
Note: This laboratory is focus only in SGT Propagation, the SGT Bindings and SGT Enforcement are made in SD-Access fabric network.
Verify
Run the command show cts interface <interface_name> to display the Cisco TrustSec information for interfaces.
SD-WAN Tunnel Interface.
#show cts interface Tunnel0
Global Dot1x feature is Disabled
Interface Tunnel0:
CTS is enabled, mode: MANUAL
IFC state: OPEN
Interface Active for 1d22h
Authentication Status: NOT APPLICABLE
Peer identity: "unknown"
Peer's advertised capabilities: ""
Authorization Status: NOT APPLICABLE
SAP Status: NOT APPLICABLE
Propagate SGT: Enabled
SD-WAN Service LAN Interface.
#show cts interface GigabitEthernet0/0/3.3
Global Dot1x feature is Disabled
Interface GigabitEthernet0/0/3.3:
CTS is enabled, mode: MANUAL
IFC state: OPEN
Interface Active for 6d14h
Authentication Status: NOT APPLICABLE
Peer identity: "unknown"
Peer's advertised capabilities: ""
Authorization Status: SUCCEEDED
Peer SGT: 999
Peer SGT assignment: Trusted
SAP Status: NOT APPLICABLE
Propagate SGT: Enabled
Configure a FIA Trace in Service LAN Sub-Interface
To identify the SGT for the packets, it can validate through the FIA Trace.
Configure the FIA Trace condition on the LAN interface (GigabitEthernet0/0/3) where SGT Inline Tagging Propagation is enabled.
clear platform condition all
debug platform packet-trace packet 2048 fia-trace data-size 2048
debug platform condition interface GigabitEthernet0/0/3.3 both
Run the command debug platform condition start to start the FIA Trace.
Run the command debug platform condition stop to stop the FIA Trace.
Run the command show platform packet-trace summary to display the FIA trace packets.
#show platform packet-trace summ
Pkt Input Output State Reason
0 Gi0/0/3.3 internal0/0/rp:0 PUNT 3 (Layer2 control and legacy)
1 Gi0/0/3.3 internal0/0/rp:0 PUNT 55 (For-us control)
2 Gi0/0/3.3 Gi0/0/0 FWD
3 Gi0/0/3.3 Gi0/0/0 FWD
4 Gi0/0/3.3 Gi0/0/0 FWD
5 Gi0/0/3.3 Gi0/0/0 FWD
6 Gi0/0/3.3 Gi0/0/0 FWD
7 Gi0/0/3.3 Gi0/0/0 FWD
Run the command show platform packet-trace packet <Packet_Number> decode to decode a packet.
In the packet, identify Feature: SDWAN Forwarding
#show platform packet-trace packet 2 decode
Packet: 2 CBUG ID: 254
Summary
Input : GigabitEthernet0/0/3.3
Output : GigabitEthernet0/0/0
State : FWD
!... Output is suppressed
Feature: SDWAN Forwarding
SDWAN adj OCE:
Output : GigabitEthernet0/0/0
Hash Value : 0x2c
Encap : ipsec
SLA : 0
SDWAN VPN : 4001
SDWAN Proto : MDATA
Out Label : 1003
Local Color : bronze
Remote Color : gold
FTM Tun ID : 2
!... Output is suppressed
MDATA ver : 0x2
MDATA next proto : IPV4(0x1)
MDATA num : 1
MDATA type : SGT_TYPE(0x1)
MDATA SGT : 5 <<<< Packet incoming with SGT 5 and forwarded by Edge router
Related Information








 Feedback
Feedback